Adversary Intelligence – Typosquatting

Introduction
Malicious actors leverage a technique called typosquatting to trick users into believing a falsified domain is legitimate. The fake domain can be used to trick users into visiting malicious site or trusting an email that they have received.
CrowdStrike Falcon Intelligence Recon provides the ability to monitor for when key terms are identified in newly created or changed domains. This can be used to monitor brands or identify when a fraudulent domain is being used.
Let’s take a look at how CrowdStrike’s typosquatting capability works.
Walkthrough
In the Recon monitoring rules, CrowdStrike provides the ability to evaluate key terms within domains as they are created or modified with the typosquatting topic.
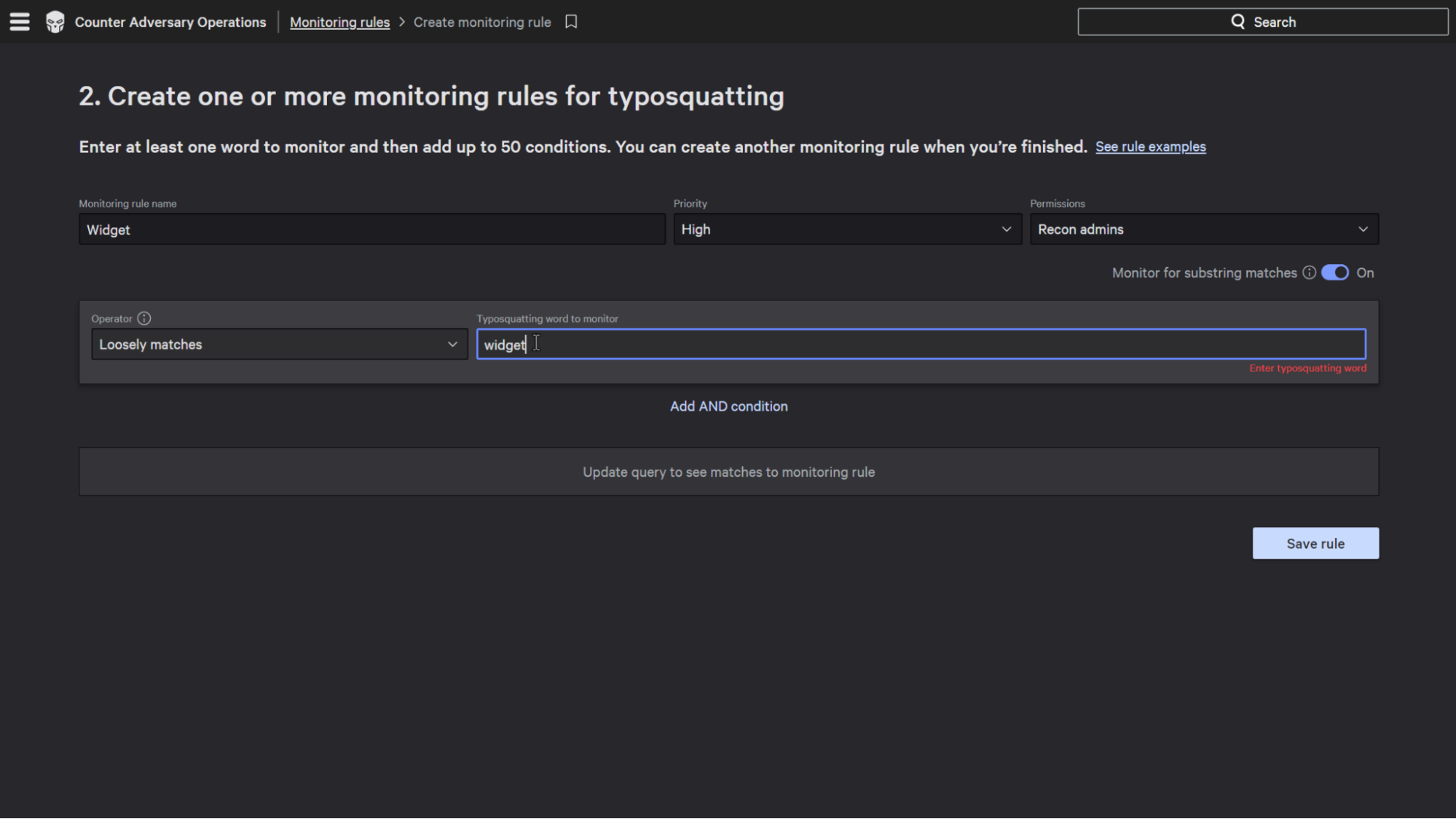
After we create the new rule, we can give the rule a name, set the priority within the notifications, and configure the permissions.
There are also a few options available to further hone our search for domains.
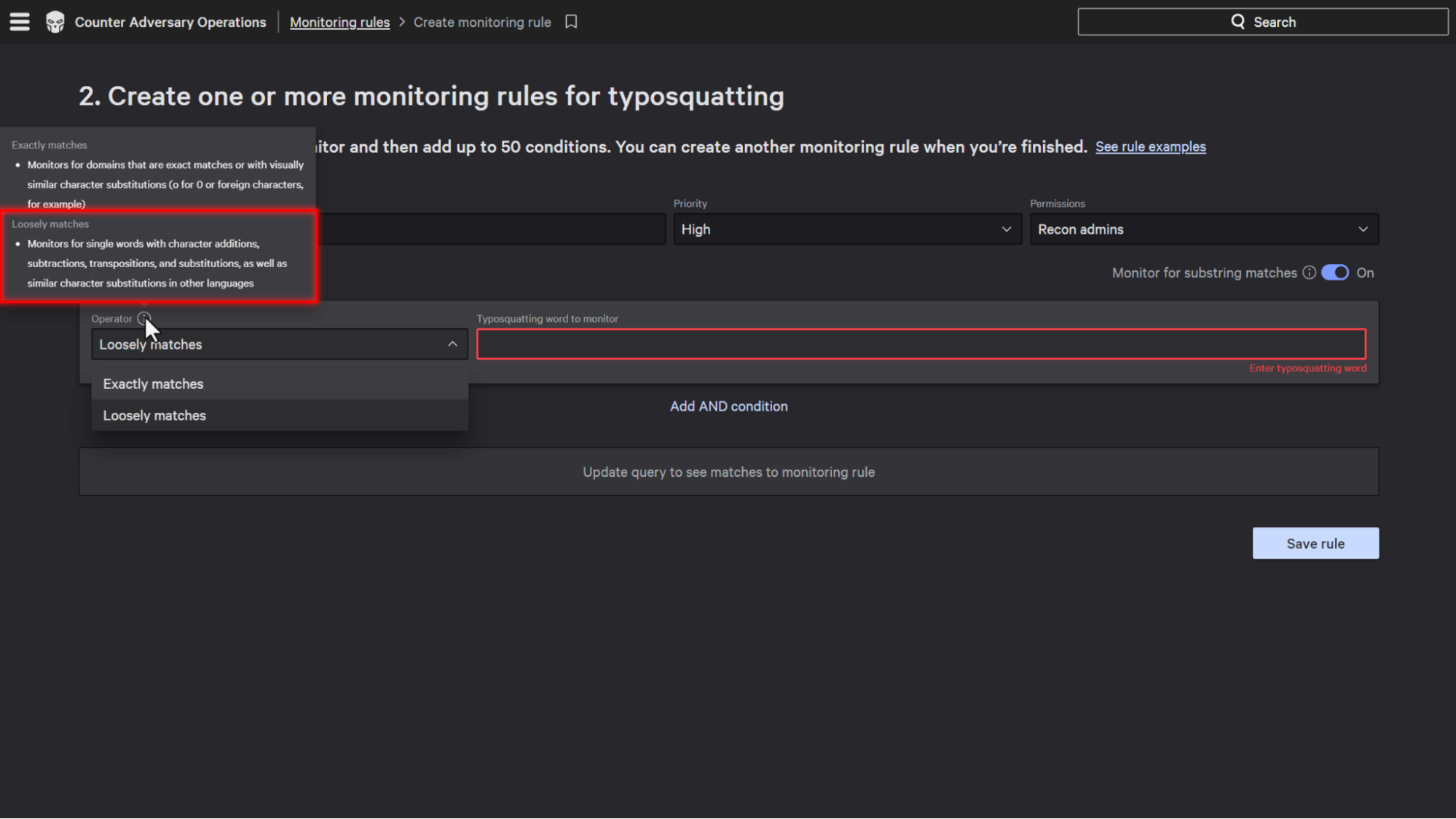
The Operator can be configured so that the key words have to be exactly matched or loosely matched.
If the key words are configured to be exactly matched, that means what it sounds like and the key term will be matched exactly.
If it is configured to be loosely matched, that includes terms with character additions, subtractions, transpositions, and substitutions.
It also includes character substitutions in other languages and character sets as well.
This will help identify domains that might look similar or identical to the key term being searched, but is actually a completely different domain.
There’s also the ability to configure the substring matches. When it is enabled, it will only provide results where the term doesn’t span across a period within the domain.
We can also add an and condition as well as an or condition to further refine our rule to identify multiple domains.
An email notification can also be sent out to notify you when the key terms have been found.
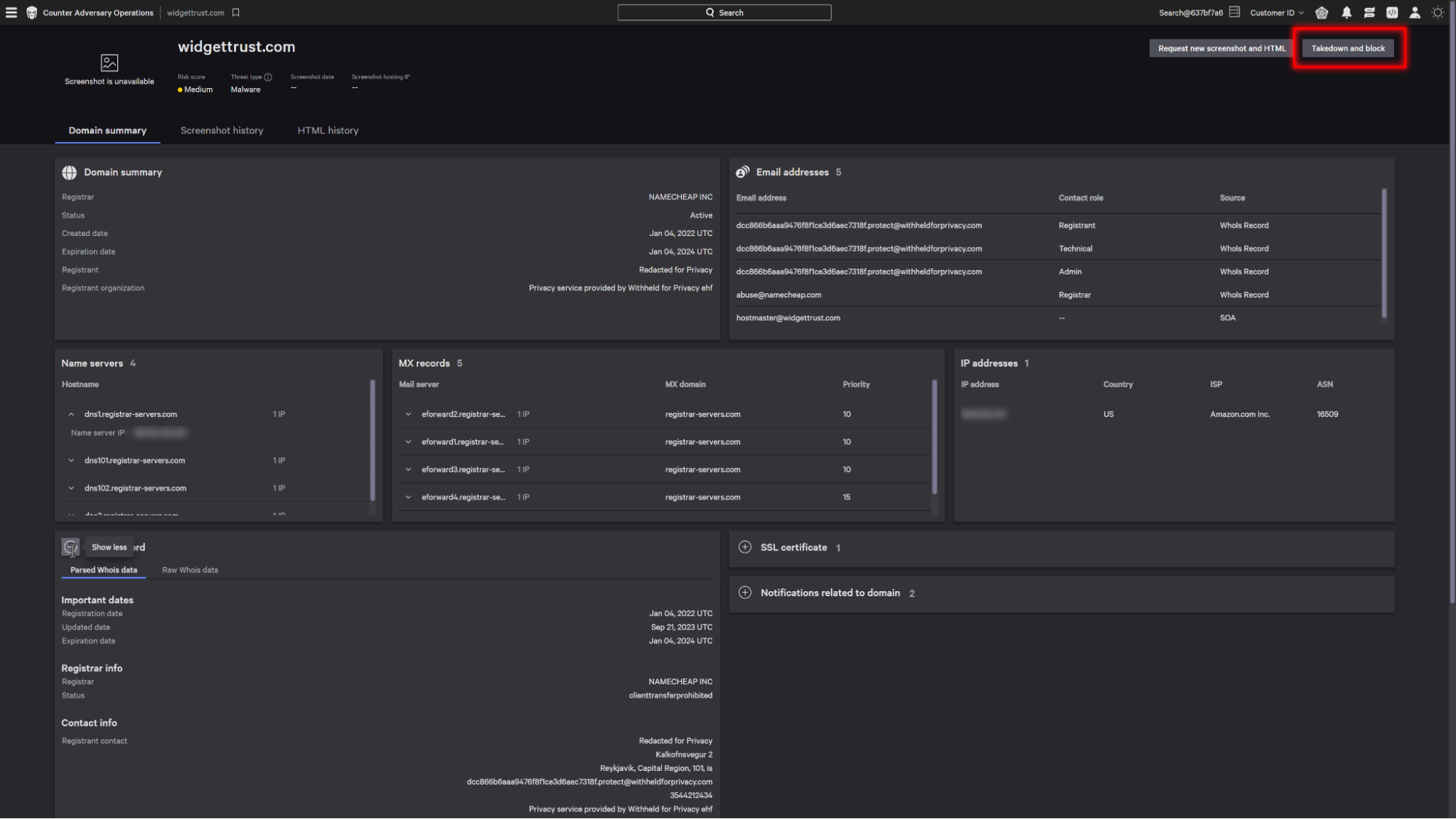
Going to our notifications screen, we can see all the domains found to match our rules.
Taking a closer look at one of the identified domains, we can see a quick snapshot of the whois summary.
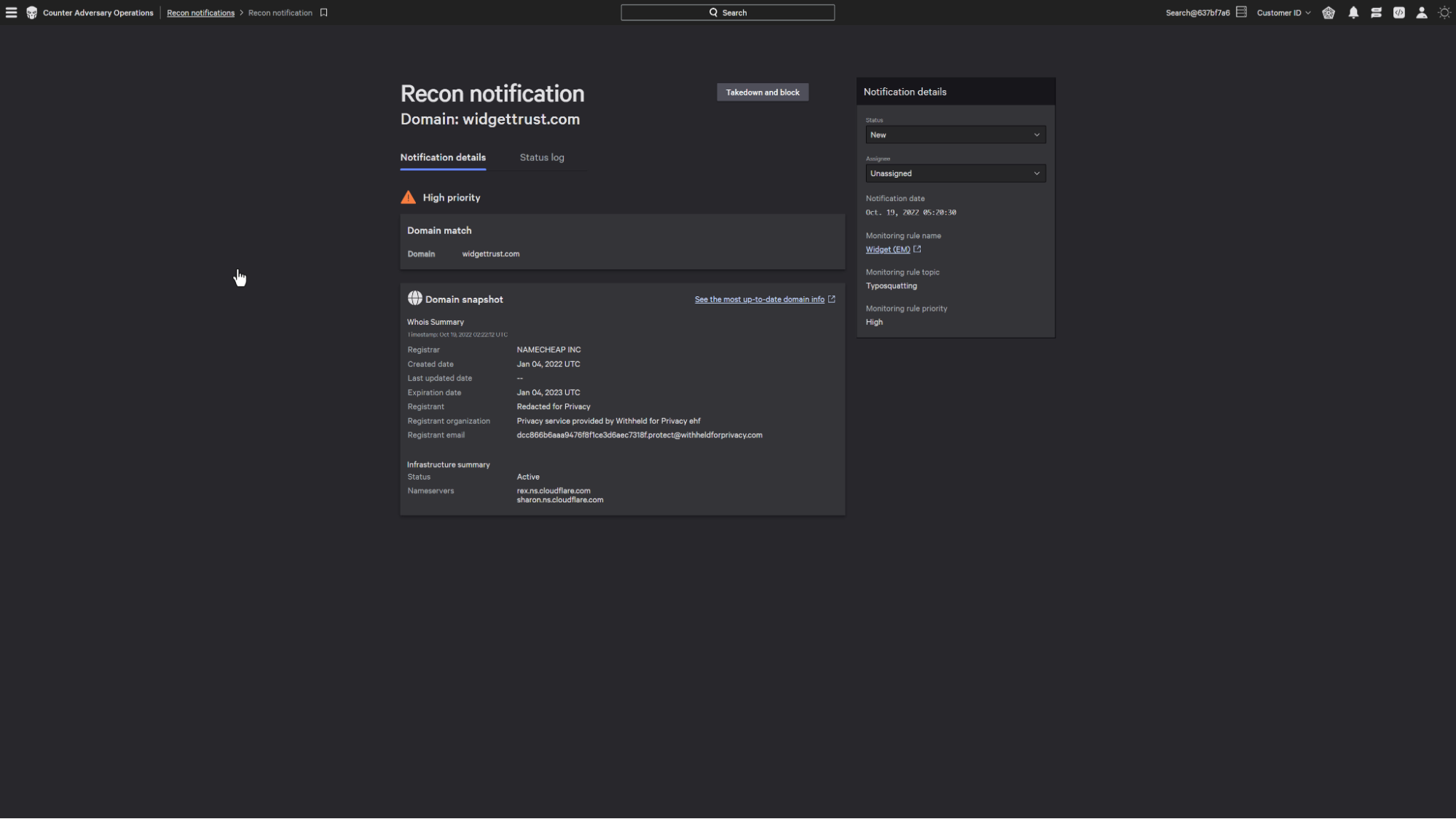
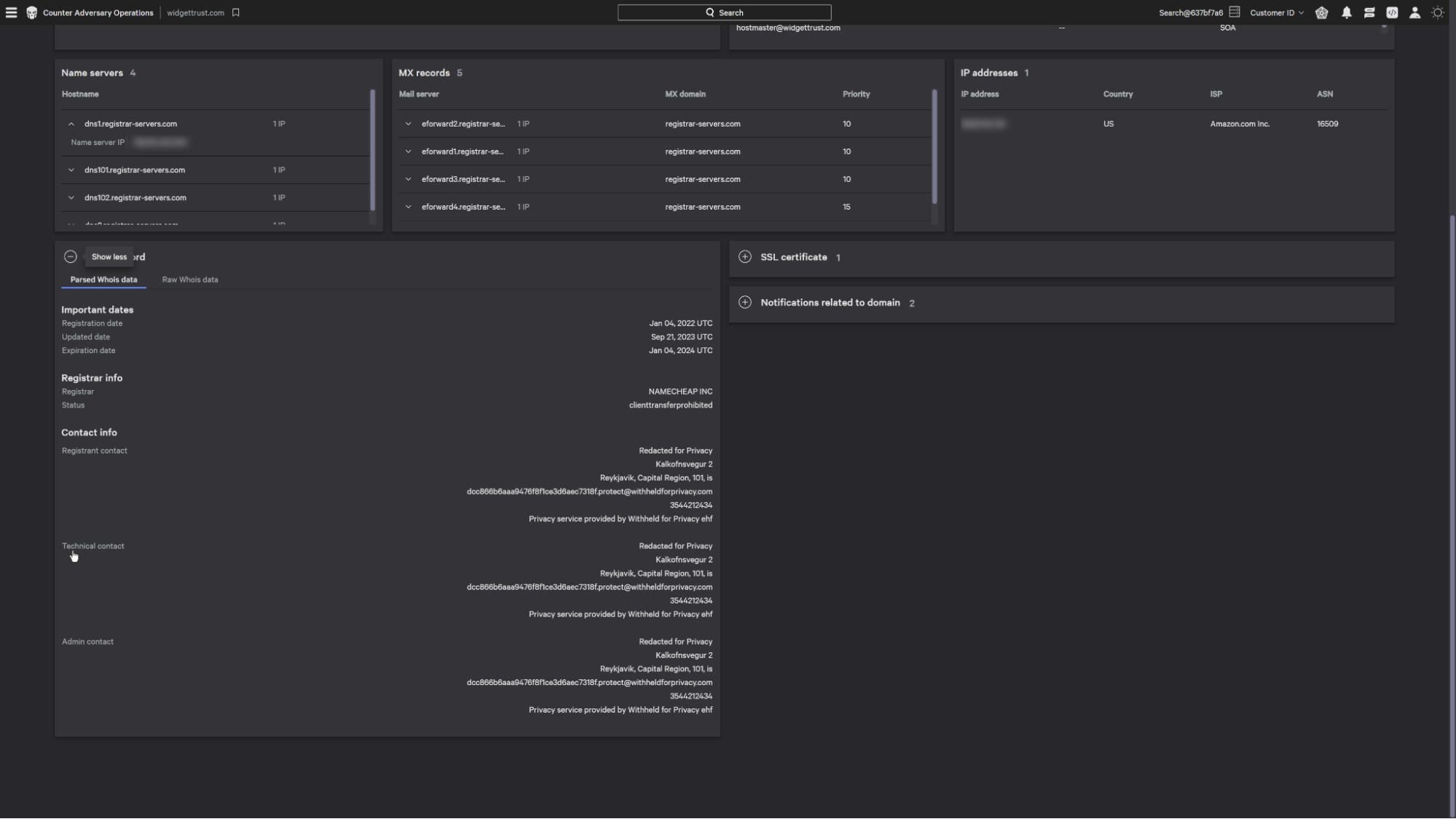
This provides information such as the name servers and mx records associated with the domain. These can be expanded to show the connected ip address.
Also available are detail parsed whois information as well as the raw whois data.
When we’ve identified this domain as being malicious, there’s a button on the page to report the domain to a blocklist as well as request a takedown.
The blocklist will report it as unsafe to industry blocklists and CrowdStrike partners in order to prevent users from interacting with it, while a takedown will report it to infrastructure-providing organizations to remove it from the internet.
Here we have a rule where the terms are loosely matched and substring matches are disabled.
These domains look similar to widget, but have letters moved around or added. This can help find domains that are trying to impersonate other domains.
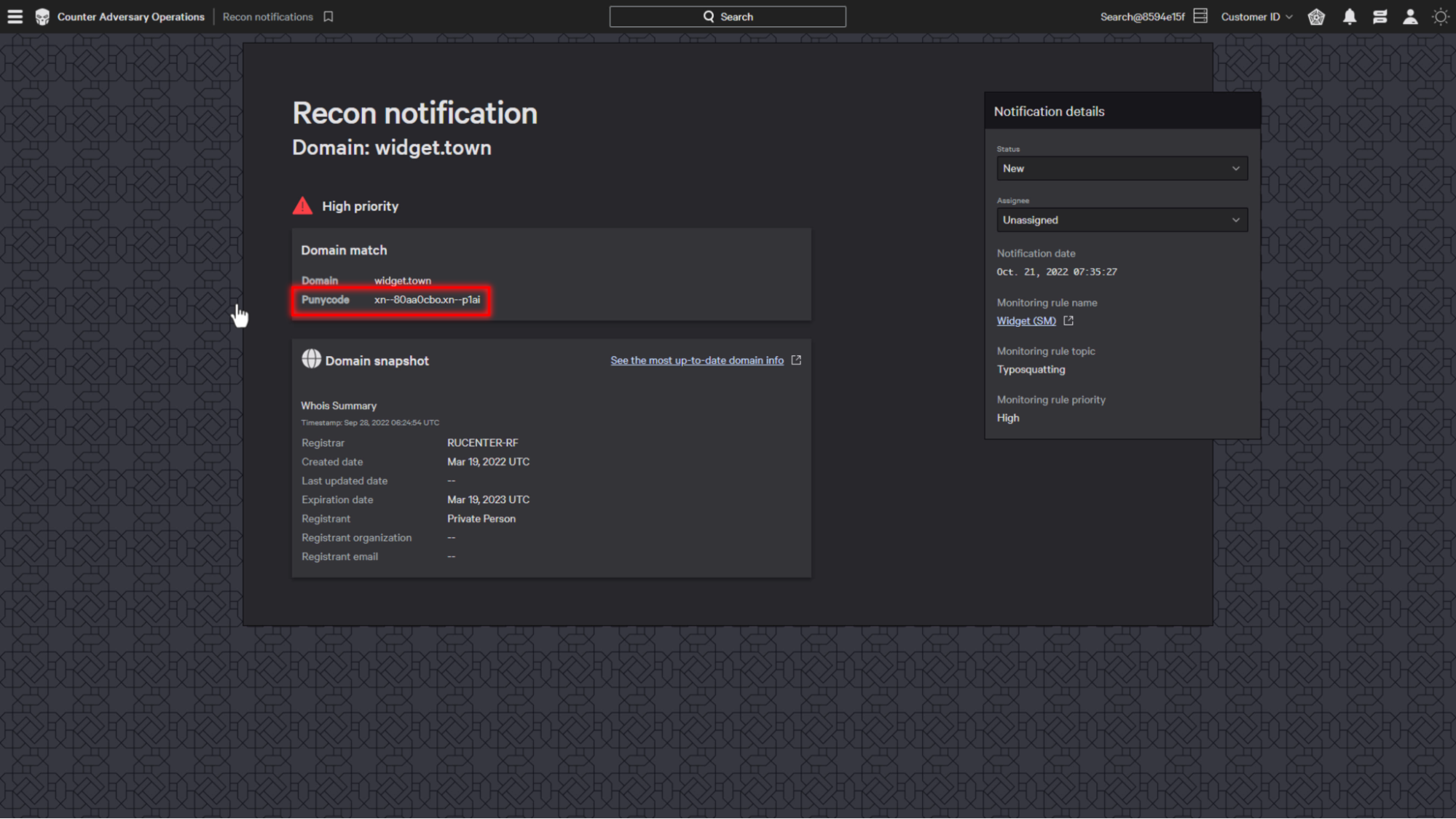
For example, here we have a domain that looks like it’s related to widgets.
When we look at the details, we can see that the punycode stored by the dns registrar is different from what we would see in the browser.
This domain is using a non-ansii character set so even though it looks like the characters widget, when we do a search for that string in the browser we can see that it only finds the rule name and not the domain.
CrowdStrike Falcon Intelligence Recon with typosquatting provides a powerful way to identify when a domain is potentially being hijacked and allows you to take actions to protect your brand and your users.