What is Ransomware as a Service (RaaS)?
Ransomware as a Service (RaaS) is a business model between ransomware operators and affiliates in which affiliates pay to launch ransomware attacks developed by operators. Think of ransomware as a service as a variation of software as a service (SaaS) business model.
RaaS kits allow affiliates lacking the skill or time to develop their own ransomware variant to be up and running quickly and affordably. They are easy to find on the dark web, where they are advertised in the same way that goods are advertised on the legitimate web.
A RaaS kit may include 24/7 support, bundled offers, user reviews, forums and other features identical to those offered by legitimate SaaS providers. The price of RaaS kits ranges from $40 per month to several thousand dollars – trivial amounts, considering that the average ransom demand in 2021 was $6 million. A threat actor doesn’t need every attack to be successful in order to become rich.
How the RaaS Model Works
The table below outlines the roles operators and affiliates play in the RaaS model:
| RaaS Operators | RaaS Affiliates |
|---|---|
| Recruits affiliates on forums | Pays to use the ransomware Agrees on a service fee per collected ransom |
| Gives affiliates access to a “build your own ransomware package” panel Creates a dedicated “Command and Control” dashboard for the affiliate to track the package | Targets victims Sets ransom demands Configures post-compromise user messages |
| Compromises the victim’s assets Maximizes the infection using “living off the land” techniques Executes ransomware | |
| Sets up a victim payment portal “Assists” affiliates with victim negotiations | Communicates with the victim via chat portals or other communication channels |
| Manages a dedicated leak site | Manages decryption keys |
There are 4 common RaaS revenue models:
1. Monthly subscription for a flat fee
2. Affiliate programs, which are the same as a monthly fee model but with a percent of the profits (typically 20-30%) going to the ransomware developer
3. One-time license fee with no profit sharing
4. Pure profit sharing
The most sophisticated RaaS operators offer portals that let their subscribers see the status of infections, total payments, total files encrypted and other information about their targets. An affiliate can simply log into the RaaS portal, create an account, pay with Bitcoin, enters detailson the type of malware they wish to create and click the submit button. Subscribers may have access to support, communities, documentation, feature updates, and other benefits identical to those received by subscribers to legitimate SaaS products.
The RaaS market is competitive. In addition to RaaS portals, RaaS operators run marketing campaigns and have websites that look exactly like your own company’s campaigns and websites. They have videos, white papers, and are active on Twitter. RaaS is business, and it’s big business: total ransomware revenues in 2020 were around $20 billion, up from $11.5 billion the previous year.
Some well-known examples of RaaS kits include Locky, Goliath, Shark, Stampado, Encryptor and Jokeroo, but there are many others and RaaS operators regularly disappear, reorganize and re-emerge with newer and better ransomware variants.
Examples of RaaS
Hive
Hive is a RaaS group that became popular on April 2022, when they targeted a large number of Microsoft’s Exchange Server customers using a pass-the-hast technique. Organizations included financial firms, non-profits, healthcare organizations, among many more. On January 26, 2023, the Department of Justice of the United States announced they disrupted Hive operations by seizing two back-end servers belonging to the group in Los Angeles, CA. It is estimated that Hive left behind over 1,500 victims worldwide and millions of dollars extorted as ransom payments.
DarkSide
DarkSide is a RaaS operation associated with an eCrime group tracked by CrowdStrike as CARBON SPIDER. DarkSide operators traditionally focused on Windows machines and have recently expanded to Linux, targeting enterprise environments running unpatched VMware ESXi hypervisors or stealing vCenter credentials. On May 10, the FBI publicly indicated the Colonial Pipeline incident involved the DarkSide ransomware. It was later reported Colonial Pipeline had approximately 100GB of data stolen from their network, and the organization allegedly paid almost $5 million USD to a DarkSide affiliate.
REvil
REvil, also known as Sodinokibi, was identified as the ransomware behind one of the largest ransom demands on record: $10 million. It is sold by criminal group PINCHY SPIDER, which sells RaaS under the affiliate model and typically takes 40% of the profits.
Similar to TWISTED SPIDER’s initial leaks, PINCHY SPIDER warns victims of the planned data leak, usually via a blog post on their DLS containing sample data as proof (see below), before releasing the bulk of the data after a given amount of time. REvil will also provide a link to the blog post within the ransom note. The link displays the leak to the affected victim prior to being exposed to the public. Upon visiting the link, a countdown timer will begin, which will cause the leak to be published once the given amount of time has elapsed.
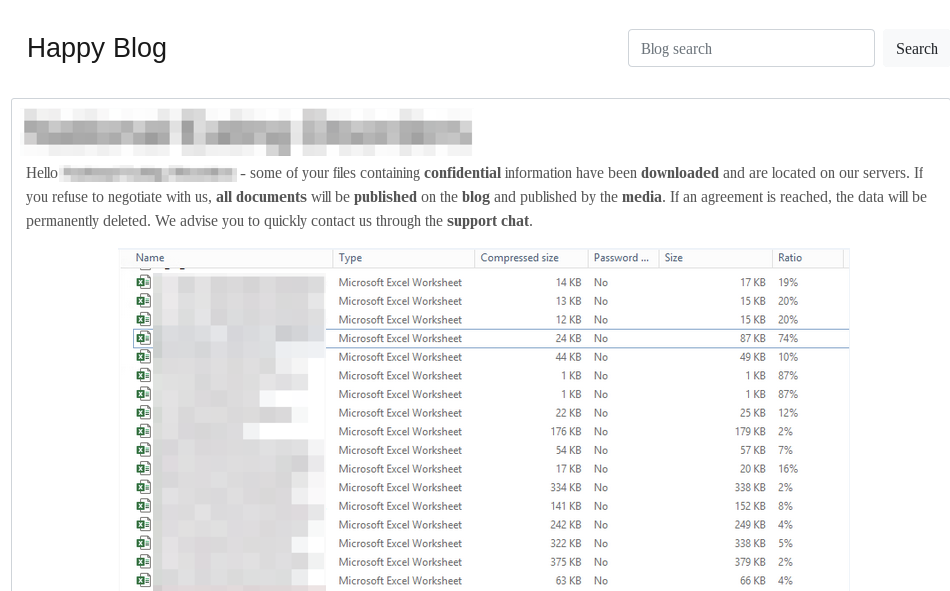
Dharma
Dharma ransomware attacks have been attributed to a financially motivated Iranian threat group. This RaaS has been available on the dark web since 2016 and is mainly associated with remote desktop protocol (RDP) attacks. Attackers usually demand 1-5 bitcoins from targets across a wide range of industries.
Dharma is not centrally controlled, unlike REvil and other RaaS kits.
Dharma variants come from many sources, and most incidents in which CrowdStrike identified Dharma revealed nearly a 100% match between sample files. The only differences were the encryption keys, contact email and a few other things that can be customized through a RaaS portal. Because Dharma attacks are nearly identical, threat hunters are not able to use an incident to learn much about who is behind a Dharma attack and how they operate.
LockBit
In development since at least September 2019, LockBit is available as a RaaS, advertised to Russian-speaking users or English speakers with a Russian-speaking guarantor. In May 2020, an affiliate operating LockBit posted a threat to leak data on a popular Russian-language criminal forum:
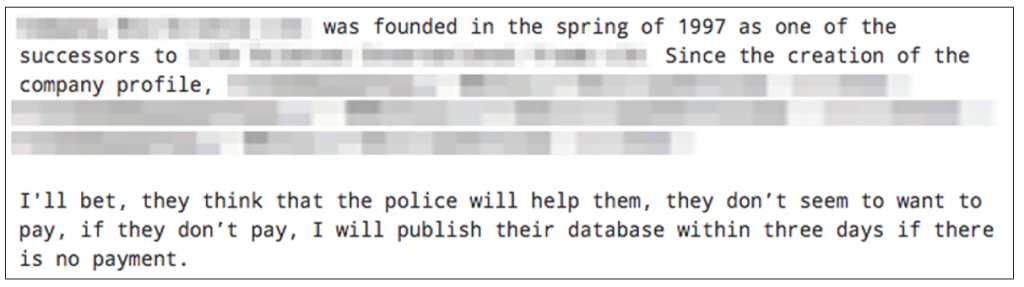
In addition to the threat, the affiliate provides proof, such as a screenshot of an example document contained within the victim data. Once the deadline passes, the affiliate is known to post a mega[.]nz link to download the stolen victim data. This affiliate has threatened to publish data from at least nine victims.
See CrowdStrike Falcon In Action
Learn how the ransom portal set up by CIRCUS SPIDER works and why NetWalker has proven to be such successful ransomware-as-a-service (RaaS).
Download nowPreventing RaaS Attacks
Recovery from a ransomware attack is difficult and costly, and as a result it’s best to prevent them entirely. The steps to prevent a RaaS attack are the same as preventing any ransomware attack, because RaaS is just ransomware packaged for ease of use by anyone with ill intent:
- Implement reliable and modern endpoint protection that can work on advanced algorithms and works automatically in the background around the clock.
- Perform regular and frequent backups. If a backup is only performed every weekend, a ransomware attack could cost an entire week of work product.
- Make multiple backups and store them on separate devices in different locations.
- Test backups regularly to ensure they can be retrieved.
- Maintain a rigorous patch program to protect from known and unknown vulnerabilities.
- Segment the network to hinder proliferation across the environment.
- Implement advanced anti-phishing protection.
- Invest in user training and build a culture of security.








