CrowdStrike vs. Splunk
Don’t let Splunk slow you down. Supercharge your SOC with CrowdStrike Falcon® Next-Gen SIEM.
Why customers choose CrowdStrike over Splunk
 Splunk Too slow for modern adversaries
Splunk Too slow for modern adversaries
-
×Poor search speeds hamper incident investigation and threat hunting
-
×Lengthy indexing creates delays in data search availability
-
×Complex infrastructure requirements for on-prem deployments degrade performance
The CrowdStrike difference
CrowdStrike Stop breaches with unprecedented speed
Built from the ground up for high performance, Falcon Next-Gen SIEM offers blazing-fast, real-time search speeds. Queries execute in a fraction of the time as legacy SIEMs, decreasing incident response times and reducing analyst burnout.
Customer Assessment
60 x
Faster search speeds than Splunk1
 Splunk Cost prohibitive
Splunk Cost prohibitive
-
×Customers are forced to exclude important data sources, creating significant visibility gaps
-
×Complex pricing model leads to unexpected costs and surprise uplifts at renewal
-
×Burdensome operational requirements drive up total cost of ownership
The CrowdStrike difference
CrowdStrike Better ROI, better outcomes
Falcon Next-Gen SIEM has modern architecture that helps customers achieve better security outcomes at a lower cost. With more affordable subscriptions and unprecedented platform scalability, CrowdStrike customers don’t need to compromise on security by excluding critical log sources.
Customer Assessment
80 %
Savings over three years versus legacy SIEM1
 Splunk Complex point product
Splunk Complex point product
-
×Relies solely on third-party log telemetry, making data onboarding and indexing complex and onerous
-
×Requires multiple dedicated employees just for maintenance, management, and usage
-
×No ability to natively consolidate across security products like endpoint, identity, cloud, exposure management and threat intelligence
The CrowdStrike difference
CrowdStrike The definitive platform for cybersecurity consolidation
CrowdStrike replaces legacy SIEMs with a modern security analyst experience delivered through a single, easy-to-use console. With all critical data and threat intelligence from CrowdStrike products already available in Falcon Next-Gen SIEM, CrowdStrike completely alleviates the painful data onboarding experience that frustrates legacy SIEM customers.
Customer Assessment
10 +
Security tools consolidated with the CrowdStrike Falcon Platform1
 Compare
Compare
 Empty heading
Empty heading
Splunk
Data onboarding
 Instant availability of first-party data
Instant availability of first-party data
Falcon Next-Gen SIEM provides instant availability of all native CrowdStrike telemetry, including endpoint, cloud, and identity data, eliminating data onboarding challenges for your SOC’s most critical data sources. Additionally, third-party data can be easily ingested through pre-built connectors.
 Complex data onboarding
Complex data onboarding
Security engineers are forced to invest significant time and resources managing data ingestion, indexing, and parsing. This increases the operational burden and creates delays between when data ingestion and when it becomes searchable.
Search speed
 Faster search speeds for rapid investigations
Faster search speeds for rapid investigations
Real-time search that’s significantly faster than legacy SIEMs. Effortlessly search across both live and historic data to find threats faster and prevent breaches.
 Slow search performance hinders incident response
Slow search performance hinders incident response
Splunk’s slower search speeds can delay threat hunting and lead to analyst burnout. As networks grow, search speeds deteriorate further without proper management.
Architecture
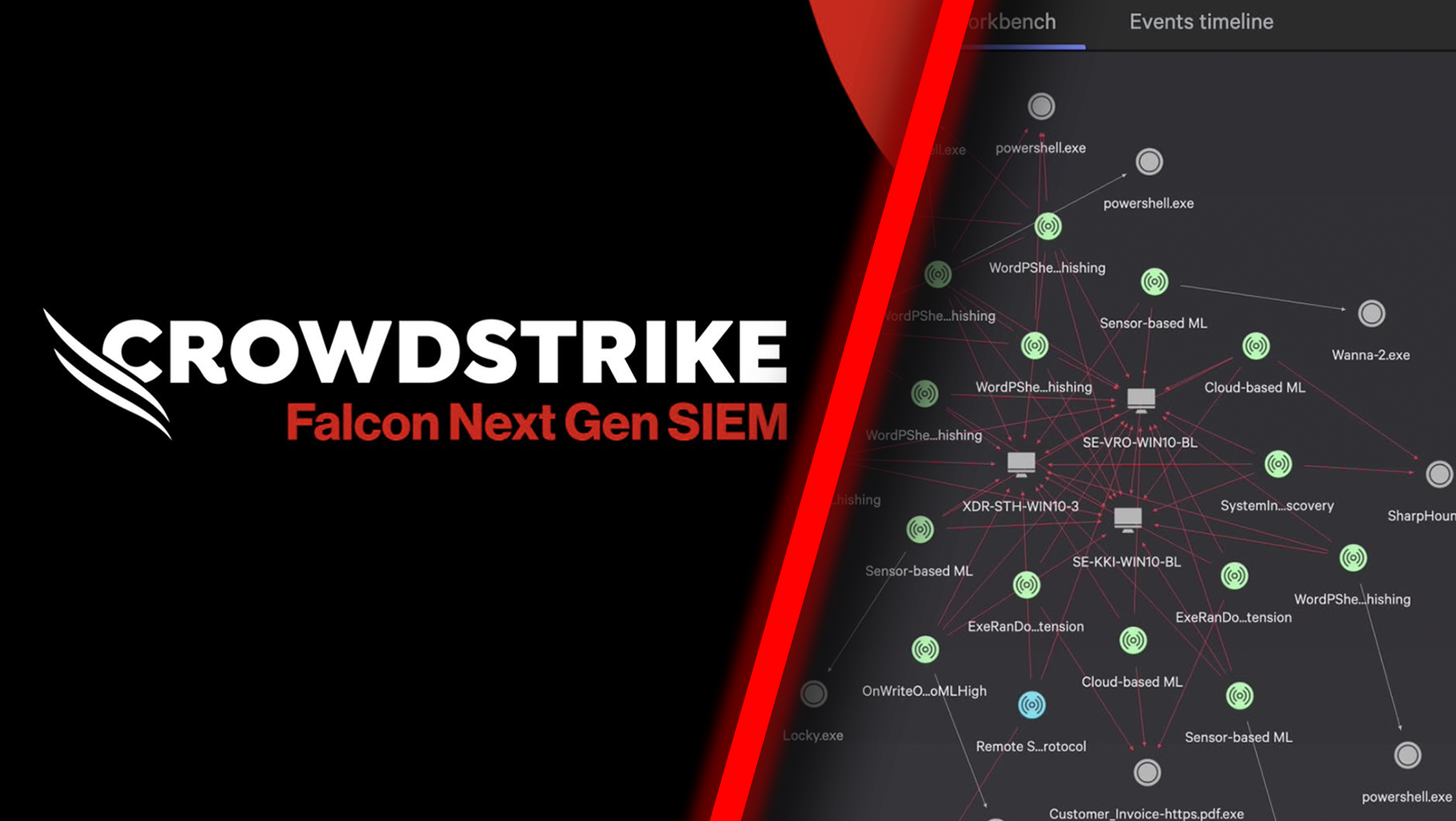
 Harness the power of “index-free”
Harness the power of “index-free”
Index-free architecture allows security teams to enjoy real-time ingestion at petabyte scale, live dashboards, and faster search and alerting capabilities.
 Index-based architecture leads to issues
Index-based architecture leads to issues
Splunk’s index-based architecture presents several challenges, including excessive resource consumption and slow search times.
Detection content
 Comprehensive out-of-the-box detections
Comprehensive out-of-the-box detections
The Falcon platform offers out-of-the-box detection content across endpoints, cloud, identity, and more, providing robust protection against today’s most sophisticated adversaries. Our superior performance in the latest MITRE detection results, combined with pre-built SIEM correlation rules, ensures comprehensive coverage.
 Limited out-of-the-box detections
Limited out-of-the-box detections
Out-of-the-box, Splunk lacks security-specific detection rules from native sources. Instead, Splunk relies on correlation rules that require manual configuration with third-party data sources or extensive custom rule-building to become operational for security use cases.
Threat intelligence
 Global threat intelligence leader
Global threat intelligence leader
Falcon Next-Gen SIEM reveals indicators of compromise (IOCs) in your environment, giving your analysts instant context to help determine adversary objectives.
 No native threat intelligence
No native threat intelligence
Splunk lacks an in-house threat intelligence service, requiring customers to supply their own threat intelligence feeds.
Managed services
 All inclusive managed services
All inclusive managed services
Falcon Complete provides full-cycle remediation without the need for additional personnel. Our world-class team shows you how to gain real-time visibility and insights from your log data to maximize security efficacy.
 No in-house managed services
No in-house managed services
Splunk doesn’t offer an in-house MDR service. Customers must allocate multiple employees to use, configure, and manage Splunk, resulting in higher costs.
 See the power of Falcon Next-Gen SIEM in under three minutes
See the power of Falcon Next-Gen SIEM in under three minutes
 See what our customers think
See what our customers think
[We secure] the data from millions of users from cyberattacks and web scraping with Falcon Next-Gen SIEM and log management platform, [which] allows us to efficiently and effectively respond to any security incident that pops up.
[CrowdStrike] gives us total visibility of our environment. Compared to other SIEMs I’ve used, [CrowdStrike] performs better, is more customizable and requires less overhead.
The ease of ingestion and search speed of Falcon LogScale definitely stood out during the POC.

The value for the money that CrowdStrike offered was hard to challenge. Pella is a growing business and we saw that investing in CrowdStrike would help us improve security in an expanding and more complex environment. Also, we found that CrowdStrike managed services have a level of maturity nobody else could match.
CrowdStrike Falcon Endpoint Protection Platform provides protections for all kinds of threats, exploits, known and unknown threats, it also supports all types of cloud infrastructures along with different types of container platforms.
One of the best EDR solutions in market. I really like the interface of the platform, it is so much user friendly. False positives are very less compared to the previous endpoint security solutions we have used. A light weight agent makes it a very stable product.
I would highly recommend CrowdStrike Falcon to any organization serious about bolstering its cybersecurity defenses. The platform’s effectiveness in threat detection, proactive mitigation, and scalability make it a valuable asset in today’s ever-evolving threat landscape.
CrowdStrike is the next level security for cyber protection offering the best protection and innovative software.
The best feature of CrowdStrike Falcon is that it is very easy to use and manage and works in offline mode also and the product implementation was very easy and the customer support was also helpful.
I have been in the industry for close to thirty years and this has been one of the best endpoint protection programs I have ever used. We feel confident as an organization that we are protected on the endpoints at all times. The Falcon Complete team is great for providing assistance whenever we need it.
CrowdStrike Falcon Cloud Security addresses critical cybersecurity challenges by providing real-time threat detection, rapid response capabilities, and seamless integration. This proactive approach enhances our overall security posture, safeguarding digital assets and ensuring a robust defense against evolving threats.
CrowdStrike Falcon Cloud Security is an awesome tool with great capabilities, it offers easy to use interface where administrator can do monitoring and do the policy configuration.
Falcon Complete is amazing for smaller Security Teams that need enterprise class endpoint protection.
CrowdStrike has built a very powerful combination of modules that cover a broad swath of the cyber security mission, especially as it relates to endpoint. While no security tool is a silver bullet, Falcon does a great job of tackling some of the most prevalent and impactful challenges in defending endpoints.
I would highly recommend CrowdStrike Falcon to any organization serious about bolstering its cybersecurity defenses. The platform’s effectiveness in threat detection, proactive mitigation, and scalability make it a valuable asset in today’s ever-evolving threat landscape.
CrowdStrike is the next level security for cyber protection offering the best protection and innovative software.
The best feature of CrowdStrike Falcon is that it is very easy to use and manage and works in offline mode also and the product implementation was very easy and the customer support was also helpful.
I have been in the industry for close to thirty years and this has been one of the best endpoint protection programs I have ever used. We feel confident as an organization that we are protected on the endpoints at all times. The Falcon Complete team is great for providing assistance whenever we need it.
CrowdStrike Falcon Cloud Security addresses critical cybersecurity challenges by providing real-time threat detection, rapid response capabilities, and seamless integration. This proactive approach enhances our overall security posture, safeguarding digital assets and ensuring a robust defense against evolving threats.
CrowdStrike Falcon Cloud Security is an awesome tool with great capabilities, it offers easy to use interface where administrator can do monitoring and do the policy configuration.
Falcon Complete is amazing for smaller Security Teams that need enterprise class endpoint protection.
CrowdStrike has built a very powerful combination of modules that cover a broad swath of the cyber security mission, especially as it relates to endpoint. While no security tool is a silver bullet, Falcon does a great job of tackling some of the most prevalent and impactful challenges in defending endpoints.
[We secure] the data from millions of users from cyberattacks and web scraping with Falcon Next-Gen SIEM and log management platform, [which] allows us to efficiently and effectively respond to any security incident that pops up.
[CrowdStrike] gives us total visibility of our environment. Compared to other SIEMs I’ve used, [CrowdStrike] performs better, is more customizable and requires less overhead.
The ease of ingestion and search speed of Falcon LogScale definitely stood out during the POC.

The value for the money that CrowdStrike offered was hard to challenge. Pella is a growing business and we saw that investing in CrowdStrike would help us improve security in an expanding and more complex environment. Also, we found that CrowdStrike managed services have a level of maturity nobody else could match.
CrowdStrike Falcon Endpoint Protection Platform provides protections for all kinds of threats, exploits, known and unknown threats, it also supports all types of cloud infrastructures along with different types of container platforms.
One of the best EDR solutions in market. I really like the interface of the platform, it is so much user friendly. False positives are very less compared to the previous endpoint security solutions we have used. A light weight agent makes it a very stable product.
I would highly recommend CrowdStrike Falcon to any organization serious about bolstering its cybersecurity defenses. The platform’s effectiveness in threat detection, proactive mitigation, and scalability make it a valuable asset in today’s ever-evolving threat landscape.
CrowdStrike is the next level security for cyber protection offering the best protection and innovative software.
The best feature of CrowdStrike Falcon is that it is very easy to use and manage and works in offline mode also and the product implementation was very easy and the customer support was also helpful.
I have been in the industry for close to thirty years and this has been one of the best endpoint protection programs I have ever used. We feel confident as an organization that we are protected on the endpoints at all times. The Falcon Complete team is great for providing assistance whenever we need it.
CrowdStrike Falcon Cloud Security addresses critical cybersecurity challenges by providing real-time threat detection, rapid response capabilities, and seamless integration. This proactive approach enhances our overall security posture, safeguarding digital assets and ensuring a robust defense against evolving threats.
CrowdStrike Falcon Cloud Security is an awesome tool with great capabilities, it offers easy to use interface where administrator can do monitoring and do the policy configuration.
Falcon Complete is amazing for smaller Security Teams that need enterprise class endpoint protection.
CrowdStrike has built a very powerful combination of modules that cover a broad swath of the cyber security mission, especially as it relates to endpoint. While no security tool is a silver bullet, Falcon does a great job of tackling some of the most prevalent and impactful challenges in defending endpoints.
[We secure] the data from millions of users from cyberattacks and web scraping with Falcon Next-Gen SIEM and log management platform, [which] allows us to efficiently and effectively respond to any security incident that pops up.
[CrowdStrike] gives us total visibility of our environment. Compared to other SIEMs I’ve used, [CrowdStrike] performs better, is more customizable and requires less overhead.
The ease of ingestion and search speed of Falcon LogScale definitely stood out during the POC.

The value for the money that CrowdStrike offered was hard to challenge. Pella is a growing business and we saw that investing in CrowdStrike would help us improve security in an expanding and more complex environment. Also, we found that CrowdStrike managed services have a level of maturity nobody else could match.
CrowdStrike Falcon Endpoint Protection Platform provides protections for all kinds of threats, exploits, known and unknown threats, it also supports all types of cloud infrastructures along with different types of container platforms.
One of the best EDR solutions in market. I really like the interface of the platform, it is so much user friendly. False positives are very less compared to the previous endpoint security solutions we have used. A light weight agent makes it a very stable product.
I would highly recommend CrowdStrike Falcon to any organization serious about bolstering its cybersecurity defenses. The platform’s effectiveness in threat detection, proactive mitigation, and scalability make it a valuable asset in today’s ever-evolving threat landscape.
CrowdStrike is the next level security for cyber protection offering the best protection and innovative software.
The best feature of CrowdStrike Falcon is that it is very easy to use and manage and works in offline mode also and the product implementation was very easy and the customer support was also helpful.
I have been in the industry for close to thirty years and this has been one of the best endpoint protection programs I have ever used. We feel confident as an organization that we are protected on the endpoints at all times. The Falcon Complete team is great for providing assistance whenever we need it.
CrowdStrike Falcon Cloud Security addresses critical cybersecurity challenges by providing real-time threat detection, rapid response capabilities, and seamless integration. This proactive approach enhances our overall security posture, safeguarding digital assets and ensuring a robust defense against evolving threats.
CrowdStrike Falcon Cloud Security is an awesome tool with great capabilities, it offers easy to use interface where administrator can do monitoring and do the policy configuration.
Falcon Complete is amazing for smaller Security Teams that need enterprise class endpoint protection.
CrowdStrike has built a very powerful combination of modules that cover a broad swath of the cyber security mission, especially as it relates to endpoint. While no security tool is a silver bullet, Falcon does a great job of tackling some of the most prevalent and impactful challenges in defending endpoints.
[We secure] the data from millions of users from cyberattacks and web scraping with Falcon Next-Gen SIEM and log management platform, [which] allows us to efficiently and effectively respond to any security incident that pops up.
[CrowdStrike] gives us total visibility of our environment. Compared to other SIEMs I’ve used, [CrowdStrike] performs better, is more customizable and requires less overhead.
The ease of ingestion and search speed of Falcon LogScale definitely stood out during the POC.

The value for the money that CrowdStrike offered was hard to challenge. Pella is a growing business and we saw that investing in CrowdStrike would help us improve security in an expanding and more complex environment. Also, we found that CrowdStrike managed services have a level of maturity nobody else could match.
CrowdStrike Falcon Endpoint Protection Platform provides protections for all kinds of threats, exploits, known and unknown threats, it also supports all types of cloud infrastructures along with different types of container platforms.
One of the best EDR solutions in market. I really like the interface of the platform, it is so much user friendly. False positives are very less compared to the previous endpoint security solutions we have used. A light weight agent makes it a very stable product.
I would highly recommend CrowdStrike Falcon to any organization serious about bolstering its cybersecurity defenses. The platform’s effectiveness in threat detection, proactive mitigation, and scalability make it a valuable asset in today’s ever-evolving threat landscape.
1. Results are from a customer. Individual results may vary.
2. These numbers are
projected estimates of average benefit based on recorded metrics provided by customers during pre-sale
motions that compare the value of CrowdStrike with the customer’s incumbent solution. Actual realized
value will depend on individual customer’s module deployment and environment.





