CrowdStrike for Department of Defense
Protecting DoD through an adversary-focused, IL5-authorized platform
Advance your DoD Zero Trust Journey with the only IL5 cloud-first and AI-native cybersecurity
platform to protect NIPRNet endpoints, identities, and workloads.
DoD challenges
Simplify Zero Trust journey, consolidate tools, and secure identities
Simplify Zero Trust journey, consolidate tools, and secure identities
Implement DoD
Zero Trust
Zero Trust
DoD must meet Target Level activities by FY27 and must protect Data Applications Assets and Services (DAAS), optimize coverage of the 152 activities, and simplify integrations.
Product sprawl
Numerous point products create complexity and seams that the adversary will exploit. Multiple consoles and screens slow defenders while the adversary takes advantage.
Stolen identities
80% of breaches involve stolen or misused credentials.1 Gaps in enterprise ICAM solutions prevent defenders from having full visibility of the identity problem.
Our solution
Cybersecurity’s AI-native platform to take
the fight to the adversary
Cybersecurity’s AI-native platform to take
the fight to the adversary
Increase visibility while reducing complexity
The average enterprise uses 45+ security tools that create visibility gaps between point products.2 Adversaries attack those seams. By consolidating into a unified, IL5 authorized security platform that is separate from the Operating System, you get native AI capabilities and complete visibility in one place to quickly and confidently discover, identify, and stop breaches.

Counter adversaries 24/7
Our Counter Adversary Operations (CAO) team provides Identity Threat Hunting that pairs intelligence on the latest adversary TTPs with Identity Threat Protection. Elite CAO Threat Hunters quickly identify and remediate compromised credentials and track lateral movement with 24/7 coverage.
Zero Trust and always verify:
protect DAAS with an AI-native platform
Implement policy decision and enforcement points
80% of attacks involve stolen or misused credentials.1 Leverage the CrowdStrike Falcon® platform to provide visibility, and security of identities as the policy decision and enforcement point in the ICAM architecture. The Falcon platform’s 100% coverage of adversary TTPs in closed and open book MITRE tests demonstrate our proficiency in stopping identity misuse.

Visibility and control of devices — managed or not
CrowdStrike integrates with Comply to Connect (C2C) solutions and enables compliance enforcement through the lightweight, CrowdStrike Falcon® sensor. Once installed, the agent gathers data from managed and unmanaged endpoints for complete visibility and control. NGAV, File Integrity Monitoring, EDR/XDR capabilities, and compliance data can all be used with C2C solutions.

Multi and hybrid cloud security
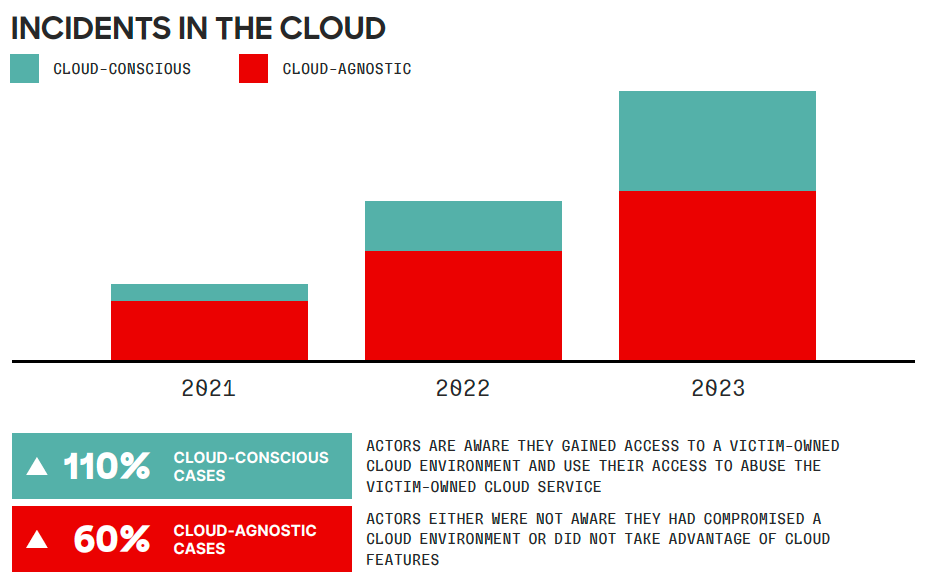
Last year saw a 110% increase in cloud-conscious threat actors and a 75% increase in cloud environment intrusions.1 CrowdStrike Falcon® Cloud Security, the industry’s most complete cloud native application protection platform (CNAPP) protects against cloud- and identity-focused adversary tactics.
Correlate and collaborate on real time detections
OMB Memo M-21-31 requires thorough logging. Leverage CrowdStrike Falcon® LogScale™ to meet those requirements with the speed, scale, and query flexibility your team needs to proactively search for and identify threats in your environment. Identity threat hunters leverage petabyte-scale logging and threat intelligence to counter the 75% increase in malware-free attacks observed in 2023.1

Encounter Sessions: hands-on labs
Encounter Sessions: hands-on labs
The definitive cybersecurity
platform of the AI era
Trillions
of security events monitored daily3
230+
adversaries tracked1
100%
Prevention of TTPs in MITRE Engenuity ATT&CK® Evaluations4