How CrowdStrike Detects and Prevents Sunburst Post-Exploit Activities
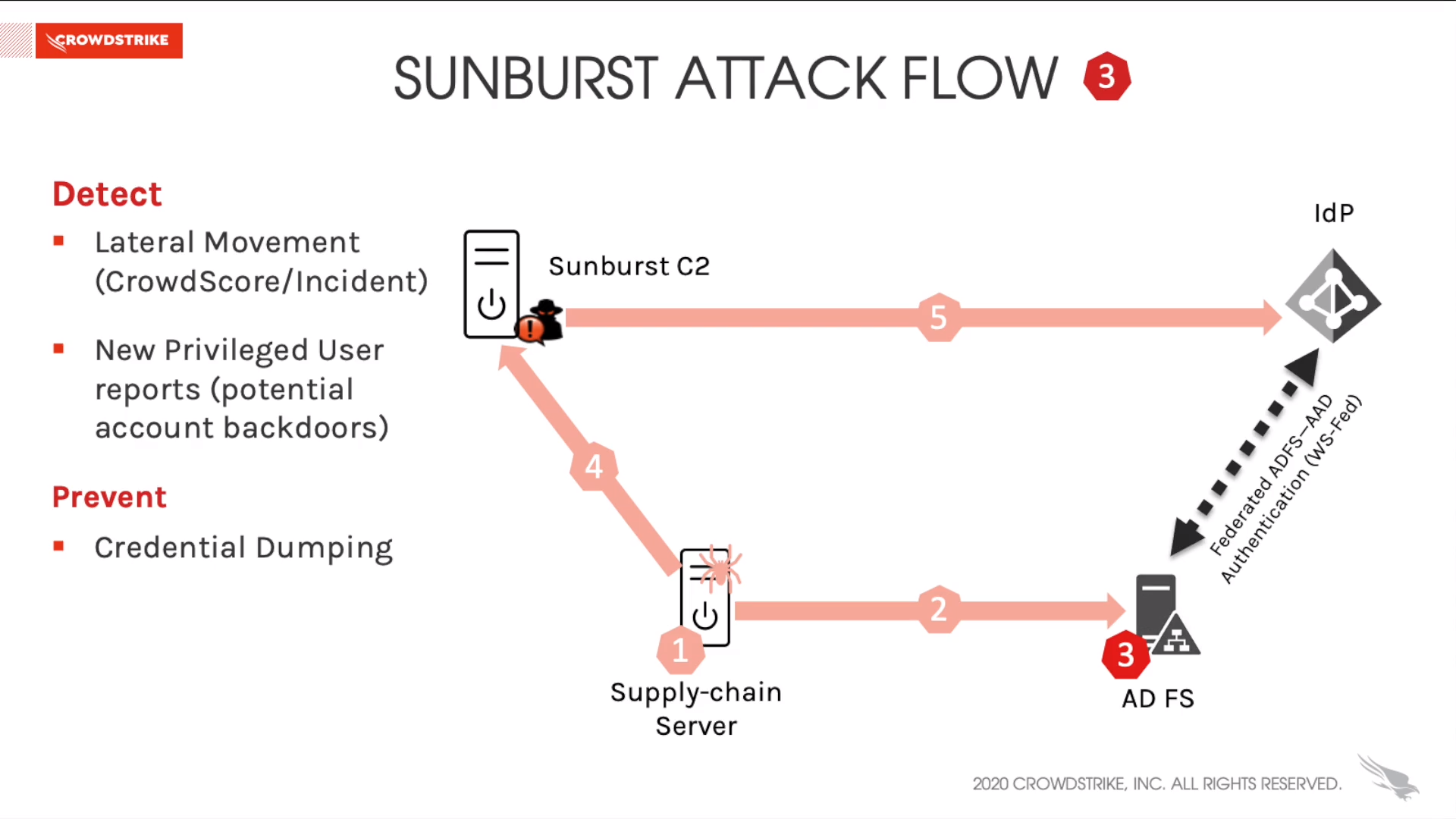
The Sunburst supply-chain attack affected industries from public to private, with the principle spread via privileged accounts and lateral movement. The principles of Zero Trust architecture can be leveraged today to contain adversaries in this type of attack, and for future 0-day attacks involving identity from initial escalation and lateral movement through persistence on the network.
Discover More at our
Resource Center
Tech Hub
For technical information on installation, policy configuration and more, please visit the CrowdStrike Tech Hub.
Visit Tech Hub