Shifting Left with the CrowdStrike and AWS CI/CD Pipeline

Introduction
CI/CD combines the practices of continuous integration (CI) and Continuous Delivery (CD) to allow DevOps teams to deliver code updates frequently, reliably, and quickly. CI/CD emphasizes automation throughout the development lifecycle (Build, Test, Deploy). By replacing the manual efforts of traditional development, code releases can happen more frequently, and with less bugs and security vulnerabilities.
At CrowdStrike, we focus on integrating security into the CI/CD pipeline. As part of the functionality of CrowdStrike’s Falcon Cloud Workload Protection (CWP), customers have the ability to create verified image policies to ensure that only approved images are allowed to progress through the CI/CD pipeline and run in their hosts or Kubernetes clusters.
Video
Lab Environment
Let’s take a look at the steps involved in setting up the environment.
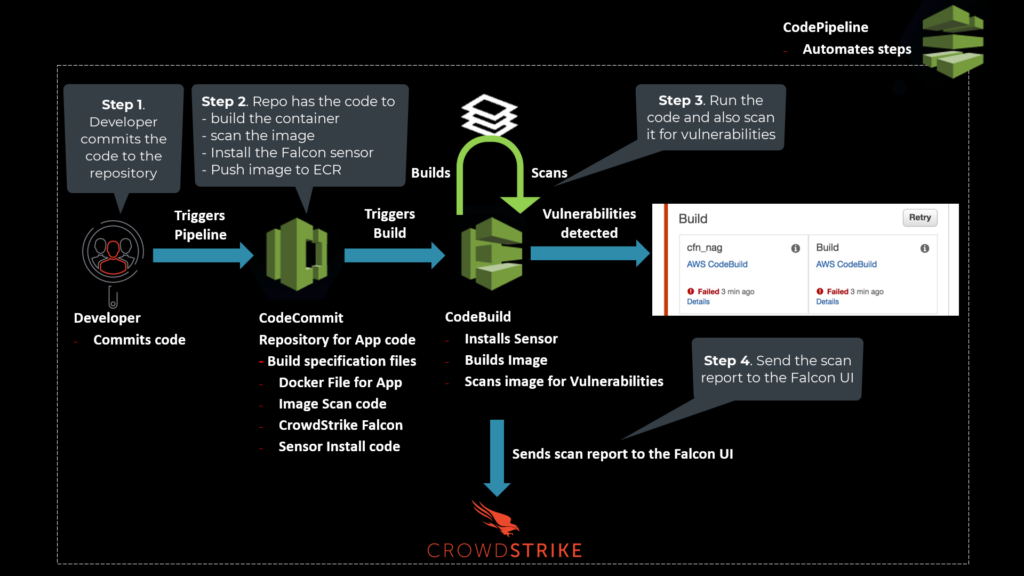
Step 1. Developer commits the code to the repository.
Step 2. The CodeCommit repo has the code to
- build the container
- scan the image
- Install the Falcon sensor
- Push image to ECR
Step 3. CodeBuild compiles the code and also scans it for vulnerabilities.
Step 4. If there are vulnerabilities found in the image, CodeBuild sends the scan report to the Falcon UI.
Step 5. If there are no vulnerabilities, CodeBuild publishes the image to ECR for deployment in production.

The role of CodePipeline in all of this is to automate the steps required to release the software changes continuously.
Demo
All the code is stored in the CodeCommit “webapp” Repository. The webapp repo has a collection of folders and buildspec files. Buildspec stands for Build Specification. A buildspec is a collection of build commands and related settings, in YAML format, that CodeBuild uses to run a build. The Full Project is available on the CrowdStrike GitHub.

- The app folder has the Docker file with the Operating system and Web application information

- The CrowdStrike image scan folder has the Code to scan the image

- The sensor image import folder has the Code to install the Falcon node sensor

- The falcon buildspec file publishes the verified (non-vulnerable) image to the Elastic Container Registry (ECR)

CodeBuild compiles the code and scans for vulnerabilities
Scenario 1 – Vulnerabilities detected
The webapp build failed as the code had vulnerabilities

Falcon UI shows the vulnerabilities found in the image. You can access this by going to Cloud Security > Kubernetes & Containers > Image Assessment > Vulnerabilities.

Scenario 2 – Vulnerabilities not detected
The webapp build passed as the code had no vulnerabilities.

If we open the Webapp project, we can see that the source provider is CodePipeline.

If we go into the Build Run, we can see that CodePipeline is the initiator.

Then we go to CodePipeline and we can see the Webapp pipeline.

CodePipeline shows all the steps involved – Source, Build, Deploy.

The passed image is published to ECR for deployment in production

The tighter the integration between security and the pipeline, the earlier threats can be identified, and the more the speed of delivery can be accelerated. By seamlessly integrating with the AWS CI/CD pipeline, Falcon CWP allows DevOps teams to respond and remediate incidents even faster within the toolsets they use.
