Overview of Detecting and Preventing Lateral Movement
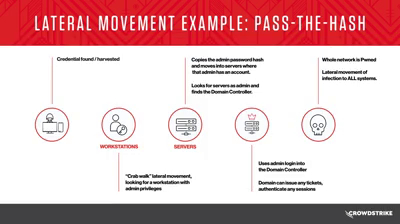
80% of all breaches involve identity-based attacks with lateral movement based on compromised credentials. Lateral movement is a common technique in scenarios from ransomware to supply chain attacks. We will show how deterministic and behavioral detection techniques can identify lateral movement to enable zero trust security in real-time, with fewer false positives, and a better user experience.
Discover More at our
Resource Center
TECHNICAL CENTER
For technical information on installation, policy configuration and more, please visit the CrowdStrike Tech Center.
Visit the Tech Center