Falcon Adversary Intelligence

Introduction
As attacks increase in sophistication, security teams need additional threat intelligence to prevent, detect, and respond to threats.
CrowdStrike Falcon Intelligence automatically performs incident investigations by analyzing malicious activity and enhancing detections with threat intelligence so security teams can make better, faster decisions. Let’s see how.
Walkthrough
CrowdStrike tracks over 215 nation-state, eCrime and hacktivists. Each profile exposes the motivation, tactics and techniques of the attacker – the more you know about your attack, the better you can protect your business.
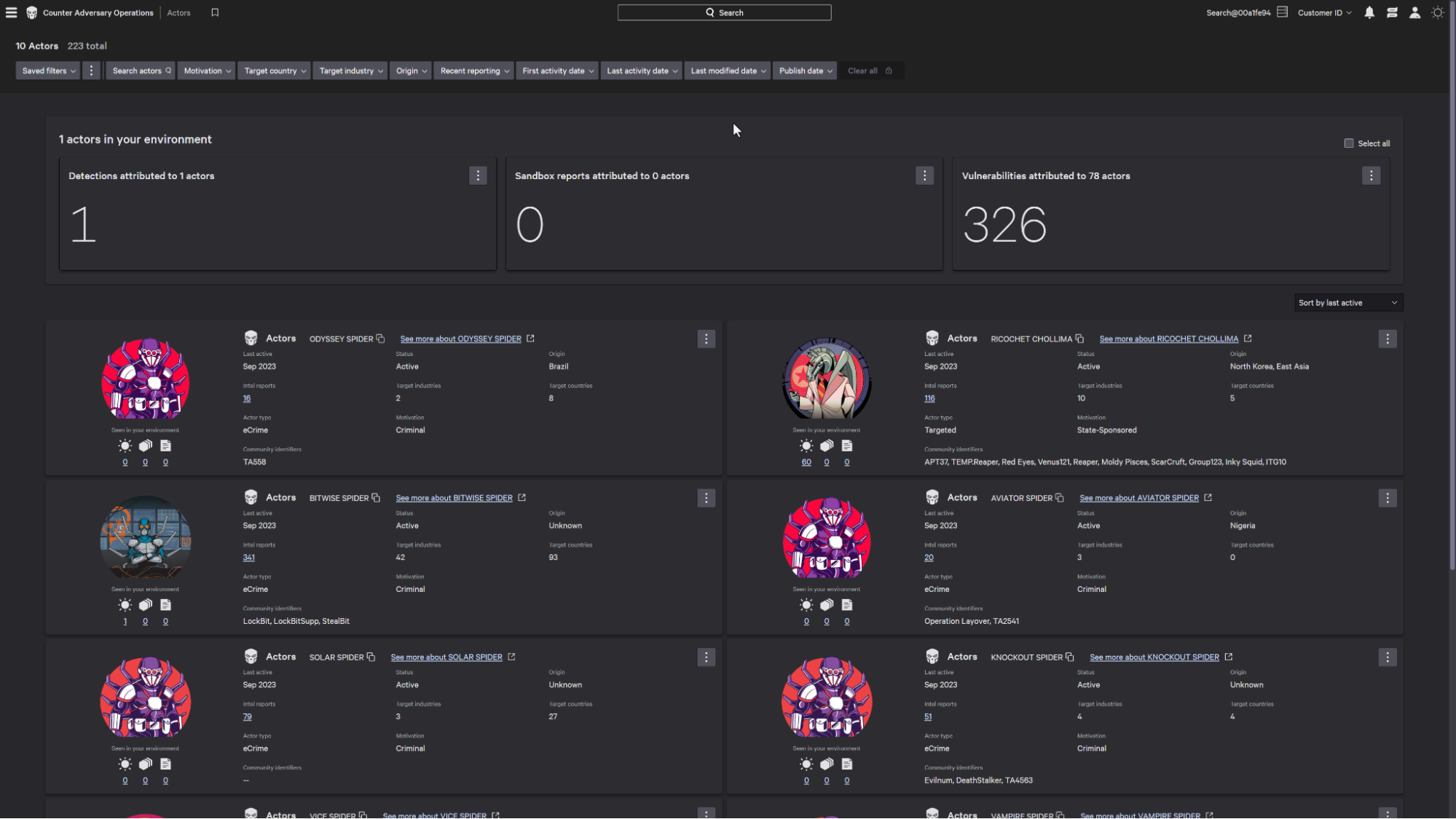
By reviewing Carbon Spider’s profile, you can immediately see they are active in your environment with a detection and 8 unpatched vulnerabilities commonly used by this attacker.
Before you respond, let’s see what else you can learn about Carbon Spider to proactively fortify your defenses.
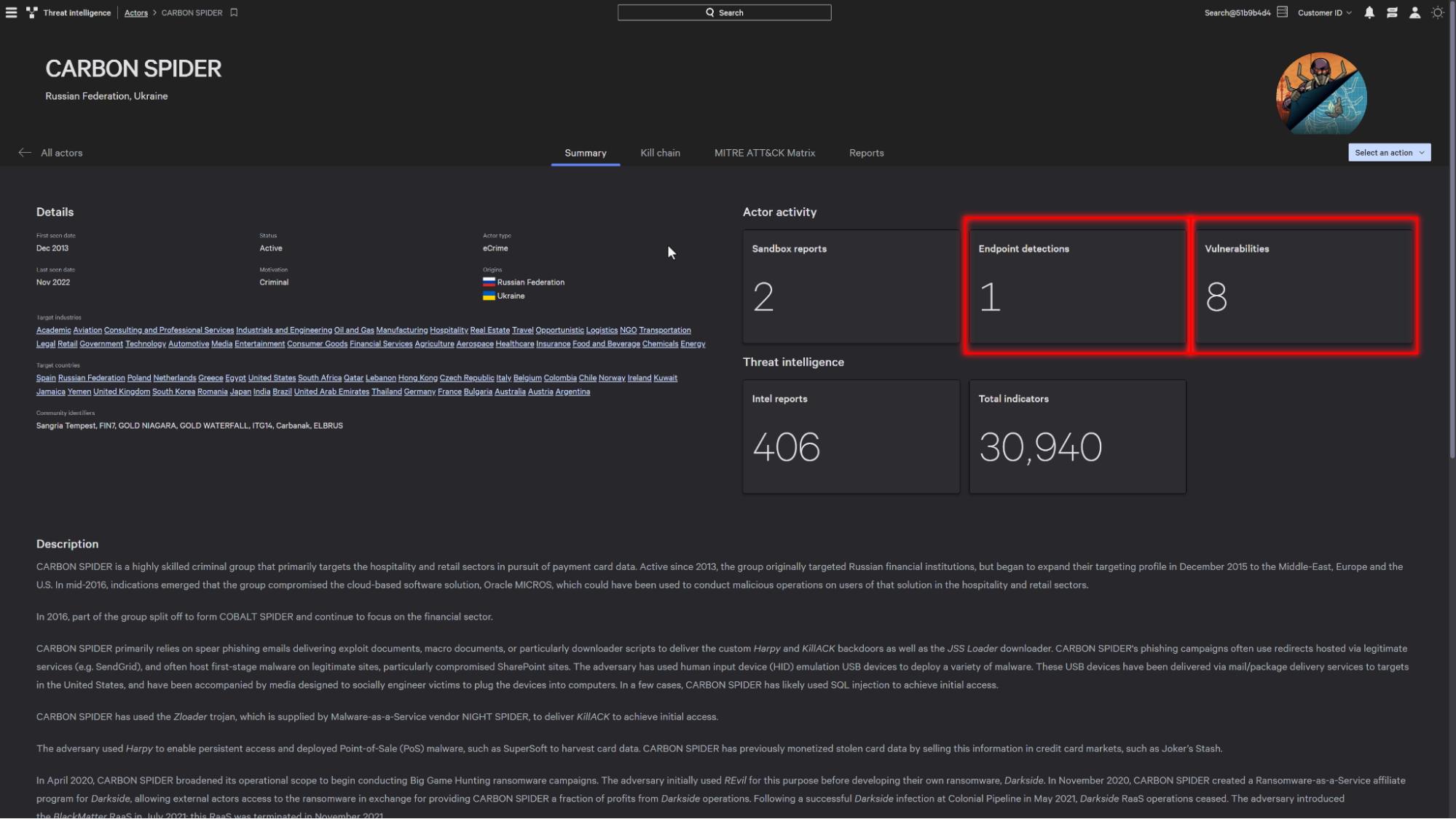
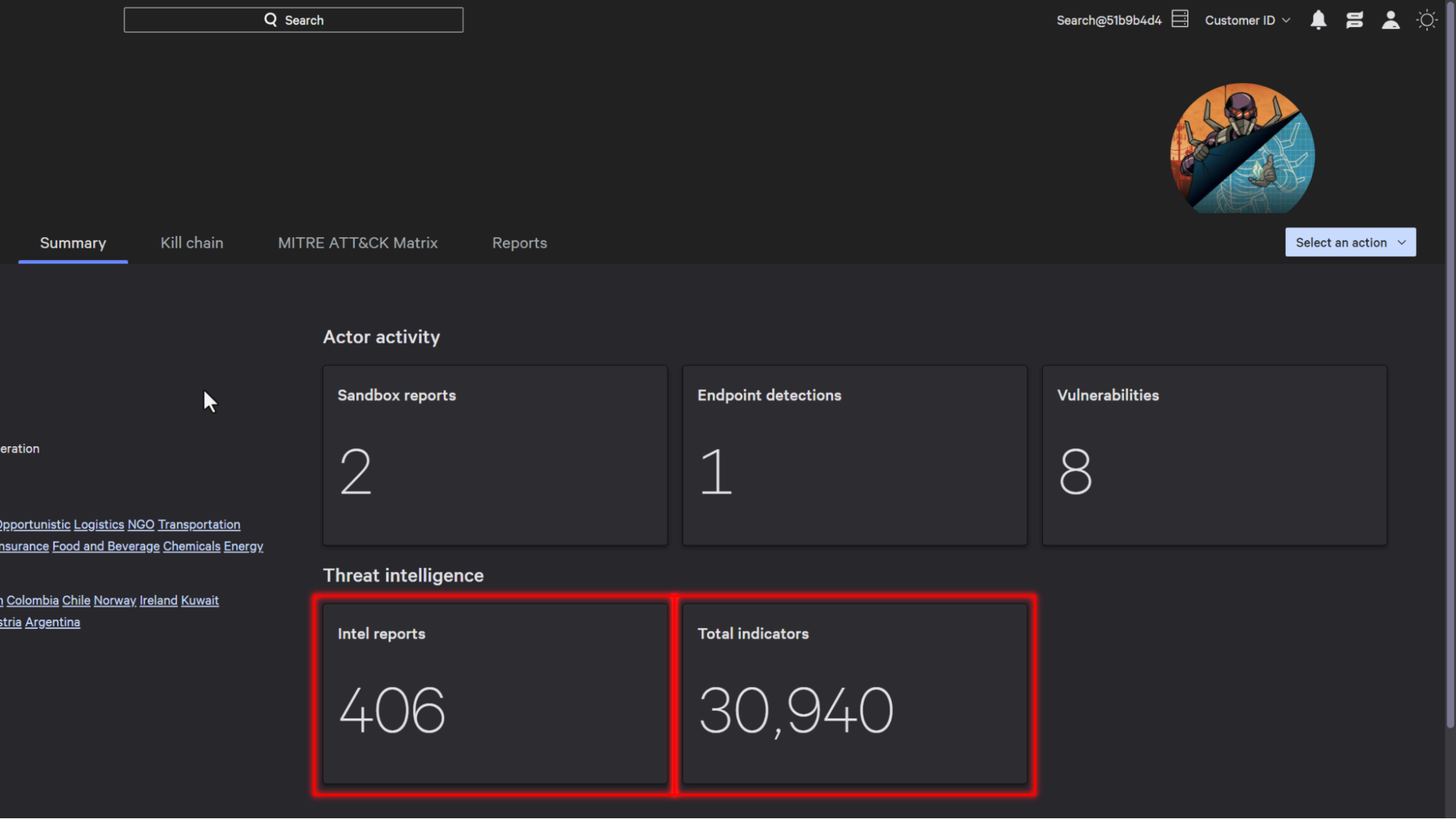
With over 30,000 IOCs and 400 threat intelligence reports related to Carbon Spider natively available within the platform, you can block the IoCs and IoAs related to the adversary with ease.
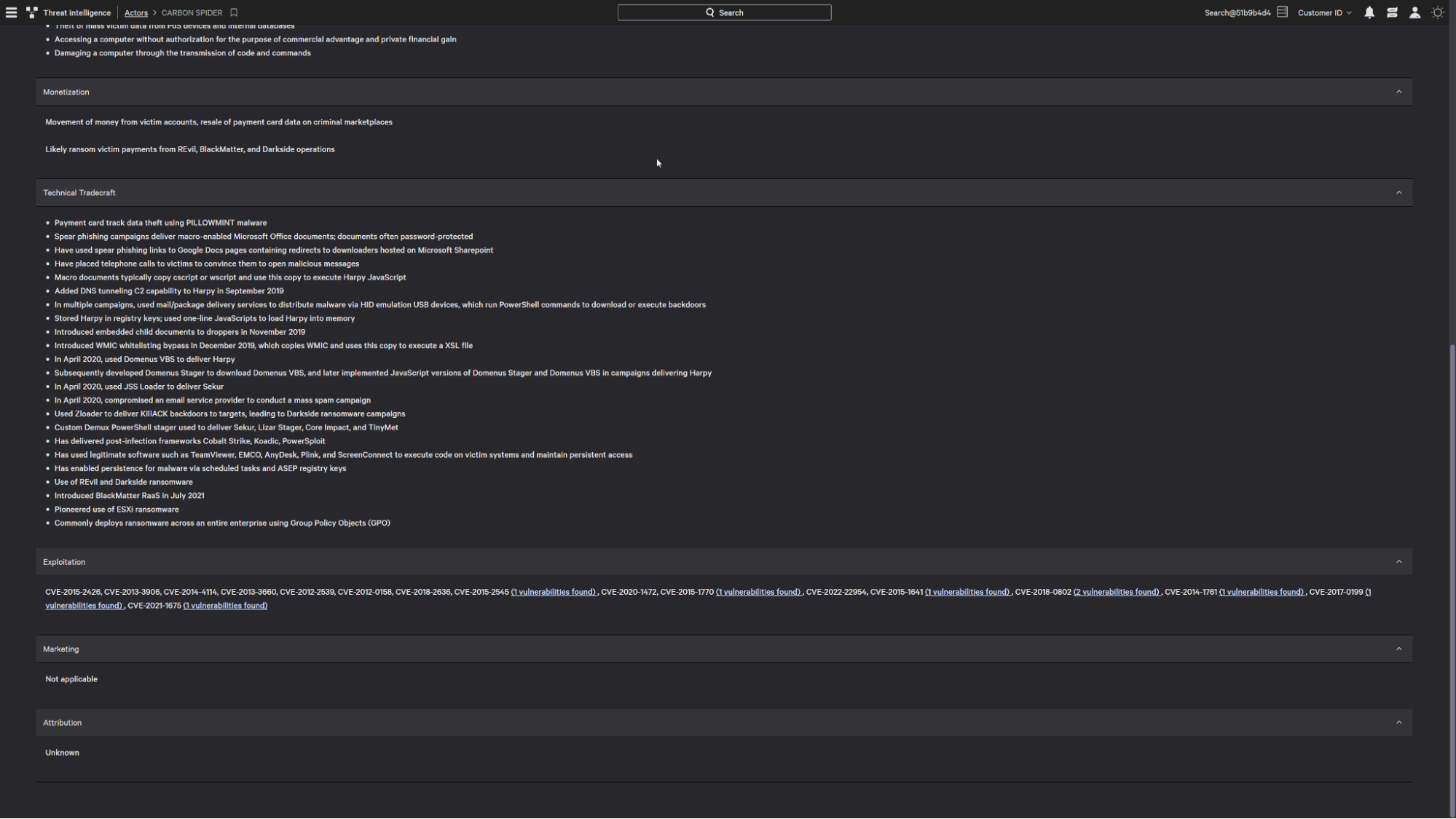
Once you’ve reviewed the adversary summary, the kill chain will give you a better understanding of the tradecraft leveraged by Carbon Spider.
They often use weaponized documents in spear phishing campaigns to exploit vulnerabilities.
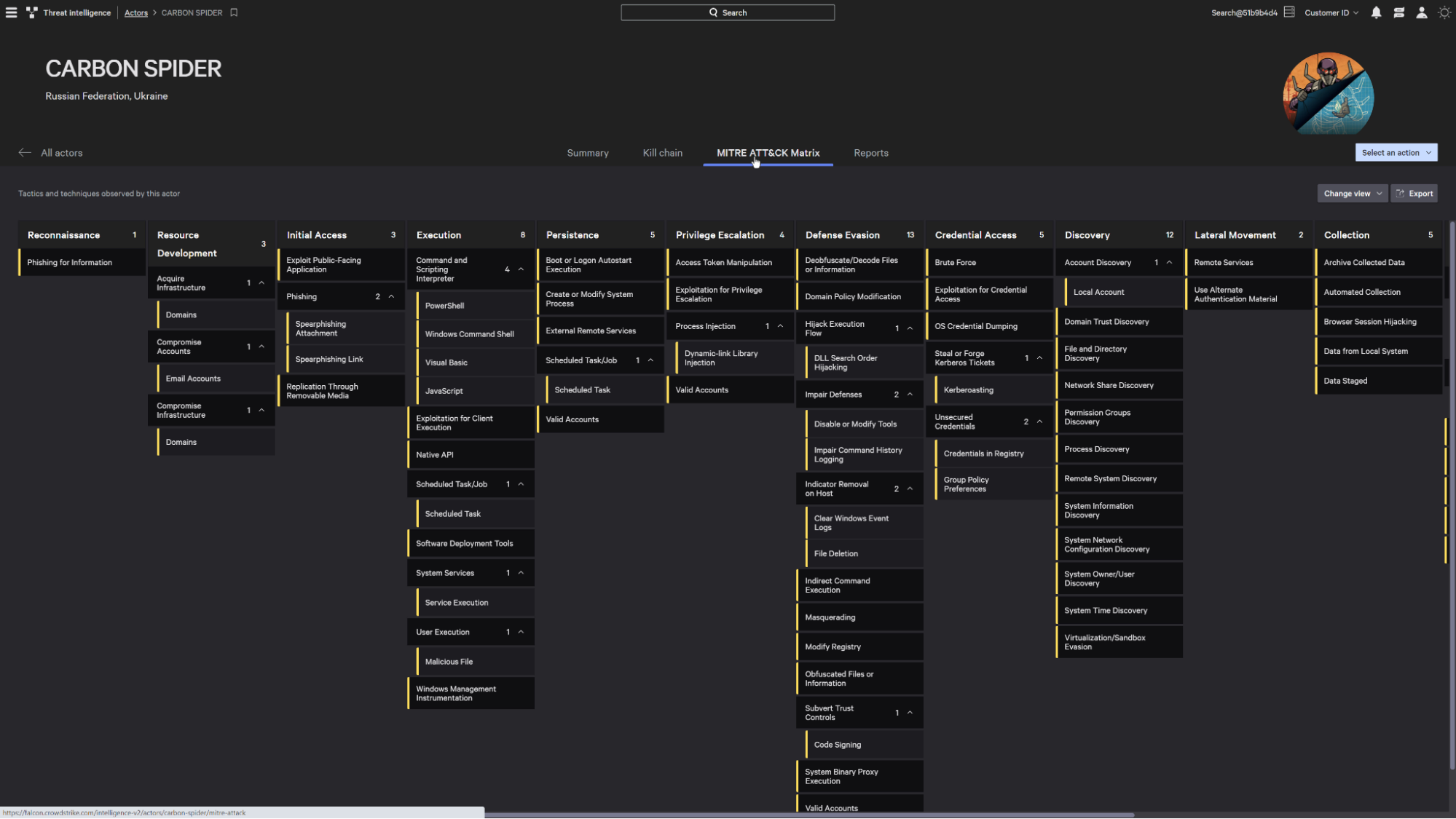
The MITRE ATT&CK Matrix provides an understanding of the full scope of tactics and techniques this adversary employs while executing an attack, allowing you to focus on the most critical stage of the attack.
Then, you can access deep research on this actor, including over 2,500 published reports per year from Falcon Intelligence Premium, ranging from timely alerts, industry specific context, technical research, and strategic guidance that can be used to help inform your cybersecurity and business strategy.
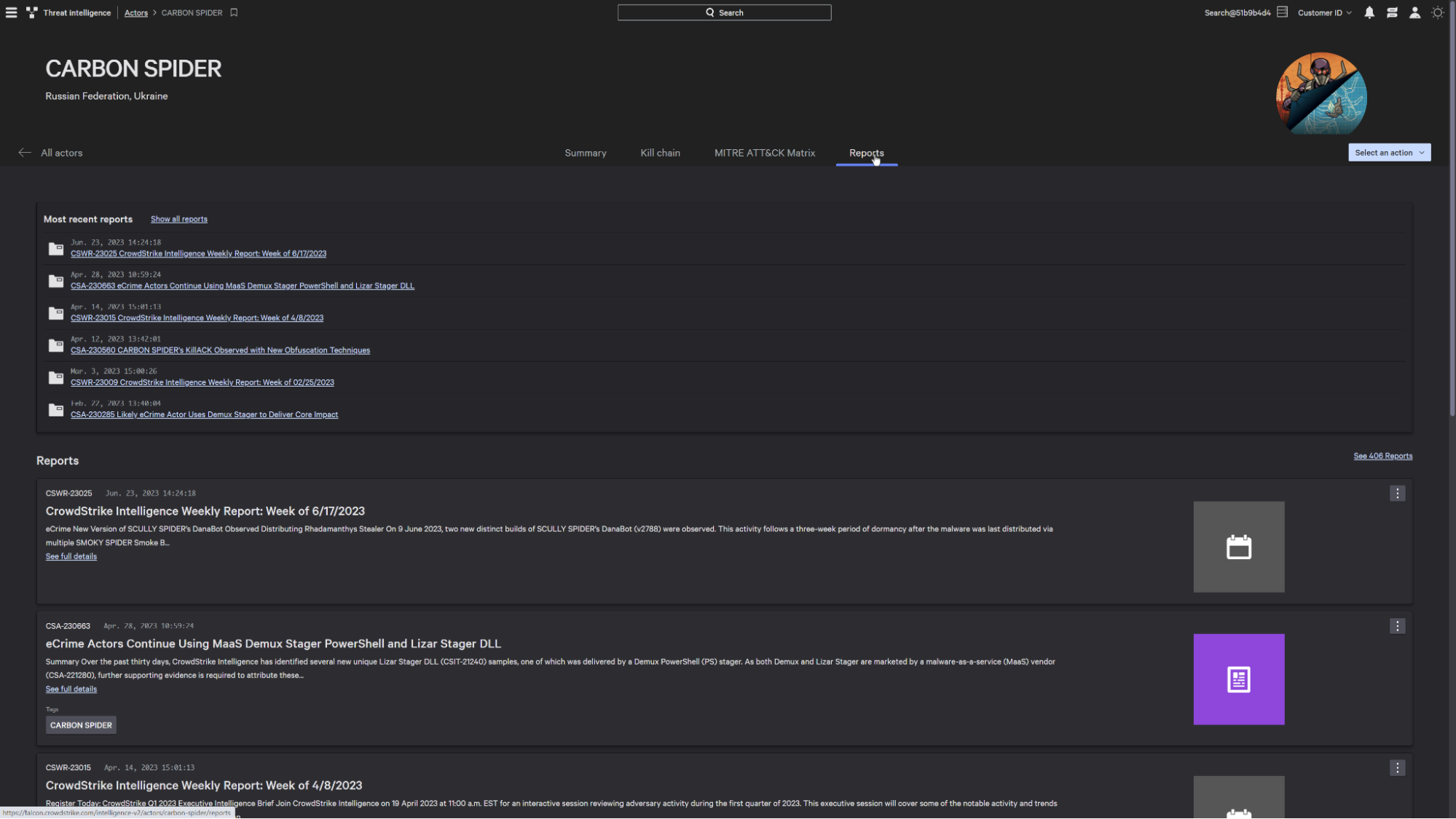
From Carbon Spider’s profile, you can take action on the detection observed within your environment to mitigate their presence.
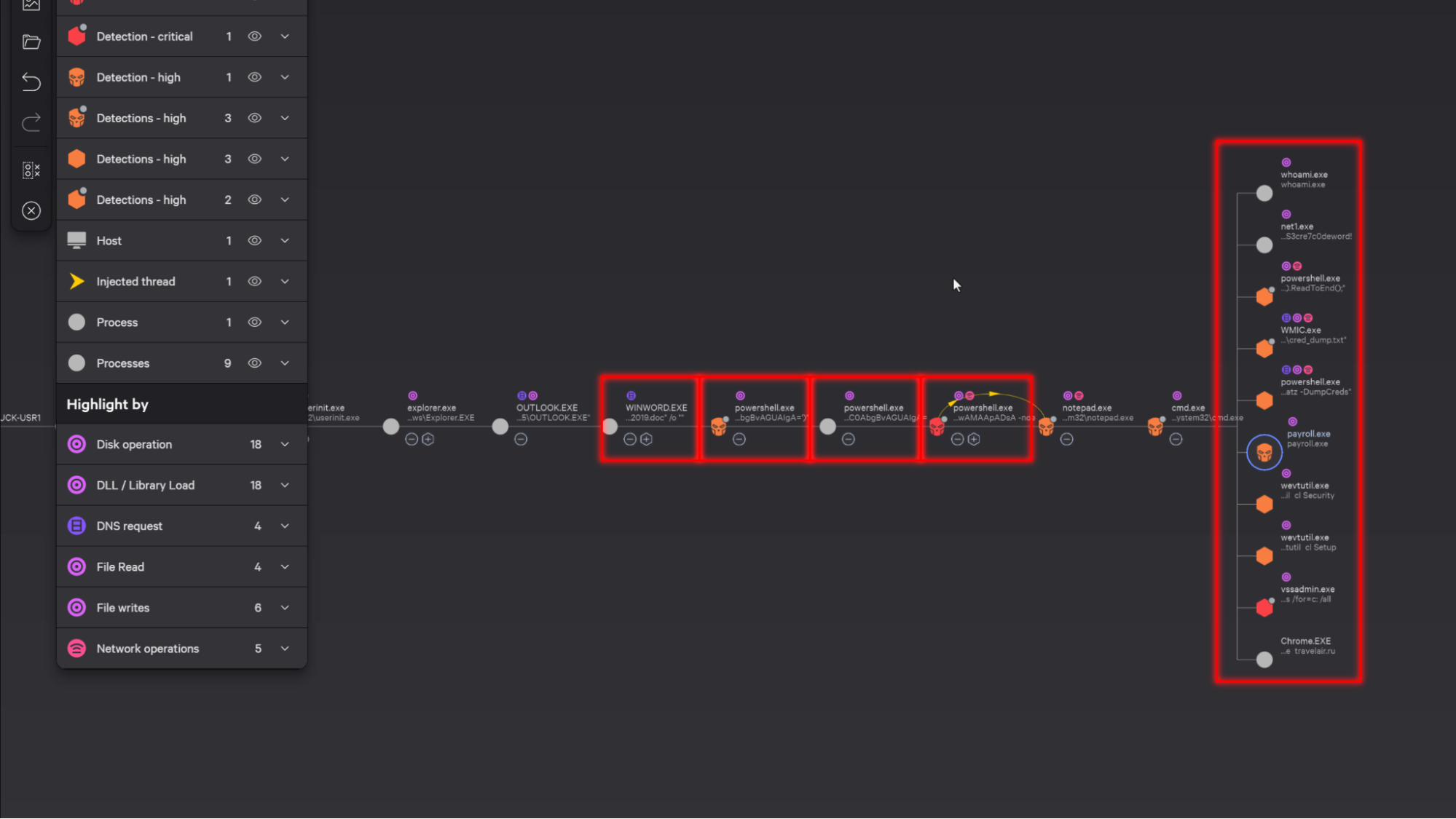
Drilling down into the detection, you can instantly understand what happened by viewing the process tree.
We can see Outlook had launched a word document which had subsequently launched a few powershell scripts and executed additional malicious payloads.
On the right is a comprehensive summary of the detection, with information such as the associated MITRE tactic & technique and any impacted endpoints.
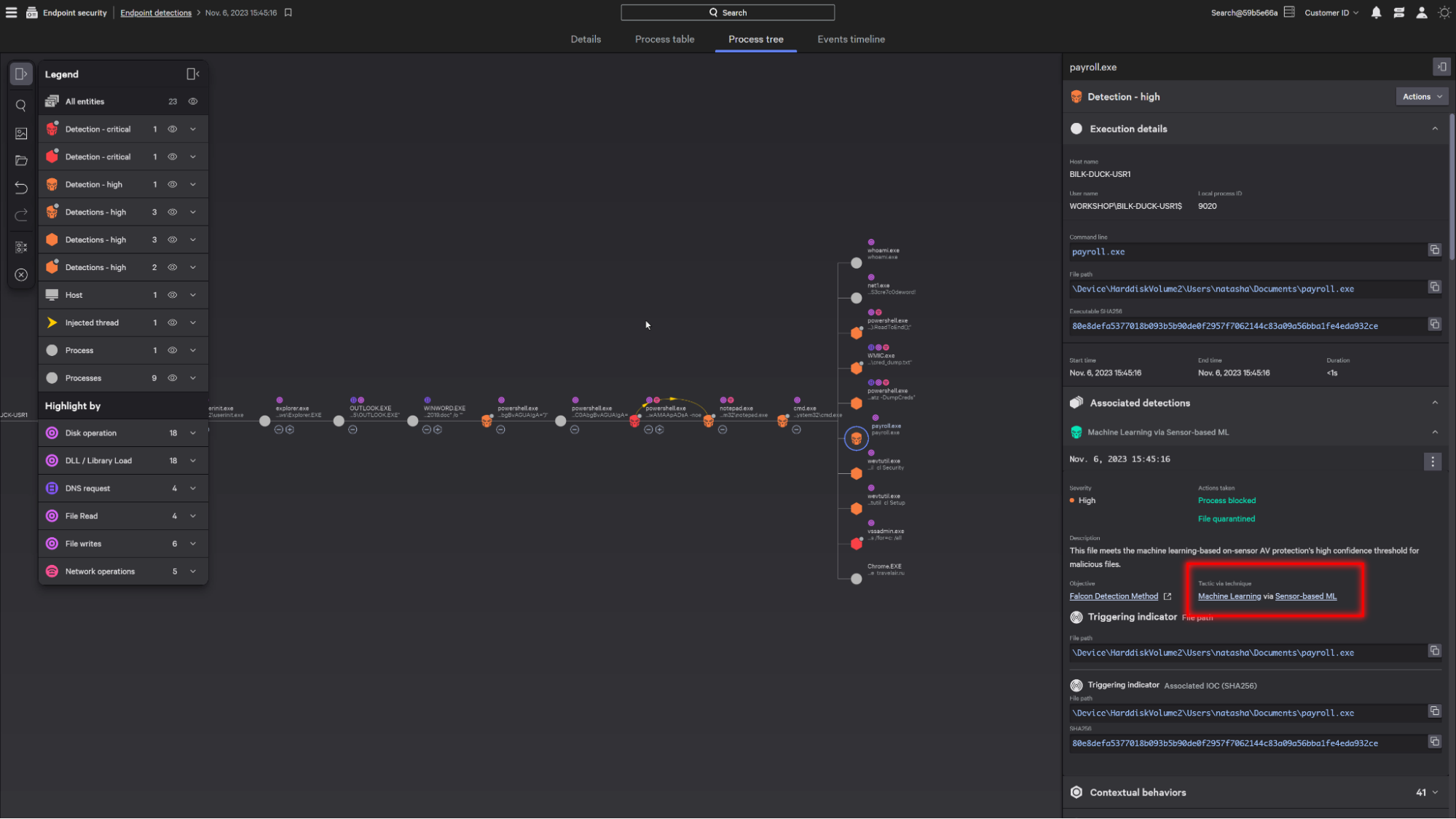
Next, the process hierarchy surfaces additional context surrounding the detection to determine the next step in the investigation.
In this case, the process is immediately blocked and the file quarantined by the platform.
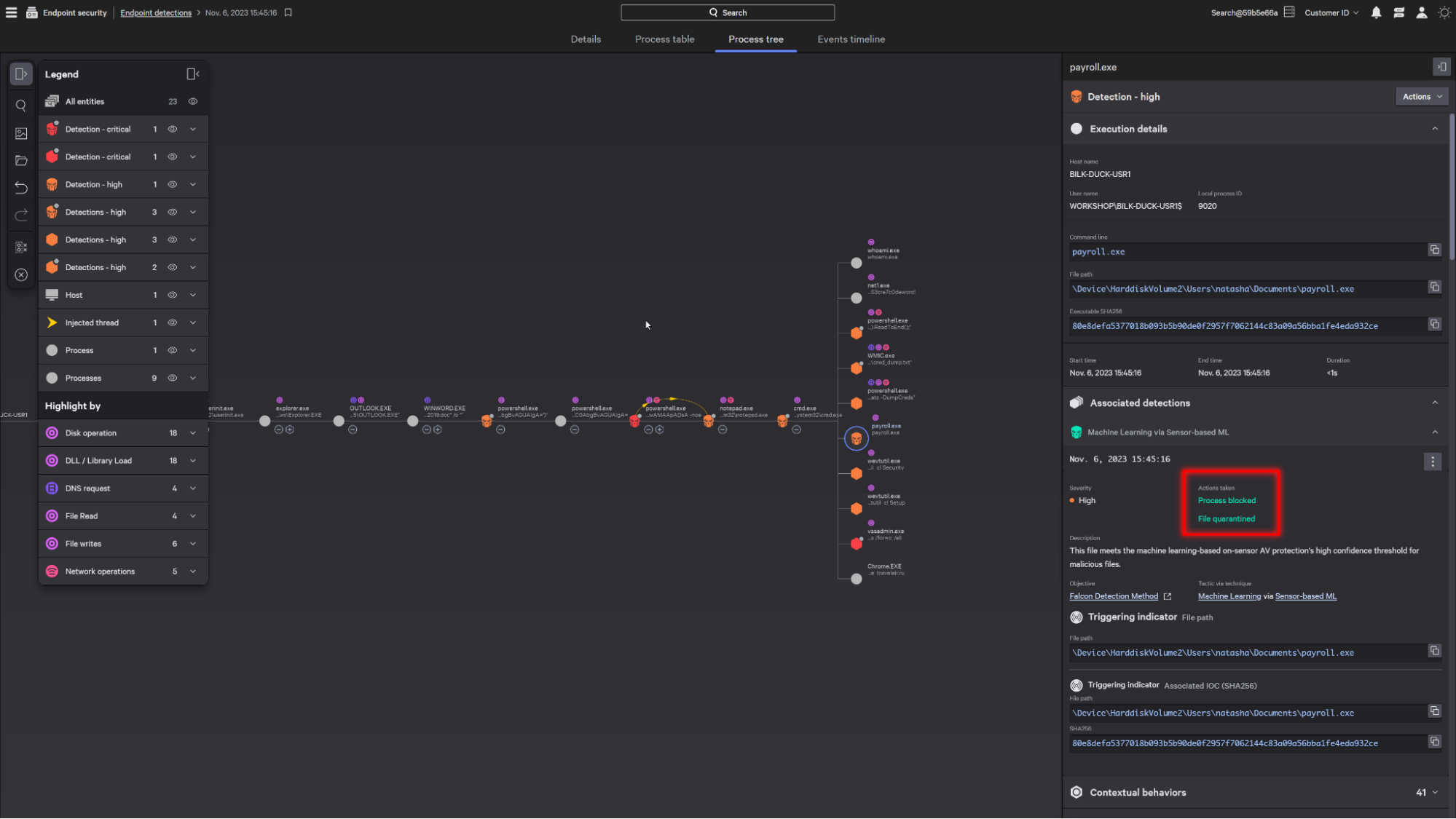
Falcon Intelligence automatically detonates quarantined files in a secure environment to understand the severity score and risk as part of the detection.
Reviewing the sandbox report enables you to surface hidden IOCs that can be leveraged to prevent future attacks.
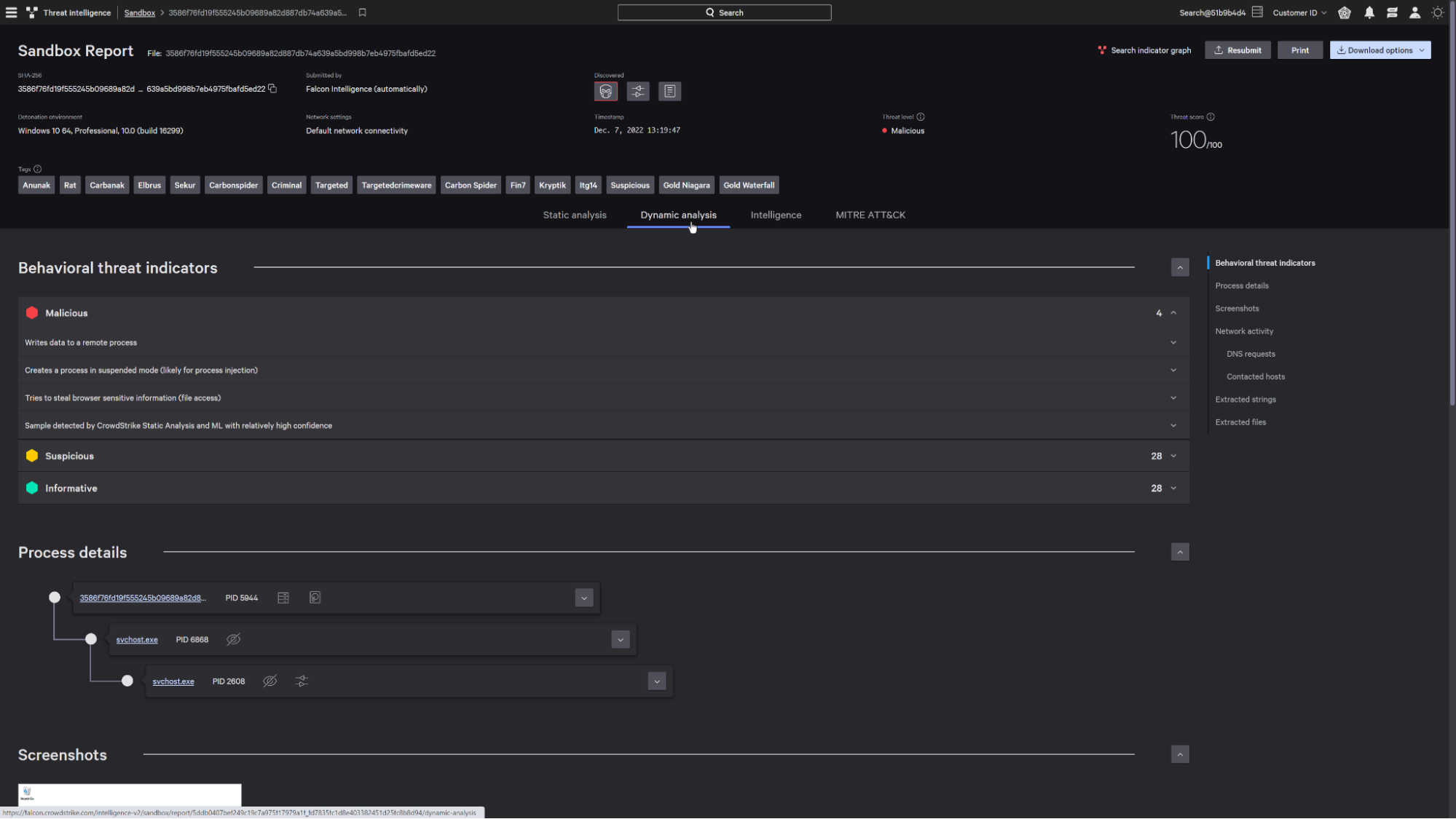
Now, you can proactively identify and remediate any potentially impacted systems.
Falcon Intelligence fully automates the analysis process, infuses native threat intelligence across the platform, and yields actionable results in minutes, not hours.
You are able to maximize your efforts, speed investigation times, and get proactive to make your organization more secure with Falcon Intelligence.