The Rise of Cross-Domain Attacks
How speed, visibility and unified security defeat the new era of cyber threats
Download ebookCrowdStrike Endpoint Security
Stop breaches with AI-powered protection, detection, and response backed by world-class adversary intelligence.
100% Detection, Protection & Accuracy: SE Labs Ransomware 2024
Download the reportCrowdStrike Named a Leader in the 2024 Gartner® Magic Quadrant™ for Endpoint Protection Platforms.
Protect
100%
Ransomware protection in the 2024 SE Labs Enterprise Advanced Security (EDR) Ransomware test1
Detect
96%
More potential threats identified in half the time3
Respond
70%
Reduction in mean time to response (MTTR)2
Stop attacks — from commodity malware to fileless and zero-day threats — with an endpoint protection platform (EPP) powered by cutting-edge AI/ML. Our elite threat intelligence, industry-first indicators of attack, script control, and advanced memory scanning detect and block malicious behaviors early in the kill chain.
With unified visibility across cloud, endpoints and identities, correlate and detect cross-domain attacks to stop adversaries from moving laterally across your environments.
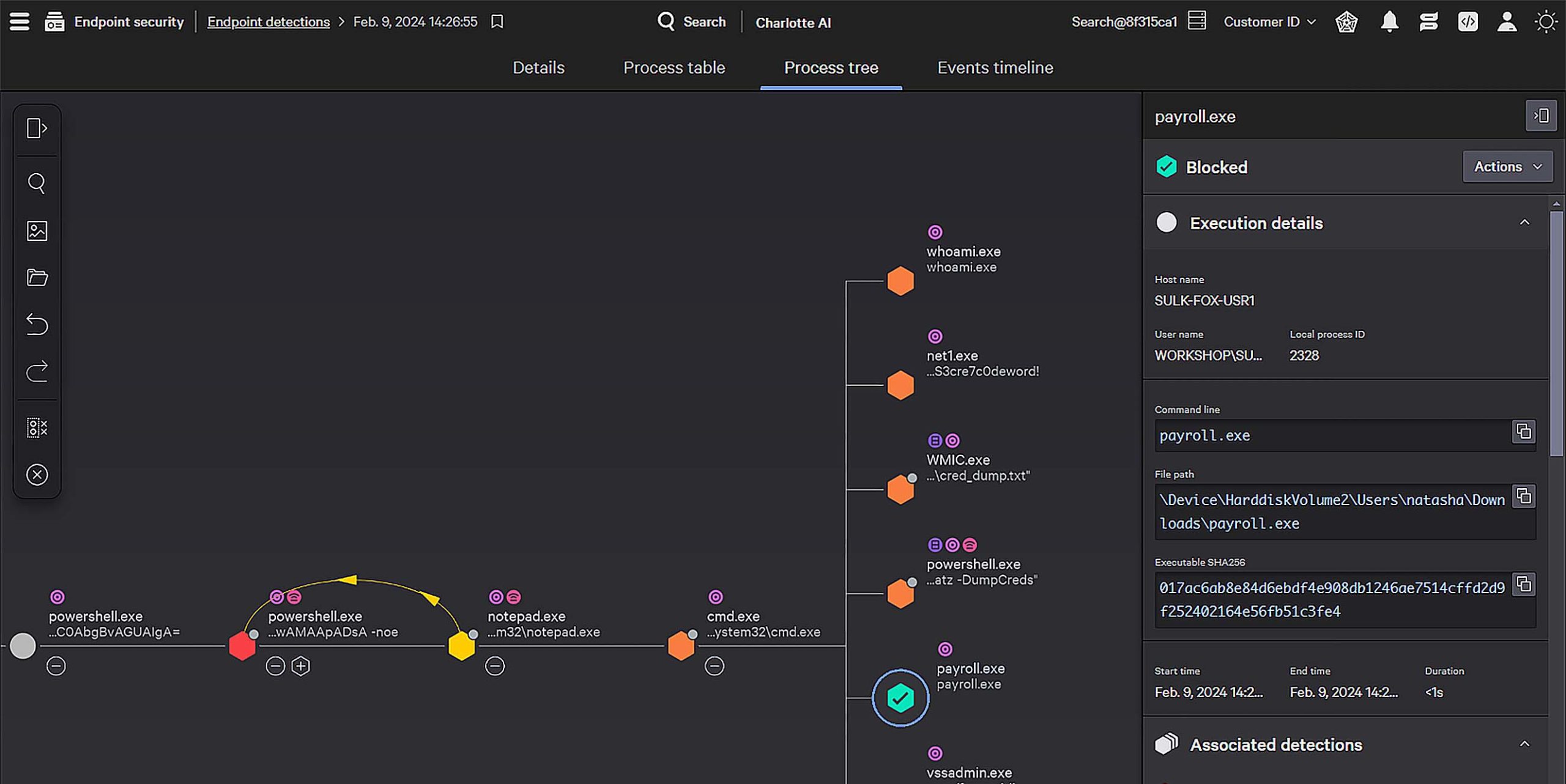
CrowdStrike pioneered EDR delivering comprehensive coverage with a single platform, single console, and single agent — shutting down the most advanced adversaries in record time. Our unique adversary-driven approach uncovers the most elusive threats with tactical precision, delivering high-quality, context-rich detections with minimal false positives.
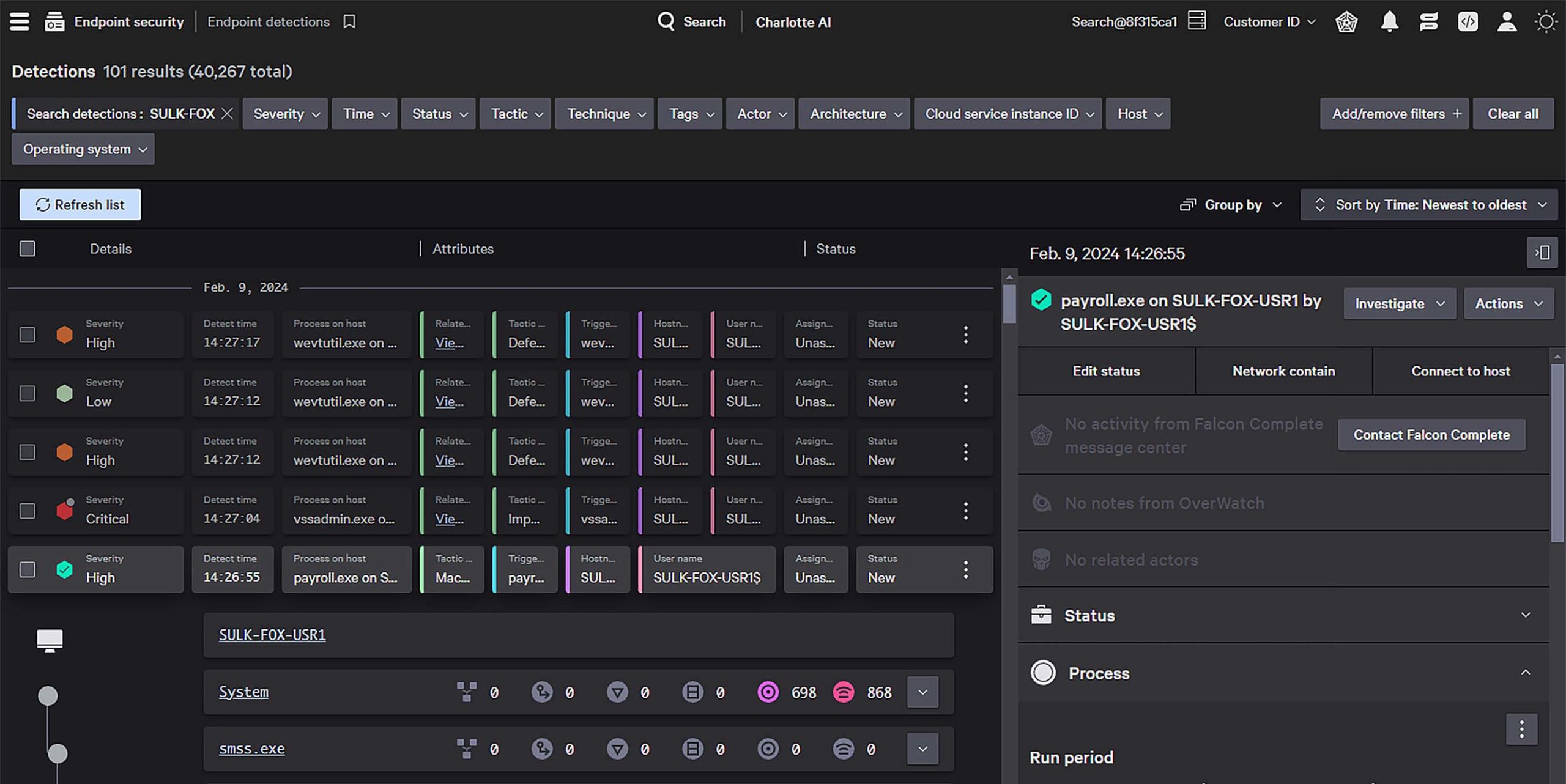
Windows, macOS, Linux, ChromeOS, Android, iOS — we protect them all, including legacy operating systems. Gain unwavering, fleet-wide visibility across all your endpoints, leaving adversaries nowhere to hide.
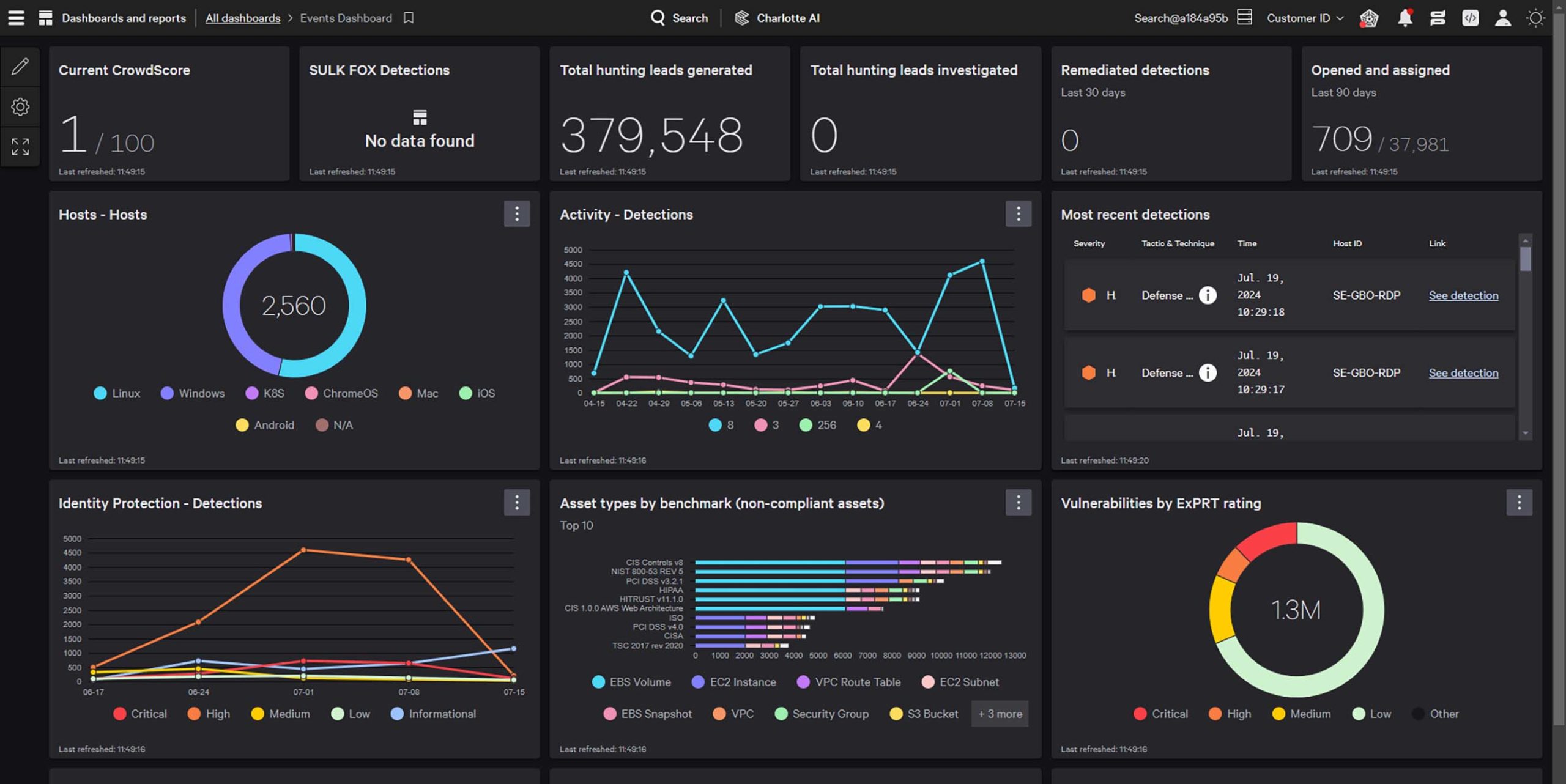
Harness the power of Charlotte AI and AI-powered risk scoring to prioritize threats and turn hours of work into minutes or seconds. Transform security operations and empower your analysts to stop breaches like the most seasoned experts.
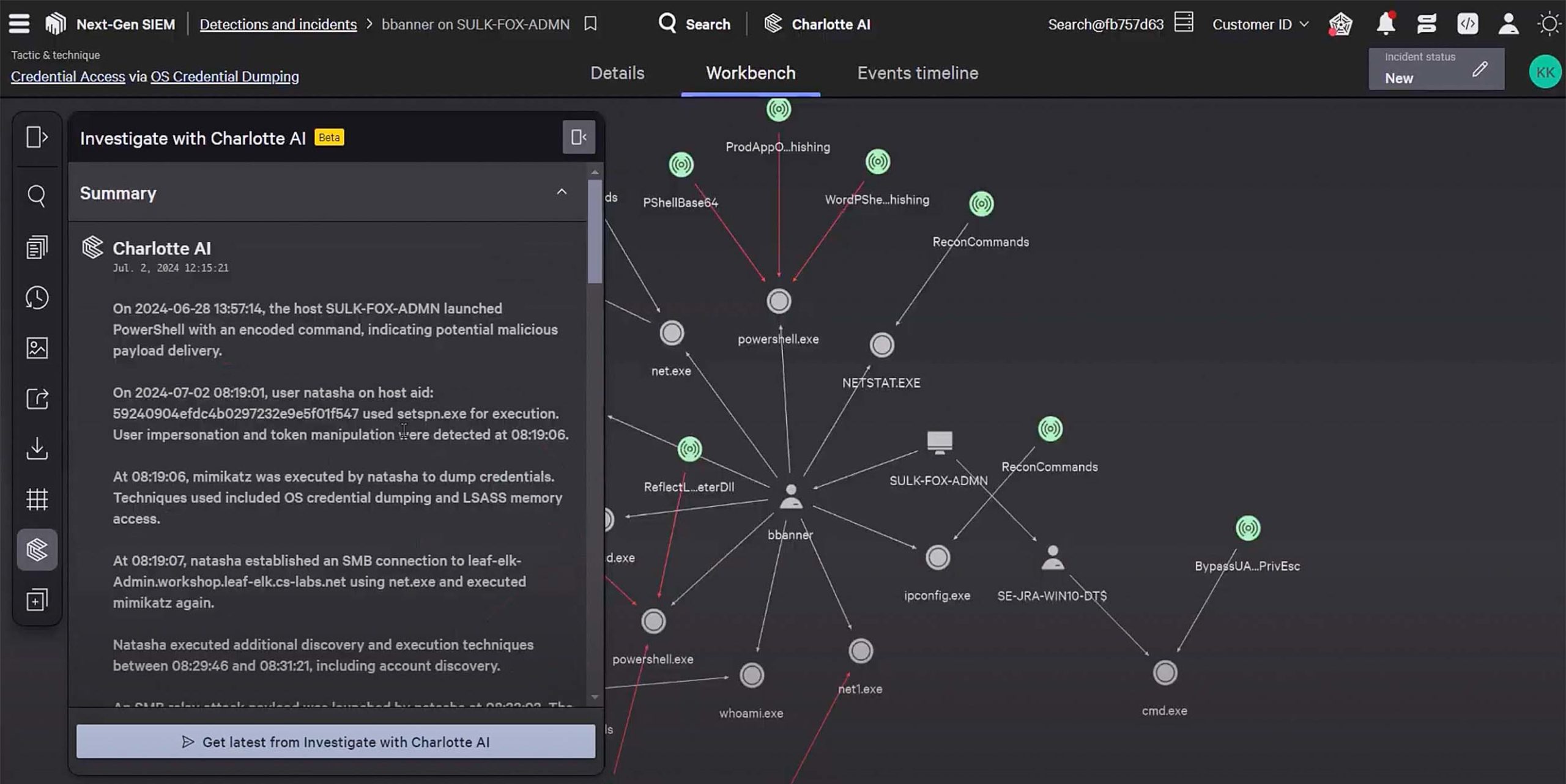
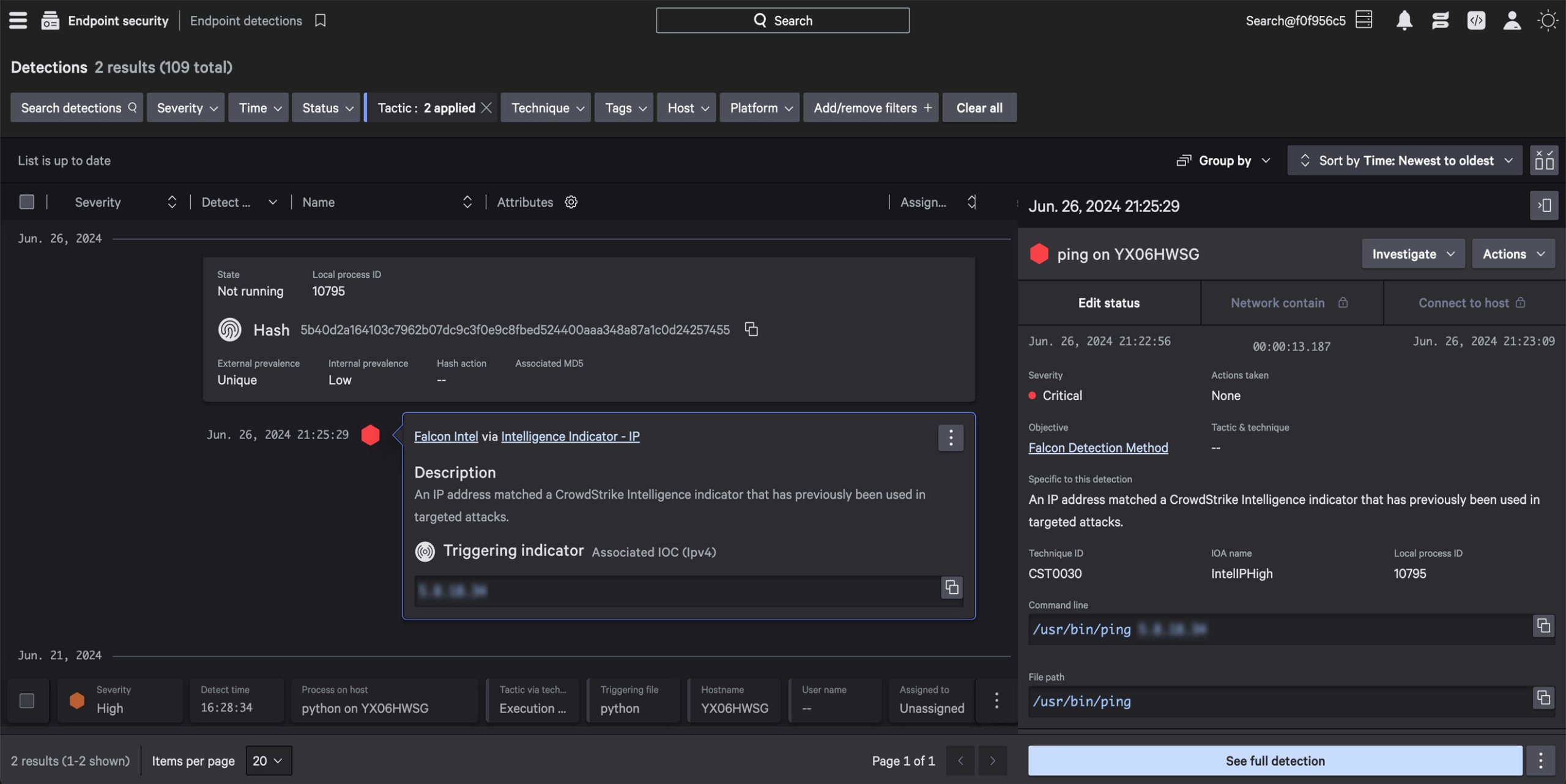
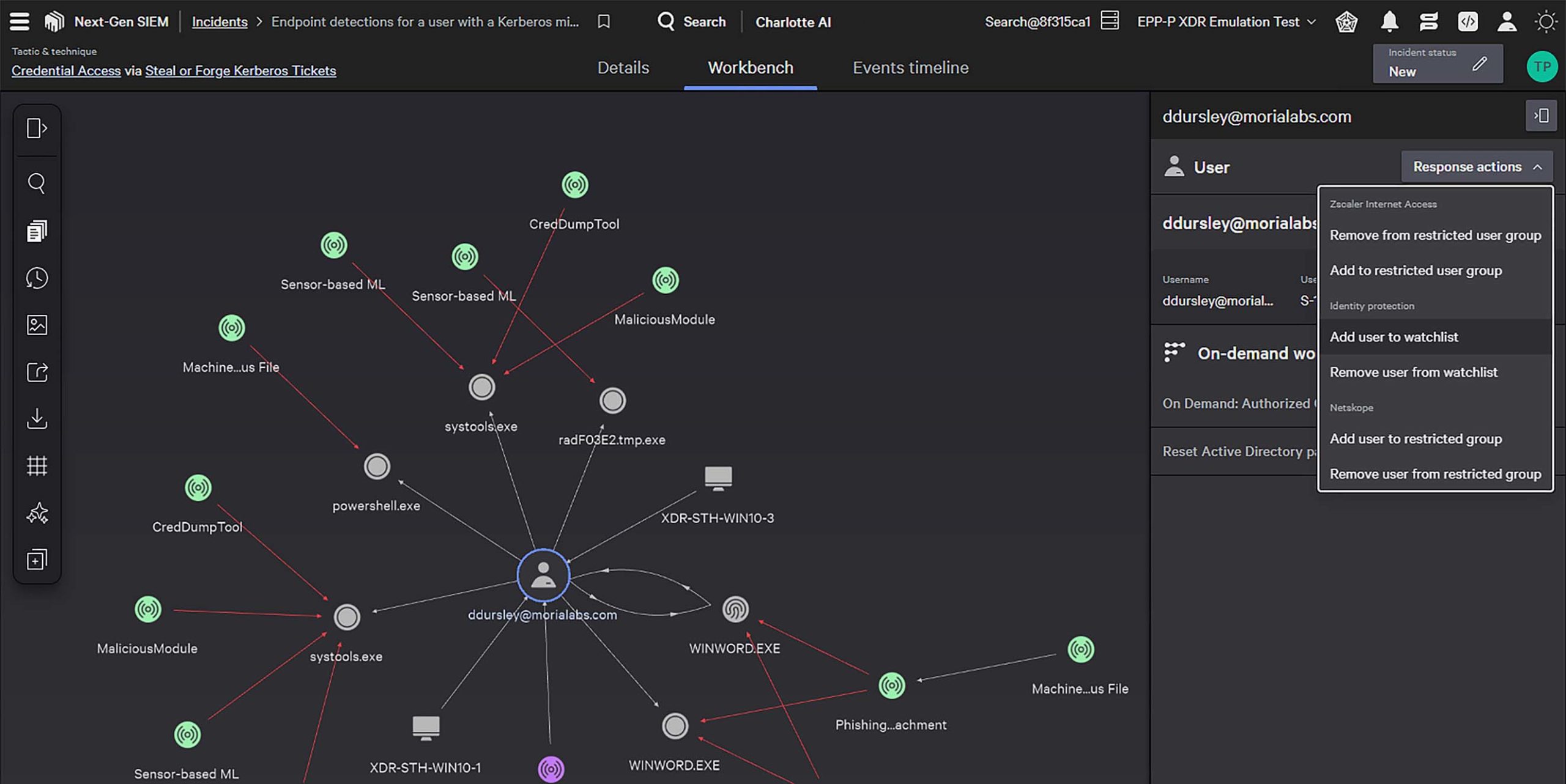
Extend industry-leading EDR with context from identity, cloud, mobile, and data flows for unified, lightning fast investigations. CrowdStrike EDR customers get native XDR at no additional cost and can extend visibility across third party data with Falcon Next-Gen SIEM, available in the same console.

Total protection has never been easier. Enjoy a free trial of the Falcon platform in just a few clicks.
Start a free trial12024 SE Labs Enterprise Advanced Security (EDR) Ransomware test
2These numbers are projected estimates of average benefits based on recorded metrics provided by customers during pre-sale motions that compare the value of CrowdStrike with the customer’s incumbent solution. Actual realized value will depend on individual customer’s module deployment and environment.
3Results are from IDC Business Value Report. Individual results may vary by customer.