The Importance of Having a Ransomware Recovery Plan
A ransomware attack is a criminal intrusion of a computer system to encrypt data and demand a “ransom,” or payment, from the victim. Criminals use ransomware, a type of malware, to both lock the data and deliver the terms for access. Failure to pay the ransom often results in criminals leaking the data or permanently blocking access to the files; however, paying does not guarantee release.
What is a ransomware recovery plan?
A ransomware recovery plan is a playbook to address a ransomware attack, which includes an incident response team, communication plan, and step-by-step instructions to recover your data and address the threat. Time is of the essence during an attack and a fast response is critical to both recover your files and avoid crippling losses, both monetary and proprietary.
What are the consequences of not having a ransomware recovery plan?
When it comes to ransomware, failing to plan is planning to fail. The longer you take to respond to an attack, the more likely it is you will lose your data, business and credibility. IBM research from 2022 found:
- The average cost of a ransomware attack was $4.54 million.
- The average time to identify and contain an attack was 326 days.
- 50% of small businesses impacted by a ransomware attack were unprofitable within a month.
5 Steps for Ransomware Data Recovery
The best way to recover from a ransomware attack is to prevent it before it happens. However, in the event you’ve been breached, you need to take immediate action to recover. Your approach and effectiveness will depend on the type of ransomware, variant and the unique context of the attack. So, what are the steps to recover data after a ransomware attack?
1. Implement Your Incident Response (IR) Plan
An effective response is predicated on having a plan. Without one, you’ll be directionless and slow to recover. Your plan should outline both immediate recovery steps and long-term preemptive actions to prevent further attacks. At a minimum, it should include:
- Initial actions such as collecting log data from the compromised system to understand the attack.
- A communication plan that identifies internal stakeholders such as IT, security and legal, and external stakeholders such as law enforcement, customers and incident response companies.
- Legal requirements — 47 U.S. states have some form of data breach notice obligation.
- Outline steps to sustain or restart the business functions impacted.
- Provide steps to start an investigation, outline monitoring requirements and discuss ways to remediate the attack.
- Outline a strategic review process to conduct long-term planning and improvement for your security.
At CrowdStrike, we’re confident in our ability to respond to a ransomware attack. A traditional IR approach operates on a timeline of weeks and months. We operate in hours and days.
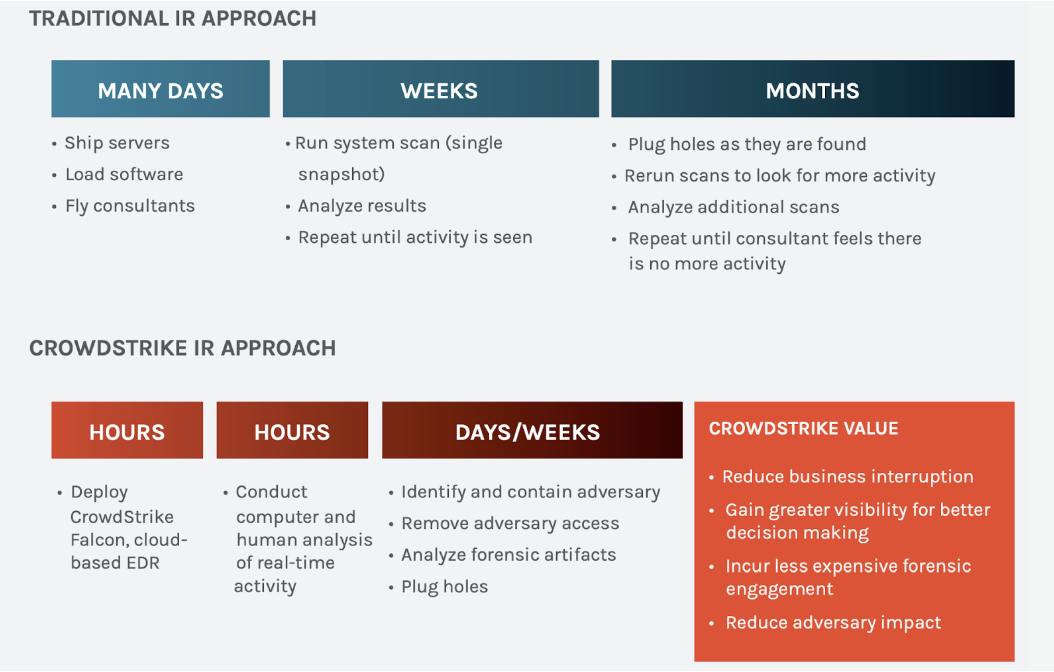
2. Determine Attack Style and Isolate Systems
Once you’ve identified an incident, it’s time to execute your IR plan:
- Pause: Victims often hastily disconnect their infected system without first understanding the nature of the attack. An attacker may have already prepared backdoors and will likely change their behavior once they’re alerted to your response. Understand the situation before you leap into action.
- Evaluate: Collect log data to understand criminal actions and review the intrusion method. Identify infected machines, the type of ransomware and how the criminals gained access.
- Isolate: Once you’ve determined the type of attack, isolate and disconnect all vulnerable and impacted systems to prevent the ransomware from spreading.
3. Back Up, Back Up, Back Up!
Without a data backup, companies are often at a complete loss when a ransomware attack occurs. This frequently leads to paying the ransom (which doesn’t guarantee file recovery). Backups are normally the quickest and most reliable way to recover. Effective methods and strategies include:
- Isolate your backups to ensure they remain safe from an attack.
- Use incremental backups to ensure there’s no data loss during an attack.
- Use storage that can’t be written over. This ensures you’ll always have a recoverable version of the impacted data.
- Implement multiple types of backups to increase your resiliency.
- Conduct regular reviews to ensure critical data and business processes are backed up in a proper location. If you need it to conduct business, back it up.
- Setup backup infrastructure to get your business up and running in minutes. While costly, a mirrored version of your primary production center, ensures your business can sustain operations even after a devastating attack.
Regardless of your method, it’s essential that you test your backups. This should be a natural part of your IR plan and security preparation. If you’ve never checked their effectiveness, you can’t be confident they’ve properly stored your data.
4. Use Data Recovery Software or Decryption Tools
As mentioned, data recovery is best conducted via backup. However, there are other ways to restore your encrypted data:
- Operating system tools: Some operating systems, like Windows 10, have built-in recovery tools. Windows System Restore utility can sometimes restore settings to a recovery point previously established. However, current ransomware can often disable and corrupt such applications.
- Data recovery software: Various third-party tools exist to both extract corrupted data from storage devices and restore the impacted files. The effectiveness of the software depends on the type of ransomware impacting your system. If it’s a new ransomware, it’s not likely software will be effective.
- Decryption tools: Depending on the ransomware variant, security researchers may have already broken the encryption algorithm. Decryption tools employ algorithms to solve the encryption and unlock your data.
5. Add Additional Security
While recovery is possible, preparation and prevention are key. Strengthening your security is the best way to avoid the devastating impacts of a ransomware breach. Some primary actions we recommend are:
- Enable two-factor authentication (aka multifactor authentication, or MFA): Remote access into your network should always require MFA. Out-of-band authentication methods such as SMS and soft tokens are commonplace, widely accepted by users and relatively easy to implement with the prevalence of smartphones.
- Change default passwords: One of the simplest attacks is to use a default password that is shipped out-of-the-box by a vendor. Internet of Things (IoT) devices are commonly highlighted for this vulnerability, but the attack scope is much broader. Default passwords, especially for hardware devices (e.g., Wi-Fi routers), can allow direct access to critical data. Extra care should be taken to require strong passwords for all users, including default or built-in accounts.
- Implement centralized logging: Robust log aggregation and retention can support a data breach investigation by assisting responders in correlating certain events and developing an incident timeline. Store log data in a protected, centralized system that is time-synchronized and easily searchable. Allocate resources to perform regular log analysis and stress-test your logging process via tabletop intrusion exercises.
- Keep a close eye on Microsoft Active Directory (AD): Attackers use AD configurations to identify attack paths and capture privileged credentials so they can deeply embed themselves into target networks. You can prevent most attacks by securing key AD components. CrowdStrike’s AD Security Assessment provides recommendations to help you secure your infrastructure.
- Implement cybersecurity training: Working through roles, responsibilities and the steps of a complete IR plan prepares your team for action and quickly identifies any weaknesses in your plan. Consider classes on threat hunting and intelligence to ensure a proactive approach to detecting intrusion attempts and activity.
CrowdStrike’s Ransomware Protection Solutions
Facing a ransomware attack is an overwhelming prospect with no easy answers. The risks can be severe. When you’re facing the worst, you want a relentless partner that works in hours and minutes, not weeks and months. CrowdStrike helps organizations of all sizes prevent and recover against ransomware attacks.
Learn More
Learn more about our CrowdStrike solutions and how they can help your organization prevent and protect from ransomware attacks.







