Unlock Advanced Security Automation for Next-Gen SIEM
Increase productivity and reduce mean time to respond (MTTR) with native workflow automation for Falcon Next-Gen SIEM

According to the CrowdStrike 2024 Global Threat Report, the fastest recorded eCrime breakout time was just 2 minutes and 7 seconds in 2023. This underscores the need to equip security analysts with modern tools that level the playing field and enable them to work more efficiently and effectively.
Today’s analysts require a new generation of security information and event management (SIEM) technology capable of scaling to manage petabytes of data, working seamlessly with security orchestration, automation and response (SOAR) capabilities to stop breaches.
CrowdStrike Falcon® Fusion SOAR, the no-code orchestration, automation and response capability built into the CrowdStrike Falcon® platform, is now available to enable workflow automation for third-party data with CrowdStrike Falcon® Next-Gen SIEM. Legacy SIEMs have failed the SOC, but Falcon Next-Gen SIEM introduces a new approach to eliminate slow queries, complex architectures and costly data ingestion. With its new features and enhancements, Falcon Fusion SOAR is well-positioned to help your security team realize the benefits that automation can deliver.
Elevate SOC Efficiency and Accuracy with Workflow Automation
Security automation is your secret weapon to stopping attacks and improving your bottom line. It reduces the time needed to respond to threats, cuts the costs of integrating and operating tools, and improves your security analysts’ job satisfaction by eliminating repetitive tasks, allowing the team to focus on higher-level responsibilities that cannot be automated.
Automation can significantly enhance the efficiency of the SOC. While SIEMs excel at detecting threats by analyzing vast amounts of data, they still force security analysts to manually triage detections and filter out false positives. Many investigation tasks are repetitive and time-consuming, keeping teams from stopping real threats quickly. This is where SOAR steps in to boost efficiency, driving detections to resolution and establishing a continuous information loop.
Enhance Security Operations from Detection to Action
Falcon Fusion SOAR slashes response times during an investigation — when every second counts. It not only improves the technical effectiveness of security operations by working as a cohesive unit but also optimizes operational efficiency by breaking down information silos and eliminating data transfer delays. It ensures that data flows seamlessly and bi-directionally between Falcon Next-Gen SIEM and Falcon Fusion SOAR to act on the most current information available, providing you with a real-time view of your security posture and a feedback loop for continuous improvement.
Falcon Fusion SOAR can query both Falcon platform data as well as third-party data in Falcon Next-Gen SIEM to further threat investigations and store data, such as query results, ensuring that security teams have the most up-to-date view of their data. It also accelerates responses, as Falcon Fusion SOAR can execute workflows that are automatically from a Falcon Next-Gen SIEM detection, scheduled for continuous protection or launched on-demand in response to critical threats.
Additionally, Falcon Fusion SOAR has the ability to drive workflow automation based on Falcon platform alerts and data, such as endpoint, cloud and identity, as well as third-party data collected by Falcon Next-Gen SIEM. This consolidated solution provides you with unrivaled visibility into your data and significantly reduces the time spent on detection, investigation and response.
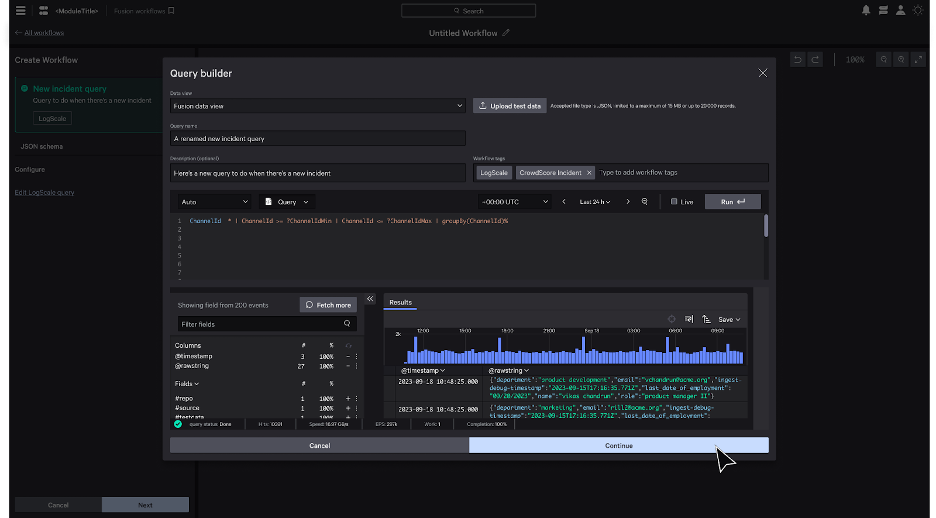
Figure 1. Optimize security operations efficiency and effectiveness with Falcon Next-Gen SIEM and Falcon Fusion SOAR.
Empowering Security Teams with No-Code Workflow Automation
Security analysts are often overwhelmed by the high number of alerts they must triage and respond to. While workflow automation is a powerful tool that can simplify security processes, cumbersome playbook development can hinder progress. Implementing orchestration and automation requires clearly defined processes, a deep understanding of the technologies being orchestrated and knowledge on how to translate these into automated processes. And often, complex decisions require human involvement. Given the advanced skills required to code playbooks and the scarcity of security talent, security teams need tools that prioritize a modern analyst experience and offer a significant advantage against adversaries.
As a native capability of Falcon Next-Gen SIEM, Falcon Fusion SOAR provides analysts with a unified experience that combines world-class security data and workflow automation to stop breaches. The newly redesigned workflow builder allows security analysts to easily visualize their workflows as they build them with an intuitive top to bottom flow for improved readability and usability. Analysts can simply select different building blocks without needing to code, making automation accessible even to more junior analysts.
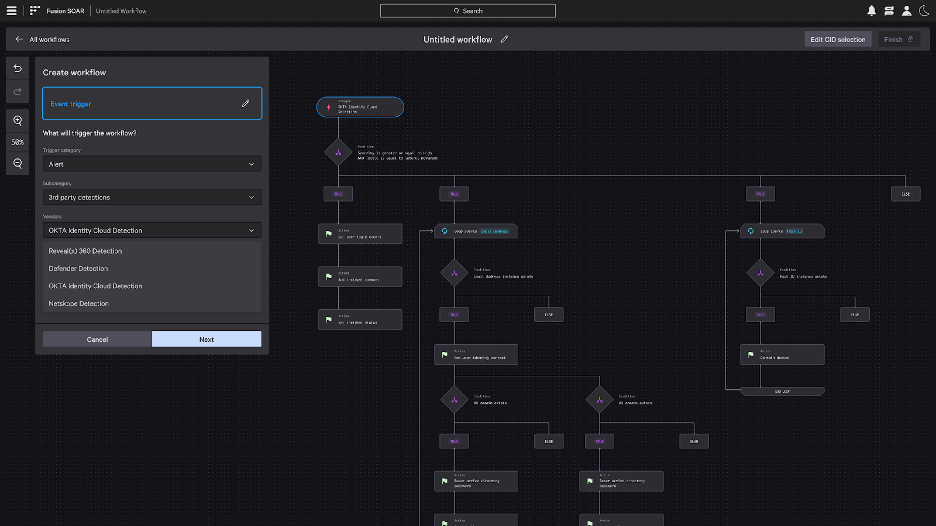
Figure 2. Deploy workflow automation in minutes with the new workflow builder interface.
Depending on the complexity of the workflow, building it can only take only a few minutes. Once the use case has been identified, analysts need to select a trigger, define conditions and configure the actions. Falcon Fusion SOAR supports the orchestration of complex use cases with conditional branching and logic, and by seamlessly integrating with Falcon Real Time Response (RTR) to execute any action on the endpoint. When key decision making and approvals are necessary, team members can be notified via email, Slack or your preferred communication method as part of the workflow.
To give your team a headstart, Falcon Fusion SOAR offers a growing library of out-of-the-box playbooks for common use cases. These playbook templates can be easily customized to meet your organization’s policies and technology stack.
Falcon Fusion SOAR recently released a new phishing integration and playbook to help your team automate response to emails reported as phishing by employees in your organization.The workflow integrates with MS365, authorizing Falcon Fusion to have read-only access to your organizations’ phishing inbox. When an email is reported as phishing, the workflow begins the investigation process by searching all email components for enrichment. If malicious indicators are identified, the workflow will quarantine or block indicators, update third-party tools and create custom IOCs to start a retroactive search.
Figure 3. Falcon Fusion SOAR’s new phishing playbook template will enable your team to deploy workflow automation as soon as an email is reported as a phishing email.
Optimize Incident Response with Workflow Automation Insights
Workflow automation helps security teams cut mean time to respond (MTTR) by gathering and enriching data, guiding analysts through investigations and orchestrating, and automatically remediating attacks. It also reduces the risk of human error by driving consistent, standardized actions. Additionally, it has the potential to improve your security posture by providing insights into trends and execution, helping to better understand performance, enhance collaboration and identify areas of improvement.
Falcon Fusion SOAR offers at-a-glance insights through a metrics dashboard that enables you to view detailed workflow executions, including the various actions executed by each workflow, and related detections. This comprehensive information, along with other trends, enhances the understanding of the status and context of an incident. All of this information is readily available in a unified view within the Falcon platform, thereby reducing “swivel-chair syndrome” for your team and allowing them to concentrate efforts on the most critical threats.
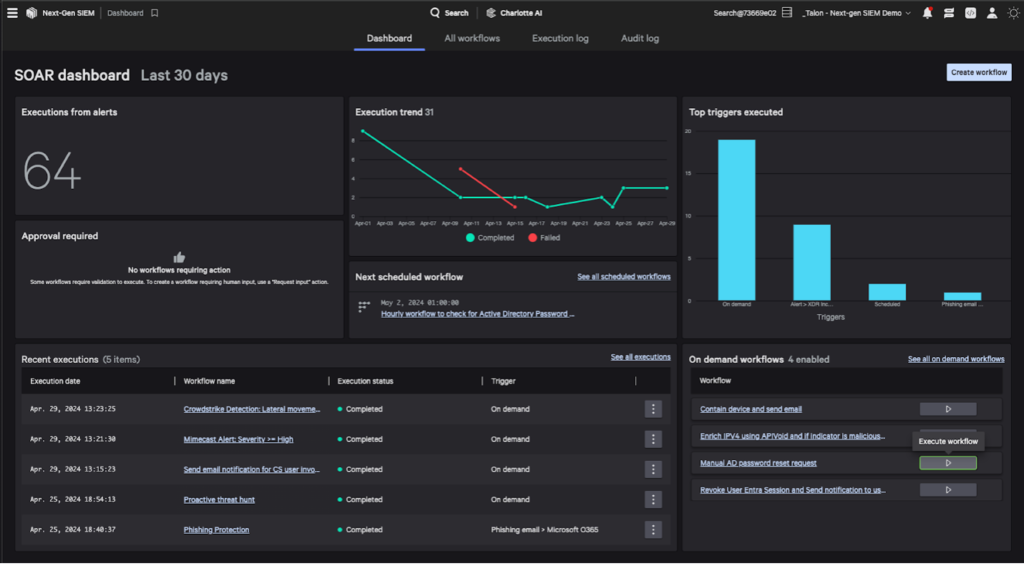
Figure 4. Understand and improve your security posture with SOAR insights at a glance.
Next-Level Threat Management with Falcon Next-Gen SIEM
With its native SOAR capabilities powered by Falcon Fusion SOAR, Falcon Next-Gen SIEM accelerates threat detection, investigation and response — all from a single console. This gives your team the speed to keep pace with adversaries and the focus to address the threats that put your organization at risk.
Additional Resources
- Want to learn more about Falcon Fusion? Visit the Falcon Fusion SOAR product page.
- Download the Falcon Fusion SOAR data sheet to learn about our integrated SIEM and SOAR capabilities.
- Sign up to attend our Next-Gen SIEM Showcase to see Falcon Next-Gen SIEM and Falcon Fusion SOAR in action.
- Sign up to request a test drive of Falcon Next-Gen SIEM to see how Falcon Fusion SOAR augments the module.
- Watch on demand: CrowdStrike’s AI-Native SOC Summit: The Next Generation of SIEM, Here Today
- Read our SOC Survival Guide to learn how to revolutionize your SOC.