Accelerated response
Act on threats faster with actionable insights, minimizing damage and reducing downtime.
Threat Intelligence
Get the edge you need. Anticipate threats before they do harm.
Reduce the need for costly in-house research with expert-driven threat intelligence.
Get detailed insights into specific threats and vulnerabilities, helping your security team understand the full scope of potential risks. These reports cover a wide range of cyber threats, from emerging malware to sophisticated nation-state campaigns.
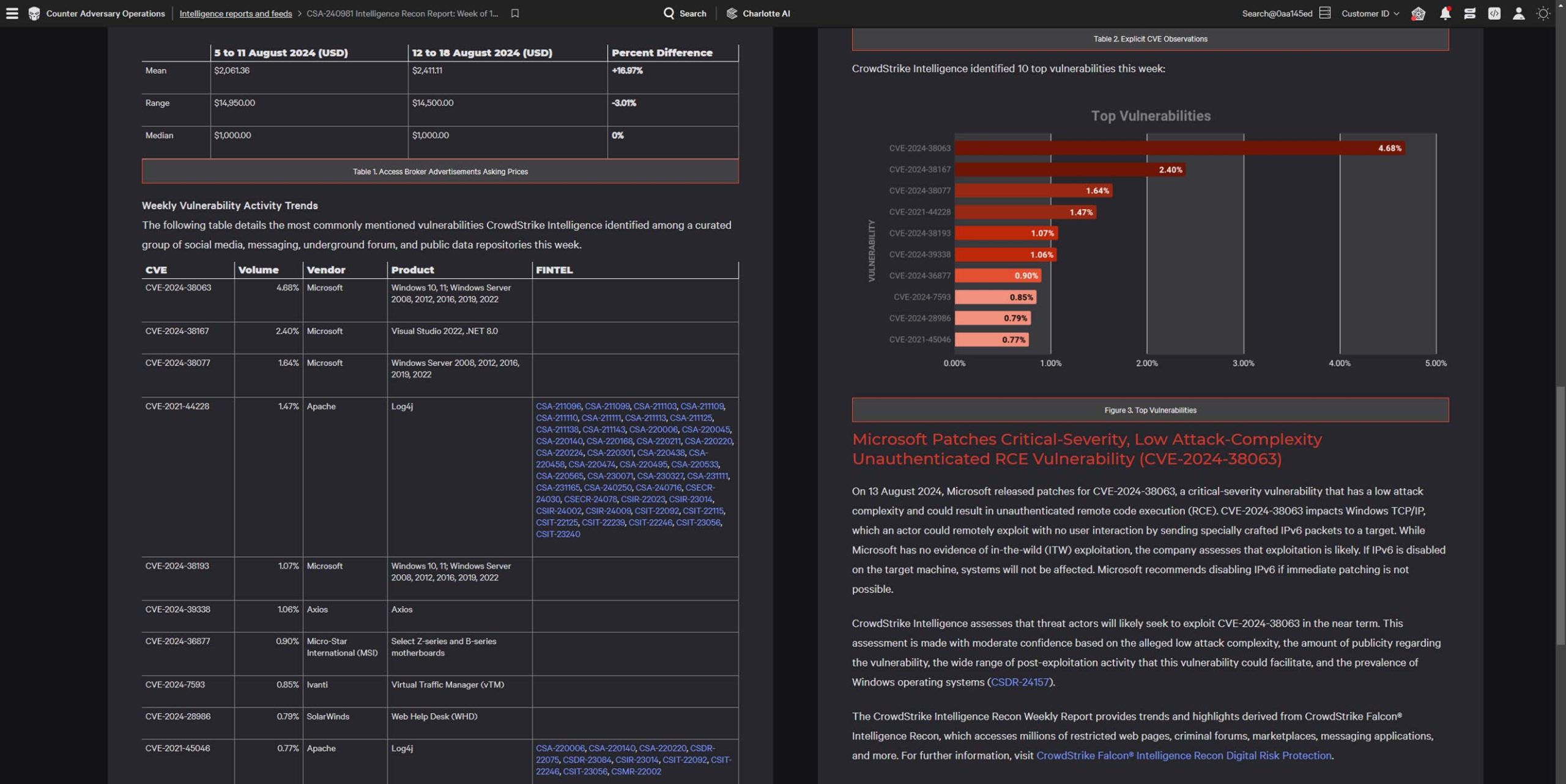
Learn about the adversaries targeting your industry. Each report includes profiles of key threat actors, outlining their motives, methods, and the sectors they frequently target, so you can better understand who you’re up against.
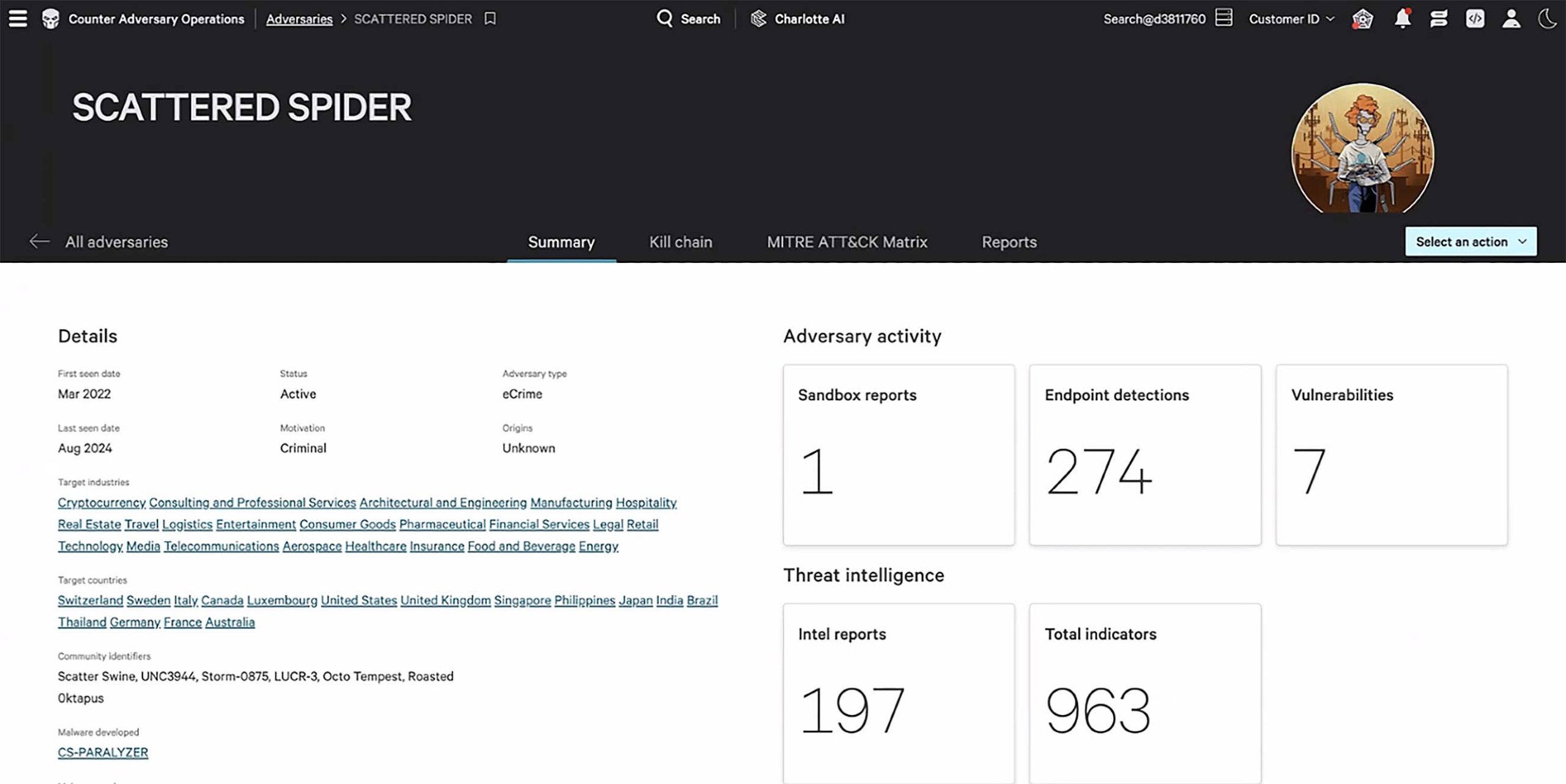
CrowdStrike doesn’t just identify threats — we tell you what to do about them. Each report comes with clear, actionable recommendations that your organization can implement immediately to enhance its security posture.

Whether you’re a CISO, security analyst, or IT manager, these reports are tailored to provide both strategic and tactical insights. From high-level overviews to granular details, you’ll get the intelligence you need to make informed decisions at every level.

CrowdStrike understands that every industry faces unique challenges. That’s why our reports are tailored to the unique needs of your sector, providing relevant, industry-specific insights that help you stay ahead of the threats most likely to target your organization.
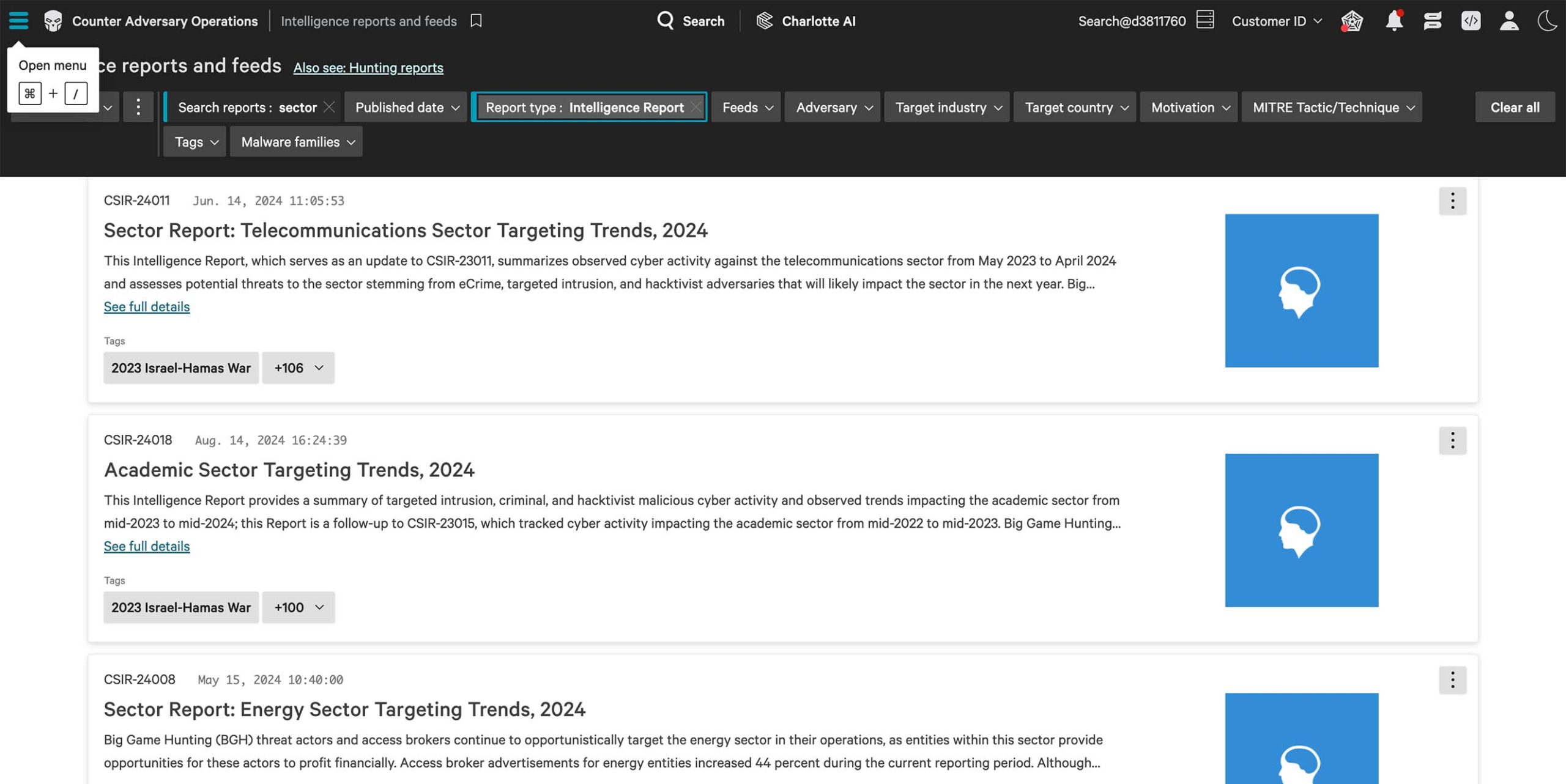
Adversaries behind BEC attacks use phishing and social engineering to infiltrate email systems and impersonate key personnel or vendors. Prevent BEC attacks with concise reports that reveal attacker tradecraft and stop fraud before it starts.
