Eliminate the next Log4J
Quickly identify and address critical vulnerabilities in software libraries, ensuring rapid response to zero-day threats.
CrowdStrike Falcon® Cloud Security
See everything in your cloud applications.
See a detailed bill of materials for every software dependency, proprietary, or open-source library that exists within your cloud applications or microservices.

Understand what critical vulnerabilities are loaded into memory and are reachable in your applications at run-time.
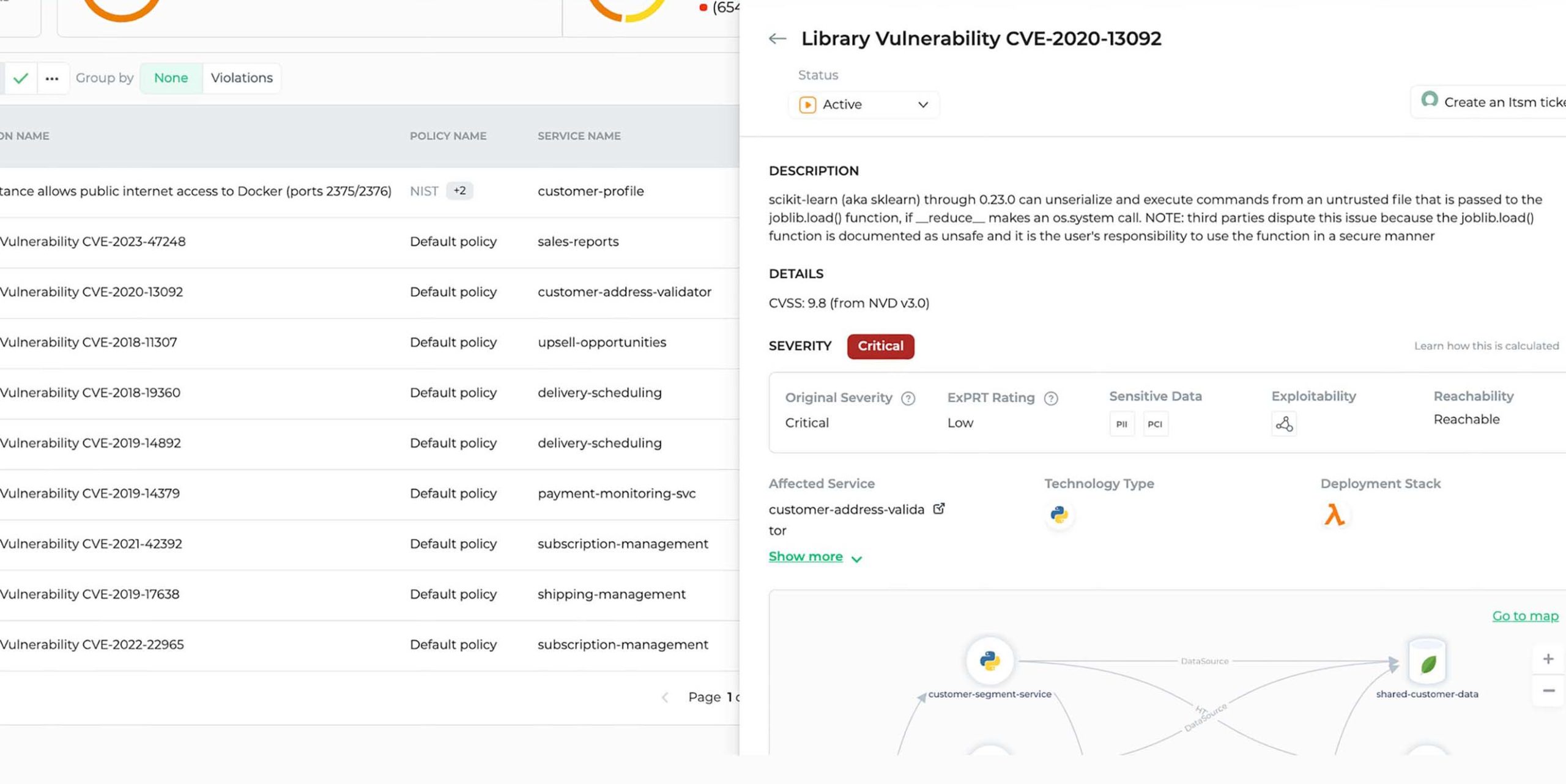
Efficiently manage and apply patches with a clear and simple overview of where software libraries are deployed.

Get transparency into the origin and maintenance history of software libraries. Know the risk of every open-source dependency, and share the threat landscape across your engineering teams.

Discover how CrowdStrike’s advanced protection can secure your cloud environment. No strings, no hassle.
Start interactive demo
Watch Falcon Cloud Security work
Enter the Falcon platform and see how we map your cloud attack surface, prioritize threats, and stop cloud breaches.