What is cyber threat intelligence?
Threat intelligence refers to the collection, processing, and analysis of data to understand a threat actor’s motives, targets, and attack methods. It transforms raw data into actionable insights, enabling security teams to make informed, data-driven decisions. This shifts organizations from a reactive to a proactive stance in defending against cyber threats.
According to Gartner, threat intelligence is evidence-based knowledge that provides context, mechanisms, indicators, and action-oriented advice on both existing and emerging threats. This knowledge includes everything from understanding attack mechanisms to predicting future threats, allowing organizations to bolster their defenses.
Why is threat intelligence important?
In the ever-evolving landscape of cybersecurity, threat intelligence plays a critical role in keeping organizations one step ahead of attackers. With the rise of advanced persistent threats (APTs), threat intelligence offers invaluable insight into adversaries’ tactics, techniques, and procedures (TTPs), helping defenders anticipate and preempt potential attacks.
While many organizations understand the importance of threat intelligence, they often use it in a limited capacity—typically by integrating threat data feeds into existing tools like firewalls, intrusion prevention systems (IPS), and security information and event management systems (SIEMs). While useful, this basic application only scratches the surface of what threat intelligence can offer.
Benefits of threat intelligence
- Illuminates the unknown: Threat intelligence uncovers hidden threats, enabling security teams to make more informed decisions and prepare for unforeseen attacks.
- Reveals adversary behavior: By understanding attackers' TTPs, security professionals gain insight into the decision-making processes of threat actors, which allows for better defense strategies.
- Empowers decision-making: Business leaders like CISOs, CIOs, and CTOs can leverage threat intelligence to make more informed investment decisions, mitigate risks, and improve operational efficiency.
- Proactive defense: Threat intelligence helps organizations move from reacting to incidents to proactively anticipating and preventing attacks.
Who benefits from threat intelligence?
Threat intelligence provides critical value to organizations of all sizes by helping them understand attackers, respond faster to incidents, and proactively anticipate threats. Here’s how different roles within an organization benefit from threat intelligence:
1. Small and Medium-Sized Businesses (SMBs):
Benefit: SMBs often lack the resources to build comprehensive in-house security operations. Threat intelligence helps them achieve a level of protection they otherwise couldn't afford, offering insights that allow them to prioritize defenses and mitigate risk.
2. Enterprises:
Benefit: For larger organizations with dedicated security teams, threat intelligence reduces costs, minimizes the required skill set for incident handling, and enhances the effectiveness of security analysts by integrating external data into their operations.
How threat intelligence benefits specific roles:
Threat Intelligence Lifecycle
The threat intelligence lifecycle is a continuous process that transforms raw data into actionable intelligence, guiding security teams to make informed decisions. This cycle consists of six key steps, each creating a feedback loop for continuous improvement:
1. Requirements:
Objective: Define the goals and methodology of the intelligence program, aligning with stakeholder needs. Key questions include understanding the attacker’s motivations, identifying the attack surface, and outlining actions to improve defenses.
2. Collection:
Objective: Gather information from sources such as traffic logs, public data, forums, social media, and subject matter experts to address the defined requirements.
3. Processing:
Objective: Organize and clean raw data into a format suitable for analysis, which may include decrypting files, translating foreign data, or formatting it into spreadsheets.
4. Analysis:
Objective: Analyze the processed data to answer questions posed in the requirements phase and produce actionable insights and recommendations.
5. Dissemination:
Objective: Present findings in a digestible format, tailored to the stakeholder audience, whether through reports or slide decks, without overwhelming them with technical details.
6. Feedback:
Objective: Gather feedback from stakeholders to refine future threat intelligence operations, adjust priorities, or change the format of reporting as needed.
Threat intelligence use cases for each role

Below is a list of use cases by function:
3 types of threat intelligence
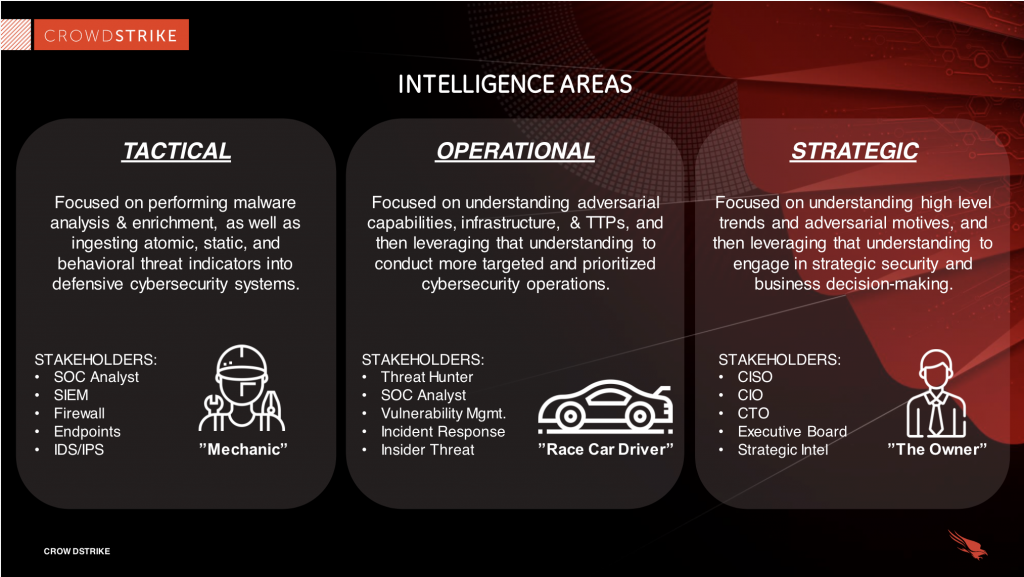
Threat intelligence comes in varying levels of complexity and detail, each catering to different audiences and offering distinct advantages. The three primary types are Tactical, Operational, and Strategic threat intelligence, representing a maturity curve in cyber threat intelligence (CTI). As you progress from tactical to strategic intelligence, the depth of analysis and context increases, making each type progressively more resource-intensive.
1. Tactical Threat Intelligence
Challenge: Many organizations focus only on immediate threats without understanding the bigger picture.
Objective: Broaden the perspective on threats to address underlying security issues.
Tactical intelligence is technical and focused on the immediate future. It deals primarily with indicators of compromise (IOCs) such as malicious IP addresses, URLs, file hashes, and domain names. This type of intelligence is often automated and machine-readable, meaning it can be integrated into security tools via data feeds or API integrations.
However, IOCs have a short lifespan, as threat actors frequently change their infrastructure, rendering these indicators obsolete in a short time. While tactical intelligence is easy to obtain from open-source feeds, it is prone to false positives and lacks strategic analysis. Simply subscribing to a feed may overwhelm a team with data without clear guidance on how to use it.
Questions to ask:
Do you have an IOC feed in place?
Are the IOCs you're using timely and relevant?
Is malware analysis automated?
2. Operational threat intelligence
Challenge: Threat actors employ techniques that are effective, opportunistic, and low-risk, making it difficult to predict their next moves.
Objective: Engage in tracking campaigns and threat actor profiling to gain insight into the adversaries' tactics, techniques, and procedures (TTPs).
Operational threat intelligence provides a deeper understanding of the "who," "why," and "how" behind an attack. This intelligence focuses on attribution (the "who"), motivation (the "why"), and the TTPs (the "how"). Operational intelligence provides context that helps security teams understand how attackers plan and sustain campaigns.
Unlike tactical intelligence, operational intelligence is not automated. It requires human analysis to convert data into actionable insights. Operational intelligence has a longer lifespan than tactical intelligence because adversaries cannot easily change their TTPs as quickly as they change specific tools or malware.
Questions to ask:
Is your SOC using threat actor TTPs to create actionable use cases?
Are you prioritizing vulnerabilities based on CTI?
Are you using CTI-derived rules (e.g., Yara or Snort) for threat hunting?
3. Strategic threat intelligence
Challenge: Poor business decisions often result from a lack of understanding of the broader context surrounding adversarial actions.
Objective: Use threat intelligence to inform business decisions and long-term cybersecurity strategies.
Strategic intelligence offers a high-level perspective on how cyber threats intersect with global events, geopolitical conditions, and organizational risks. For example, nation-state attacks may be linked to geopolitical events, and financially motivated cybercrime groups adapt their techniques based on broader economic trends.
This type of intelligence is typically used by executive leadership (CISOs, CIOs, CTOs) to understand the impact of cyber threats on the organization and guide cybersecurity investments that align with the company’s strategic priorities.
Strategic intelligence is the most difficult to generate, requiring human expertise in both cybersecurity and geopolitics. It typically comes in the form of detailed reports that inform long-term decision-making.
Questions to ask:
How do global and local events affect the organization's cybersecurity?
Is your leadership using strategic intelligence to make informed decisions about cybersecurity investments?

2024 Threat Hunting Report
In the CrowdStrike 2024 Threat Hunting Report, CrowdStrike unveils the latest tactics of 245+ modern adversaries and shows how these adversaries continue to evolve and emulate legitimate user behavior. Get insights to help stop breaches here.
Download NowCrowdStrike's threat intelligence tools

CrowdStrike Falcon® Adversary Intelligence, provides organizations with powerful tools to consume, analyze, and act on threat intelligence effectively. It helps businesses of all sizes operationalize their cybersecurity by automating investigations, delivering actionable insights, and providing custom intelligence tailored to the specific threats an organization faces.
How CrowdStrike operationalizes threat intelligence
1. Integrated intelligence, tailored to your organization
- CrowdStrike Falcon® Adversary Intelligence automates threat investigation, allowing organizations to stop manually selecting which threats to prioritize. Instead, it delivers custom indicators of compromise (IOCs) tailored to the threats identified on your endpoints. This automated approach helps businesses quickly analyze the most relevant threats and take proactive action.
- The solution integrates seamlessly into the organization's cybersecurity operations, ensuring that the intelligence is not just collected but also actionable, helping security teams respond faster and more effectively.
2. Comprehensive toolset for threat investigation
CrowdStrike Falcon® Adversary Intelligence combines the essential tools used by elite cyber threat investigators into a single, integrated solution. These tools include:
- Malware analysis: Automatically analyze malicious files to understand their behavior and origins.
- Malware search: Identify known malware strains targeting the organization.
- Global IOC feed: Gain real-time access to CrowdStrike’s expansive IOC database for proactive threat hunting and defense.
These tools enable organizations to identify and respond to cyber threats quickly and effectively, no matter the size or sophistication of their security teams.
3. Prebuilt integrations and API access
CrowdStrike supports SIEMs and Threat Intelligence Platforms (TIPs) by offering prebuilt integrations and API access to its Falcon Adversary Intelligence solution. This allows businesses to integrate threat intelligence directly into their existing security infrastructure, enhancing the value of their existing tools and enabling more streamlined intelligence operations.
CrowdStrike Falcon® Adversary Intelligence Premium: the human element
For organizations that require deeper insights, CrowdStrike Falcon® Adversary Intelligence Premium provides access to the expertise of CrowdStrike’s Counter Adversary Operations team, which includes seasoned analysts, security researchers, cultural experts, and linguists. The premium service offers:
- Expert analysis: With over 245+ tracked nation-state, cybercrime, and hacktivist groups, CrowdStrike offers unparalleled insights into adversaries' tactics, techniques, and motives.
- Proactive intelligence: The Counter Adversary Operations team uncovers unique and emerging threats, helping organizations stay ahead of attackers by providing groundbreaking research that fuels proactive defenses.
- Tailored reports: Custom intelligence reports tailored to an organization’s specific needs and threats, empowering businesses to make informed decisions that improve their overall security posture.
Falcon Adversary Intelligence Premium includes all capabilities provided by CrowdStrike Falcon® Adversary Intelligence
Key benefits of CrowdStrike threat intelligence tools:
- Automated investigations: Reduce manual effort by automating threat detection and investigation processes.
- Tailored intelligence: Receive custom IOCs and insights that are relevant to the organization’s unique threat landscape.
- Faster response: With integrated tools and actionable intelligence, organizations can respond to threats quicker and more effectively.
- Expert support: Access to world-class analysts and researchers for in-depth threat analysis and strategic advice.
CrowdStrike’s intelligence modules provide a comprehensive, proactive approach to cybersecurity, empowering businesses to stay ahead of attackers and continuously strengthen their defenses.
Cyber Threat Intelligence FAQs
Q: What is cyber threat intelligence?
A: Threat intelligence refers to the collection, processing, and analysis of data to understand a threat actor’s motives, targets, and attack methods. It transforms raw data into actionable insights, enabling security teams to make informed, data-driven decisions.
Q: Why is threat intelligence important?
A: With the rise of advanced persistent threats (APTs), threat intelligence offers invaluable insight into adversaries’ tactics, techniques, and procedures (TTPs), helping defenders anticipate and preempt potential attacks.
Q: What are the three types of threat intelligence data?
A: Tactical, operational, and strategic threat intelligence.
Q: What does a cyber threat intelligence analyst do?
A: Dig deeper for signs of intrusions and review threat actor reports to improve detection capabilities.