What is next-generation antivirus (NGAV)?
Next-Generation Antivirus (NGAV) uses a combination of artificial intelligence, behavioral detection, machine learning algorithms, and exploit mitigation, so known and unknown threats can be anticipated and immediately prevented. NGAV is cloud-based, which allows it to be deployed in hours instead of months, and the burden of maintaining software, managing infrastructure, and updating signature databases is eliminated.
NGAV is the next step in endpoint protection, using a signature-less approach to deliver more complete and effective endpoint security than is possible with legacy AV.

Modern Adversaries and Evasion Techniques
86% of eCrime actors us evasion techniques to bypass AV software. Learn how legacy antivirus is an easy target for adversaries and techniques they use that legacy AV can't stop.
Download NowNext-gen AV vs. legacy AV
|
|
| |
|---|---|---|
| Detection of Unknown Threats |
|
|
| Impact on the Endpoint |
|
|
| Time-to-value |
|
|
Detecting known/unknown threats
Legacy AV uses strings of characters called signatures that are associated with specific types of malware to detect and prevent further attacks of similar types. This approach is becoming obsolete as sophisticated attackers have found ways around legacy AV defenses, such as by leveraging fileless attacks that use macros, scripting engines, in-memory, execution, etc., to launch attacks.
Legacy AV leaves organizations locked into a reactive mode, only able to defend against known malware and viruses catalogued in the AV provider’s database. That approach was the best available in the past, but today, when unknown threats need to be addressed with the same rigor as known threats, it is sorely inadequate. In a Ponemon survey, 80 percent of respondents who had been compromised say the attack was a new or unknown zero-day attack. Only 19 percent of compromised respondents identified a known threat as the source.
NGAV eliminates these shortcomings as the integration of more sophisticated prevention methods – such as machine learning, behavioral detection, and artificial intelligence – eliminates the sole reliance on signatures to detect malicious activity. NGAV protects against unknown threats as well as known threats, which is increasingly important as the use of fileless attacks rises among attackers. NGAV enables both types of threats to be exposed in near real time, and is much more effective at helping organizations block these threats at far greater speed than in the past.
Time-to-value
Legacy AV also lags in terms of time-to-value, with the average deployment taking three months. This timeframe is necessary because legacy AV often relies on hardware to be installed at the physical premises. Moreover, once installed, most legacy solutions require quite a bit of tuning and configuration for them to be fully functional.
Deploying a true cloud-native NGAV solution, however, is nowhere near as cumbersome and can take just a few hours to fully implement. Because NGAV is based in the cloud, there is no additional hardware or software to procure, no infrastructure to deploy, no need to architect a new solution, and the pain of ongoing maintenance and signature updates is eliminated.
Impact on the endpoint
Once up and running, the footprint of legacy AV on the endpoint can be significant due to the inefficient addition of security capabilities overtime that bloat agents and negatively impact performance. Moreover, its reliance on signatures means that signature databases need to be updated constantly to include the latest additions. These updates consume a great deal of resources and time, and the moment an update is completed, it is already out of date.
NGAV solutions are designed to employ a single, lightweight agent that is unobtrusive in nature and has a minimal impact on the endpoint.
Learn More
Download our buyer's guide on endpoint protection to learn the must-have features and capabilities for a modern endpoint protection strategy.
What to look for in an NGAV solution?
An effective NGAV solution will use innovative technologies to prevent the rapidly changing tactics, techniques, and procedures (TTPs) used by adversaries to breach organizations, including commodity malware, zero-day malware and even advanced malware-free attacks. Here are the prevention capabilities to look for:
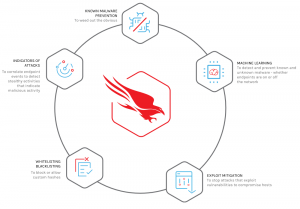
1. Prevention of known and unknown malware
a. Signature-less malware protection
Signature-less malware protection uses machine-learning algorithms to determine the likelihood that a file is malicious. New threats are stopped immediately, and time-to-value is reduced to zero.
b. Machine learning
Machine learning can detect and prevent both known and unknown malware on endpoints, whether they are on and off the network. It enables faster and more complete discovery of indicators of attack, eliminates ransomware, and fills the gaps left by legacy AV.
2. Prevention of malware-free attacks
a. Indicators of attack (IOAs)
IOAs correlate endpoint events to detect stealthy activities that indicate malicious activity. A solution that relies on retrospective offline analysis to find IOAs will not be able to keep up with emerging threats and will take a great deal of resources to manage. Online algorithms that use machine learning and do not require an entire data set to perform a useful analysis are faster, more efficient, and more effective.
b. Exploit blocking
Malware is not always delivered in a file. Attacks that use macros, execution, in-memory, and other fileless techniques are on the rise. Exploit blocking detects and blocks exploitation as it occurs.
3. Threat intelligence integration
Integrated threat intelligence enables the immediate assessment of the origins, impact, and severity of threats in the environment, and also provides guidance on how to best respond and remediate.
4. Cloud-native
Cloud architecture is the critical component in the delivery of true next-gen AV. Cloud-based NGAV can be fully operational in seconds, with no reboot, signature updates, configuration, or infrastructure purchases required. Algorithms can process endpoint activity as it occurs, exposing malicious files and suspicious behaviors in near real time with no impact on endpoint performance.
How NGAV works
NGAV uses new technologies to protect endpoints in a way that is fundamentally different from traditional AV. By using machine learning algorithms on a cloud-based architecture, NGAV can stop the rapidly-evolving threats that are typical today.
Here’s how it works:
1. Single lightweight agent
Cloud-based architecture and a single lightweight agent create virtually no impact on the endpoint. Performance doesn’t have to suffer for the sake of security.
2. State-of-the-art prevention capabilities
A true next-generation antivirus should use sophisticated prevention tools and methods that will not only block malware, but also stop malware-less attacks, regardless of the tactics, techniques, and procedures (TTPs) used by attackers. Some of these methods and tools include machine learning, exploit blocking, custom whitelisting and blacklisting, behavioral indicators of attack (IOAs), attack attribution and adware blocking.
3. No need for signature updates
Machine learning can help employ sophisticated algorithms to analytics millions of file characteristics in real time to determine if a file is malicious. Signatureless technology enables NGAV solutions like CrowdStrike Falcon® to detect and block both known and unknown malware, even when the endpoint is not connected to the cloud.
4. Online and offline prevention
The CrowdStrike Falcon® intelligent agent offers prevention whether online or offline and supports data processing and decision-making on the endpoint. This not only enables highly accurate detection and prevention, it keeps the endpoint protected everywhere, online or off.
5. Immediate time-to-value
NGAV solutions should be deployed and operational in hours, with no additional hardware or software and no tuning or configuration. Customers report the installation of as many as 70,000 agents in a single day.
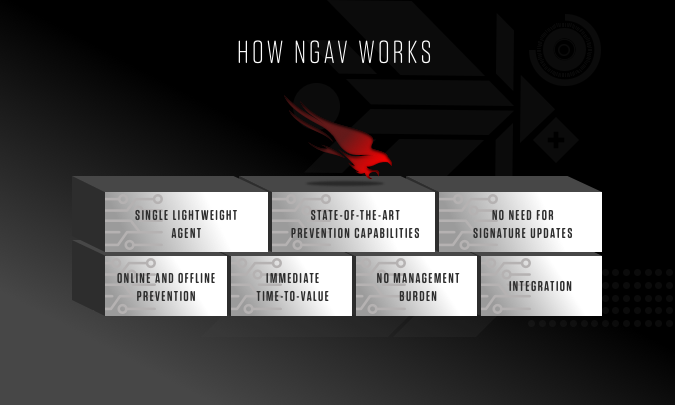
6. No management burden
NGAV solutions are designed to integrate seamlessly into environments without adding complexity. It requires no on-premises management infrastructure.
7. Integration
NGAV solutions easily integrate with existing SIEMs. CrowdStrike's Falcon Sensor pulls in events collected from endpoints and Falcon APIs integrate with existing third-party intelligence and indicators of compromise (IOCs), so organizations can get the most value from their entire security investment.
Replace your outdated antivirus
CrowdStrike Falcon Prevent is the new standard in prevention, delivering superior protection from malware, exploits, malware-free intrusions, and advanced persistent threats. Organizations gain an unprecedented level of visibility into attempted attacks in an easy-to-read process tree that provides the details and context necessary to understand what’s happening on the endpoint and how to remediate effectively.
Falcon Prevent has virtually no impact on endpoints, and can be fully operational across tens of thousands of endpoints within hours. Once deployed, management and maintenance are handled in the cloud, which also enables easy integration with existing SIEMs.
Learn More
Download the Falcon Prevent Data Sheet to learn about the product capabilities that safeguard organization against breaches and why our NGAV solution is an industry-recognized AV replacement.
NGAV FAQs
Q: What is next-generation antivirus (NGAV)?
A: NGAV uses a combination of artificial intelligence, behavioral detection, machine learning algorithms, and exploit mitigation, so known and unknown threats can be anticipated and immediately prevented.
Q: What is the difference between NGAV and AV?
A: NGAV uses new technologies to protect endpoints in a way that is fundamentally different from traditional AV. By using machine learning algorithms on a cloud-based architecture, NGAV can stop the rapidly-evolving threats that are typical today.
Q: What to look for in an NGAV solution?
A: An effective NGAV solution will use innovative technologies such as threat intelligence, IOAs, cloud computing, and machine learning to prevent the rapidly changing tactics, techniques, and procedures (TTPs) used by adversaries to breach organizations





