What is the difference between the deep web and the dark web?
“Deep web” and “dark web” are not interchangeable terms. Although the entire dark web is part of the deep web, the deep web is not a part of the dark web. Simply put, the deep web is any part of the internet that is not indexed by search engines. This includes websites that gate their content behind paywalls, password-protected websites, and even the contents of your email. The dark web, on the other hand, uses encryption software to provide even greater security.
What is the deep web?
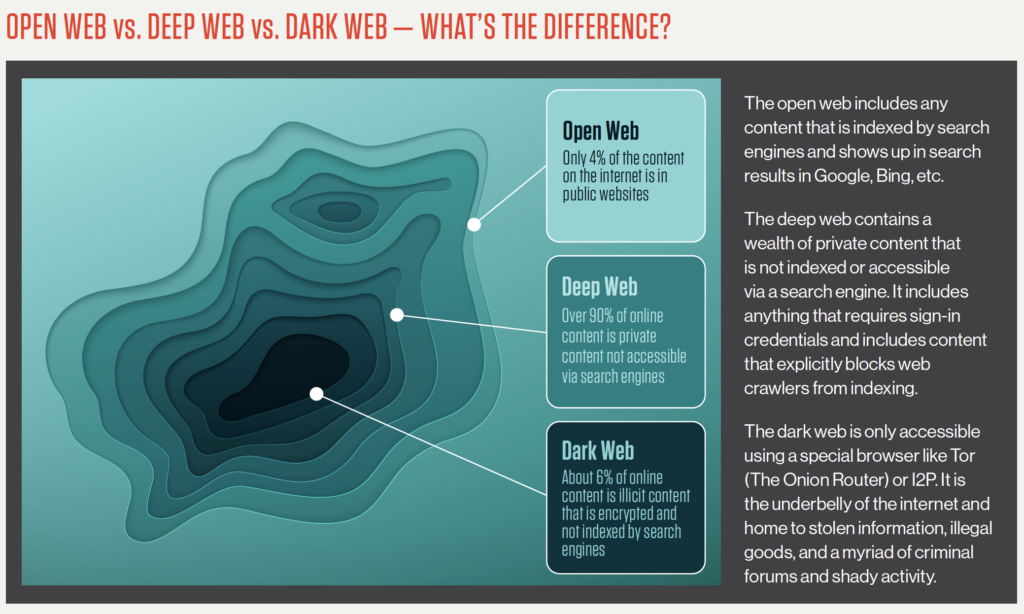
The “deep web” includes everything on the internet that is password-protected, paywalled, or even just protected from crawling by a site’s robots.txt file. Altogether, this accounts for about 90% of the content of the internet, if not more. When you log in to your favorite video streaming site or check your bank account balance online, that’s the deep web at work.
What is the dark web?
The dark web, on the other hand, makes up a tiny fraction of the internet as a whole. To access it at all, you need to use an anonymizing web browser such as “The Onion Router” (Tor) and a virtual private network (VPN). Later, we’ll delve deeper into how to access the dark web, but for now, you should just be aware that if you find yourself on a webpage and have no idea how you got there, it isn’t part of the dark web. You have to be intending to visit it.
What is the surface or open web?
The surface web, which is also called the visible web and the open web, is any website that search engines can add to their database. This includes websites, blogs, online product listings, and even public posts on social media.
Deep web vs. dark web vs. surface web
To help remember the differences between the surface web, the deep web, and the dark web, think of the differences between “public,” “private,” and “secret.”
Source: Exposing the Open, Deep, and Dark Web
The surface or open web is entirely public. The person or group who has posted a webpage on the open web doesn’t care who has access to it or what can be done with it. To use a real-world example, you probably don’t care who in a large group knows your name or the color of your hair.
The deep web, on the other hand, is private. The average person doesn’t share their private life with just anyone; they let specific people know about it when the information is needed. For example, you might tell your closest friend about a problem in your personal life, but you would not tell the clerk at your grocery store.
The dark web is secret. This is akin to the things you actively hide from other people and don’t want anyone else to learn about. They don’t have to be deep, dark secrets — not even your closest friends need to know the password to your email account, for instance.
| Deep Web Use Cases | Dark Web Use Cases |
|---|---|
| Routine Use: Users logging into routine websites such as bank accounts or social media using personal credentials do so on the deep web without realizing it. | Uncensored Journalism: Journalists use the dark web frequently (usually via the Tor Project), especially when they are working on sensitive stories or traveling to foreign countries. |
| Secure Payments: Everytime consumers pay for a product or service online, they enter payment information through the deep web. | Free Speech: Citizens of oppressive regimes (such as North Korea) use the dark web to safely organize and speak freely. The dark web was critical for protesters avoiding Net censorship during the Arab Spring after governments shut down access to social media. |
| Campaigns: Website Developers can have certain part of their websites or pages on the deep web to track campaigns, such as displaying specific homepage designs for users on specific locations | Safety: Many corporate and government whistleblowers rely on the dark web to ensure their safety. Notably, WikiLeaks has a counterpart on the dark web for exactly this reason. |
| Paid Subscriptions: Paywalls prevent search engine crawlers from accessing certain content that only users who paid for or subscribed to can access. This content, by definition, is on the deep web. | Privacy: Victims of stalking and similar online threats may use the dark web to cover their tracks as they find their way out of their situation. |
Risks of accessing the deep web vs. the dark web
The deep web and dark web have many uses, but they also come with risks. If you know anything about data privacy and protecting yourself from identity theft, it’s easy to mitigate these risks on the deep web. In fact, you probably already do it whenever you log in to a secured website. Accessing the dark web, however, is riskier.
Though the dark web may not be the monster it’s often made out to be, its very existence poses a risk to the rest of the World Wide Web. Organizations constantly face the risk of data breaches, but the existence of the dark web amplifies this risk. For instance, if a company suffers a quiet data breach, its users’ personal information will likely end up for sale on a dark web marketplace. For this reason, dark web monitoring is critical for security.
Safely accessing the deep web and dark web
In general, the rules for accessing the deep web and the dark web safely are similar to the best practices for accessing the surface web. However, you cannot simply browse to sites on the dark web — you have to take steps to ensure privacy first.
How to access the deep web safely
As previously mentioned, more than 90% of the traffic on the internet is already on the deep web, so the keys to accessing it safely are virtually the same as the keys to accessing the open web safely. Assess every website you visit for threats and security holes. Though you don’t have to perform a penetration test on every website you log in to, you should ensure that it runs on a secure framework that uses HTTPS encryption.
Once you’ve accessed deep web websites running a secure framework, take the following best practices to mitigate risk:
Have strong and unique credentials. Having a strong password can make it hard for attackers to gain access to your private information. Change the generic password provided by the company if applicable.
Maintain good IT hygiene. Only access the deep web using networks you know and trust, especially when submitting payments and other sensitive information like Social Security numbers.
- Adopt cybersecurity training. The best way a company can protect its information is by ensuring all stakeholders within the organization are aware of — and comply with — all cybersecurity policies. This includes providing instructions and best practices when accessing the deep web.
How to access the dark web safely
To browse the dark web, you need to take preemptive steps toward anonymity. In particular, you will need a VPN connection and a secure web browser (such as the Tor browser). Depending on your needs, you may want to use your VPN to download the secure browser of your choice.
Once you’ve downloaded your chosen security software, take the following steps to access the dark web:
Activate your VPN first. Make sure that you’ve disabled any unnecessary software, especially programs such as browser add-ons. (In general, the only browser add-ons that you need to access the dark web come preinstalled with most secure browsers.)
Open your secure browser and make sure it is fully updated. For the greatest level of security, avoid changing the size of your browser window.
- Navigate to the dark web website that you want to access. Instead of a regular top-level domain, it will have a domain name ending in .onion, and it will usually also contain a random, frequently changing series of numbers and letters.

2024 Threat Hunting Report
In the CrowdStrike 2024 Threat Hunting Report, CrowdStrike unveils the latest tactics of 245+ modern adversaries and shows how these adversaries continue to evolve and emulate legitimate user behavior. Get insights to help stop breaches here.
Download NowBest browsers for accessing the deep and dark web
When accessing the dark web, you can only use a secure browser (which is also called an onion browser). There are a few options available for this:
- Tor Browser: This browser (created by the Tor Project) is what people most commonly use when accessing the dark web. Unlike many other secure browsers, the Tor Browser is ready to use as soon as you download it.
- The Invisible Internet Project (I2P): This web browser and private network layer was designed to help people in oppressive regimes avoid internet censorship.
- Subgraph OS: Subgraph is an operating system and not a traditional web browser. This allows it to be bundled with a variety of advanced security features, including a secure email client and instant messaging program.
- Tails: The Amnesic Incognito Live System is a free operating system designed for browsing the dark web. You can download it onto a USB drive or a DVD and bring it with you on any computer. Because it runs primarily on RAM, it leaves no trace on the computer you use it on.
- Whonix: This is another operating system designed for dark web browsing. It doesn’t rely solely on Tor exit nodes, isolating its data streams for heightened security.
How CrowdStrike protects you from illegal dark web activity
It is absolutely critical to know if your information is on the dark web in order to properly protect yourself from threats. Dark web monitoring tools help find leaked or stolen information such as compromised credentials, intellectual property, and other sensitive data that has a presence in the dark web and is in danger of being shared by malicious actors operating on the dark web.
CrowdStrike Falcon® Adversary Intelligence provides comprehensive monitoring of the deep and dark web to identify threats targeting an organization’s brand, employees, and data. It helps detect compromised credentials, block fraudulent domains, and protect against phishing, brand impersonation, and cyber threats. By proactively alerting teams to potential risks and offering automated responses — such as disabling compromised accounts — CrowdStrike helps mitigate digital risks before they escalate into serious breaches.







