Zero Trust can be challenging to implement due to complexity of the technology stack, cross departmental organizational challenges, and mapping out a process for budgeting and execution.
Although each organization’s needs are unique, CrowdStrike offers the following recommendations to move Zero Trust along a journey of maturity based on your needs and priorities:
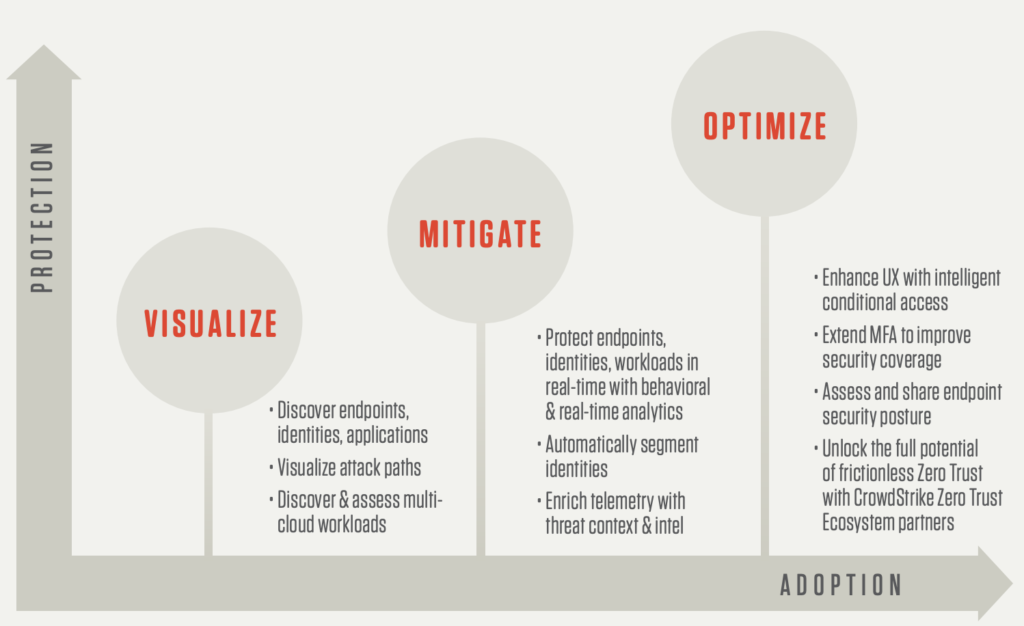
Stage 1: Visualize
In this stage, the intent is to understand all of the resources, their access points, and the risks involved. In the NIST framework, this is a continuous process as resources will change both in terms of availability, risk, and importance.
Key Goals:
- See all entities (identities, workloads, endpoints)
- Understand vulnerabilities or risks for all entities to see the attack path and key resources to defend
Best Practices:
- Avoid gaps in visibility, especially when dealing with various business units, M&A scenarios, and multi-cloud implementations (Azure, GCP, AWS, etc...).
- Avoid identity store gaps when using multiple identity providers (AD, Entra ID, SSO, etc…)
- Look at threats/risks against the entire Identity Store (e.g. protocol NTLM and relay attacks or Golden Ticket attacks on AD) as they compromise your entire environment very quickly
- Looking at all entities regardless of location or owner (endpoints, workloads, humans, workloads, apps, etc..). For example, service accounts can easily be overlooked - and most will bypass additional validation (i.e. MFA or audit). Workloads (and containers) are also critical to examine since attack vectors can bypass endpoints and start at workload via privileged users.
Resources:

The Complete Guide to Building an Identity Protection Strategy
Take the first step toward a resilient identity security posture and download the Complete Guide to Building an Identity Protection Strategy to protect your organization’s digital identity landscape today.
Download NowStage 2: Mitigate
In this stage, an organization is ready to detect and stop threats or mitigate impact of the breach in case a threat cannot be immediately stopped. NIST calls out automation and orchestration as this is critical for real-time detection and response.
Key Goals:
- Real-time threat mitigation and policy response looking at mitigation at each component (endpoint, workload, identity, etc..)
- Incorporate behavioral analytics to detect threats such as
- Insider threats
- Takeover of legitimate credentials
- Limit breach impact with segmentation and least privileged principles
- New ways of segmentation that don’t require many policy updates and are not network/infra dependent
- Stop lateral movement inside the environment
Best Practices:
- Minimize operational overhead due to security policy updates by
- Using identity based segmentation (vs. legacy way of using network and app segmentation that can change frequently)
- Incorporating a policy model for both security and compliance/corporate needs easily
- Need to test and ensure policy is “ready” before deploying
- Threat detection thresholds and false positives
- Risk analysis based on static and dynamic factors
- Extend context with additional informational sources (including from legacy systems and SSO credentials systems)
- Have actionable information even as ML models are learning (eg. static AD info)
- Find threats with reduced management of data storage and analysis
- A cloud and real-time approach minimizes data volume and management overhead requirements
- Increase automation for faster response time and cost efficiency
- Incorporating policy actions into existing SOAR workflows
- Continuous adjustments (of policy, thresholds, ML, etc.)

2024 Threat Hunting Report
In the CrowdStrike 2024 Threat Hunting Report, CrowdStrike unveils the latest tactics of 245+ modern adversaries and shows how these adversaries continue to evolve and emulate legitimate user behavior. Get insights to help stop breaches here.
Download NowStage 3: Optimize
At this stage, the goal is to extend protection to every aspect of the IT infrastructure and all resources regardless of location without creating a poor user experience (which can lead to non-compliance and lower productivity).
Key goals:
- Deploy conditional access (risk-based) for continuous verification without compromising a positive user experience.
Best Practices:
- Eliminate MFA fatigue with risk-based, conditional access even for privileged users (which only challenges users when risk levels change on the endpoint, identity itself, workload, or on other systems via API integrations)
- Extend MFA protection to legacy systems to ensure a no-gap coverage (and protect the typically most vulnerable systems)
- Detecting and responding to threats for public clouds (SaaS) and SSO credentials even if a sensor/agent is not possible to deploy
Additional Resources:
- ZTA - Zero Trust Assessment brief





