Endpoint Security – Context Enrichment

Introduction
Cyberattacks are constantly increasing in sophistication and severity, and organizations are typically responding by increasing the number of security tools within their arsenal to combat such threats.
As their security stack grows, it results in too many interfaces to navigate across and a security solution that is too complex to utilize effectively.
With the CrowdStrike Falcon® platform, it solves the problem by being able to enrich existing data with additional threat intelligence from outside vendors all within the Falcon user interface and simplifies the security workflow.
This provides a unified console experience that enhances existing Falcon data based on the context of the security artifact and will significantly reduce the time spent triaging and remediating alerts.
Now, let’s take a look to see how easy it is to enable a new integration and the capabilities that are available after we’ve completed the initial setup.
Walkthrough
We’ll start with the CrowdStrike Store.
Here, we’ll use the Category filter and select Context Enrichment and click apply.
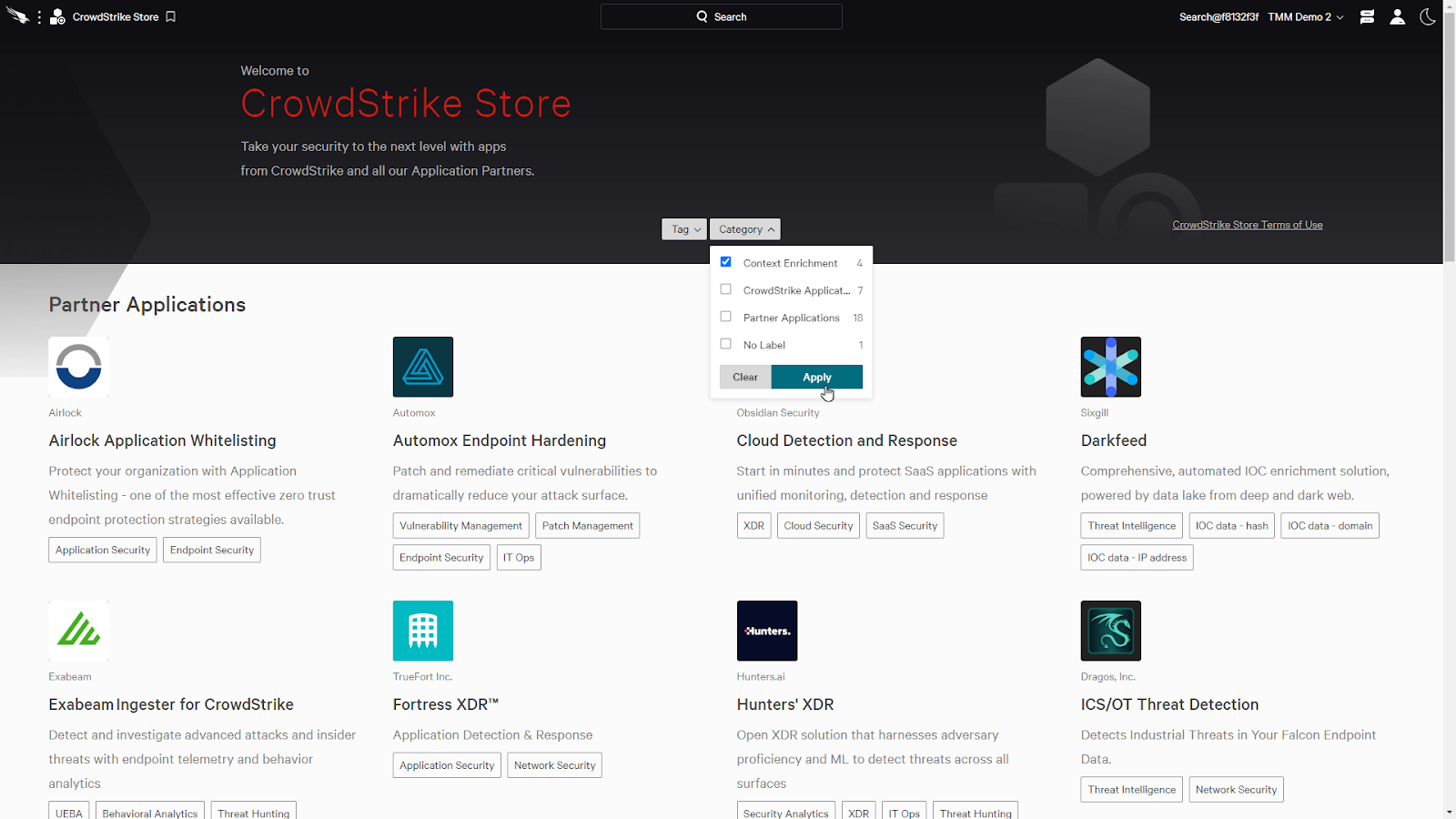
This will list all the applications that provide context enrichment. When we click on an app, such as Sixgill’s Darkfeed, it’ll provide an overview and links to any additional assets such as a demo video.
Looking at Darkfeed’s description, we can see that it provides visibility and context of IOCs from the deep and dark web and is powered by Sixgill’s data lake of underground threat intelligence.
We can try the app for free or activate an existing subscription by clicking on the Try it free button.
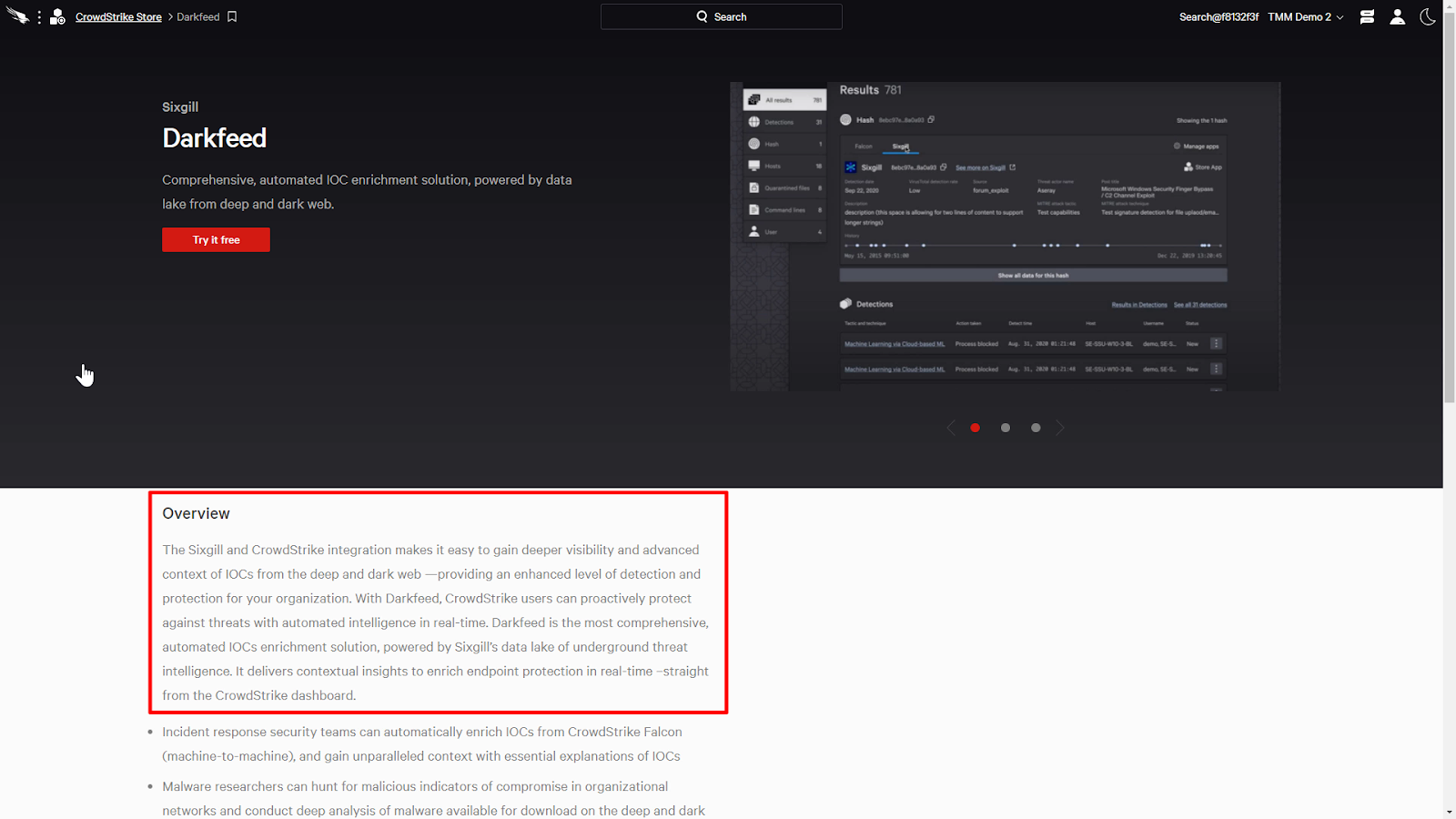
It allows us to bring our own API credentials if we’re already a customer, or we can request a trial by checking the “I don’t have API credentials” box and clicking on the Agree & Request Trial button.
After the initial setup, it will say “Active” or “Trial is in progress” depending on its current status. At the end of the trial, there will be an email with additional information on how to continue to use the application.
Now that the setup is complete, we’ll have access to the information from the integrated vendors directly within the Falcon console.
One method of viewing the enriched intelligence data is to use the Global Search at the top of the page.
The global search can search through many aspects of the Falcon platform, such as actors, detections, documentation, and incidents. We can also search directly for IOCs, such as file hashes, IP addresses, or domains.
Let’s say that we received a file hash through a threat feed and we wanted to find more details on the file. We can paste the hash directly into the global search box and hit enter.
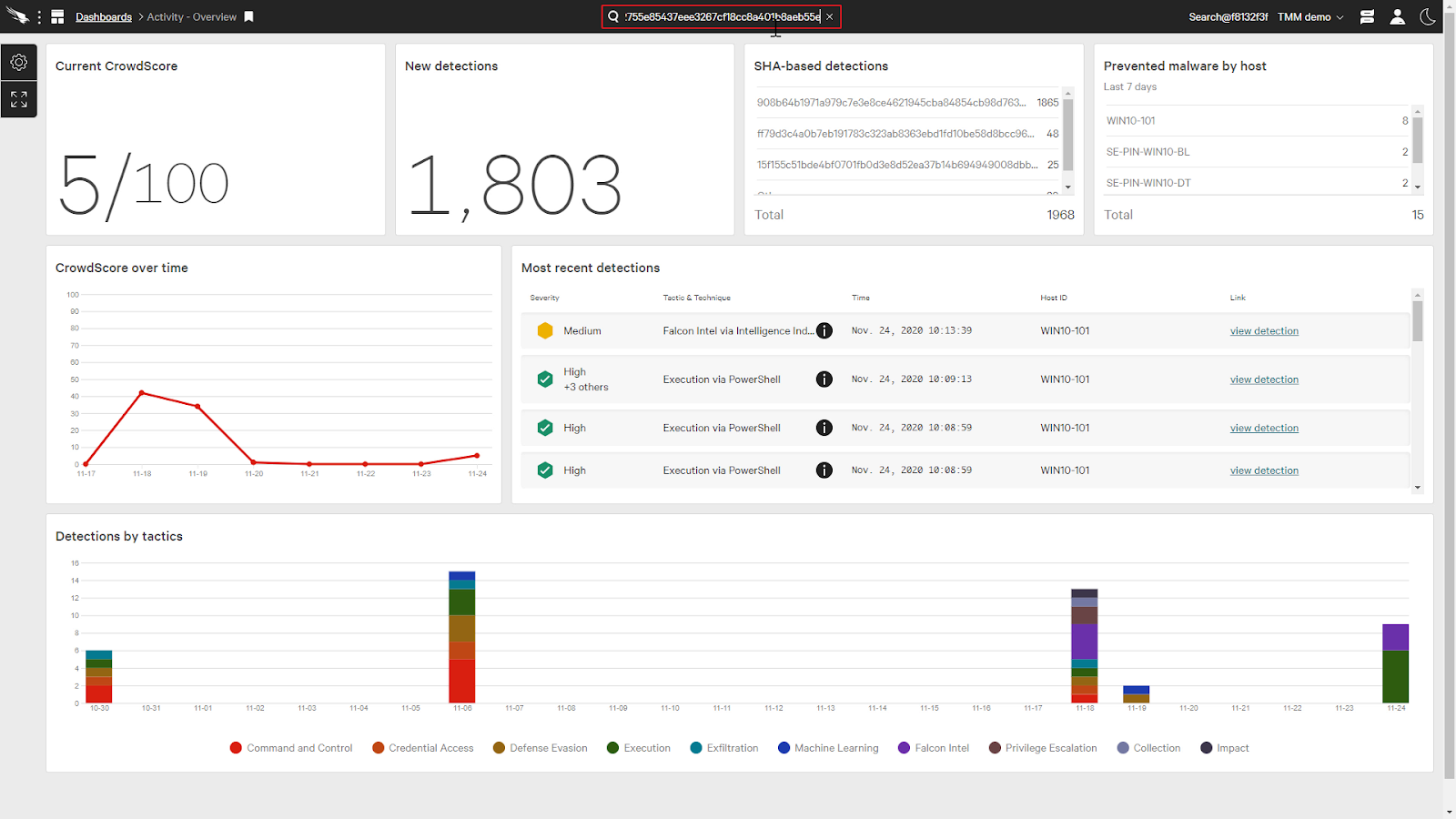
This will bring up the result card for the hash and we can see the information from CrowdStrike’s Intelligence.
On the card, we can also see the tabs of any Context Enrichment apps for this type of IOC that we have enabled on our Falcon Platform.
We can just click on a tab and it’ll show us the curated data from that app. Here we can see the intelligence information provided by OPSWAT.
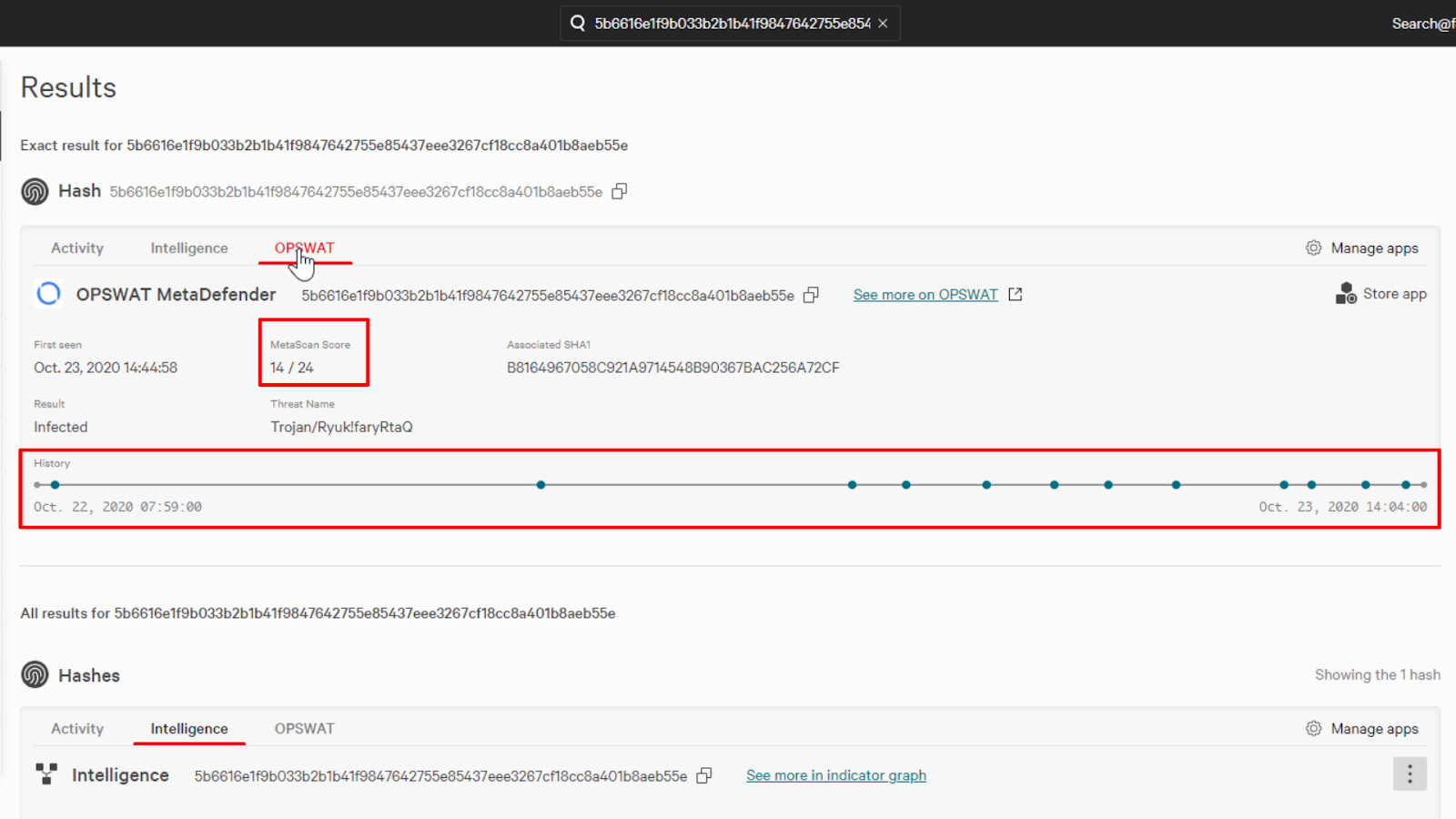
The intelligence data presented depends on the application, but we can see that OPSWAT has information such as a Metascan Score and a history timeline.
This diversified scanning engine can provide additional context on the nature of the threat.
We can also use the “See more at OPSWAT” link to pivot directly to OPSWAT’s site which will provide us with additional data directly from their site.
Okay, the global search works great if we wanted information on a specific IOC, but what about if we find a detection in the workflow?
CrowdStrike is also able to seamlessly provide context on artifacts identified within incidents.
Incidents are a list of alerts driven by its Crowdscore, which combines disparate security detections into a single alert.
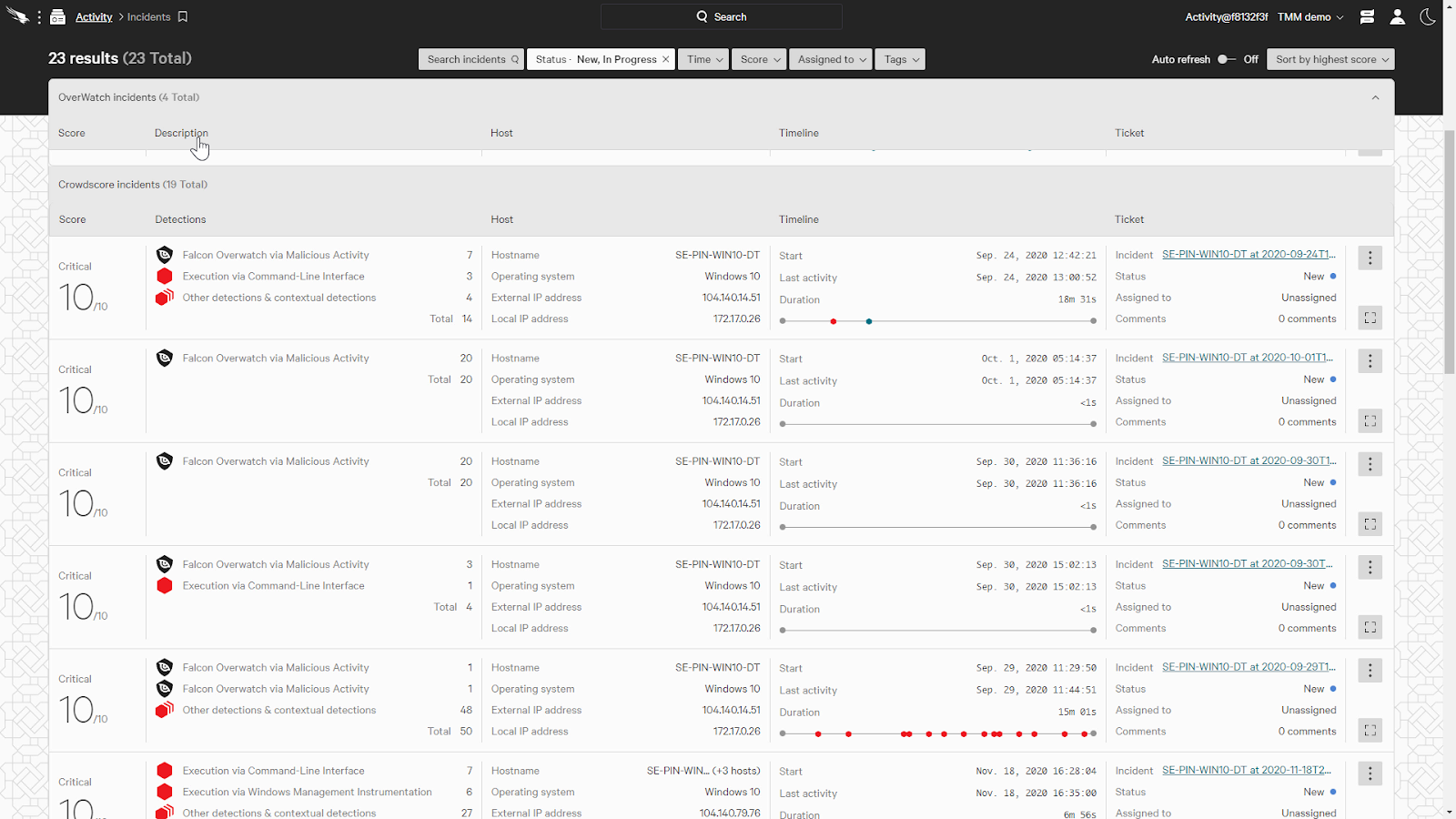
This allows us to prioritize critical incidents and reduces noise of inconsequential detections.
When we click on an incident, it’ll provide a summary preview of the incident.
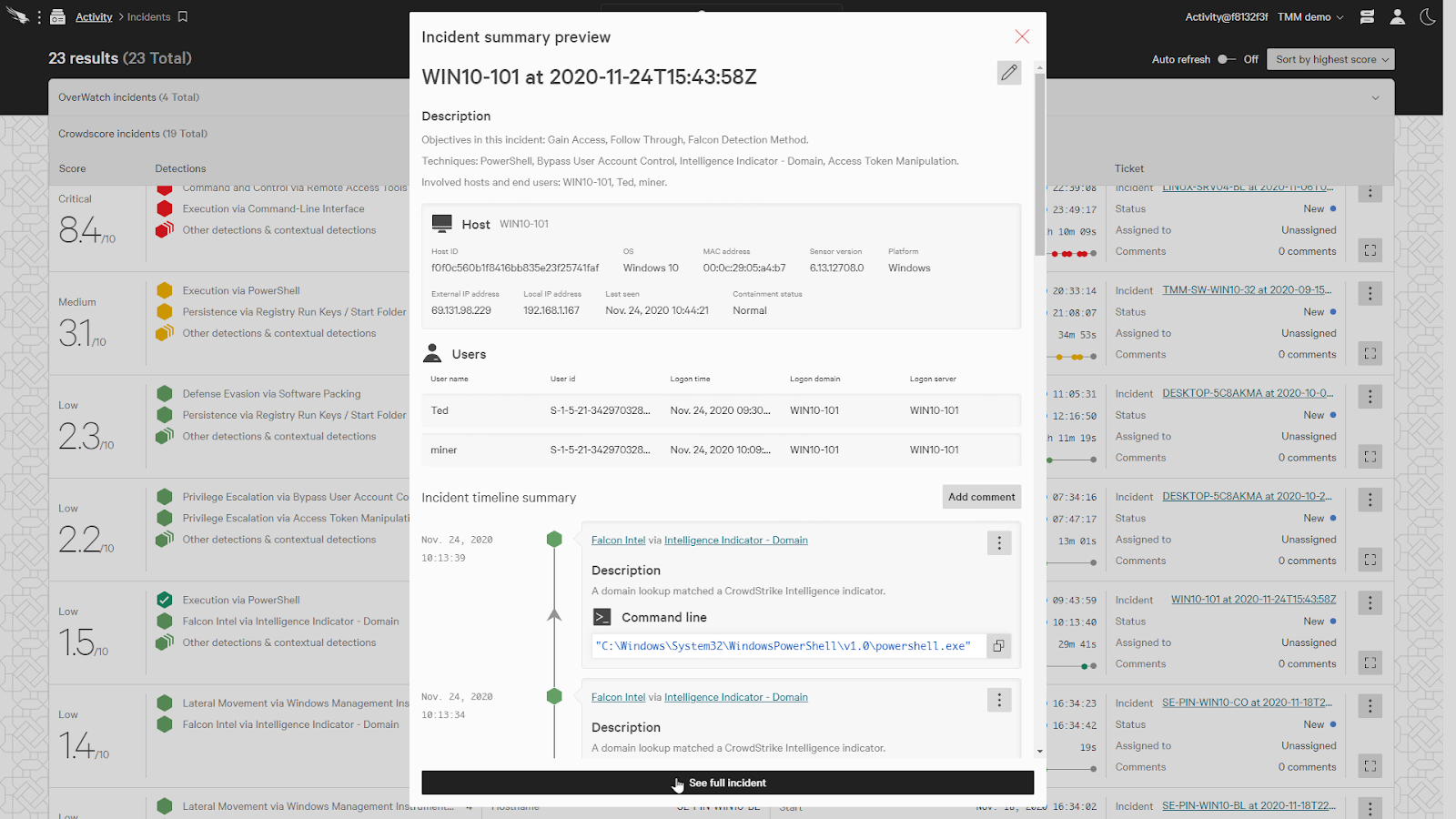
This gives us an overview at a quick glance. We’ll click on the “See full incident” button for additional lenses with which we can use to view the incident.
The Table view will provide a table of the processes and artifacts associated with the incident.
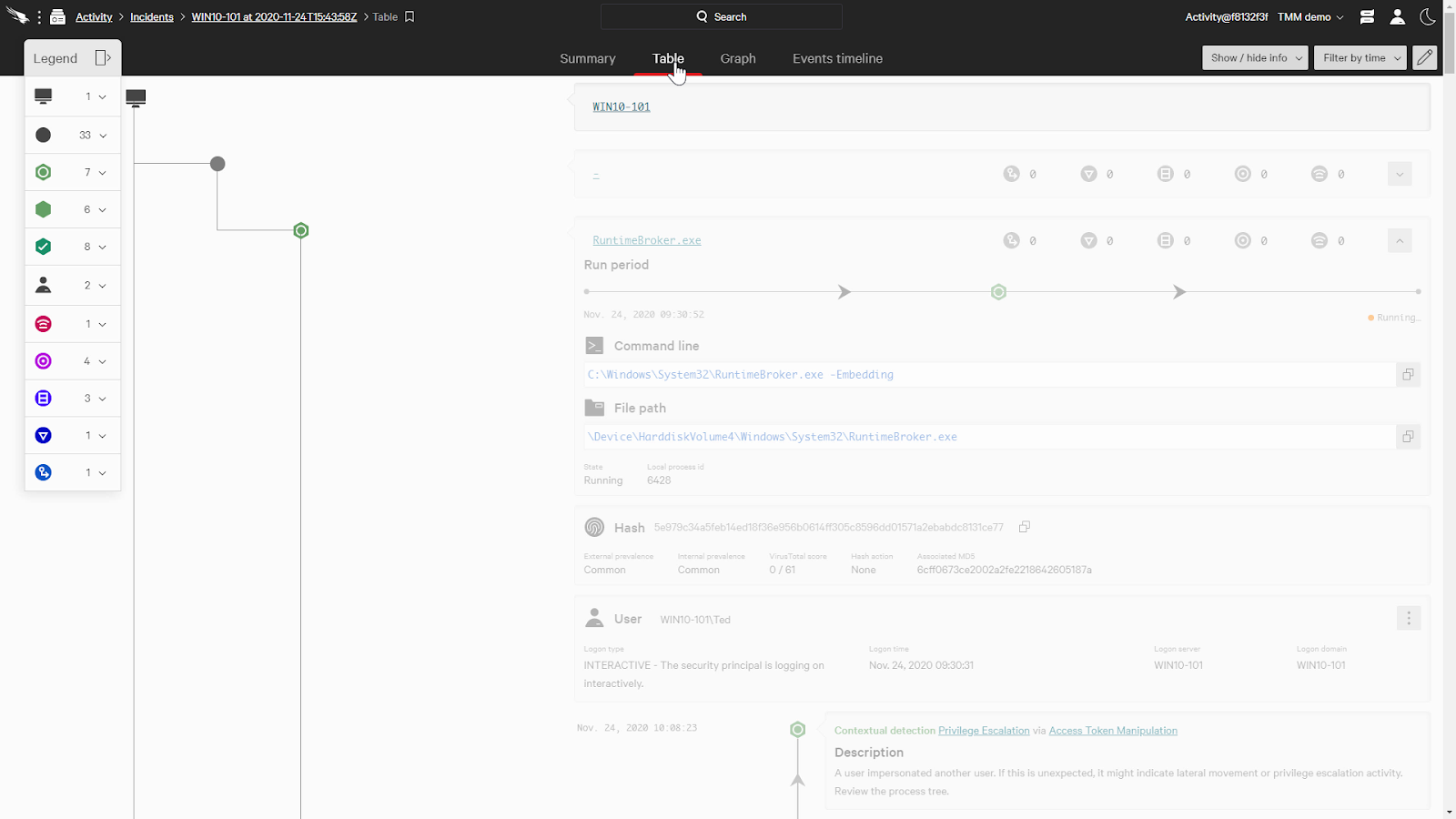
I do want to quickly mention that even though we’ll just be looking at the table view, the cards with the context enrichment are also available in Graph and Event Timeline views as well.
When we click on Powershell.exe. This will bring us to the process in the process trace as well as open a tab for this process at the bottom.
Here, it’ll show us additional information on the detection, but if we scroll to the DNS requests section, we can see all the DNS requests that were made by the process.
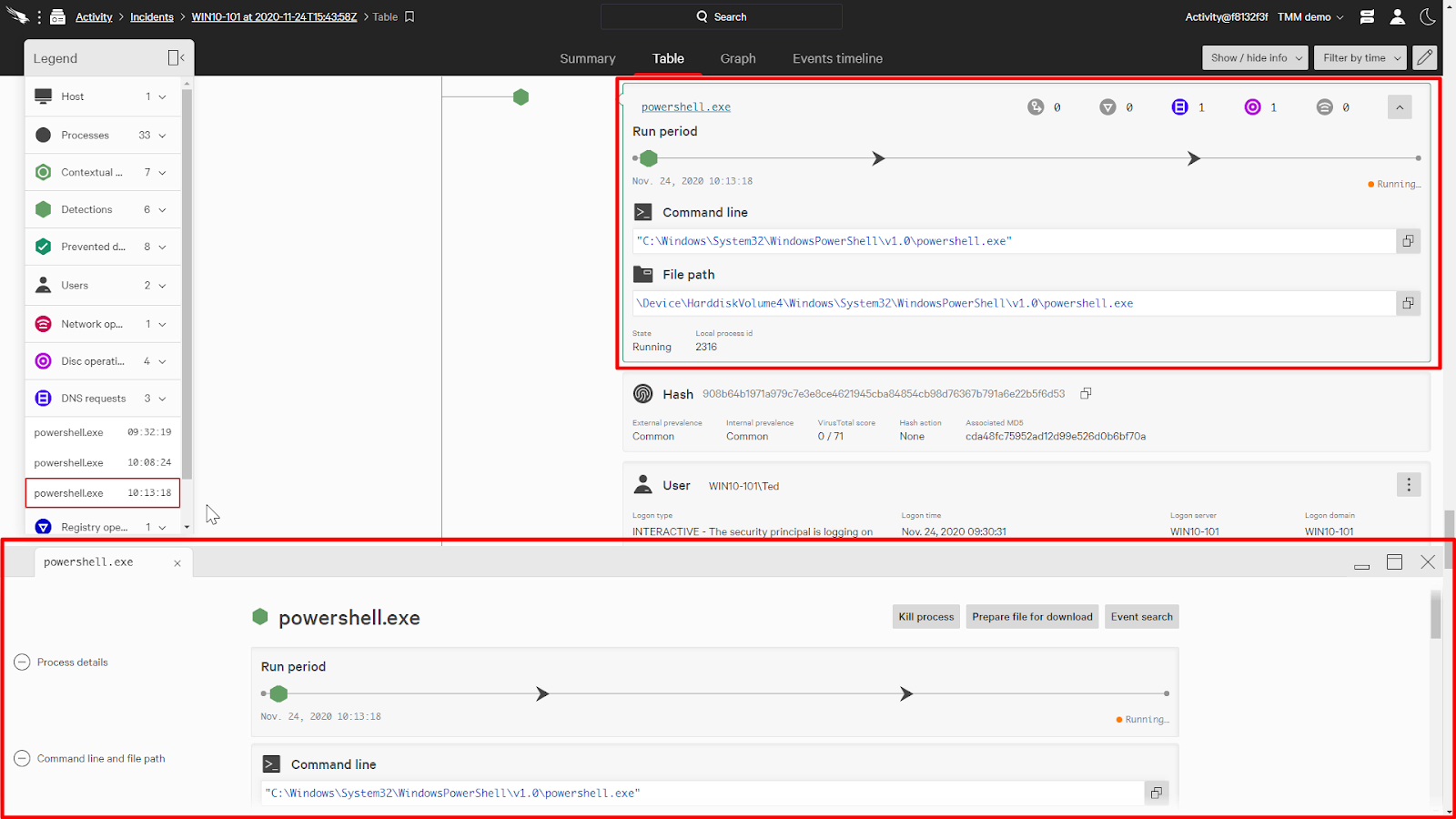
Clicking on a domain will bring up its card.
On the card, it’ll start us off with the CrowdStrike’s Activity tab, which will show us its detection within the environment.
We can also take a look at the CrowdStrike’s Intelligence tab. That will show us intelligence information provided by the Falcon platform.
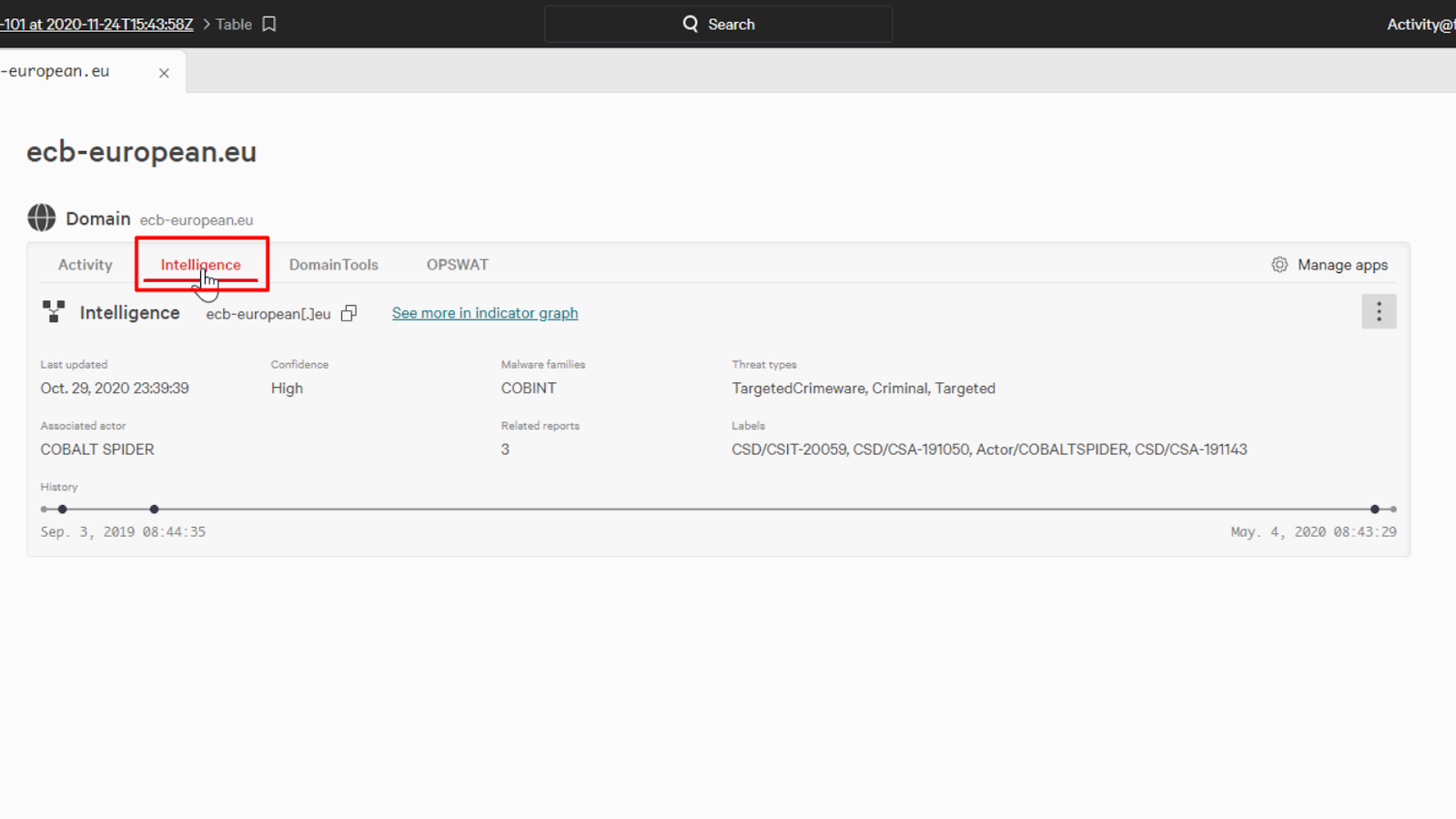
Also on the card are tabs for the other vendors that can enrich our content.
Something that you might have noticed is that there are additional vendors listed here that weren’t listed when we were looking at the file hash earlier.
That’s because only vendors that have information to provide will have tabs in the interface, otherwise they won’t be listed.
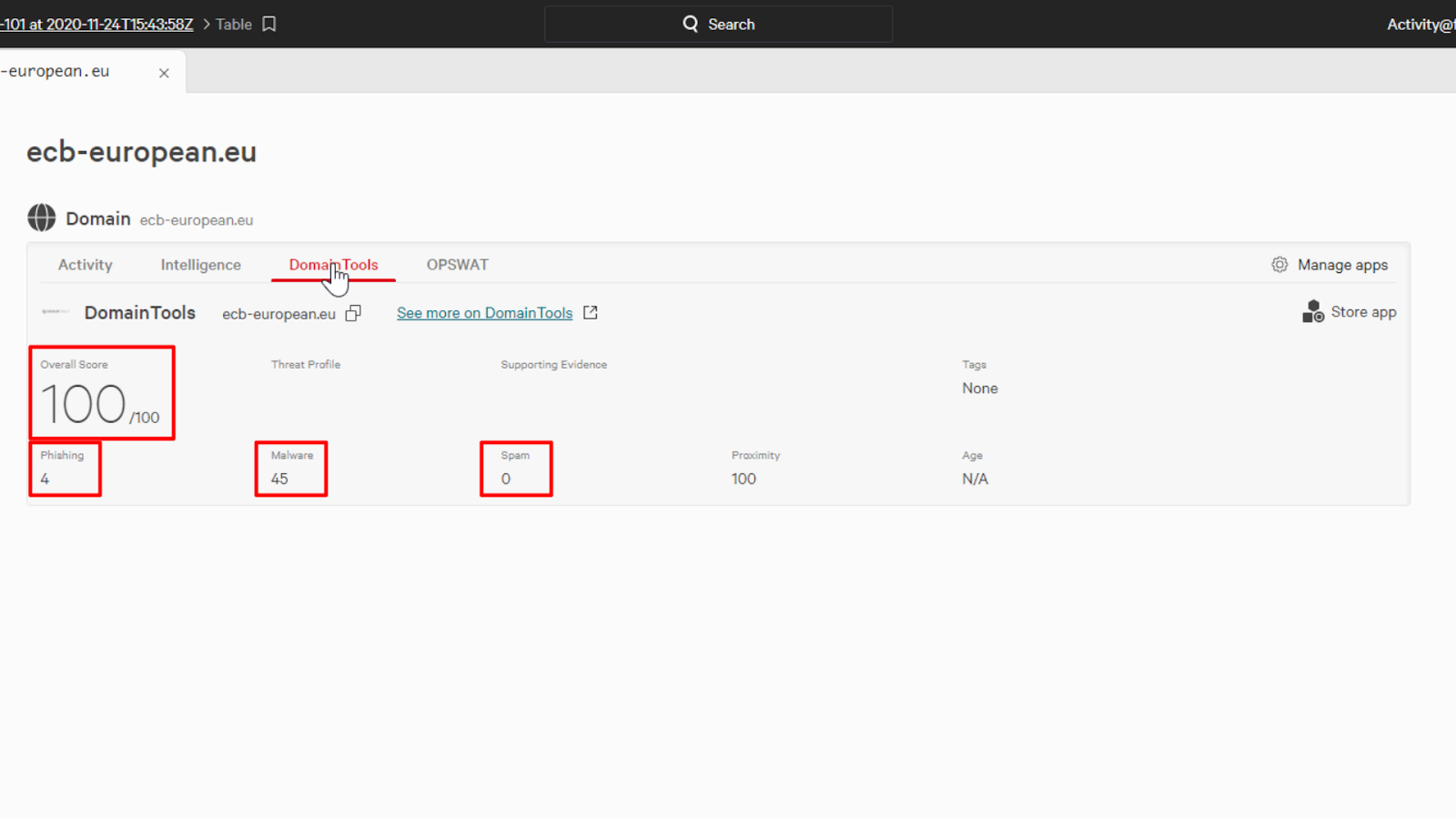
Now, we’ll just click on DomainTools to see the enhanced domain intelligence data that is provided.
Alongside Falcon Intelligence data, DomainTools has over 30 years of intelligence experience with domain registries.
It looks like they have rated the domain with an Overall Risk Score of 100, which is extremely high. DomainTools also breaks out the phishing, malware, and spam scores into individual components providing us with additional context.
Conclusion
As we can see, CrowdStrike Falcon with Context Enrichment enables security teams to reduce the time necessary for triaging and remediating incidents.
The seamless integration simplifies the workflows by bringing in rich data from other vendors directly into the Falcon console user interface, allowing for rapid investigation of sophisticated incidents without having to jump through multiple security tools.