What is a Botnet?
A botnet is a network of computers infected with malware that are controlled by a bot herder. The bot herder is the person who operates the botnet infrastructure and uses the compromised computers to launch attacks designed to crash a target’s network, inject malware, harvest credentials or execute CPU-intensive tasks. Each individual device within the botnet network is called a bot.
How are Botnets Controlled?
Bot herders control their botnets through one of two structures: a centralized model with direct communication between the bot herder and each computer, and a decentralized system with multiple links between all the infected botnet devices.
Centralized, Client-Server Model
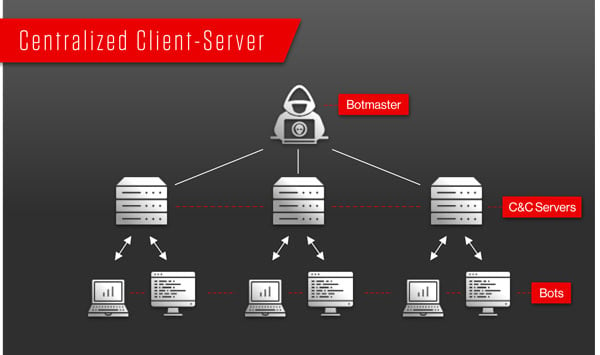
The first generation of botnets operated on a client-server architecture, where one command-and-control (C&C) server operates the entire botnet. Due to its simplicity, the disadvantage of using a centralized model over a P2P model is that it is susceptible to a single point of failure.
The two most common C&C communication channels are IRC and HTTP:
IRC (Internet Relay Chat) botnet
IRC botnets are among the earliest types of botnet and are controlled remotely with a pre-configured IRC server and channel. The bots connect to the IRC server and await the bot herder’s commands.
HTTP botnet
An HTTP botnet is a web-based botnet through which the bot herder uses the HTTP protocol to send commands. Bots will periodically visit the server to get updates and new commands. Using HTTP protocol allows the herder to mask their activities as normal web traffic.
Decentralized, Peer-to-Peer Model
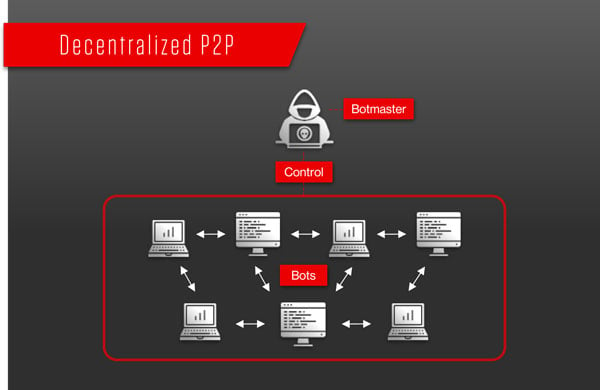
The new generation of botnets are peer-to-peer, where bots share commands and information with each other and are not in direct contact with the C&C server.
P2P botnets are harder to implement than IRC or HTTP botnets, but are also more resilient because they do not rely on one centralized server. Instead, each bot works independently as both a client and a server, updating and sharing information in a coordinated manner between devices in the botnet.
How Does a Botnet Work?
The stages of creating a botnet can be simplified into these steps:
- Expose
- Infect and Grow
- Activate
In stage 1, the hacker will find a vulnerability in either a website, application, or user behavior in order to expose users to malware. A bot herder intends for users to remain unaware of their exposure and eventual malware infection. They may exploit security issues in software or websites so that they can deliver malware through emails, drive-by downloads, or trojan horse downloads.
In stage 2, victims’ devices are infected with malware that can take control of their devices. The initial malware infection allows hackers to create zombie devices using techniques like web downloads, exploit kits, popup ads, and email attachments. If it’s a centralized botnet, the herder will direct the infected device to a C&C server. If it’s a P2P botnet, peer propagation begins and the zombie devices seek to connect with other infected devices.
In stage 3, when the bot herder has infected a sufficient amount of bots, they can then mobilize their attacks. The zombie devices will then download the latest update from the C&C channel to receive its order. The bot then proceeds with its orders and engages in malicious activities. The bot herder can continue to remotely manage and grow their botnet to carry out various malicious activities. Botnets do not target specific individuals since the bot herder’s goal is to infect as many devices as possible so they can carry out malicious attacks.
Types of Botnet Attacks
Once an adversary is in control of a botnet, the malicious possibilities are extensive. A botnet can be used to conduct many types of attacks, including:
1. Phishing
Botnets can be used to distribute malware via phishing emails. Because botnets are automated and consist of many bots, shutting down a phishing campaign is like playing a game of Whack-A-Mole.
2. Distributed Denial-of-Service (DDoS) attack
During a DDoS attack, the botnet sends an overwhelming number of requests to a targeted server or application, causing it to crash. Network layer DDoS attacks use SYN floods, UDP floods, DNS amplification, and other techniques designed to eat up the target’s bandwidth and prevent legitimate requests from being served. Application-layer DDoS attacks use HTTP floods, Slowloris or RUDY attacks, zero-day attacks and other attacks that target vulnerabilities in an operating system, application or protocol in order to crash a particular application.
Many will remember the massive Mirai botnet DDoS attack. Mirai is an IoT botnet made up of hundreds of thousands of compromised IoT devices, which in 2016, took down services like OVH, DYN, and Krebs on Security.
3. Spambots
Spambots harvest emails from websites, forums, guestbooks, chat rooms and anyplace else users enter their email addresses. Once acquired, the emails are used to create accounts and send spam messages. Over 80 percent of spam is thought to come from botnets.
How to Protect Against Botnets
To prevent your devices from becoming part of a botnet, we recommend your organization consider the following recommendations:
- A regular security awareness training program that teaches users/employees to identify malicious links.
- Always keep your software updated to decrease the chances of a botnet attack exploiting weaknesses in the system.
- Use two-factor authentication to prevent botnet malware from breaking into devices and accounts if a password has been compromised.
- Update passwords across all devices, especially the privacy and security options on those that connect device-to-device or to the internet.
- A quality antivirus solution that is kept up to date and scans the network regularly.
- Deploy an intrusion detection system (IDS) across your network.
- An endpoint protection solution that includes rootkit detection capability and that can detect and block malicious network traffic.







