What is Proactive Threat Hunting?
Threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. Cyber threat hunting digs deep to find malicious actors in your environment that have slipped past your initial endpoint security defenses.
After sneaking in, an attacker can stealthily remain in a network for months as they quietly collect data, look for confidential material, or obtain login credentials that will allow them to move laterally across the environment.
Once an adversary is successful in evading detection and an attack has penetrated an organization’s defenses, many organizations lack the advanced detection capabilities needed to stop the advanced persistent threats from remaining in the network. That’s why threat hunting is an essential component of any defense strategy.
Threat hunting is becoming increasingly important as companies seek to stay ahead of the latest cyber threats and rapidly respond to any potential attacks.

2023 Threat Hunting Report
In the 2023 Threat Hunting Report, CrowdStrike’s Counter Adversary Operations team exposes the latest adversary tradecraft and provides knowledge and insights to help stop breaches.
Download NowThreat Hunting Methodologies
Threat hunters assume that adversaries are already in the system, and they initiate investigation to find unusual behavior that may indicate the presence of malicious activity. In proactive threat hunting, this initiation of investigation typically falls into three main categories:
1. Hypothesis-driven investigation
Hypothesis-driven investigations are often triggered by a new threat that’s been identified through a large pool of crowdsourced attack data, giving insights into attackers’ latest tactics, techniques, and procedures (TTP). Once a new TTP has been identified, threat hunters will then look to discover if the attacker’s specific behaviors are found in their own environment.
2. Investigation based on known Indicators of Compromise or Indicators of Attack
This approach to threat hunting involves leveraging tactical threat intelligence to catalog known IOCs and IOAs associated with new threats. These then become triggers that threat hunters use to uncover potential hidden attacks or ongoing malicious activity.
3. Advanced analytics and machine learning investigations
The third approach combines powerful data analysis and machine learning to sift through a massive amount of information in order to detect irregularities that may suggest potential malicious activity. These anomalies become hunting leads that are investigated by skilled analysts to identify stealthy threats.
All three approaches are a human-powered effort that combines threat intelligence resources with advanced security technology to proactively protect an organization’s systems and information.
Learn More
Download the threat hunting white paper, Proactive Hunting: The Last Line of Defense Against the “Mega Breach”, to get a detailed analysis of how highly skilled human hunters pair with technology to aggressively seek out threats.
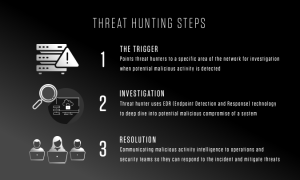
Threat Hunting Steps
The process of proactive cyber threat hunting typically involves three steps: a trigger, an investigation and a resolution.
Step 1: The Trigger
A trigger points threat hunters to a specific system or area of the network for further investigation when advanced detection tools identify unusual actions that may indicate malicious activity. Often, a hypothesis about a new threat can be the trigger for proactive hunting. For example, a security team may search for advanced threats that use tools like fileless malware to evade existing defenses.
Step 2: Investigation
During the investigation phase, the threat hunter uses technology such as EDR (Endpoint Detection and Response) to take a deep dive into potential malicious compromise of a system. The investigation continues until either the activity is deemed benign or a complete picture of the malicious behavior has been created.
Step 3: Resolution
The resolution phase involves communicating relevant malicious activity intelligence to operations and security teams so they can respond to the incident and mitigate threats. The data gathered about both malicious and benign activity can be fed into automated technology to improve its effectiveness without further human intervention.
Throughout this process, cyber threat hunters gather as much information as possible about an attacker’s actions, methods and goals. They also analyze collected data to determine trends in an organization’s security environment, eliminate current vulnerabilities and make predictions to enhance security in the future.
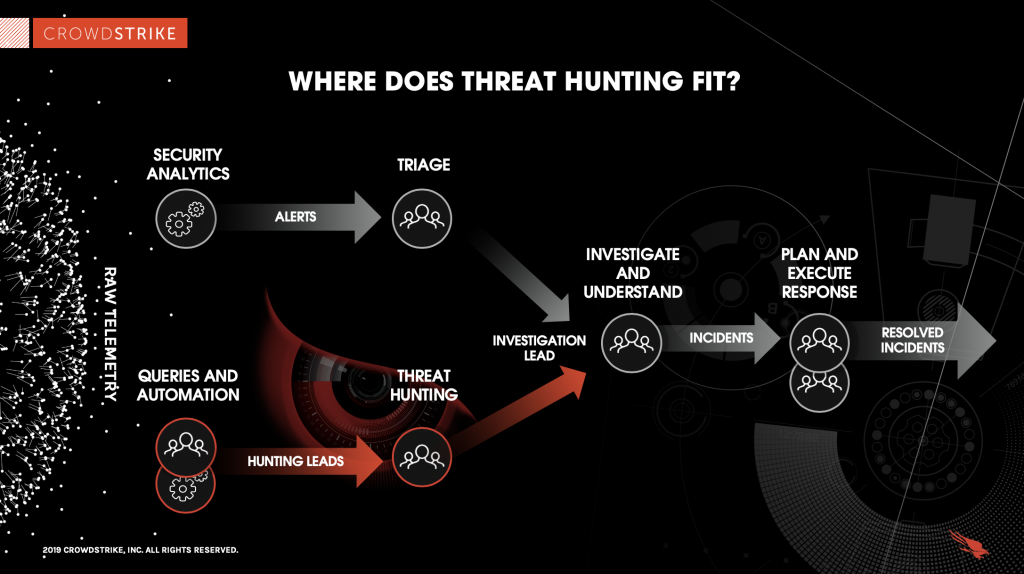
Where Does Threat Hunting Fit?
Threat hunting is highly complementary to the standard process of incident detection, response, and remediation. As security technologies analyze the raw data to generate alerts, threat hunting is working in parallel – using queries and automation – to extract hunting leads out of the same data.
Hunting leads are then analyzed by human threat hunters, who are skilled in identifying the signs of adversary activity, which can then be managed through the same pipeline. This process is illustrated below:
Should You Enlist a Managed Threat Hunting Service?
Although the concept of threat hunting is clear, the challenge comes with actually sourcing personnel who can conduct the exercise properly. The best threat hunters are those that are battle-tested with ample experience in combating cyber adversaries.
Unfortunately, there is a major skills shortage in the cybersecurity industry when it comes to threat hunting, meaning that seasoned hunters don’t come cheap. That’s why many organizations find themselves turning to managed services, who can deliver deep expertise and 24x7 vigilance at a more affordable cost.
Below, let’s explore what to look for in a threat hunting service:
What's Required to Start Threat Hunting?

A top threat hunting service takes a three-pronged approach to attack detection. Along with skilled security professionals, it includes two other components necessary for successful hunting: vast data and powerful analytics.
1. Human Capital
Every new generation of security technology is able to detect a greater number of advanced threats — but the most effective detection engine is still the human brain. Automated detection techniques are inherently predictable, and today’s attackers are very aware of this and develop techniques to bypass, evade or hide from automated security tools. Human threat hunters are an absolutely critical component in an effective threat hunting service.
Since proactive hunting depends on human interaction and intervention, success depends on who is hunting through the data. Intrusion analysts must have expertise to identify sophisticated targeted attacks, and they also must have the necessary security resources to respond to any discovery of unusual behavior.
2. A Wealth of Data
The service must also have the ability to gather and store granular system events data in order to provide absolute visibility into all endpoints and network assets. With the use of a scalable cloud infrastructure, a good security service then aggregates and perform real-time analysis on these large data sets.
3. Threat Intelligence
Lastly, a threat hunting solution should be able to cross-references internal organizational data with the latest threat intelligence about external trends and deploys sophisticated tools to effectively analyze and correlate malicious actions.
All of this takes time, resources and dedication — and most organizations aren’t adequately staffed and equipped to mount a continuous 24/7 threat hunting operation. Fortunately, there are managed security solutions that have the right resources — the necessary people, data and analytical tools — to effectively hunt for unusual network activity and hidden threats.
 Benefits of Managed Services
Benefits of Managed ServicesHow Does Extended Storage Help with Threat Hunting?
Retaining security data for extended periods of time enables threat hunters to extract enhanced visibility and threat context from real-time and historical data, supporting the completeness and accuracy of investigation and analysis. This extended storage of security data empowers teams to proactively and more quickly search and uncover hidden threats in the environment; remove advanced persistent threats (APTs) by sifting through the data to detect irregularities that might suggest potentially malicious behavior; and better prioritize and address vulnerabilities before they can be weaponized.
By ingesting and retaining security data in a repository, users can quickly search and correlate disparate data sets to get new insights and a clearer understanding of the environment. With the unification of multiple log sources including security detections and threat intelligence, hunters can better define and narrow the scope of detections to precisely match adversary techniques and behaviors, resulting in fewer false positives. Once extended storage and management is enabled with enriched security telemetry, security teams gain the needed visibility and context for their investigations to accelerate detection and response of potential threats.
CrowdStrike’s Managed Threat Hunting Service
CrowdStrike Falcon® OverWatch™ brings together all three prongs in a 24/7 security solution that proactively hunts, investigates and advises on threat activity in an organization’s environment.
Watch the video below to see how the OverWatch team hunts for threats in an environment:
Our elite team of hunters sift through endpoint event data from across CrowdStrike’s worldwide customer community to swiftly identify and stop highly sophisticated attacks that would otherwise go undetected.
This proactive managed hunting finds breaches days, weeks or even months before they would have been uncovered by conventional automated-only methods, effectively limiting the opportunity for attackers to coordinate data exfiltration operations that ultimately lead to mega breaches.
Falcon OverWatch can help you detect and respond to cyber incidents around the clock. Find out more about the powerful security advantage that Falcon OverWatch gives you by visiting the product page or downloading the data sheet: