Cloud Detection and Response: 5 Key Take-Aways
A Unified CDR Platform integrates CWP, CSPM, CIEM, and ASPM into one cloud-native platform for threat detection, response, and adversary intelligence.
CDR enables real-time threat management including immediate threat detection, mitigation, and swift cloud workload protection via real‑time response.
24/7 Expert Services combine proactive threat hunting, incident response, and managed services to minimize cloud security gaps.
Enhanced Cloud Visibility offers deep visibility into scalable, ephemeral cloud assets, reducing alert fatigue and improving risk prioritization.
CDR is Adaptive for Cloud Complexity, built to address alert overload, integration challenges, and the dynamic nature of cloud environments..
What is CDR (Cloud Detection and Response)?
The cybersecurity landscape is evolving rapidly. Part of this evolution is driven by businesses increasingly shifting their operations and data to the cloud. What are the implications for organizations that need to protect their digital assets? Many enterprises are strategically pivoting their security approach to integrate cloud detection and response (CDR) — in conjunction with expert incident response and breach recovery services — to address the unique challenges posed by cloud environments.
As businesses leverage cloud services for their flexibility and scalability, the complexity of securing these environments grows. CDR can meet the challenges of this complexity. In this post, we’ll look at what CDR is, why it’s essential, and how it fits within the broader context of cybersecurity technologies.
Before we dive into CDR, let’s briefly review the top behaviors of adversaries lurking in the cloud today.

The Complete Guide to CNAPPs
Download CrowdStrike's Complete Guide to CNAPPs to understand why Cloud-Native Application Protection Platforms are a critical component of modern cloud security strategies and how to best integrate them to development lifecycles.
Download NowCommon cloud adversary TTPs
Adversaries use a range of tactics, techniques and procedures to target cloud environments. Below are some of the common TTPs used to target the cloud.
- Initial access: Threat actors often use credentials from legitimate accounts, reset passwords, or exploit public-facing applications to gain initial cloud access. From there, they seek further access via credentials in files or through instance metadata services from cloud providers.
- Discovery: Attackers examine cloud accounts, seeking long-term latent access, privilege escalation, and reachable network services. They also search for permission groups, infrastructure, and storage buckets.
- Privilege escalation: By accessing accounts with higher privileges, attackers can gain more access to cloud resources.
- Lateral movement: Leveraging SSH, Remote Desktop Protocol (RDP), or Server Message Block (SMB) protocols, attackers move laterally within a cloud environment. They may also look to cloud orchestration tools to aid them.
- Defense evasion: Efforts to bypass security include disabling security products in VMs or trying to impersonate valid users by connecting via proxies geographically closer to their locations.
These behaviors underscore the need for robust defense mechanisms tailored for the cloud. This leads us to CDR and its critical role in the modern cybersecurity strategy.
Learn More
CrowdStrike has enhanced its CrowdStrike Falcon® Cloud Security capabilities to ensure organizations can protect their cloud workloads throughout the entire software development lifecycle and effectively combat adversaries targeting the cloud. Learn more!
CDR components and use cases
CDR is a security approach specifically designed for cloud environments that focuses on threat detection, immediate incident response, and service integrations. It aims to ensure comprehensive security coverage that is tailored to the unique aspects of cloud computing, such as scalability, data sovereignty, and innovation.
Key components of CDR include:
- Complete unified CNAPP: combines technologies such as CWP, CSPM, CIEM and ASPM into a single solution
- Proactive services: including threat hunting, incident response, proactive security services
- Adversary intelligence: up-to-date intelligence on the latest behaviors / TTPs of adversaries.
Traditional point security solutions aren’t equipped to fully handle the dynamic nature of the cloud, with its rapid scalability, ephemeral resources, and global distribution of services and data. CDR offers a more adaptable and integrated approach. It's crafted to handle the cloud's fluidity, leveraging real-time data and cloud-native threat hunting capabilities to protect your digital assets.
CDR solutions' capabilities make them a vital tool for securing cloud environments, offering a specialized approach that traditional point solutions can't match. However, implementing CDR comes with its own set of challenges:
- Integration complexities when working with existing security tools and cloud services
- Alert management and prioritization to avoid alert fatigue and ensure that critical threats are addressed promptly
Because of these challenges, CDR is most effective when it is part of a larger, unified cybersecurity platform that integrates capabilities for prevention, detection, and rapid response. Couple this with adversary-based threat intelligence and 24/7 services from a team of cybersecurity experts, and the result is a CDR approach that ensures the protection of your cloud environments.
The benefits of Cloud Detection and Response
CDR can be transformative for an organization’s cloud security, vastly enhancing its ability to deal with cloud-based threats.
- Reduce cloud risks by proactively identifying and mitigating vulnerabilities
- Stop cloud breaches by preventing unauthorized access and subsequent data exfiltration
- Enhance visibility into cloud environments
- Respond faster with quicker threat detection and mitigation
- Minimize the blast radius of an incident due to swift detection and response
- Employ scalable security measures that adapt to the changing scale of cloud resources for consistent protection

Navigating the Clouds: A Comprehensive Guide to Cloud Detection and Response
Download this guide to learn how to proactively manage defenses against sophisticated threats in today’s dynamic cloud environment.
Download NowLearn More
Learn how CrowdStrike combines cloud scale with machine learning expertise to improve the efficacy of our machine learning models.
Blog: How CrowdStrike's ML Model Automation Uses the Cloud to Maximize Detection Efficacy
Key Cloud Detection and Response capabilities
The key CDR capabilities of CrowdStrike Falcon® Cloud Security are:
- Real-time, context-rich threat detection — Falcon Cloud Security employs sophisticated algorithms and analyzes cloud behaviors and configurations to identify malicious activities as they happen.
- Clear prioritization of vulnerabilities based on exposure risk and breadth of potential impact, showing organizations how to assign resources for mitigation efforts.
- Continuous security monitoring to keep a watchful eye on cloud environments, constantly looking for any signs of compromise.
- Automated response and remediation to streamline the prioritization, containment, and neutralization of threats, minimizing manual intervention and remediation time.
- Integration of threat intelligence through advanced analytics, helping organizations anticipate and counter threats and make intelligent decisions with native context on 230+ adversaries and their tradecraft.
- 24/7 threat hunting, automated investigations, and expert insights to enable organizations to outpace the adversary.
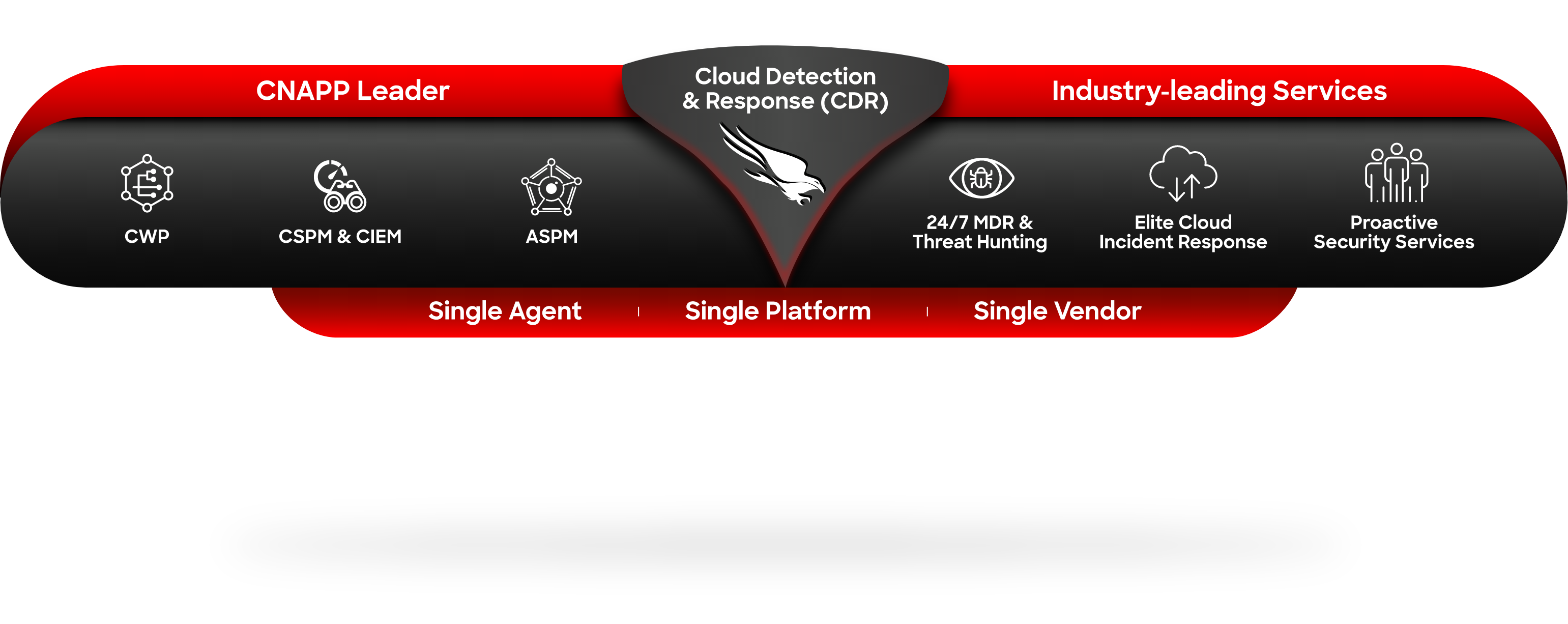
Protect your entire cloud with CrowdStrike
CDR solutions have emerged as an indispensable tool in the cybersecurity arsenal — especially as cloud adoption accelerates. They address the cloud threat landscape and empower organizations to respond swiftly and effectively.
CrowdStrike offers the only CDR solution that unifies world-class threat intelligence and elite 24/7 services with a complete cloud security platform. Coupled with proactive threat hunting and AI-native adversary intelligence, Falcon Cloud Security ensures your cloud security stays ahead of malicious attackers. CrowdStrike Falcon® Next-Gen SIEM and CrowdStrike Falcon® Fusion SOAR help organizations seamlessly integrate log aggregation, monitoring, and security automation into their broader security and strategy.
Finally, enterprises also lean on CrowdStrike Falcon Adversary OverWatch and incident response services to help accelerate cloud incident investigations with a team of cybersecurity experts. CrowdStrike ensures that your cloud is protected in every way — from proactive vulnerability management to rapid threat response — providing a seamless security experience across your entire digital landscape.
To learn more about CrowdStrike, contact our team today. Have you experienced a breach? If so, reach out to the CrowdStrike Services team immediately.
Cloud Detection and Response (CDR) FAQs
Q: What is cloud detection and response?
A: Cloud Detection and Response (CDR) is a security solution that provides real-time threat detection, analysis, and response in cloud environments. It enables organizations to identify and mitigate cyber threats before they cause damage.
Q: What is CDR cloud security?
A: CDR cloud security involves monitoring cloud workloads, analyzing security events, and responding to potential cyber threats using automation and artificial intelligence. It helps protect cloud infrastructure, applications, and data.
Q: How does CDR work?
A: CDR works by continuously collecting and analyzing security data from cloud services, identifying anomalies, and triggering automated responses to neutralize threats. It integrates with cloud-native security tools for comprehensive protection.
Q: What is the difference between EDR and CDR?
A: EDR continuously monitors individual devices—like laptops and desktops—to detect and respond to threats at the endpoint level. In contrast, CDR is tailored for cloud environments, focusing on the unique risks associated with cloud workloads, applications, and configurations. Both are critical in cybersecurity, each optimized for their respective environments.
Q: What is threat detection and response in cloud?
A: Key features of a CDR solution include real-time monitoring, AI-driven threat detection, automated incident response, cloud-native integrations, and compliance management.



