Adversary Intelligence – Recon Search

Introduction
Criminal underground digital economies are hidden throughout the recesses of the internet. To find the activity of these malicious actors, not only do you need to search the open web, but the deep web and dark web as well.
CrowdStrike Falcon Adversary Intelligence enables organizations to better protect their brand, employees, and sensitive data by allowing security teams to easily conduct investigations of underground activity.
By empowering security teams to conduct investigations in real time, they can proactively uncover fraud, data breaches, phishing campaigns and protect their brand from other online threats that target their organization.
Let’s go ahead and take a look at Falcon Adversary Intelligence.
Walkthrough
For our demonstration, let’s assume that we are an electric power company and we currently want to know if any of our data is being sold in an underground data market.
We can do a search with Falcon Adversary Intelligence by using the centralized search in the Falcon Console at the top. This search can also search across the entire Falcon Platform, but we’re going to focus on the Recon Intelligence results.
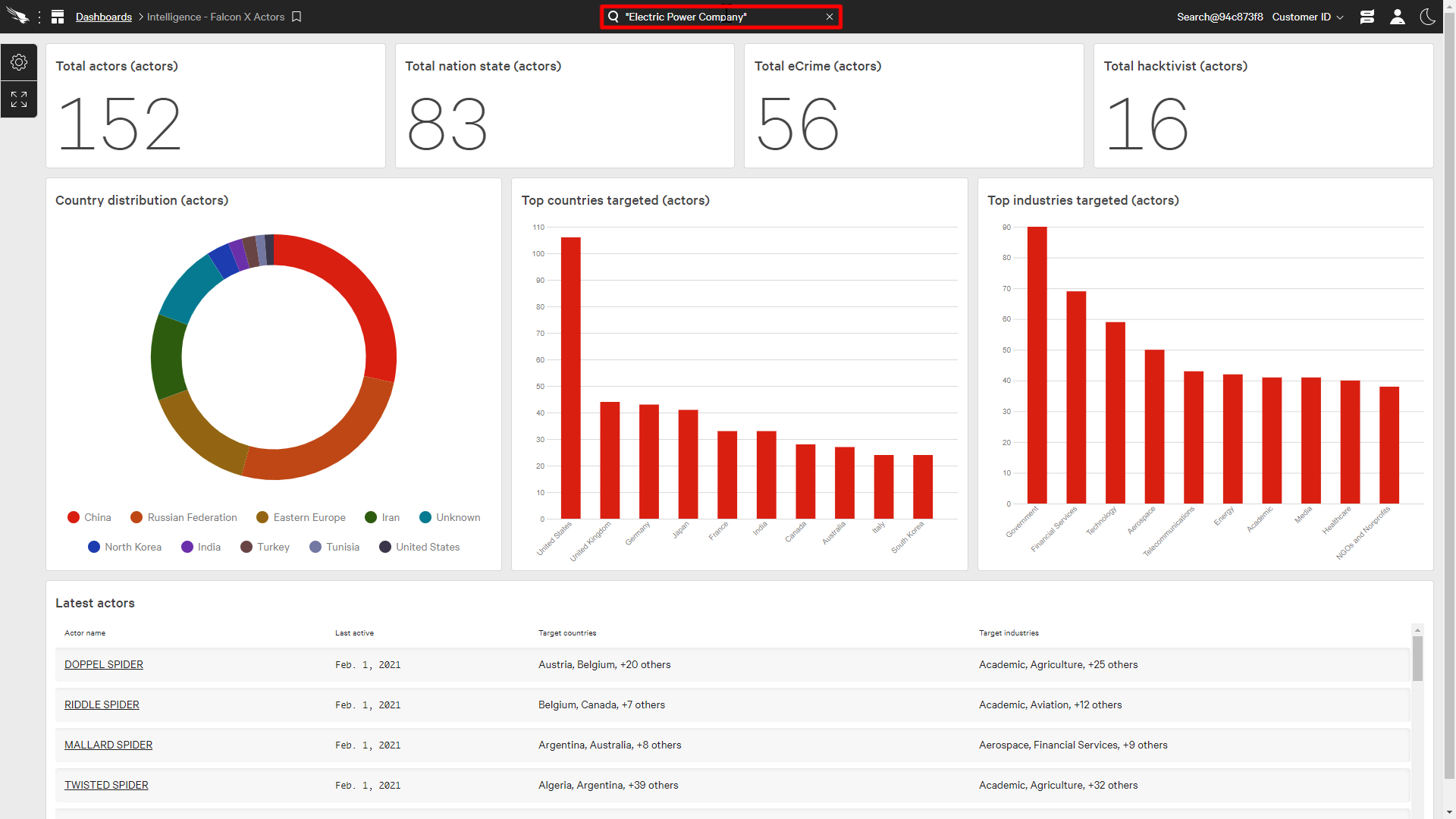
After the search of Recon Intelligence is complete, it will pull up all the relevant data found across the open, deep, and dark web.
Filters are available to narrow down our search to just the data we’re interested in. Here we’ll just focus on the commerce category, which is the buying and selling of data.
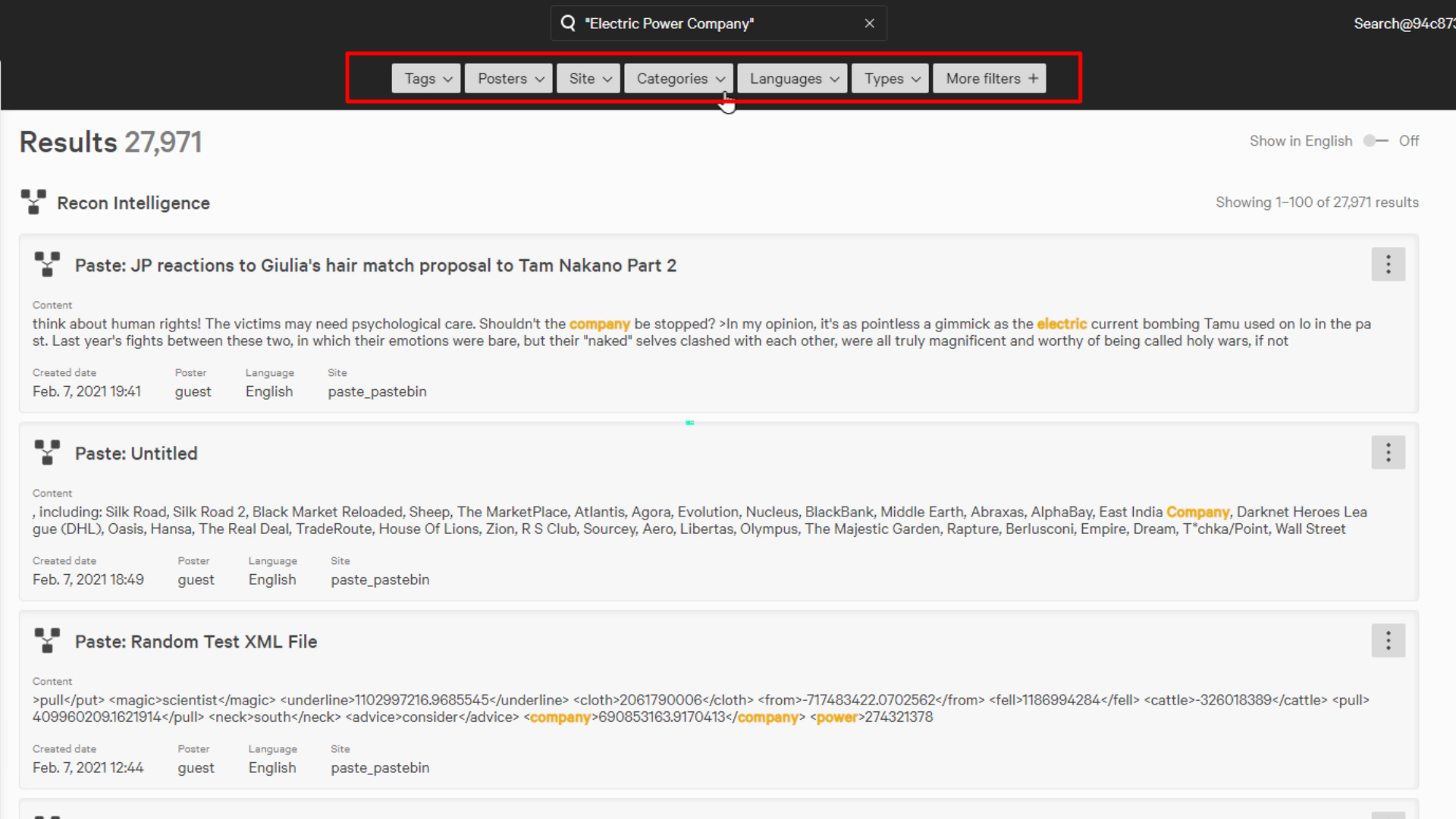
This post describes the organization, type of credentials, and cost of the data. We can also go to the details page which can provide more information.
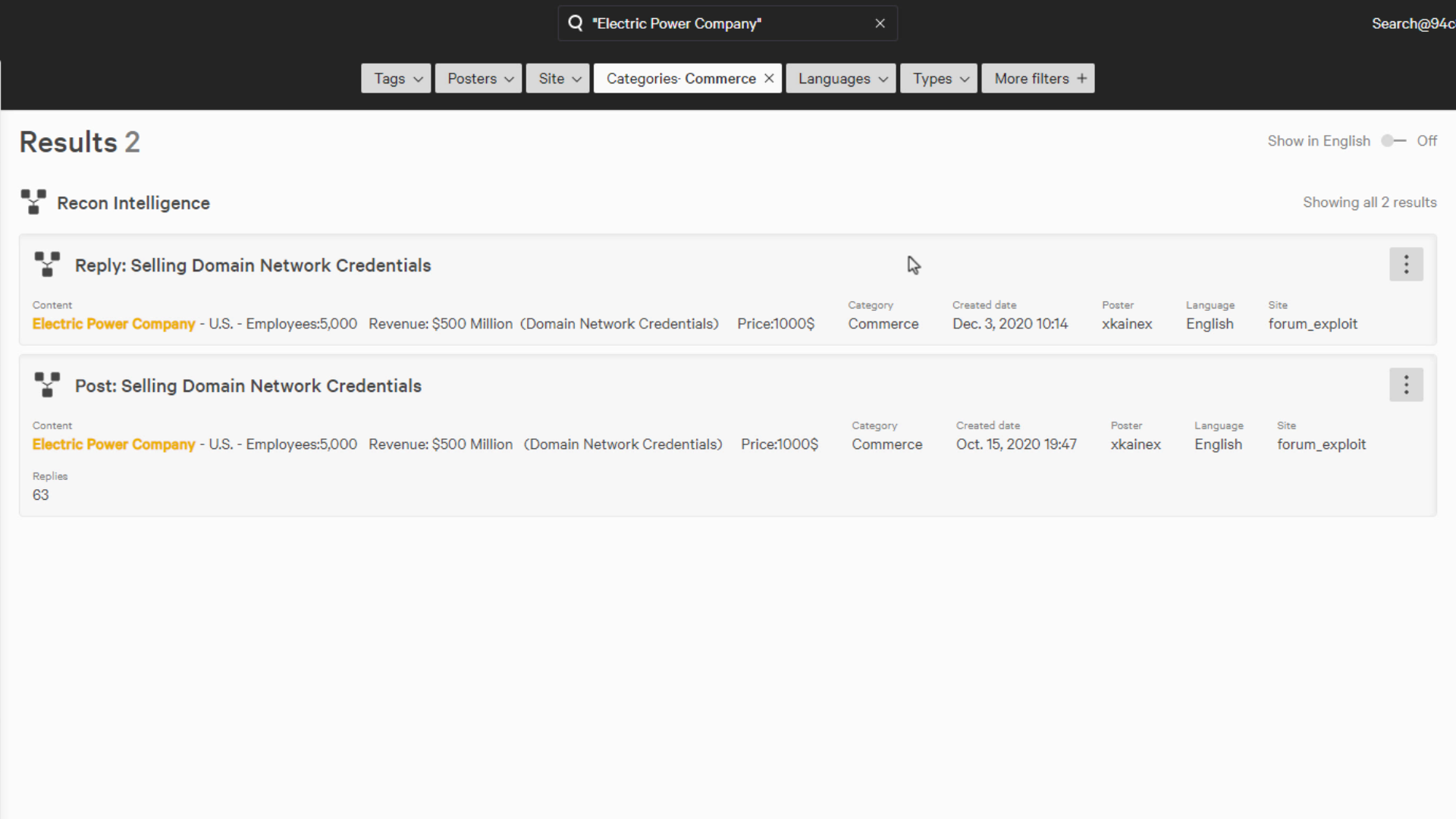
Armed with this discovery, we can decide if it is relevant to us and determine the best course of action.
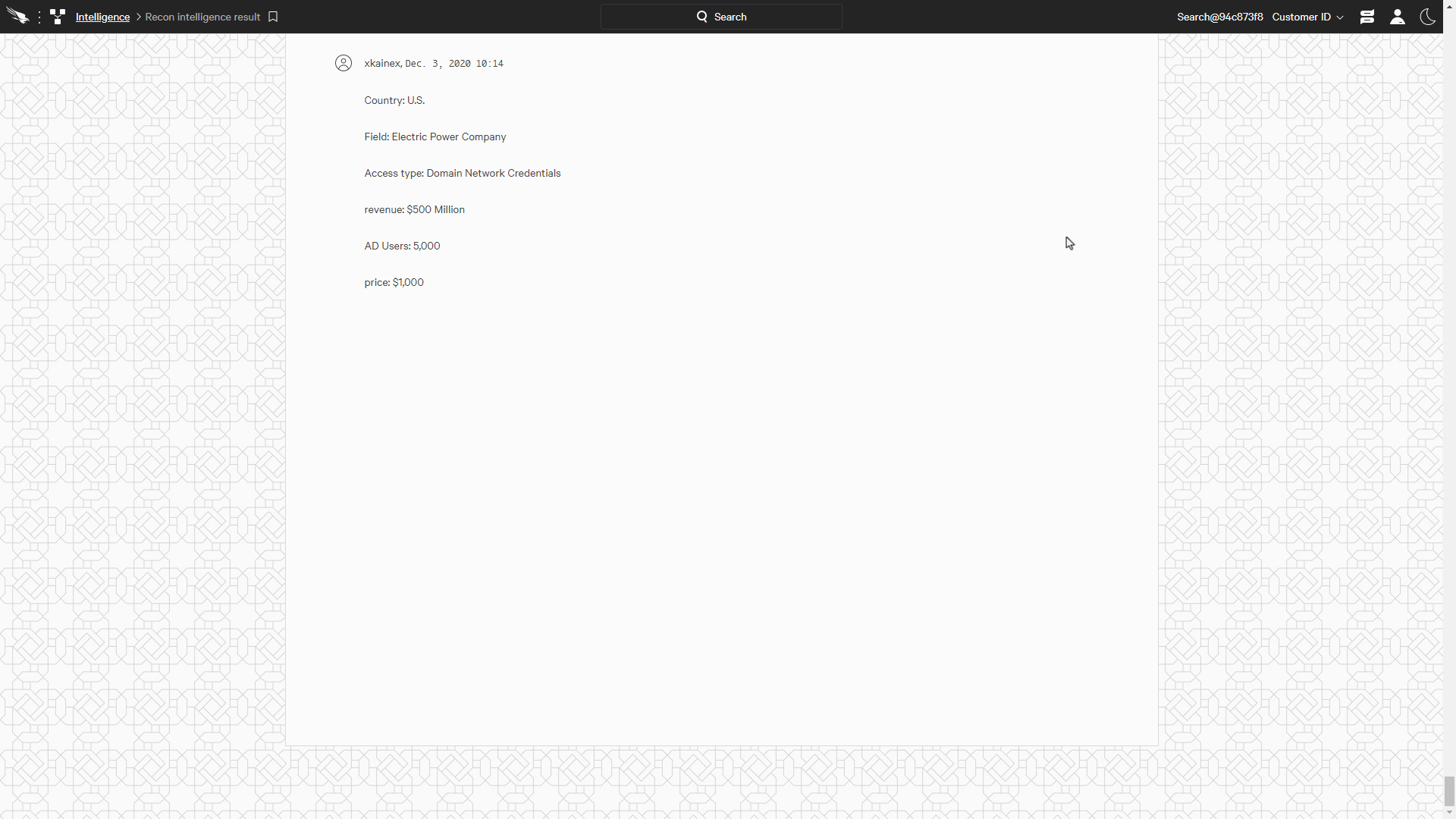
We can see that this data here is from a power company in the US with revenue of 500 million dollars, and 5000 domain network credentials are for sale.
Falcon Adversary Intelligence can also provide results to other types of searches as well, for example, if a new attack is trending in the media or if a CISO is interested in a specific threat.
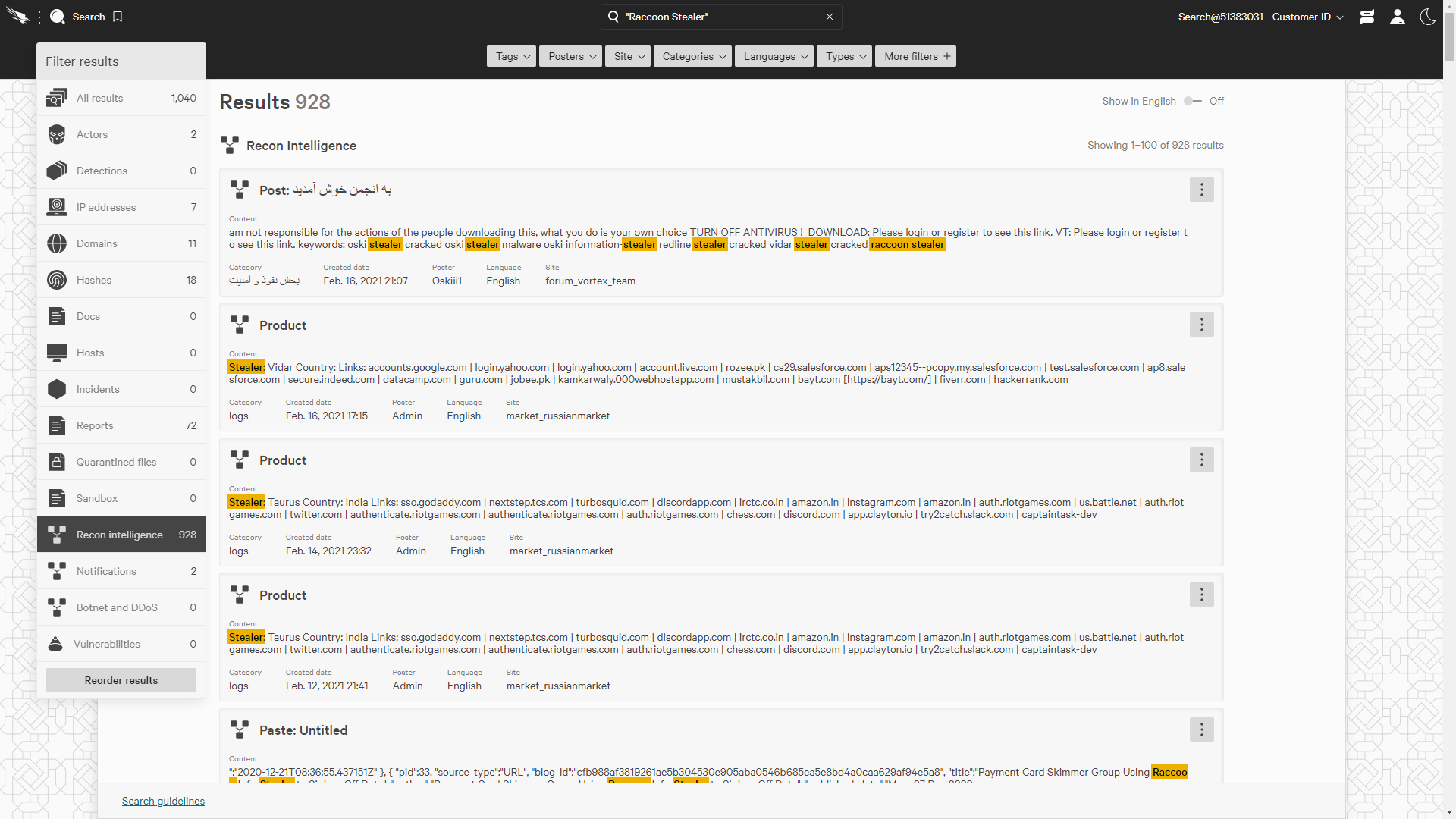
For example, let’s do a search for “raccoon stealer”, a malicious information gathering tool.
We can see a lot of results for this threat in Recon Intelligence. Let’s take a look at all the results for Raccoon Stealer.
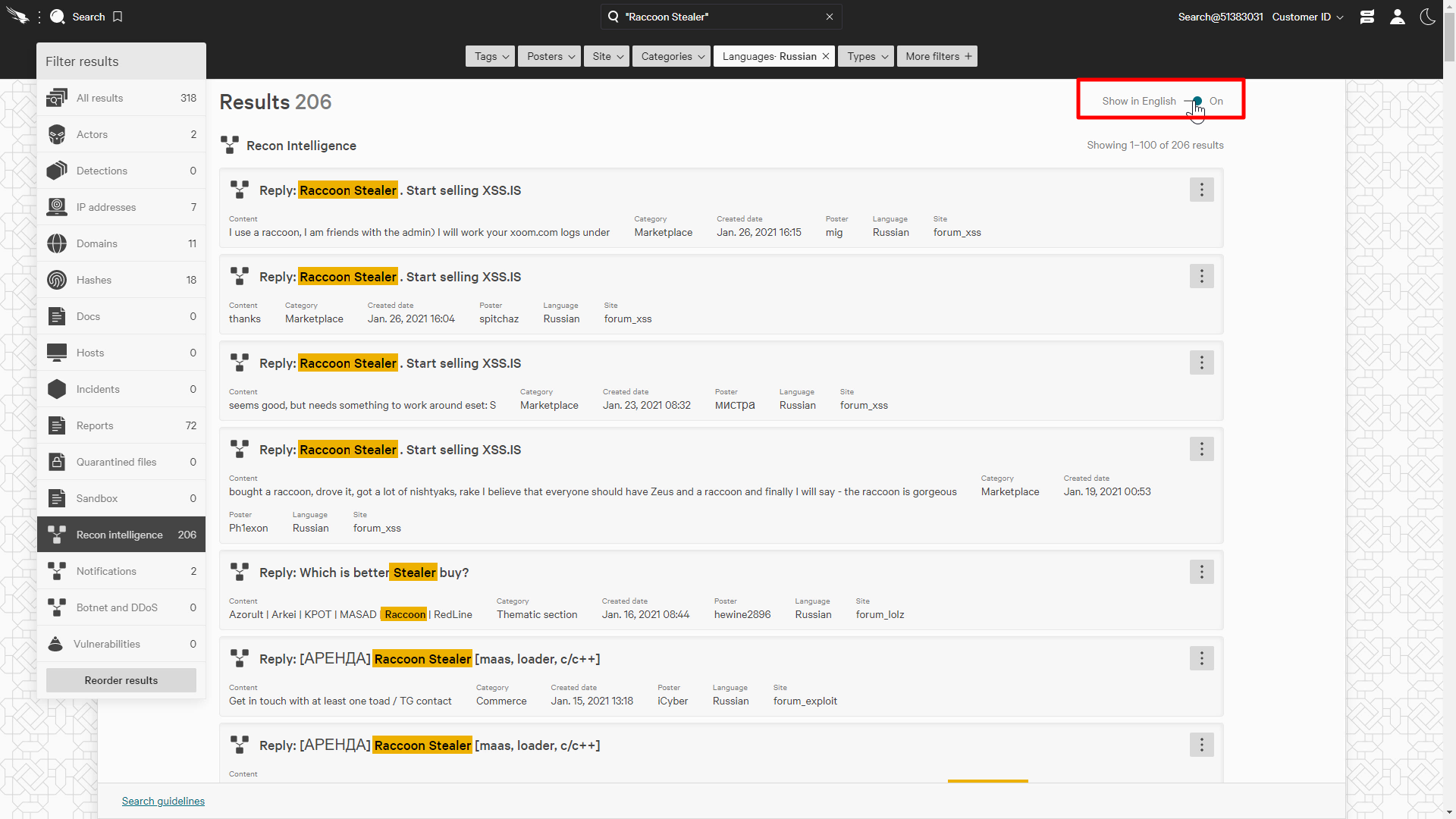
Oftentimes posts will be in a foreign language. Let’s see what the other side of the world is saying about this threat.
Using the filters again, we can filter the language to Russian which will limit our results to just Russian.
Many organizations don’t have an in-house foreign language translator for security, but we can use the translate toggle to automatically translate the contents into english.
The translator is augmented with hacker slang to enable a more accurate translation, This provides the security teams the capability to analyze the message even if it was originally written in a foreign language.
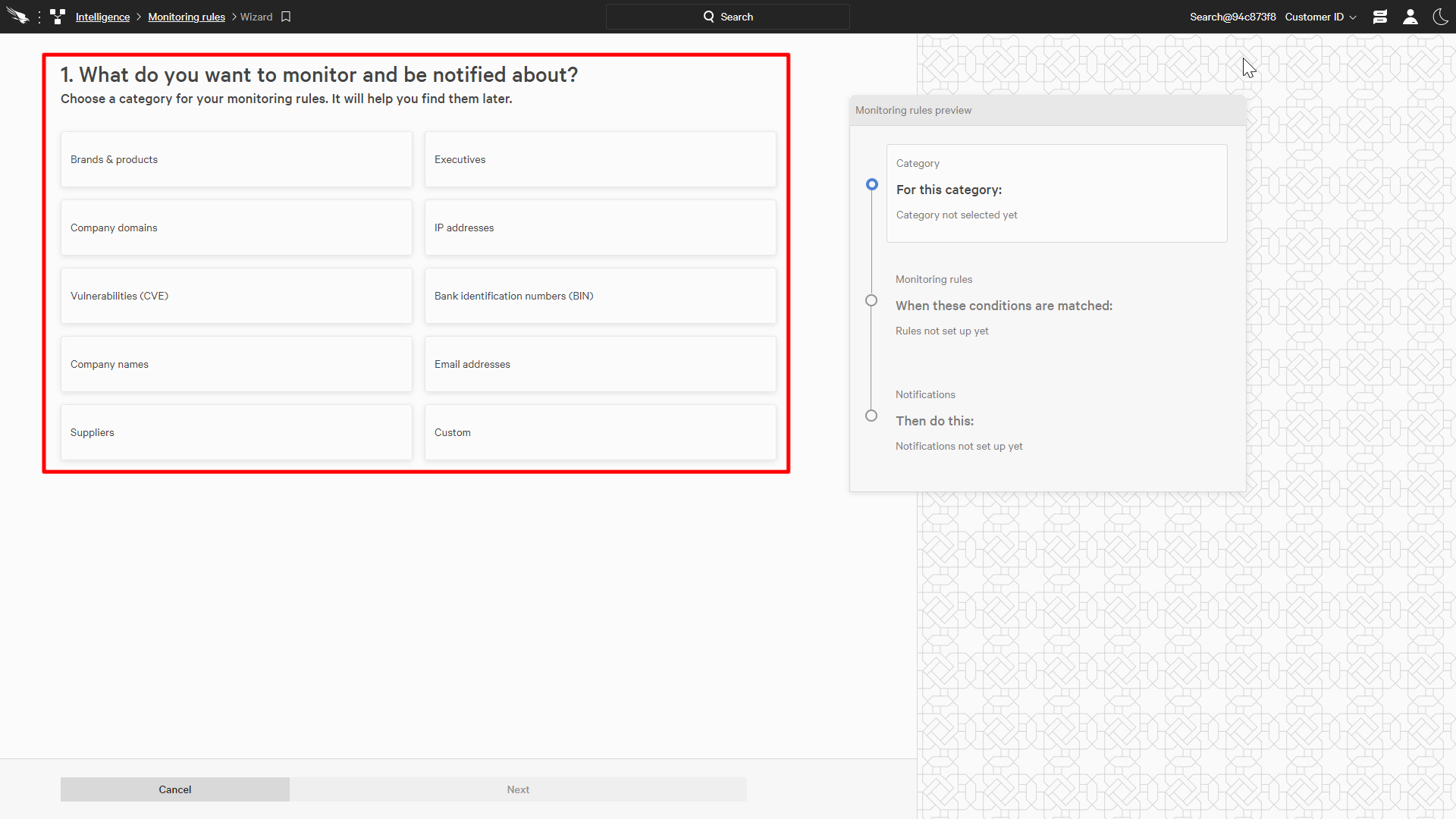
In addition to real time searches, we can also create monitoring rules that will automatically send notifications when certain criteria are detected. This allows security teams to streamline their security processes with customized notifications and increase the speed of their responses.
The monitoring rules provide topics for multiple categories of detections. This will allow you to focus your findings and triage the relevant data to the appropriate teams, even if they are outside of the security team.
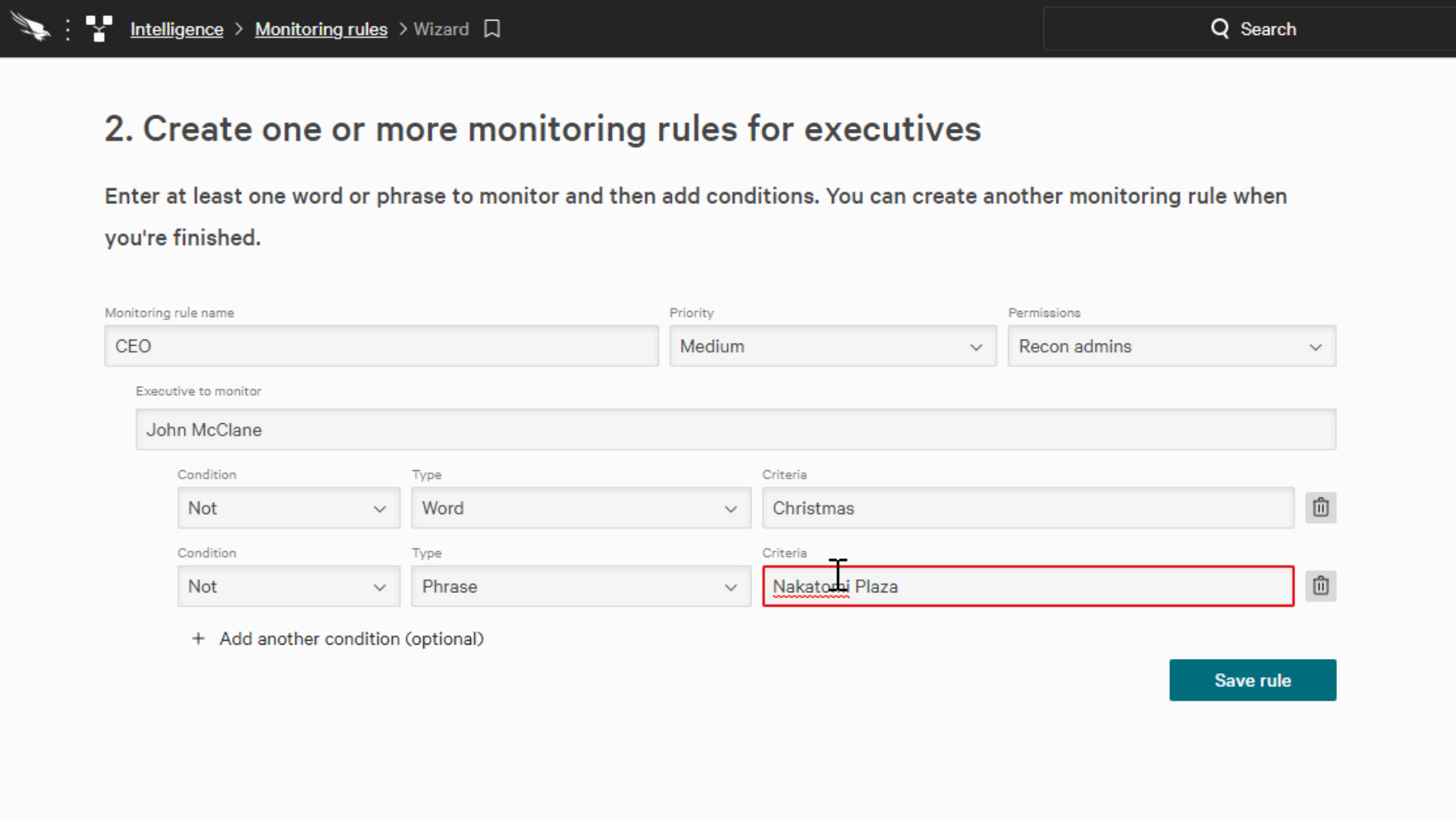
Taking a look at the “High-profile employees” category, we can provide the name of an executive that we would like to monitor.
When the executive’s name surfaces, even if it’s on the deep and dark web, a notification will automatically be sent to the appropriate team.
We can also add additional and/or conditions to ensure that the search terms aren’t too broad causing us to receive too many irrelevant notifications.
John McClain
And
Nakatomi plaza
Or
Christmas
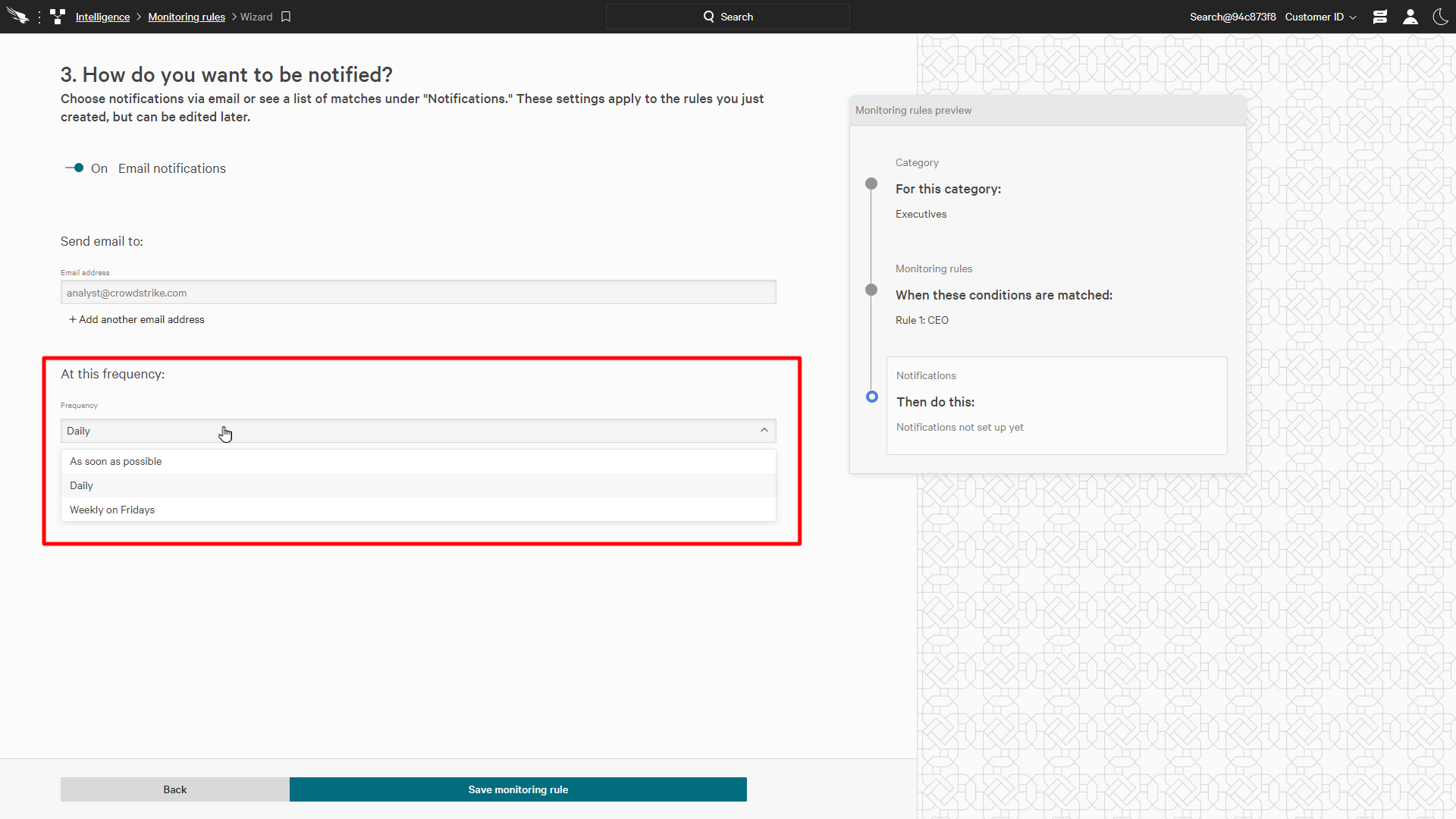
You can designate a list of recipients to receive the email and these can be delivered immediately or scheduled for a daily or weekly digest of alerts.
Taking a look at one of the other available topics, customized notifications allow for alerts with specific criteria to be generated.
Templates that provide rules created by security experts are also available to quickly create notifications, like this rule that finds new hacking tools being discussed on these underground channels.
For this example, we’ll generate notifications anytime the phrase “Electric Power Company” is seen so that we can proactively identify potential threats.
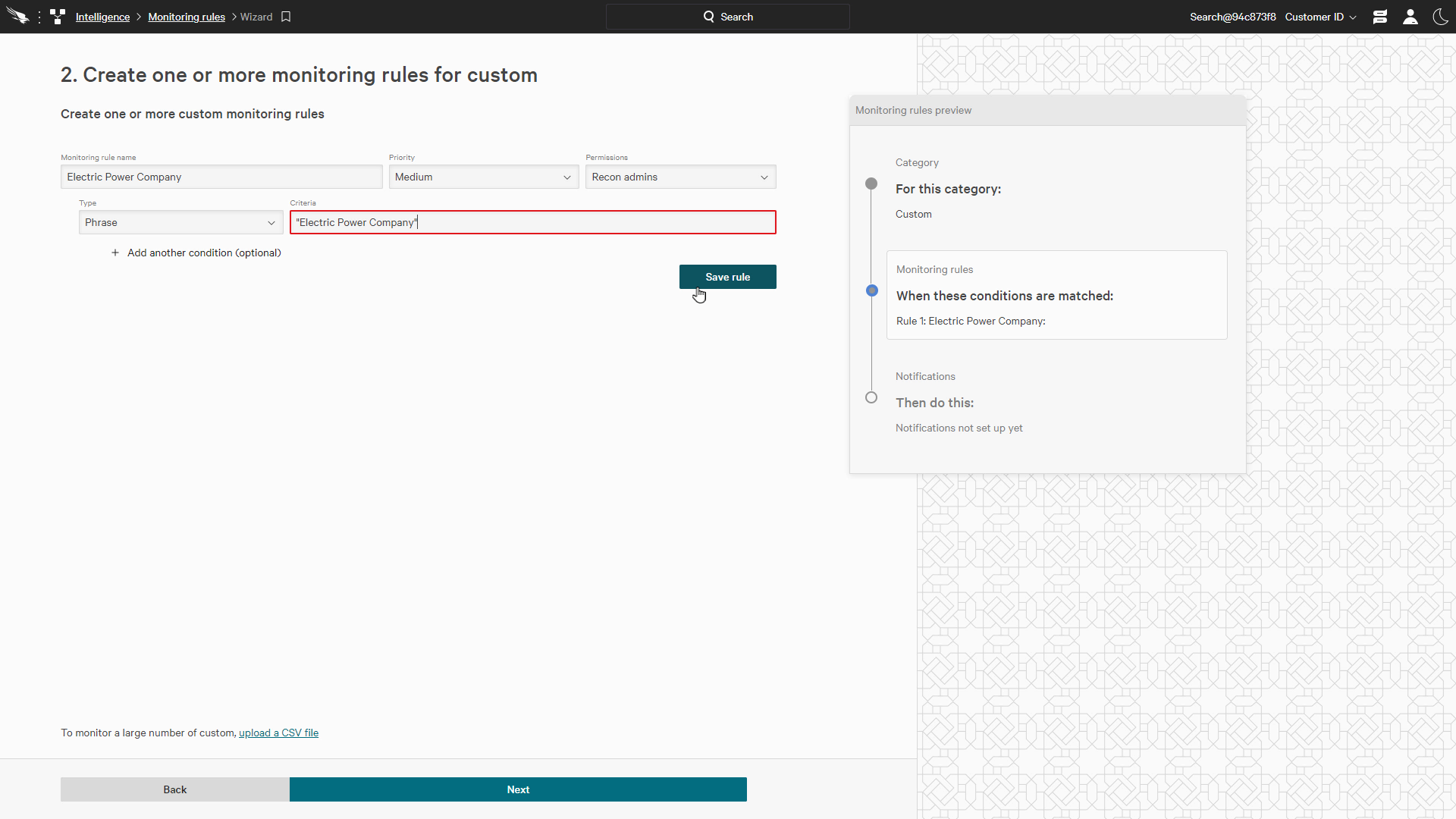
We can use any relevant criteria here giving us lots of flexibility to find exactly what we’re looking for to protect our organization.
CrowdStrike Falcon Adversary Intelligence is the premier tool for digital risk reconnaissance. With continuous monitoring that goes beyond just the open web, security teams can easily search restricted underground activity and identify threats to the organization.
With Falcon Adversary Intelligence in their arsenal, it allows them to protect their brand, discover data leaks, monitor supply chains, and protect executives.