CrowdStrike Falcon® Identity Protection
Stop modern identity-based attacks in real time
The industry’s only unified identity and endpoint security solution
-
Real-Time Protection for EntraID is now GA.
Check out the Press Release
Stolen credentials have become a primary tool for adversaries to infiltrate organizations. Traditional security measures fall short against these sophisticated identity-based attacks.

What's new
Identity is one of the fastest growing threat vectors
Get real-time identity protection to stay ahead of the modern adversary.
Why choose Falcon Identity Protection?
Faster Detection
85%
faster detection of identity attacks, offsetting ~5,000 investigation hours1
Time Reduction
75%
reduction of time and resources spent supporting password resets1
Investment Benefit
310%
return on investment (ROI) and a payback period of less than 6 months2
310% ROI with Falcon Identity Protection
ROI in under six months and breach risk reduced by 50% — learn more in the commissioned Total Economic Impact™ study by Forrester Consulting.
See how CrowdStrike secures identities
Falcon Identity Protection Overview (3 min)
Demo: Stopping Lateral Movement (1 min)
Demo: Secure Your Cloud Identity Environment (2:20 min)
Unified Identity Protection
Secure your organization with real-time identity protection
AI-driven identity security, from endpoint to cloud
Unified identity and endpoint security
Deploy a single agent for immediate value. Gain full visibility and protection across attack paths, boosting response times and stopping modern adversaries.
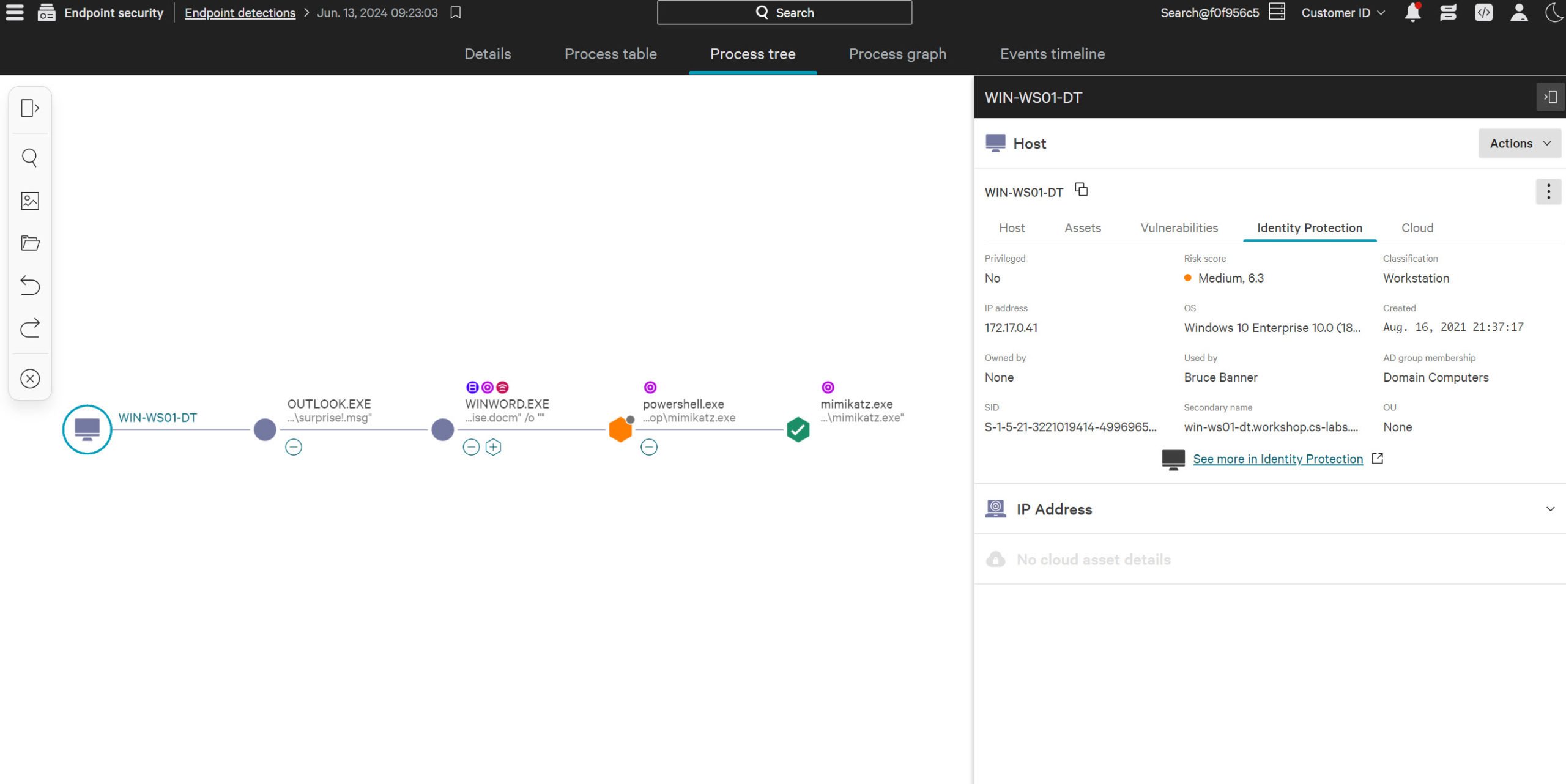
Stop cross-domain attacks
With unified visibility across cloud, endpoints and identities, correlate and detect cross-domain attacks to stop adversaries from moving laterally across your environments.
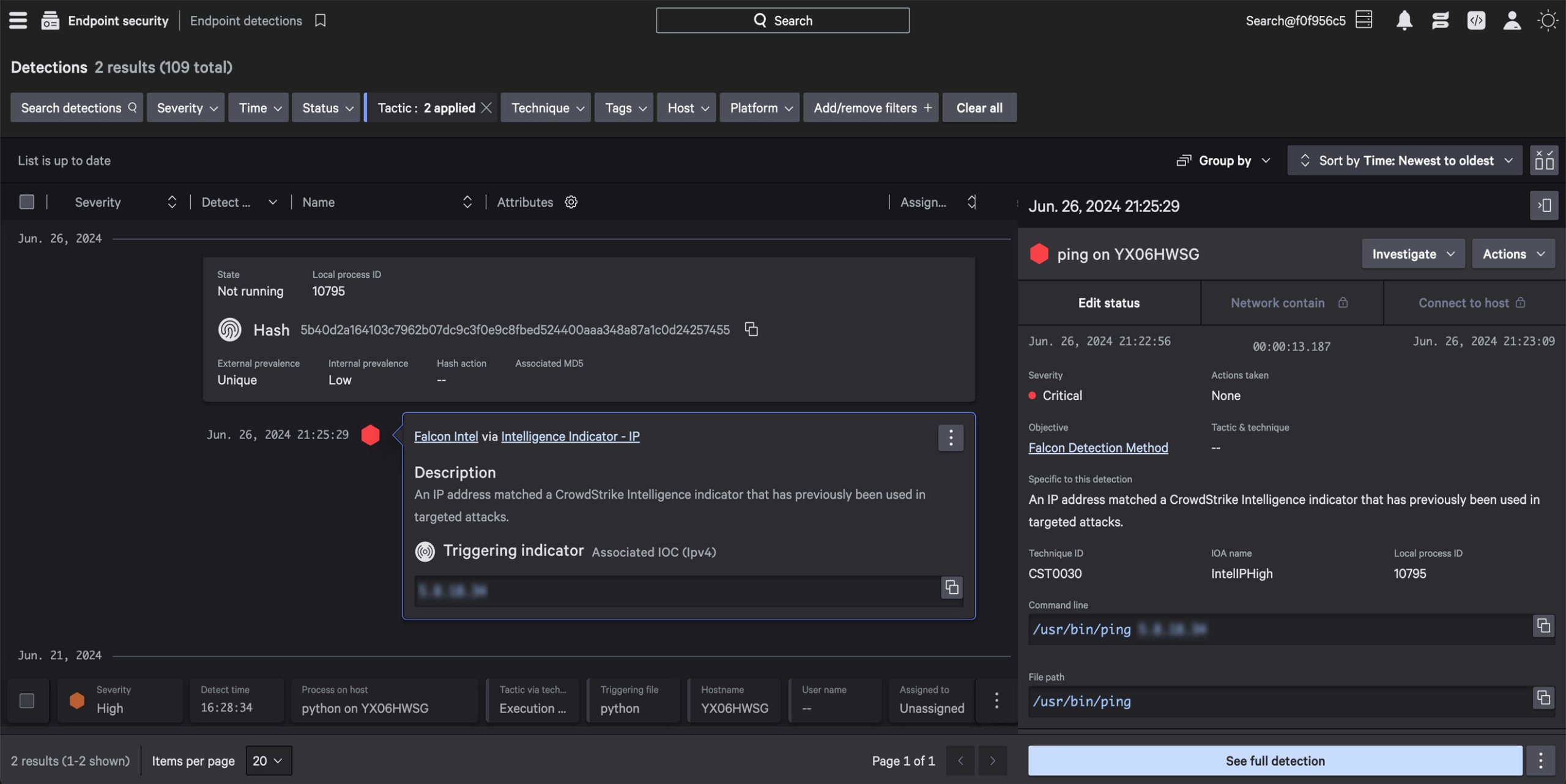
Comprehensive protection for hybrid identity environments
Get complete visibility and real-time protection across Active Directory, cloud identity providers— such as Entra ID and Okta, as well as your SaaS applications, with built-in industry-leading threat intelligence.
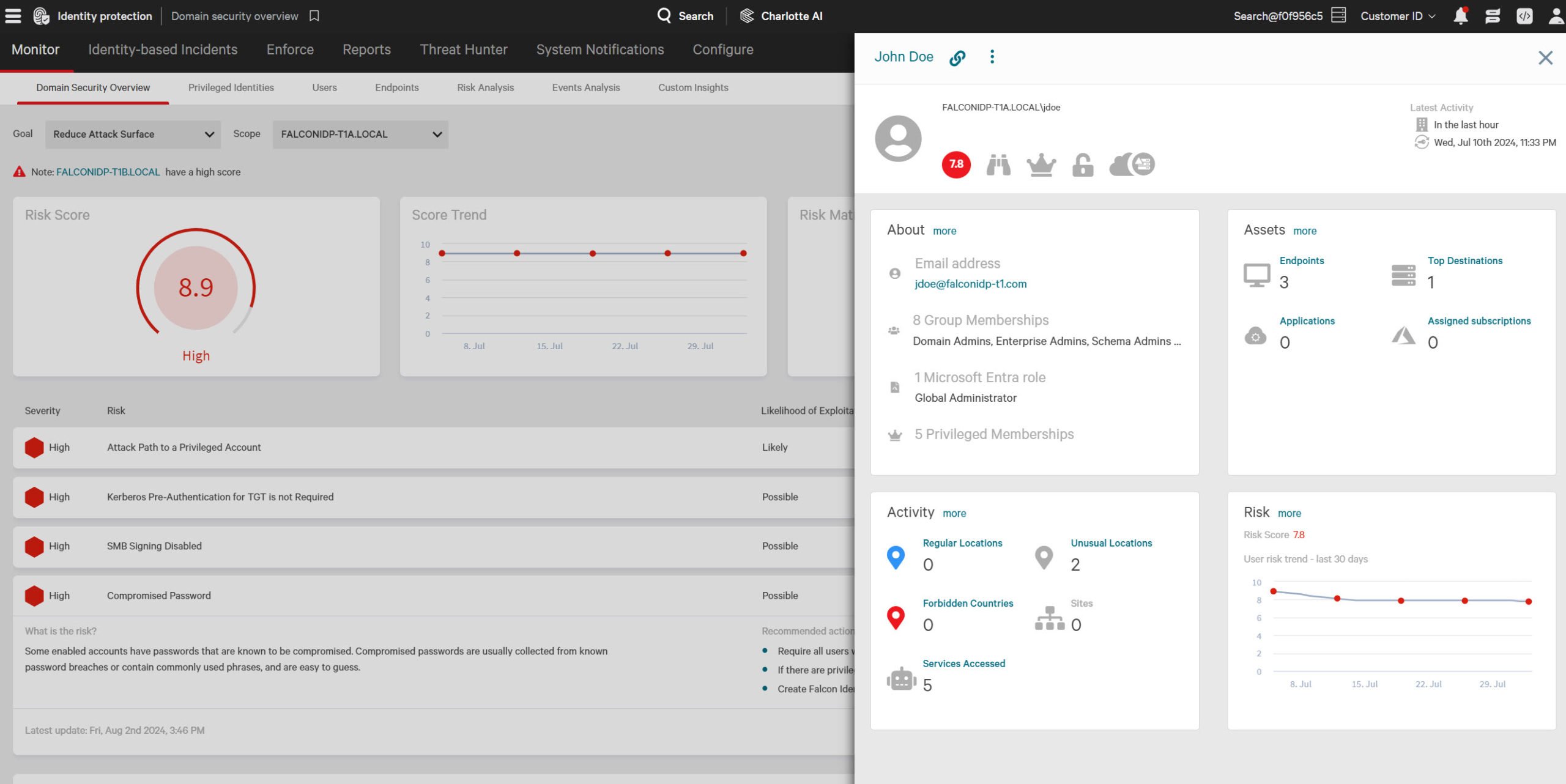
AI-powered detection to catch hidden adversaries
Automatically establish a baseline for typical user behavior to swiftly identify anomalies and neutralize sophisticated identity based threats.
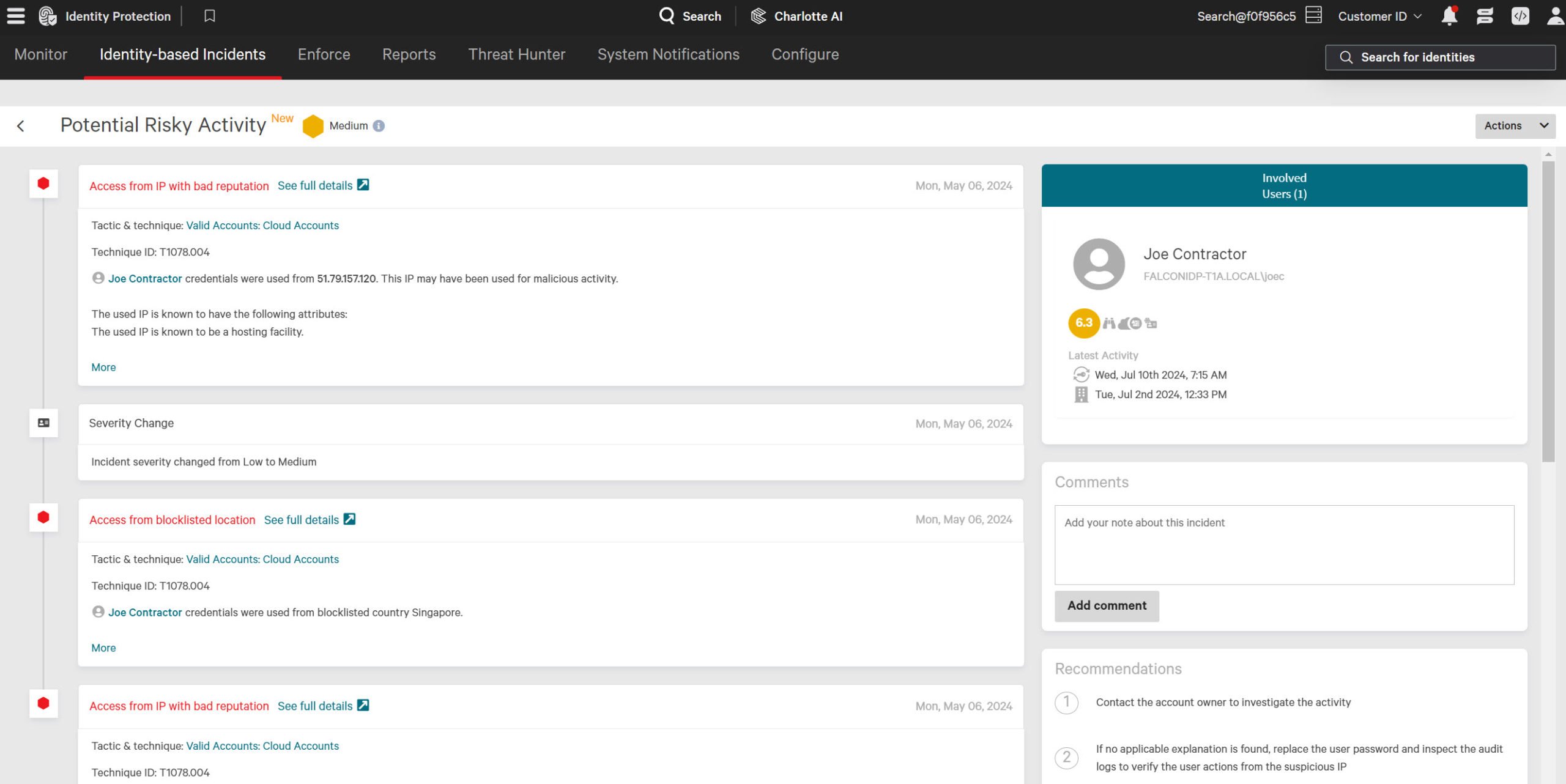
Stop lateral movement in real time
Block lateral movement of the adversary across the authentication layer and endpoints. Improve your response times and eliminate the need to hunt through logs.
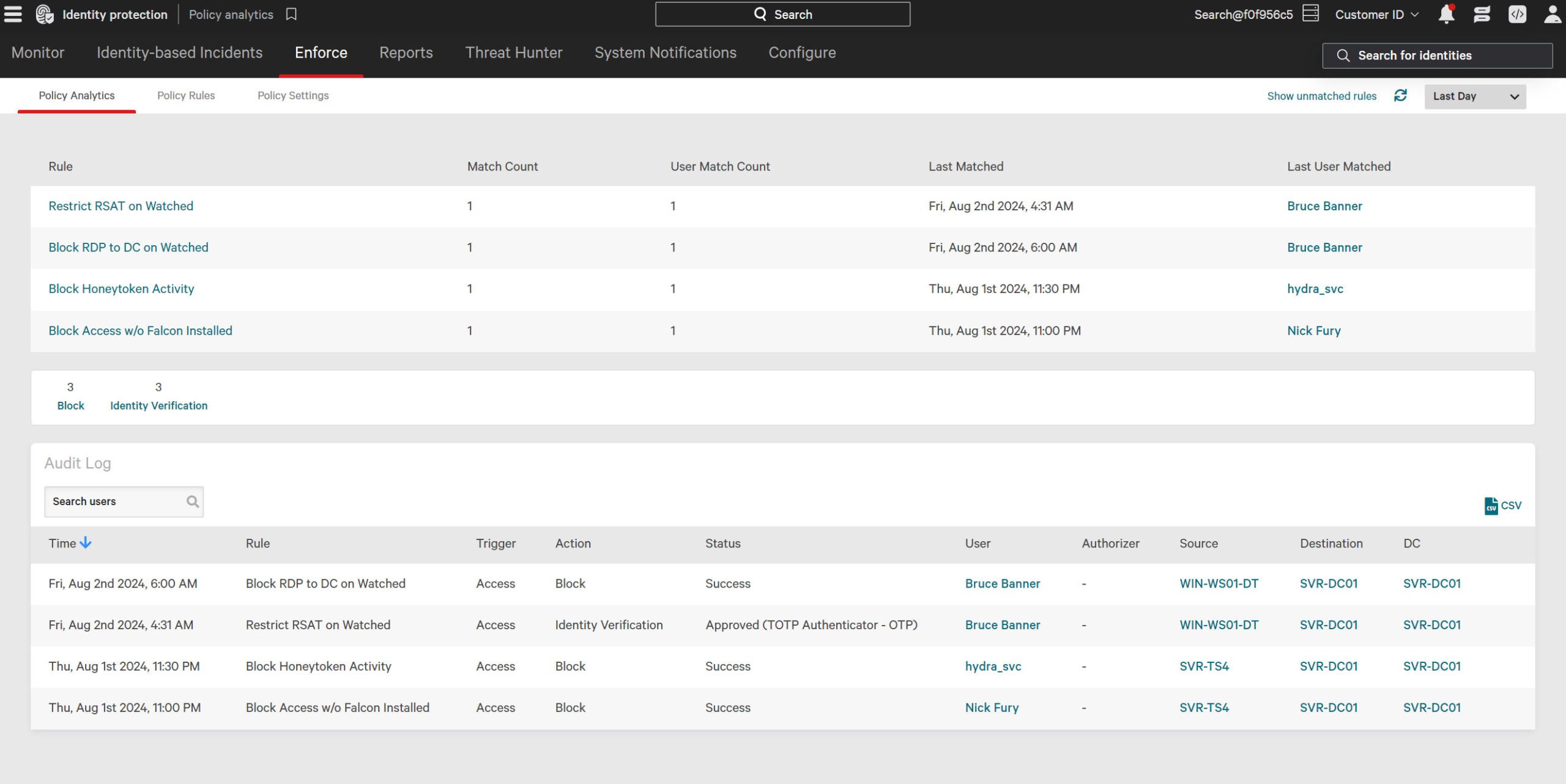
Dynamic, risk-based conditional access
Continuously monitor user behavior and risk context with dynamic enforcement of multi-factor authentication (MFA) when risk changes. Seamlessly extend MFA coverage to legacy systems and protocols that are likely to be exploited.
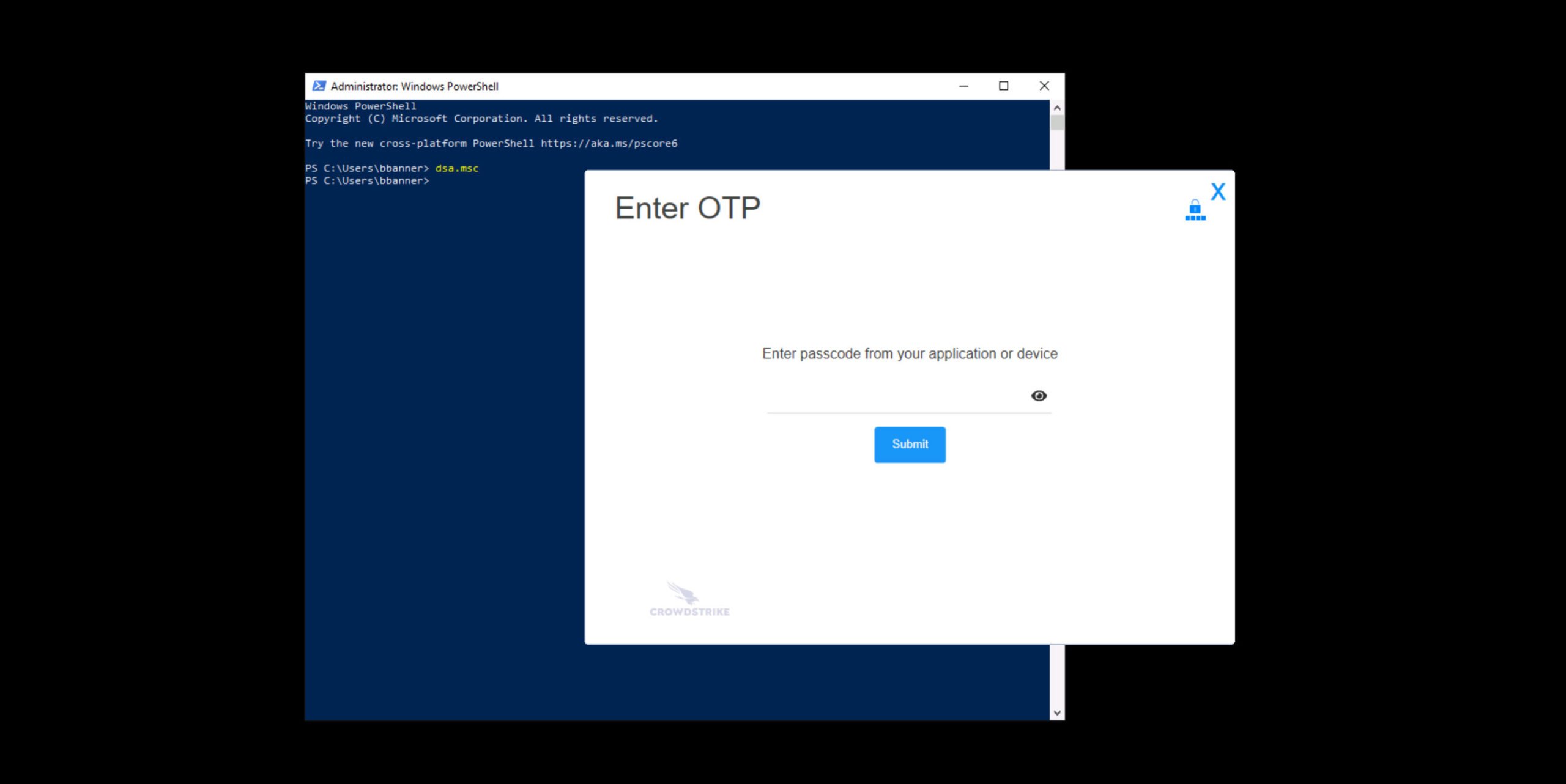
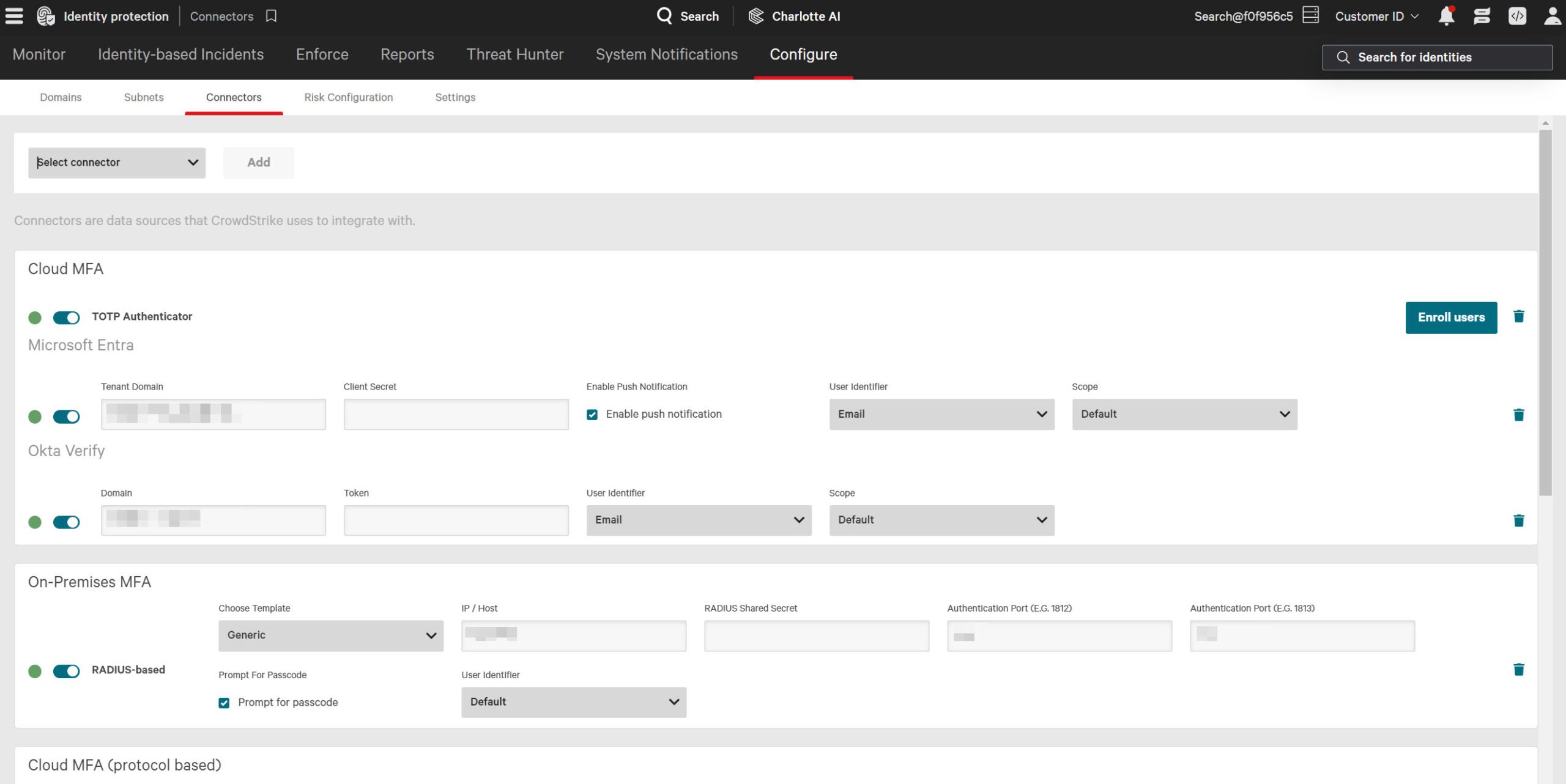
Seamless integration for rapid time to value
Integrate Falcon Identity Protection effortlessly with the security infrastructure of your choice. Use APIs to connect seamlessly with MFA providers, SIEM, and SOAR technologies, ensuring a cohesive and comprehensive security strategy.
24/7 Managed Detection and Response for modern threats
Leverage industry-leading managed detection and response services for continuous monitoring and expert threat hunting. Ensure your identity infrastructure is always secure, with around the clock responses to any potential threats.
Customers trust CrowdStrike for
Identity Protection
CrowdStrike named an Overall Leader in the ITDR Leadership Compass by KuppingerCole
See why customers trust CrowdStrike

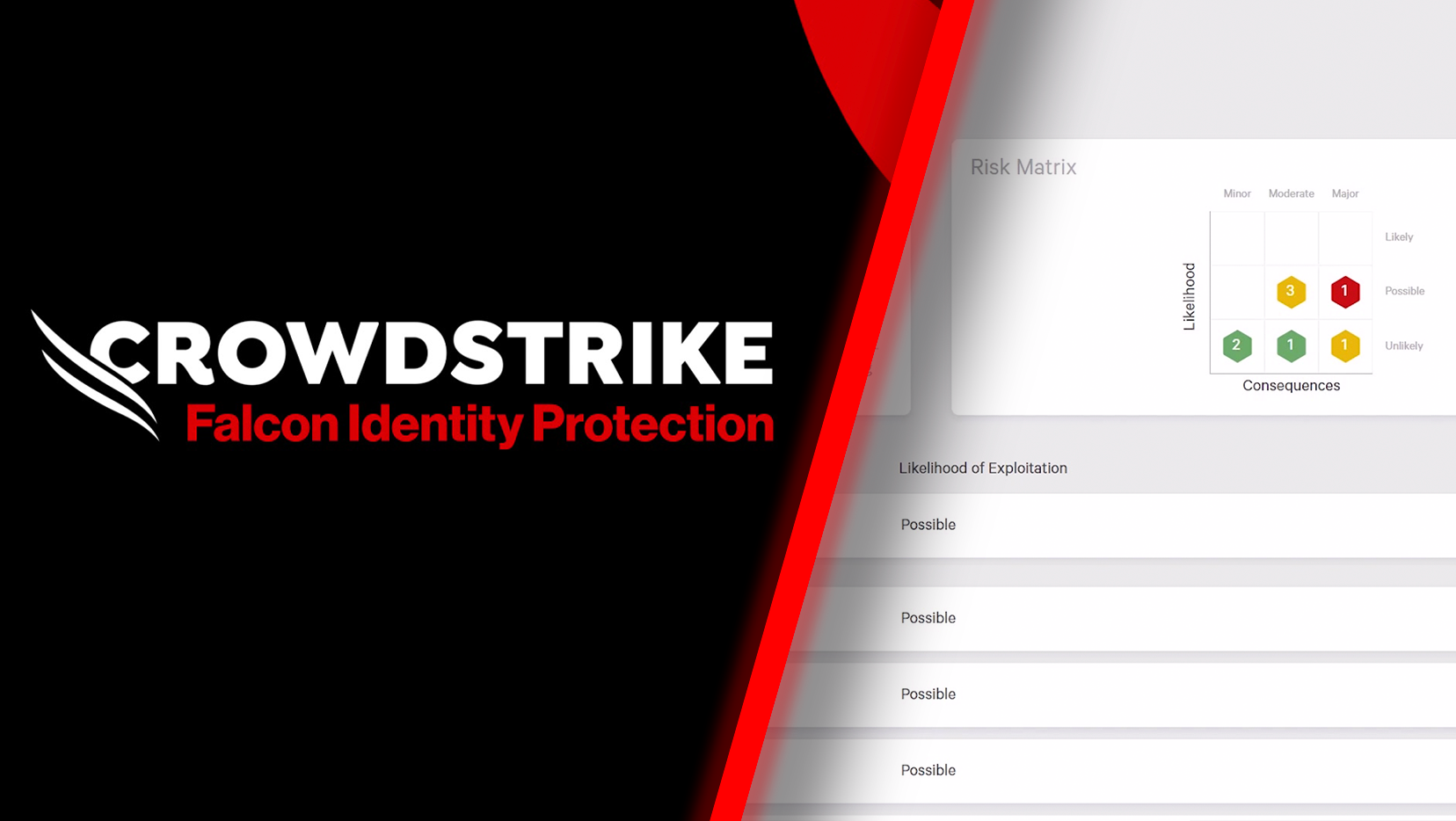
Get an Identity Security Risk Review
Evaluate your current Microsoft Entra ID and Active Directory security posture with a detailed report and a 1:1 session with a CrowdStrike identity expert.
Schedule free reviewComprehensive Identity Security
Explore identity protection use cases

Start protecting identities today
Take the first step towards comprehensive identity security with a complimentary Identity Security Risk Review.
Schedule free reviewFeatured resources
1 These numbers are projected estimates of average benefit based on recorded metrics provided by customers during pre-sale motions that compare the value of CrowdStrike with the customer’s incumbent solution. Actual realized value will depend on individual customer’s module deployment and environment.
2 Forrester Total Economic Impact (TEI) for Falcon Identity Protection