What are the 5 Steps of the Vulnerability Management Lifecycle
There are five main stages in the vulnerability management cycle include:
- Step 1. Assess
- Step 2. Prioritize
- Step 3. Act
- Step 4. Reassess
- Step 5. Improve

Step 1. Assess your Assets
Assessment is the first stage of the cycle. In this stage, security analysts should narrow down and define the assets to be assessed for vulnerabilities. The next step is to assess each asset for vulnerabilities, generating a report to determine which assets are at risk and need patching or further investigation and remediation.
There are two common approaches to conducting a vulnerability assessment: using a network-based solution or using an installed sensor, or “agent,”on each asset.
With a legacy, network-based solution, all endpoints are required to be on the network, and a vulnerability assessment tool queries the devices in the network and then conducts a scan. Challenges associated with network-based scans include access issues and limited visibility. If an asset is not connected to the network, the security analyst cannot see what’s at risk. And typically, with legacy, network-based solutions, credentials are required for full visibility. For many organizations, managing the level of credentialing needed to perform a successful vulnerability scan is layered and complex, which can lead to an incomplete picture of which assets are safe and which are not. Additionally, with a traditional vulnerability solution, plug-ins are often added to the tool (sometimes hundreds or thousands of components), and they don’t all “play nicely” with an organization’s existing software. This adds to the length of time it takes to scan a host, and it could even break a functioning environment.
An agent-based assessment requires the use of an installed sensor on individual assets. Today, most agent-based vulnerability scanners require the installation of bulky agents. These agents are typically so large that they weigh down an endpoint extensively, bogging down, reducing or crashing systems as it runs scans.
Due to the significant performance impact of legacy network and agent-based scanning tools, it is often necessary to scan only a portion of the environment at a time, which slows down the assessment process. By taking it slow, or segmenting systems, security teams can avoid connection hang-ups and system crashes. However, this inhibits the goal of checking for vulnerabilities on all relevant hosts in a timely manner and then resolving them.
After scanning, these legacy solutions provide a report — a massive, bulky document that analysts must sift through to determine the right areas to target for remediation. Another challenge with this type of scan and its reporting method is again timeliness. As soon as a report is generated, it’s outdated. New vulnerabilities can then go by undetected for months or longer.
Today, thanks to cloud technologies and a lightweight agent architecture, modern vulnerability management tools (such as Falcon Spotlight™, a vulnerability management solution that’s part of the CrowdStrike Falcon® platform) are able to run continuously. It serves as a scanless solution, allowing a vulnerability management team to see a variety of vulnerabilities immediately because data is housed in the cloud and therefore always available. Because the data is available in real time, scanning is an ongoing, continuous process rather than a single point in time.
Once an assessment has been completed for all assets, the next stage is prioritizing vulnerabilities. (For potential solutions, jump to “Vulnerability Management Solutions: What to Look For.”)
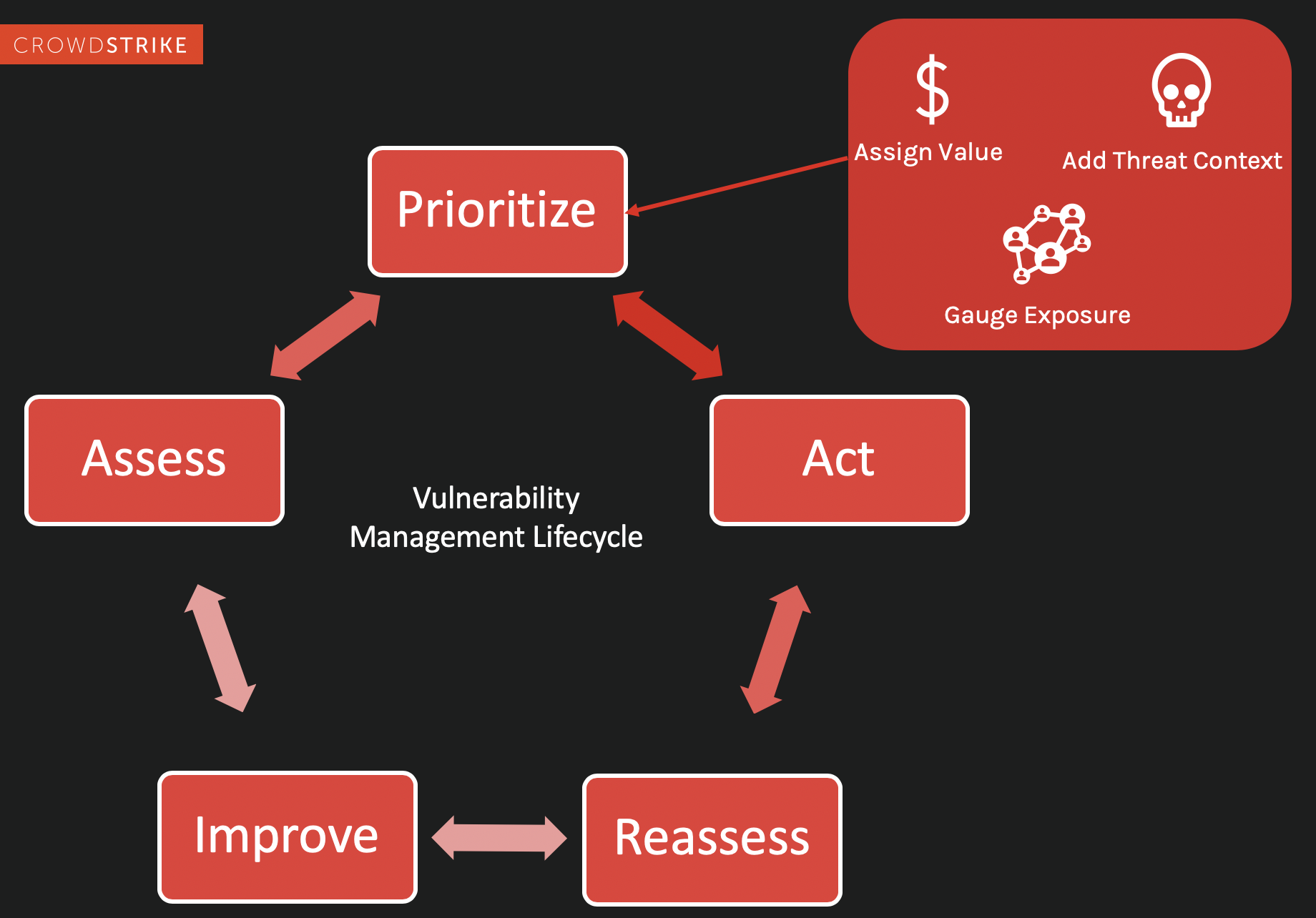
Step 2. Prioritize Vulnerabilities
Once you have gathered data on which assets and systems are potentially weakened or exposed, the real work begins. In this stage of the cycle, the VM team takes three steps to determine the actions of the next stage.
1. Assign value. This is where your pre-work becomes valuable. Since you have already identified which assets are critical, it should be relatively easy to prioritize each asset for investigation.
2.With your prioritized list of assets, you need to gauge the threat exposure of each asset. This requires some investigation and research to determine the level of risk for each one.
3.Add threat context to your report. Communicating with your greater security operations team and using a powerful set of endpoint security tools are invaluable. A deep dive into threat intelligence (both internally gathered and from third-party sources) can dramatically change the level of risk assessed and prioritized in Steps 1 and 2.
Expert Tip
The CrowdStrike Falcon® platform offers a comprehensive solution to view and assess vulnerabilities via Falcon Spotlight. In addition to vulnerability assessment CrowdStrike Falcon® Intelligence offers the industry’s only solution that integrates threat intelligence data within the platform. The data is constantly updated by CrowdStrike’s world-class threat hunters, researchers and intelligence experts, who provide highly actionable information about nation-state actors, e-criminal organizations, hacktivist groups and other adversaries, along with their malicious activity, targeted attacks and targeted industries. They connect this information to specific CVEs, providing organizations with immediate data on how to best protect themselves.
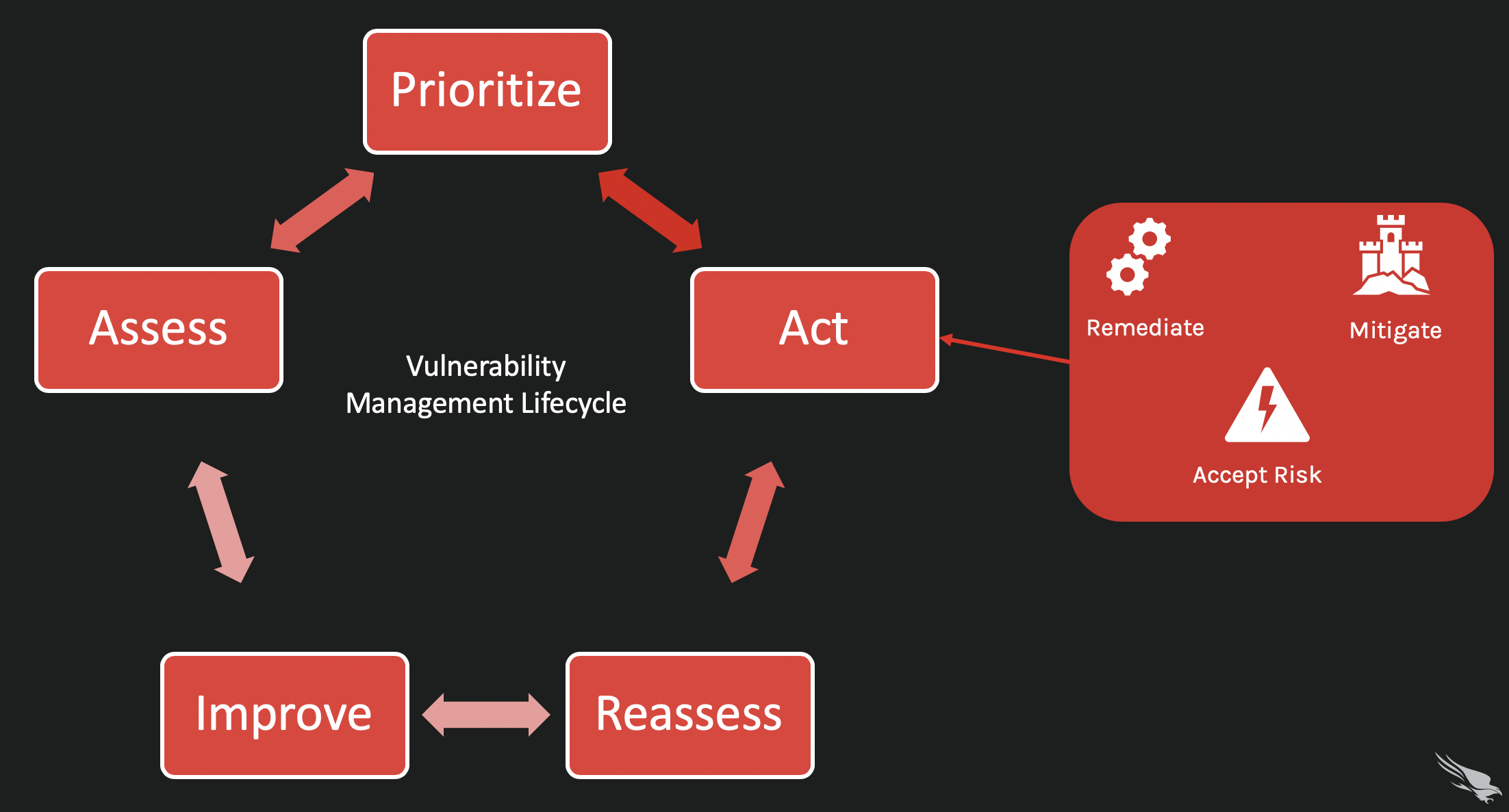
Step 3. Act
What do you do with the information gathered in the prioritization stage? There are three options:
- You can accept the risk of the vulnerable asset to your system. This is a likely option for non-critical assets or systems, and the threat of exposure is very low.
- You can mitigate the vulnerability, or you can develop a strategy or technique to make it difficult or impossible for an attacker to exploit the vulnerability. This doesn’t remove the vulnerability, but the policies or protections you put in place keep your systems safe.
- You can completely remediation the vulnerability. This is the preferred option if the vulnerability is known to be high risk and/or is part of a critical system or asset in your organization. Patch or upgrade the asset before it becomes an entry point for an attack.
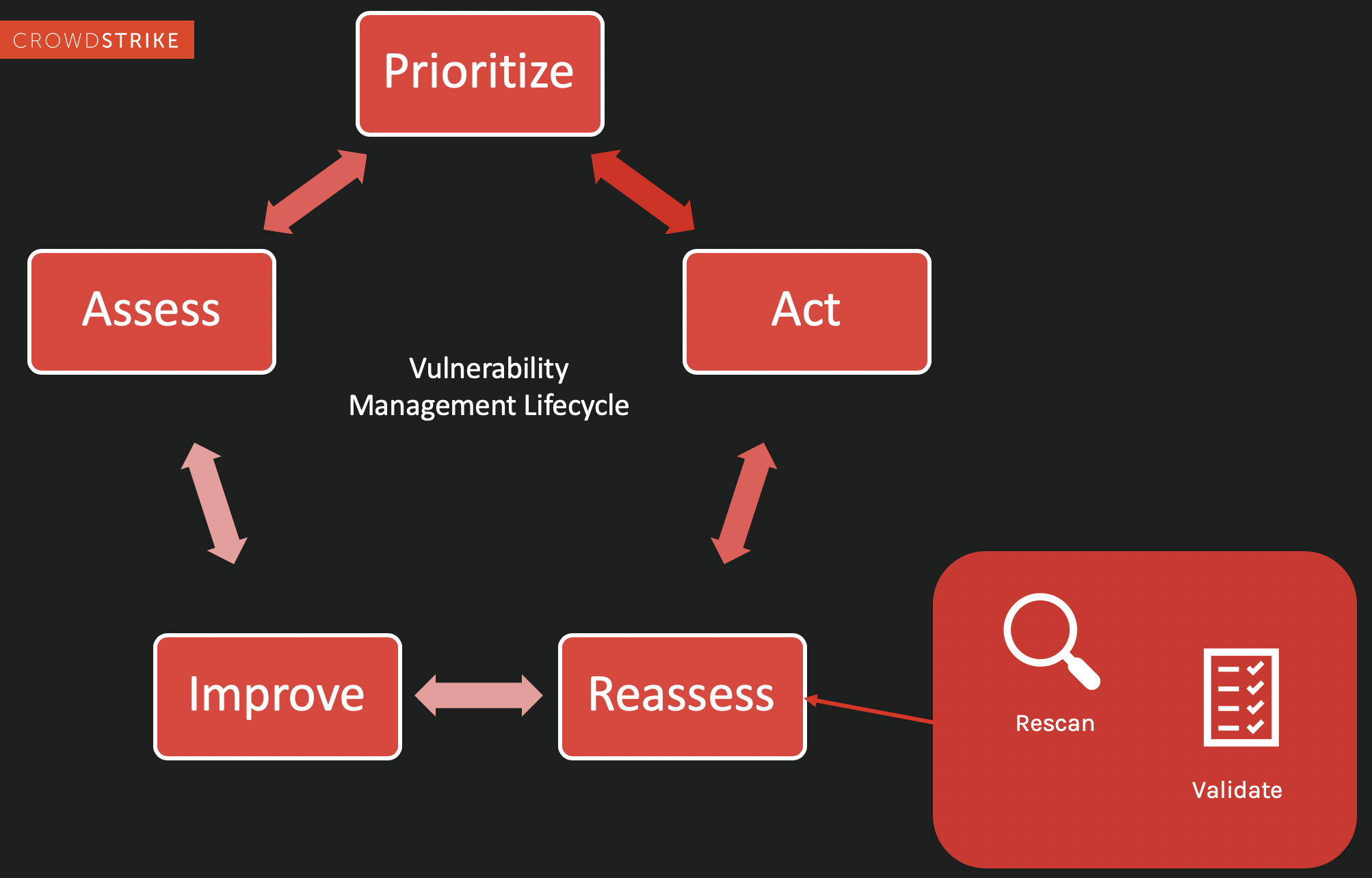
Step 4. Reassess
Once you have prioritized your vulnerability list and assigned actions based on the level of exposure, it’s time to reassess and check your work. A reassessment will tell you whether the actions you’ve decided on have been successful and if there are new issues around the same assets, allowing you to validate your work, cross those issues off your list and add new ones, if needed. The reassessment stage is also useful for reporting metrics of your team’s ongoing efforts to upper management.
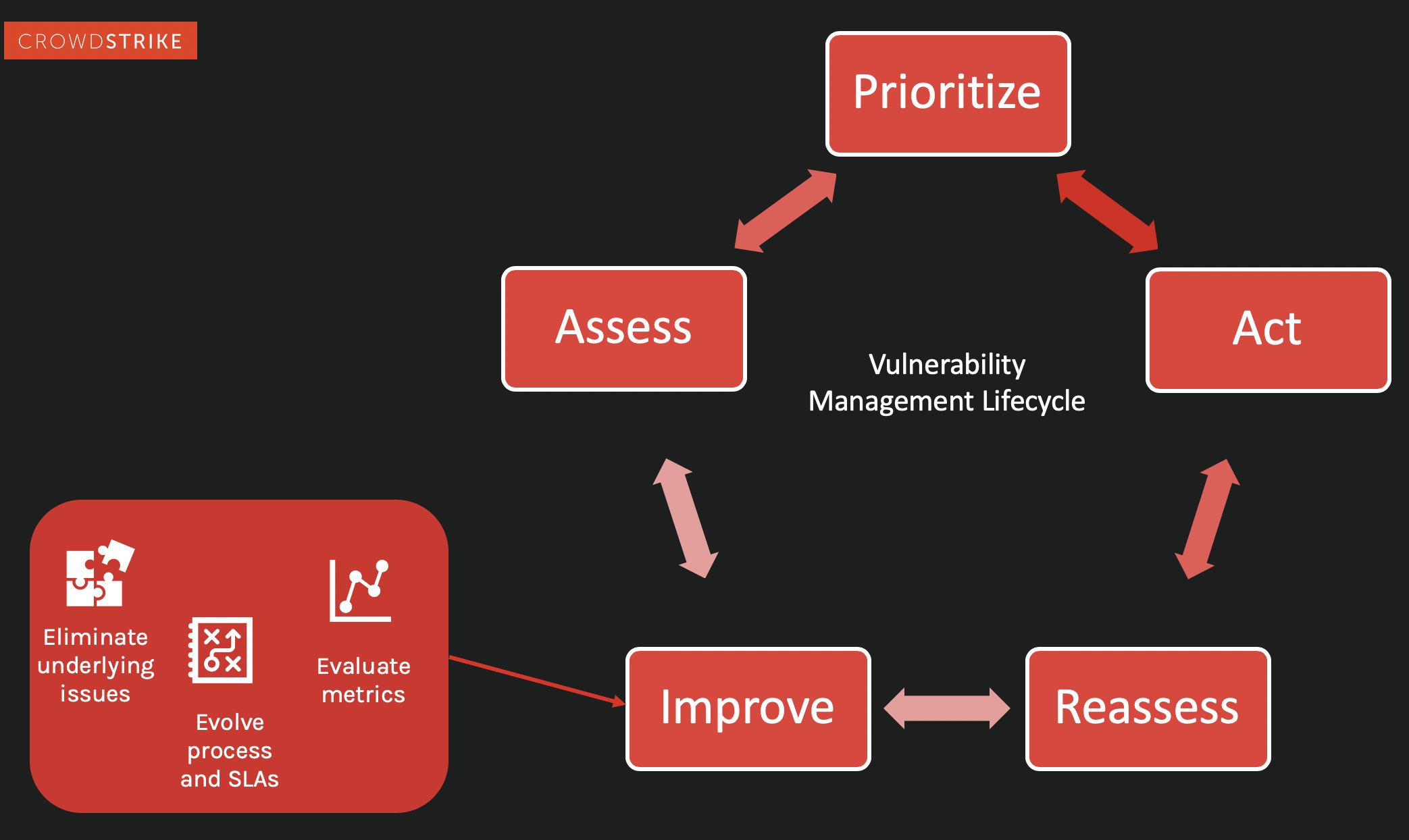
Step 5. Improve
This is the final stage of the vulnerability management cycle. The best vulnerability management programs aim for consistent improvement, shoring up weak defenses, actively working to eliminate underlying issues, reevaluating the pre-work phase and revisiting those first pre-work questions. By regularly examining the entire vulnerability lifecycle and looking for ways to evolve and improve, you can proactively defend against any kind of vulnerability an attacker could use to threaten your organization.

Falcon Spotlight Data Sheet
Download the Falcon Spotlight Data Sheet to learn CrowdStrike's approach to vulnerability management.
Download Now




