CrowdStrike 2024 Threat Hunting Report
86% of hands-on-keyboard attacks were executed by eCrime actors
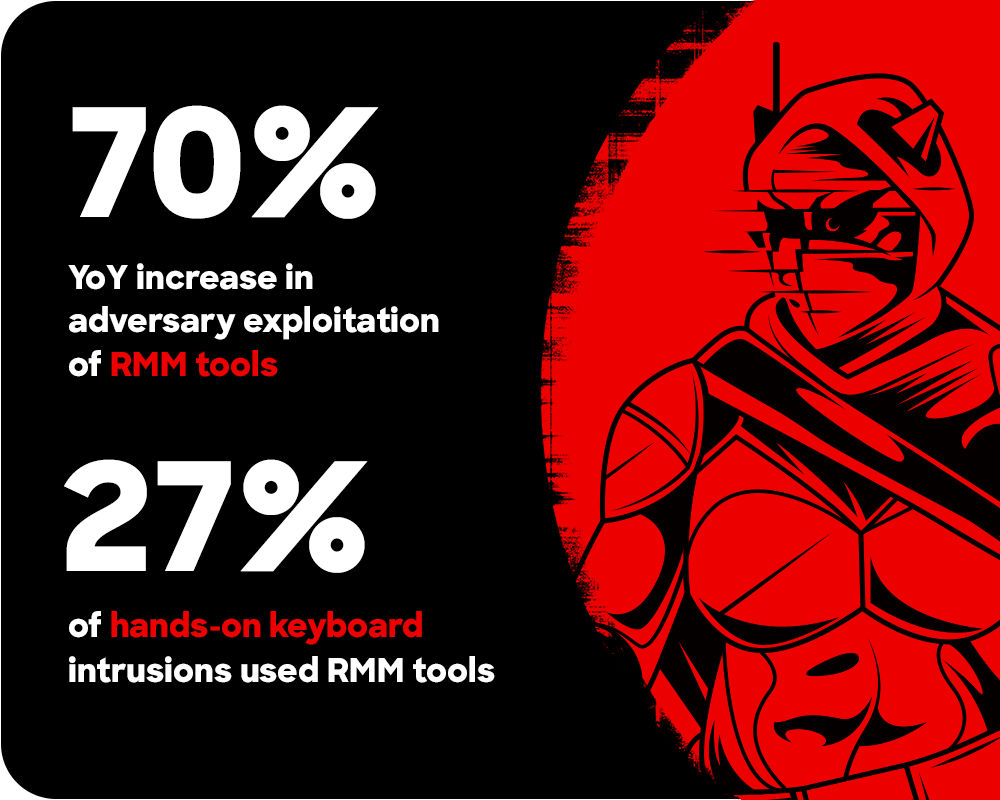
70% YoY increase in adversary exploitation of RMM tools
Threat hunting insights to outsmart
modern adversaries
The CrowdStrike 2024 Threat Hunting Report unveils the latest tactics of the 245+ adversaries we actively track. This year’s report shows how modern adversaries continue to evolve as they emulate legitimate user behavior — with 86% of hands-on keyboard attacks by eCrime actors seeking financial gain. They are also expanding their reach to execute cross-domain attacks across clouds, identities, and endpoints.
Read the CrowdStrike 2024 Threat Hunting Report
Cross-domain attacks and insider threats
are on the rise
Adversaries are executing cross-domain attacks, targeting identity, cloud, and endpoint domains. Most often, they use stolen credentials to break into the cloud and move laterally to endpoints. Cross-domain threats are prevalent among malicious insiders, who can log in and quickly compromise multiple domains.
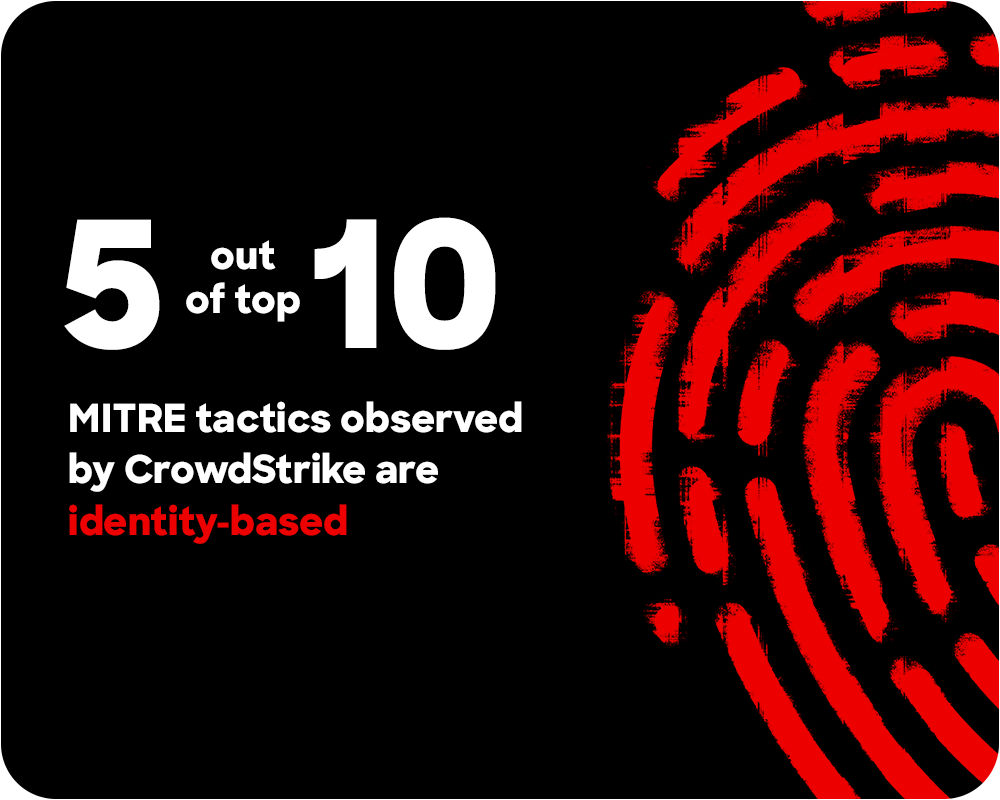
Legitimate credentials are exploited to gain easy access
Adversaries aren’t breaking in — they’re logging in with stolen credentials sourced from social engineering or access brokers. However, their misuse of valid accounts in suspicious ways creates abnormal patterns that help expert threat hunters shut them down, making human validation critical.
Adversaries are gaining full control of the cloud
As organizations move to the cloud, threats from adversaries like SCATTERED SPIDER intensify, leveraging spear phishing, policy modifications, and password manager access to infiltrate and exploit cloud environments. Penetrating the cloud control plane gives adversaries broad access and the capability to compromise the entire cloud infrastructure.

Endpoint attacks use remote monitoring and management (RMM) tools
The use of RMM tools for endpoint attacks surged by 70% in the past 12 months, accounting for 27% of hands-on-keyboard intrusions. Adversaries like STATIC KITTEN gain access with stolen credentials or phishing, then deploy RMM tools to blend in with legitimate operations. RMM-based attacks are here to stay, making it essential for protectors to continuously monitor these tools.
Know them. Find them.
Stop them.
Explore your threat landscape and find out which adversaries are
targeting organizations like yours in the Adversary Universe.




