CrowdStrike vs. Wiz
Don’t settle for an incomplete cloud security (CNAPP) point product that can’t stop breaches.
Why customers choose CrowdStrike over Wiz
 Wiz An incomplete CNAPP
Wiz An incomplete CNAPP
- ×Lacks essential cloud security capabilities
- ×Runtime protection is based on static rules that can generate a significant amount of false positives
- ×No native ASPM, leading to reduced visibility into application workloads and APIs
- ×Missing native security modules needed for critical alert context and attack path analysis (EDR, identity, threat intel, exposure management)
The CrowdStrike difference
CrowdStrike The industry’s most complete CNAPP
CrowdStrike Falcon® Cloud Security integrates all aspects of cloud security — CWP, CSPM, CIEM, CDR, ASPM, AI-SPM, and DSPM — into a unified console, enhancing threat visibility and correlation across cloud, endpoint, identity, and more, for complete attack path analysis and quicker investigations.
 Wiz Lacking in prevention capabilities, and can’t stop breaches effectively
Wiz Lacking in prevention capabilities, and can’t stop breaches effectively
- ×Limited runtime prevention capabilities to stop threats in real-time
- ×Can’t terminate malicious container processes or quarantine files after initial detection
- ×Absence of agent-based AI/ML detection needed to catch stealthy attacks
- ×Forces customers to rely on third-party tools for incident response
The CrowdStrike difference
CrowdStrike Built to stop breaches
CrowdStrike’s advanced runtime protection capabilities are built on the same unified agent as our leading EDR and identity protection. The Falcon agent delivers deep visibility, detection, and real-time response across the entire cloud-native stack, including all workloads, containers, and Kubernetes.
 Wiz Incomplete CDR and lacks expert services
Wiz Incomplete CDR and lacks expert services
- ×No in-house managed services, widening the skills gaps for customers
- ×No in-house managed cloud threat hunting
- ×No Digital Forensics and Incident Response (DFIR), penetration testing, or adversary emulation, yielding ineffective response
- ×No integrated threat intelligence, leaving customers unprepared for today’s sophisticated attacks
The CrowdStrike difference
CrowdStrike The CDR Pioneer
CrowdStrike is the only CDR that unifies world-class threat intelligence and elite 24/7 managed services with complete, industry-leading cloud security. CrowdStrike’s integrated threat intelligence tracks 230+ adversaries, providing a comprehensive understanding of a wide array of potential threats, enabling organizations to anticipate and respond to attacks more effectively.
 Compare
Compare
Wiz
Cloud-Native Application Protection Platform (CNAPP)
 The industry’s most complete CNAPP
The industry’s most complete CNAPP
The industry’s only CNAPP that natively integrates CWP, CSPM, CDR, CIEM, ASPM, AI-SPM, and DSPM in a single, unified platform to deliver unified visibility and blocks threats across cloud infrastructure, applications, and data.
 An incomplete CNAPP
An incomplete CNAPP
Inadequate CNAPP lacks key cloud security features, such as runtime prevention, visibility into application workloads and APIs.
Runtime Protection
 Comprehensive runtime protection
Comprehensive runtime protection
The Falcon agent delivers deep visibility, detection, and real-time response across the entire cloud-native stack, including all workloads, containers, and Kubernetes applications to prevent cloud-based threats.
 Immature, limited agent
Immature, limited agent
Wiz’s runtime protection capabilities were released very recently and are based on static rules that can generate a significant amount of false positives, leaving customers unable to effectively stop initial intrusion or ongoing attacks in real time, and cannot prevent breaches effectively against advanced techniques.
Cloud Detection and Response (CDR)
 The new standard in CDR
The new standard in CDR
Unrivaled protection, unifying the world’s most complete CNAPP with pioneering adversary intelligence and elite 24/7 services to shut down cloud breaches.
 No in-house services for CDR
No in-house services for CDR
Wiz has no professional or managed services offerings, which leaves customers facing potential skill gaps in implementation, threat hunting, incident investigation, and response.
Threat Intelligence
 World-class threat intelligence
World-class threat intelligence
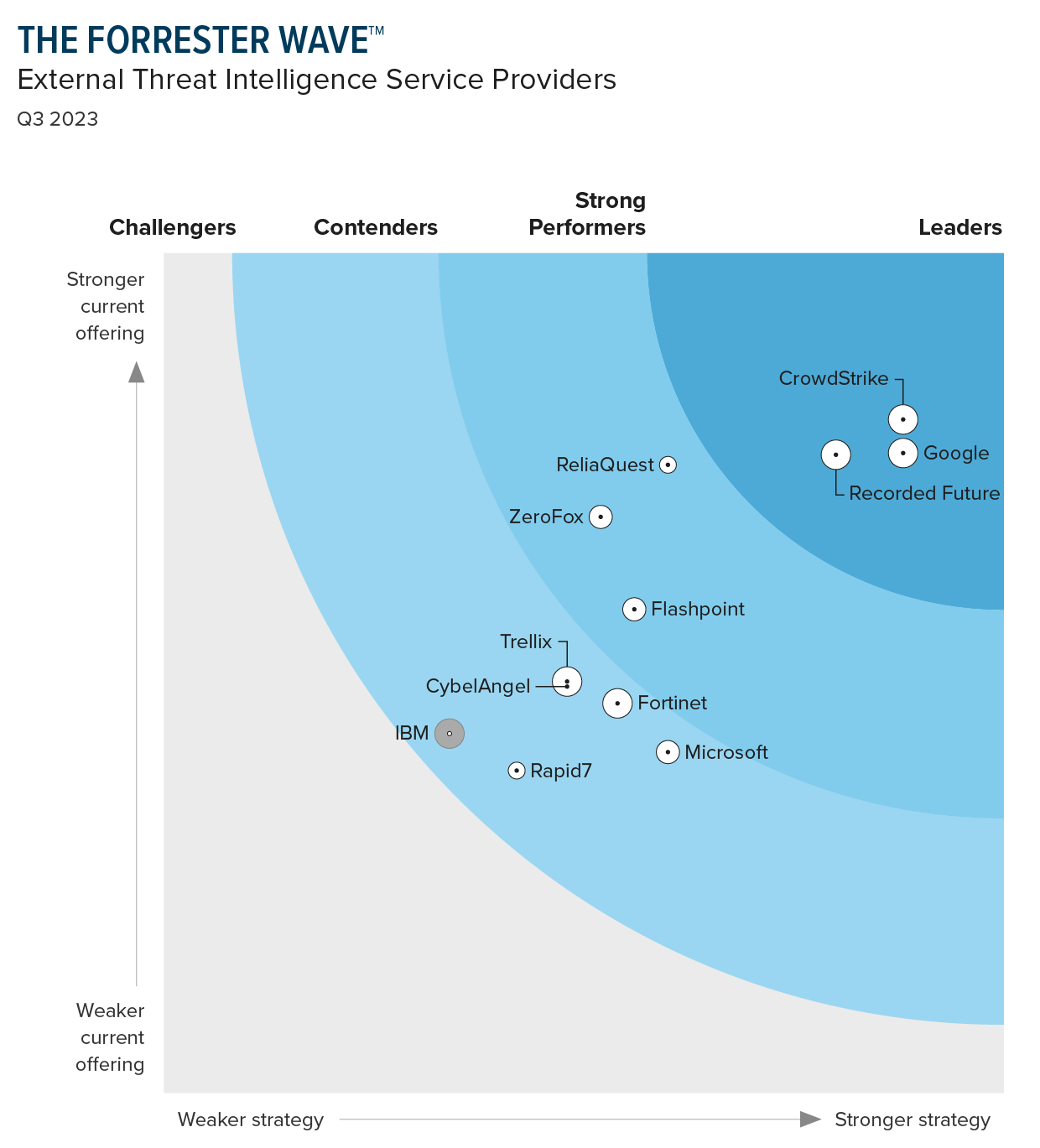
CrowdStrike was named a Leader in External Threat Intelligence Services, with the highest ranking of all vendors in the Current Offering category. Full alert context and advanced detections defeats adversaries proactively.
 Limited intelligence means ineffective response
Limited intelligence means ineffective response
Wiz has no integrated threat intelligence, leaving SOC teams blind. With no threat actor profiles, adversary tactic discovery or documented IOCs, customers are ill-equipped to defend against today’s sophisticated adversaries.
Analyst Validation
 The validated market leader
The validated market leader
CrowdStrike is a Leader in:
 Just a follower
Just a follower
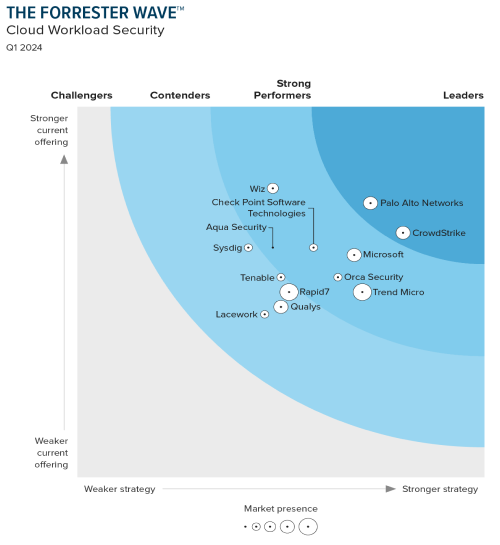
Wiz was only a “Strong Performer” in the Forrester Wave™: Cloud Workload Security, Q1 2024. They were excluded entirely from the Gartner MQ for EPP and Forrester Waves for Threat Intel and MDR because they don’t offer these solutions, exposing significant gaps in their offerings.
Generative AI
 Accelerate SecOps with Charlotte AI
Accelerate SecOps with Charlotte AI
CrowdStrike enhances the analyst experience at every stage by leveraging AI and machine learning. This includes high-fidelity ML-powered classification from sensor to cloud, cross-domain behavioral analysis at runtime, and GenAI-assisted workflows to accelerate investigation and response.
 Slow, manual operations
Slow, manual operations
Wiz lacks a GenAI assistant to aid analysts in investigation and response. The scope of Wiz’s AI/ML is limited and often results in a high rate of false positives, complicating the analyst’s work experience and delaying effective response.
 Validated by industry leading analysts
Validated by industry leading analysts
 See what our customers think
See what our customers think
1. Results are from a customer. Individual results may vary.
2. These numbers are projected estimates of average benefit based on recorded metrics provided by customers during pre-sale motions that compare the value of CrowdStrike with the customer’s incumbent solution. Actual realized value will depend on individual customer’s module deployment and environment.