Endpoint Security – Falcon Insights XDR tour

Introduction
Many organizations today suffer from disjointed cybersecurity solutions, leading to delayed detections and responses to threats.
CrowdStrike Falcon® Insight XDR correlates native and third-party cross-domain telemetry to deliver high-confidence detections that would be invisible to siloed solutions.
Let’s take a look at how Falcon XDR is able to leverage events from multiple security tools to surface hidden threats and enrich existing detections.
Walkthrough
We’ll start with a dashboard that shows detections from across security domains in a centralized location.
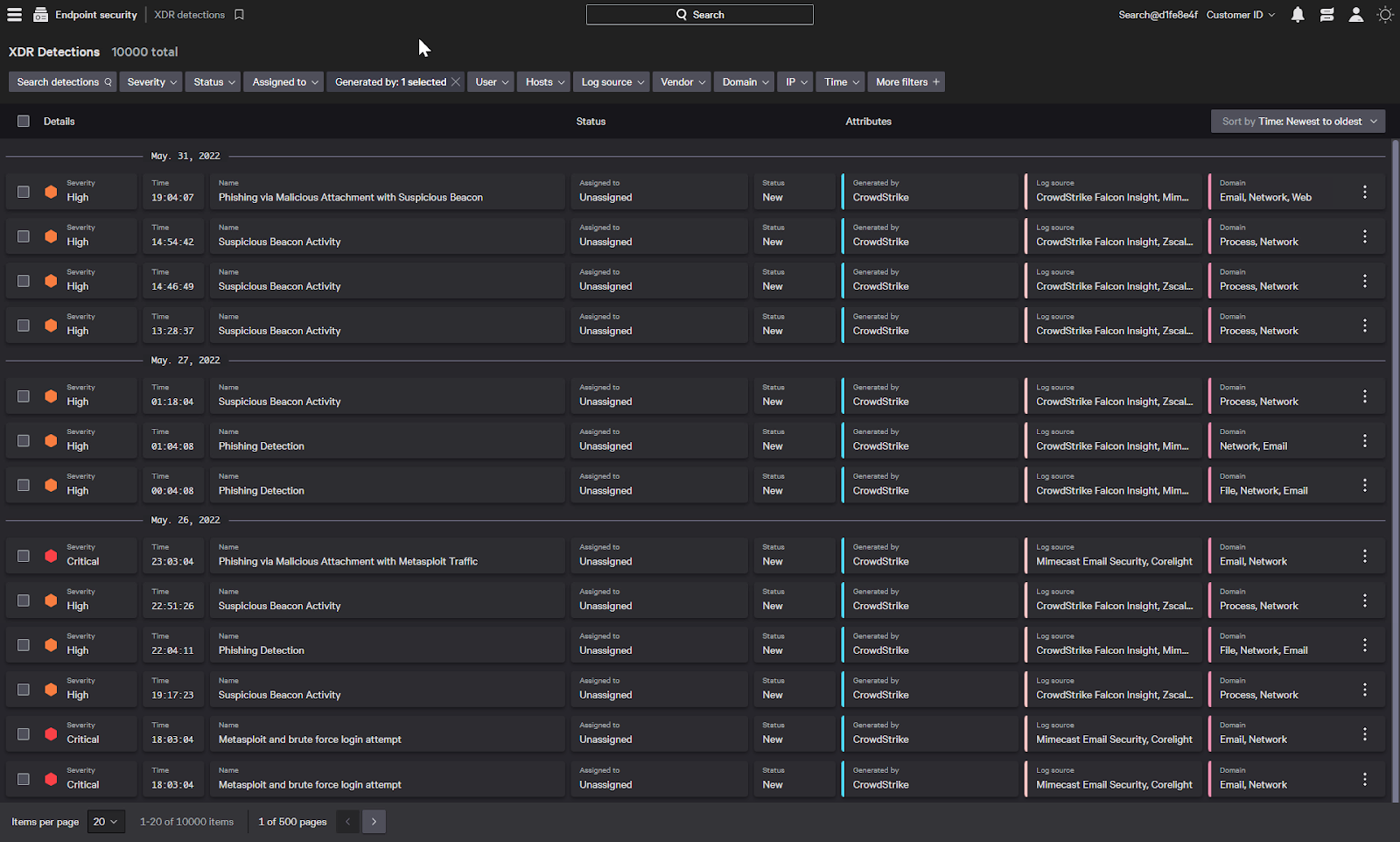
While individual events from third party security devices might not provide adequate visibility, when they’re analyzed holistically, it can generate detections of an attack that’s difficult to see if those security devices are viewed on an individual basis.
Here we can see detections that Falcon XDR has identified by combining insights from email protection, web gateway, and network security devices.
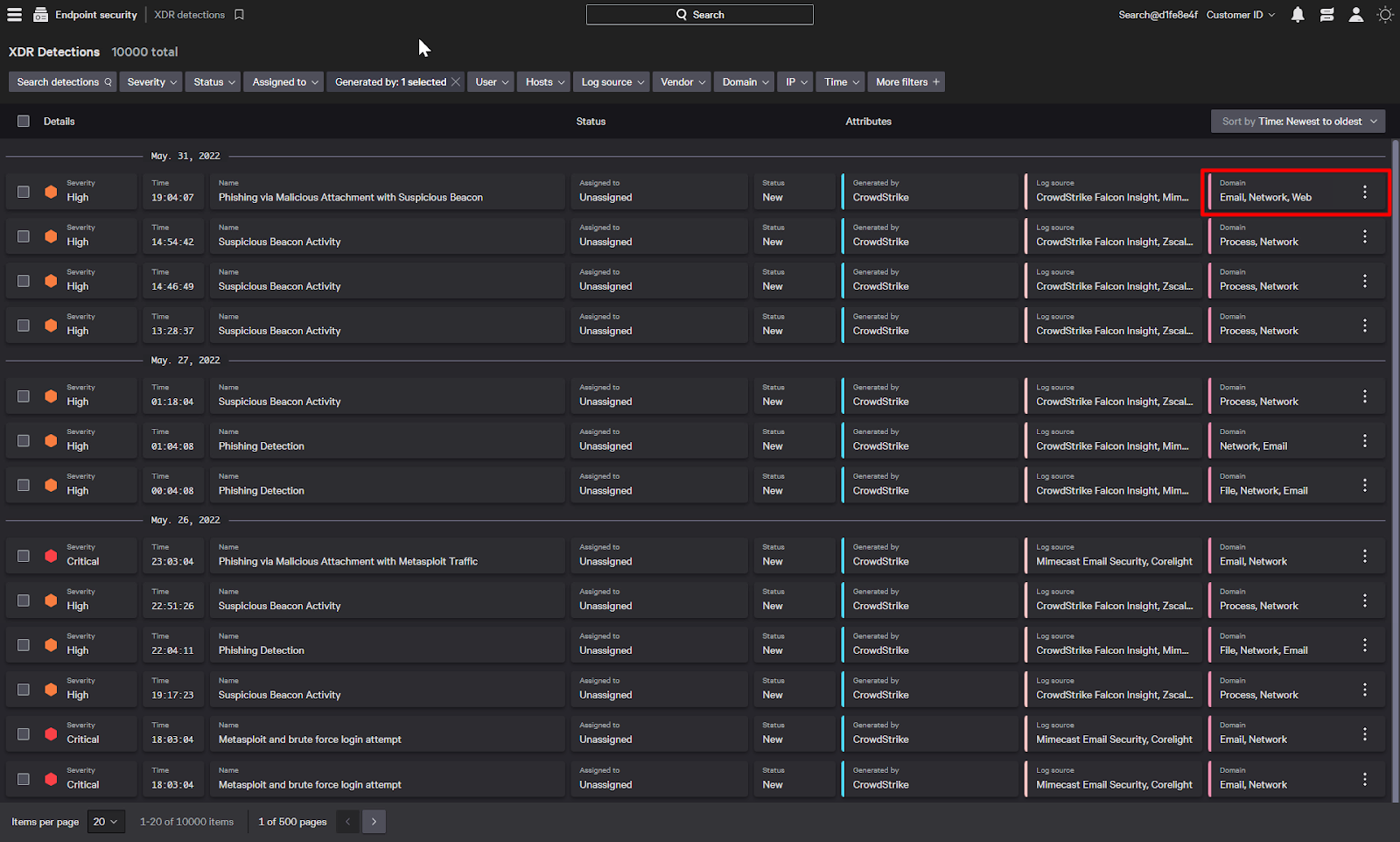
Taking a look at the detection, Phishing via malicious attachment with suspicious Beacon, we can see a quick description of the attack in the inspector on the side.
It looks like there was an attachment in an email that communicated with a remote host and we should investigate to see if any of our systems are compromised by the phishing attack.
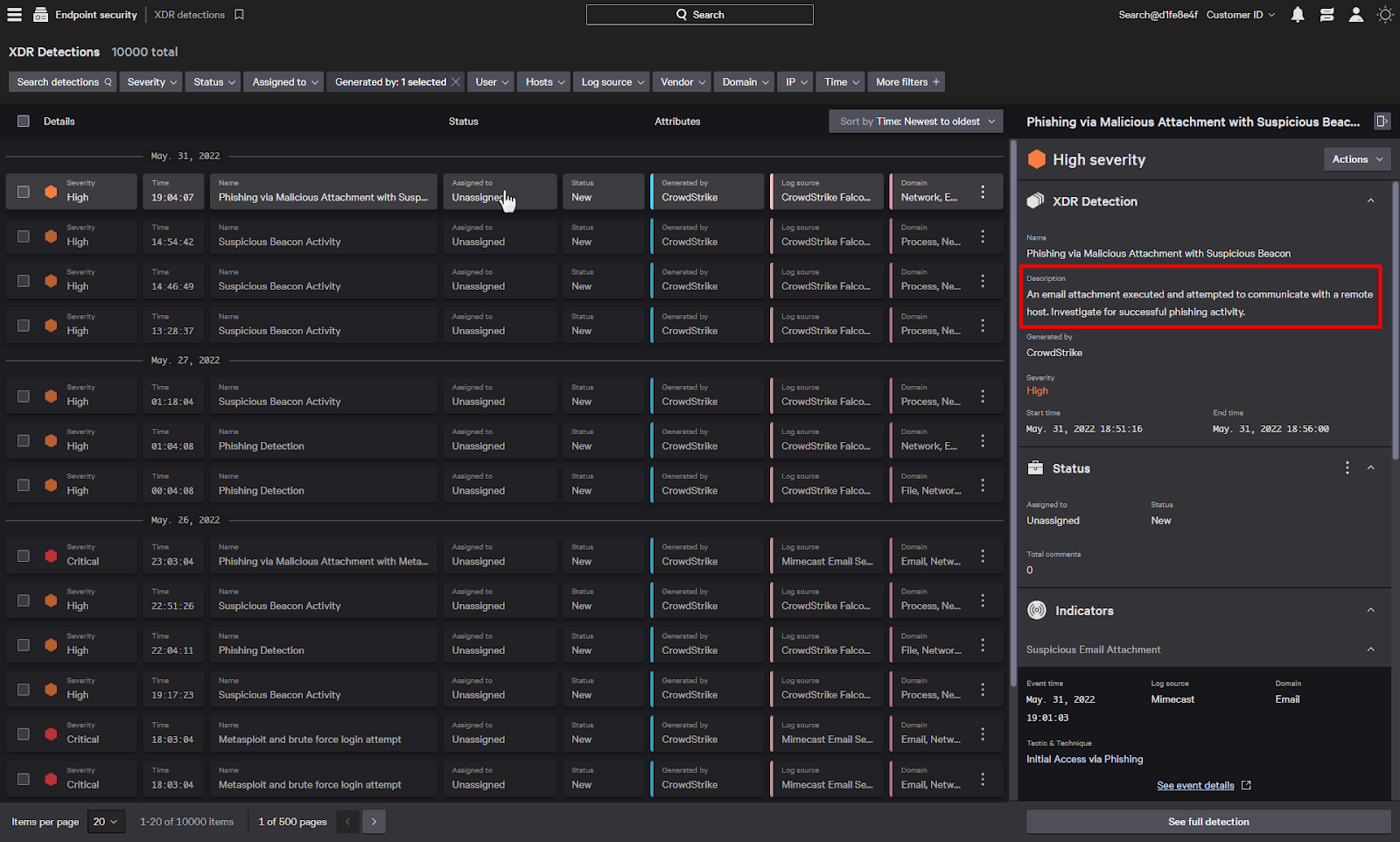
Let’s dig deeper by taking a look at the full detection.
We can see that multiple indicators have come together to form this detection.
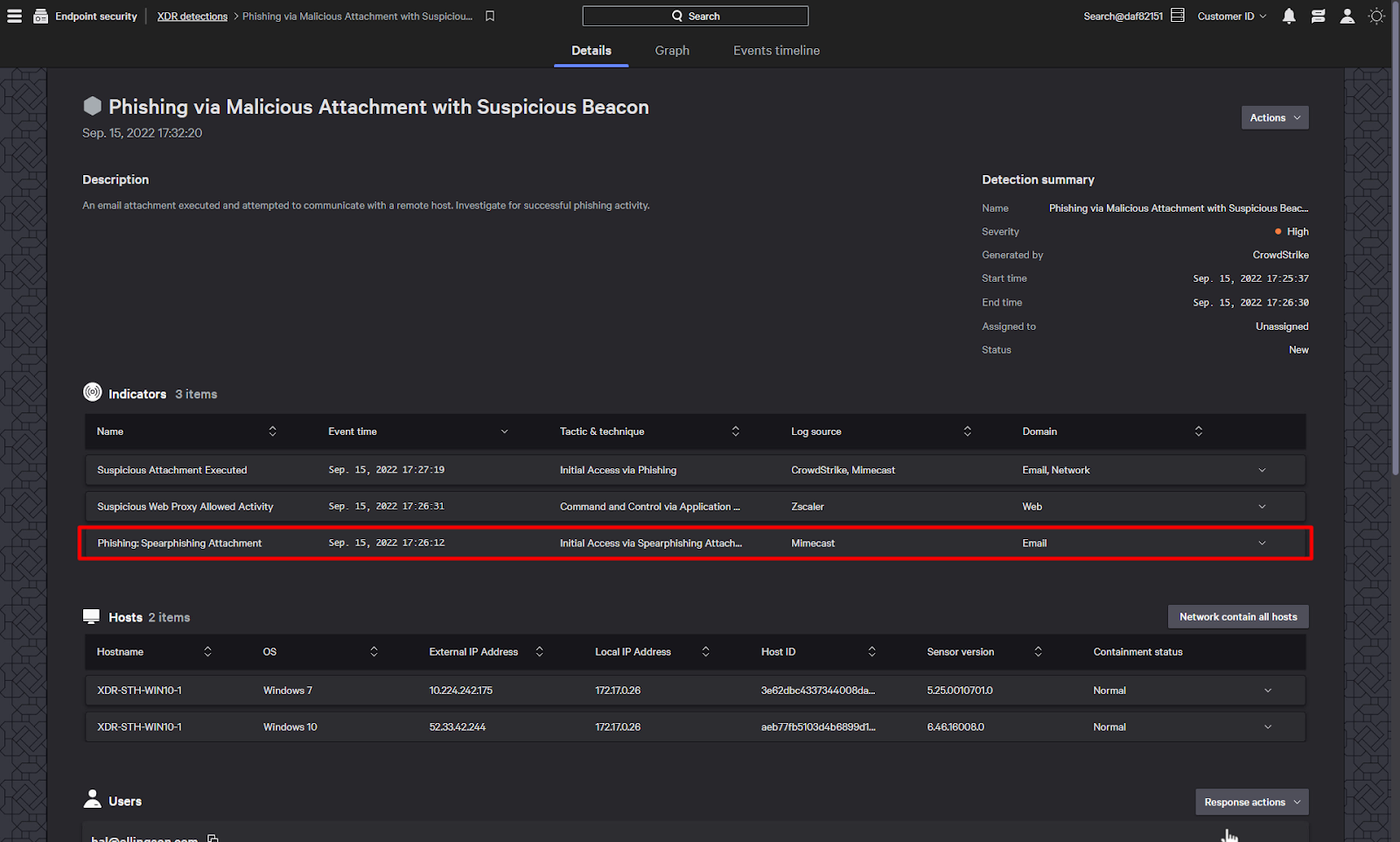
It all started with a suspicious email attachment that was identified by Mimecast, which provides email security.
Next we can see that the attachment was actually opened, which, of course, is pretty concerning.
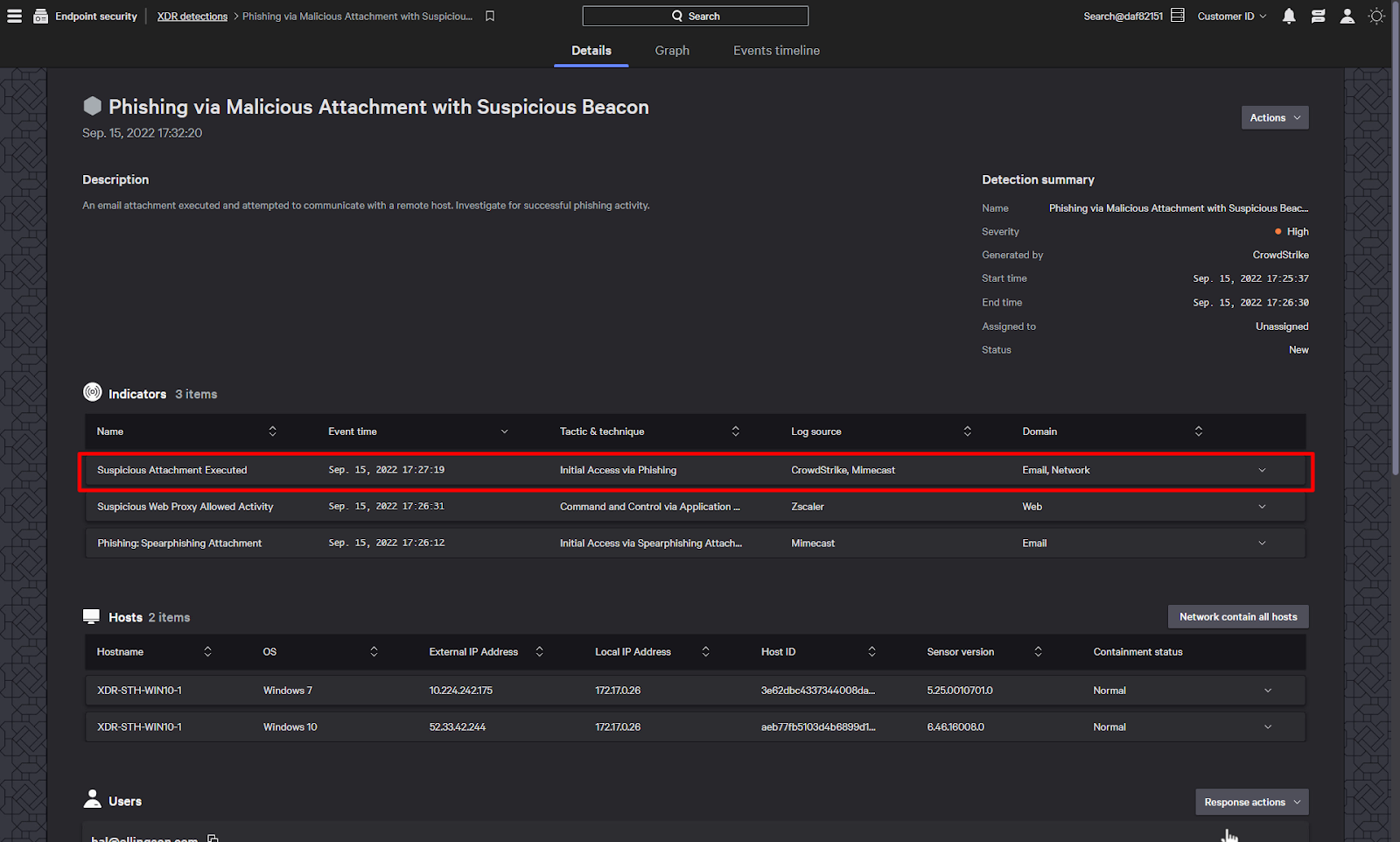
There is also a suspicious indicator from the Zscaler web proxy. This shows that after the attachment was opened, the endpoint reached out to a suspicious IP address.
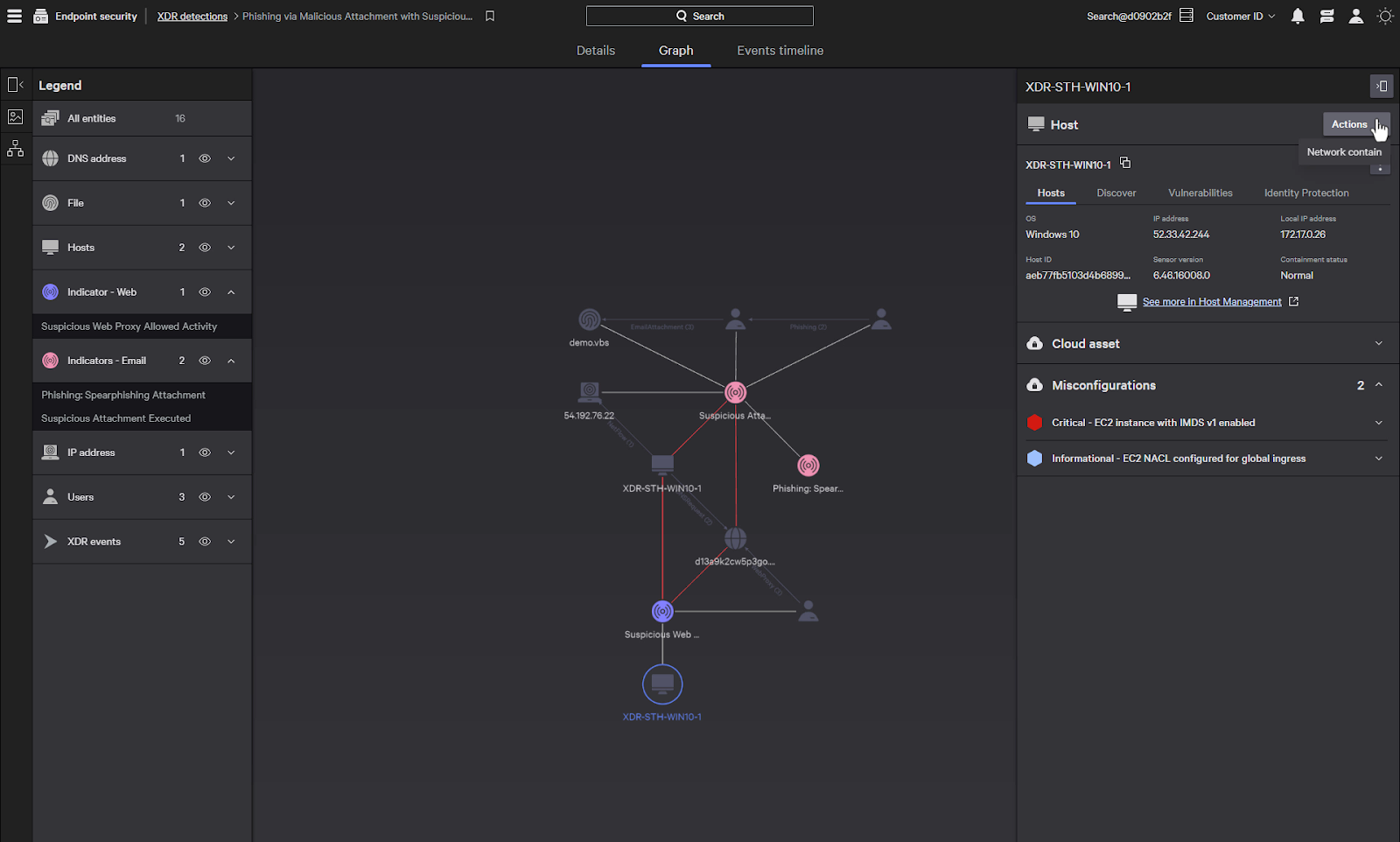
Information about the hosts are listed and there is the ability to network contain them all to sever any outbound communication.
Any users that have been identified as being associated with this detection are also listed since compromised identities are a frequent vector for attack.
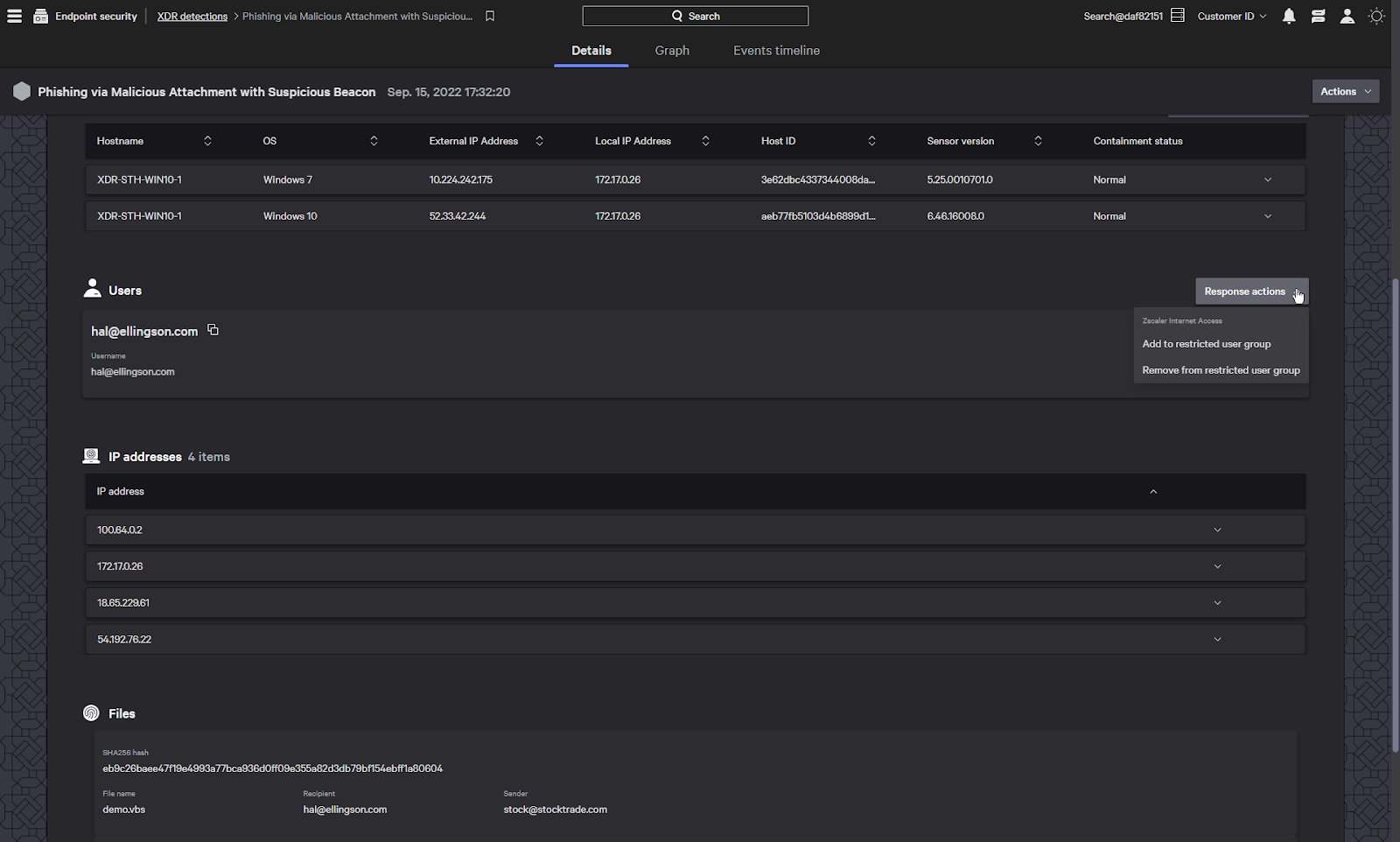
CrowdStrike XDR is also able to perform response actions directly on third party devices from the interface.
For example, we can add the user to a restricted user group on the zscaler web proxy to block their access to corporate resources.
CrowdStrike also includes the ability to visualize the incident in a graph view.
The graph details the interaction between the elements associated with this detection and can provide insights into the nature of the attack.
A legend provides a quick guide to the objects on the graph, or we can interact with the graph directly.
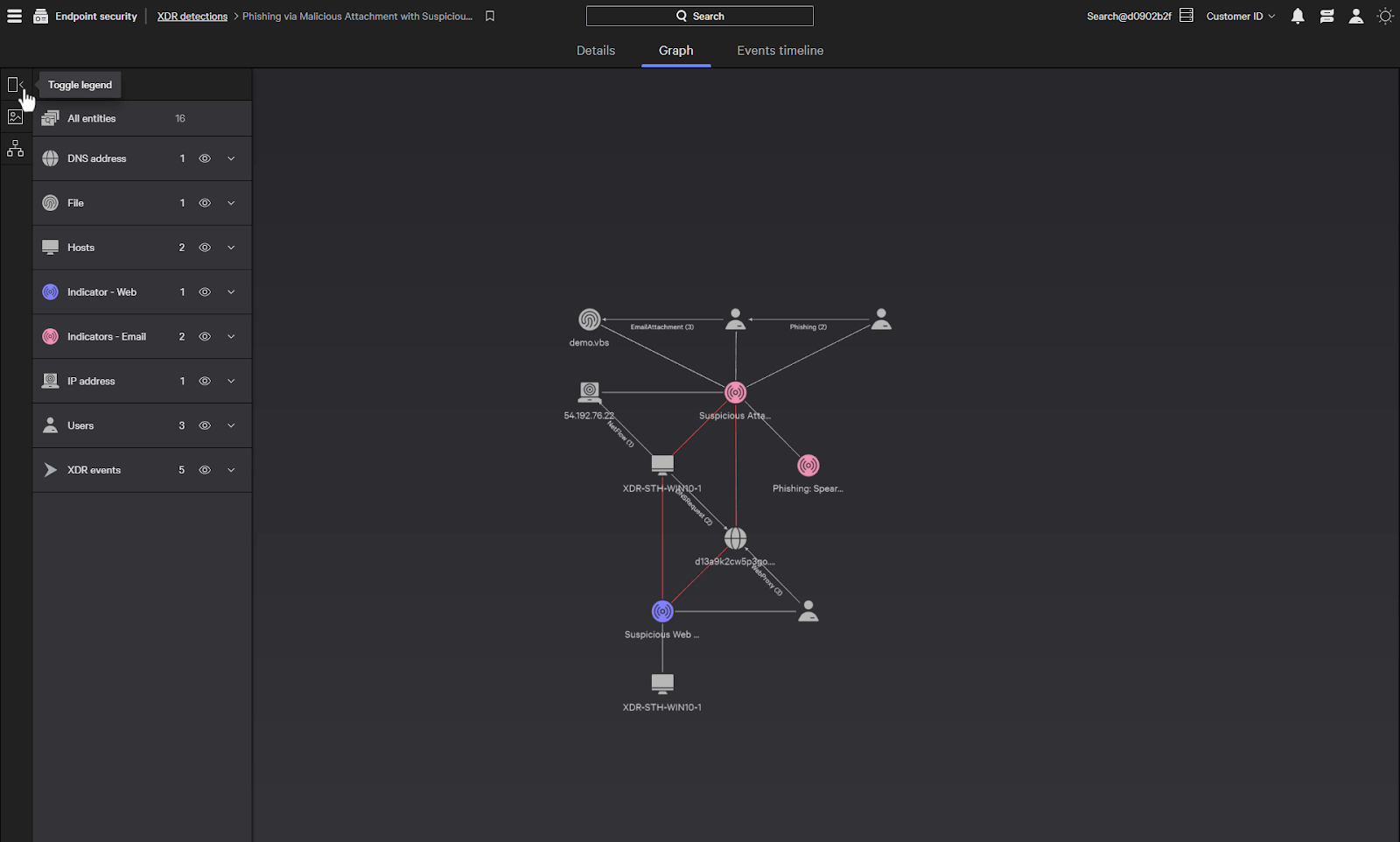
We can still see our indicators from the Details view, but the graph view also provides enriched data from the XDR events and hosts information.
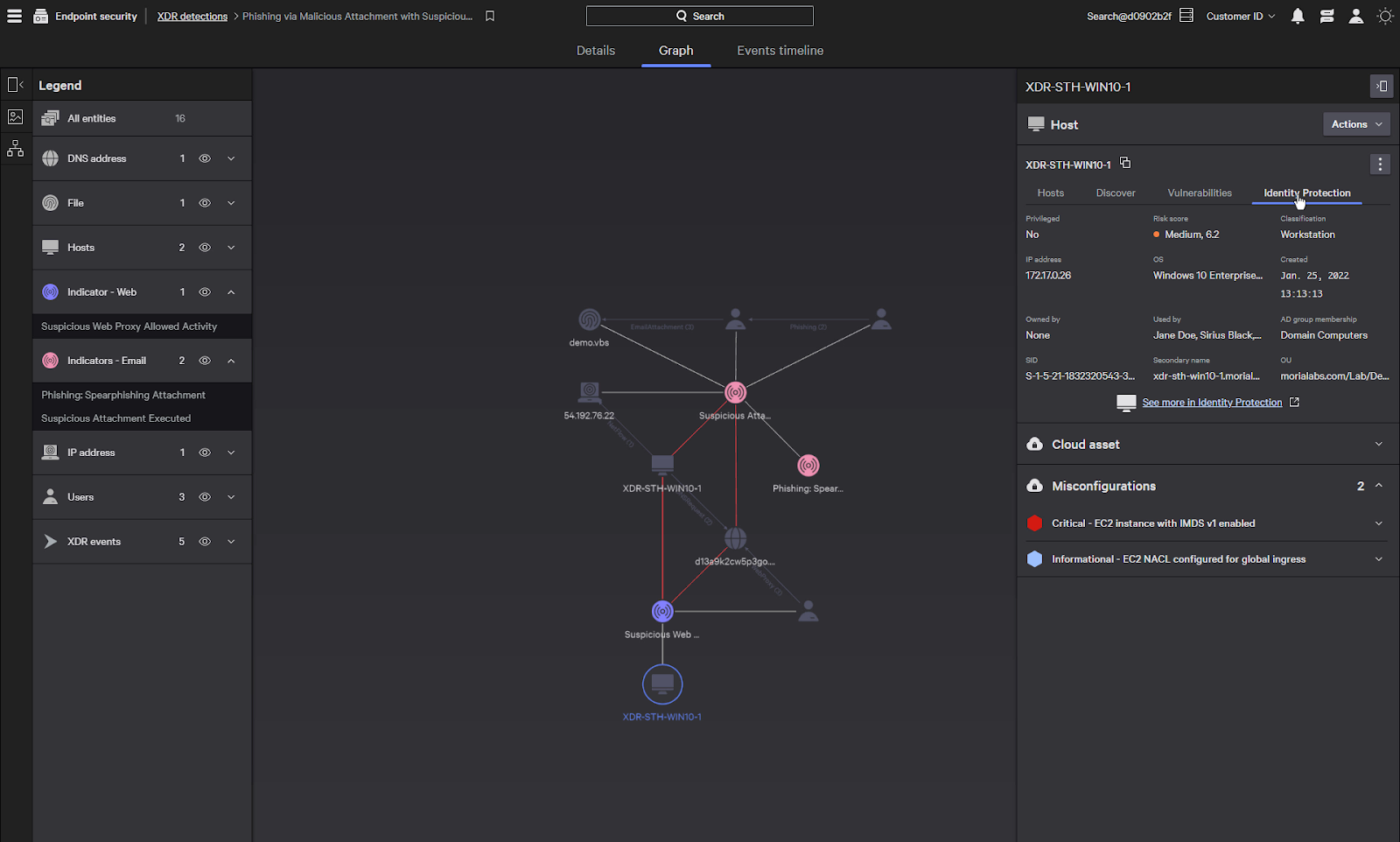
Let’s start by taking a look at the host that this detection is centered around.
When we select the host, we can see information about the host and there are also several actions that we can take.
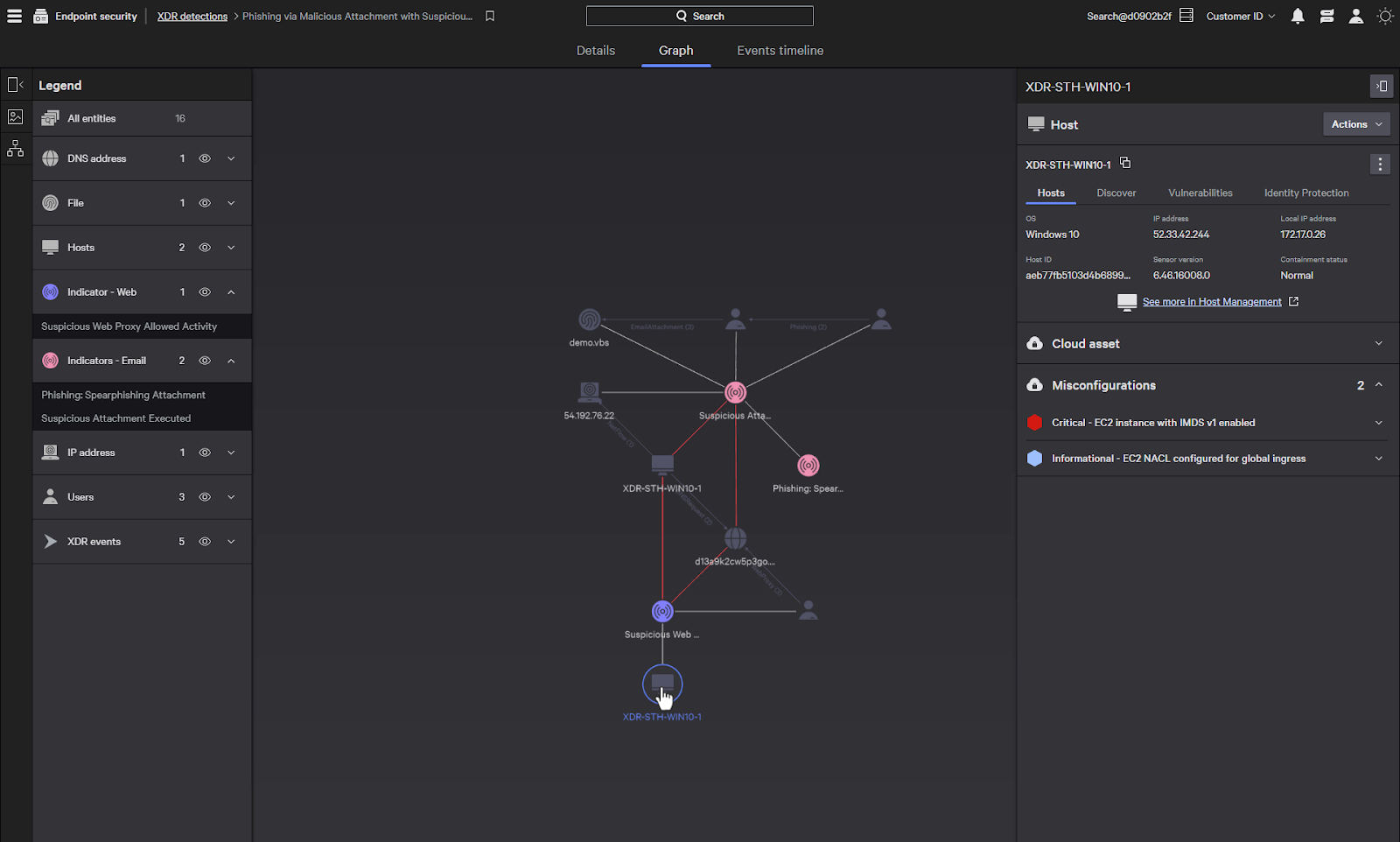
Any cloud misconfigurations are shown here which allows you to find and resolve cloud security issues.
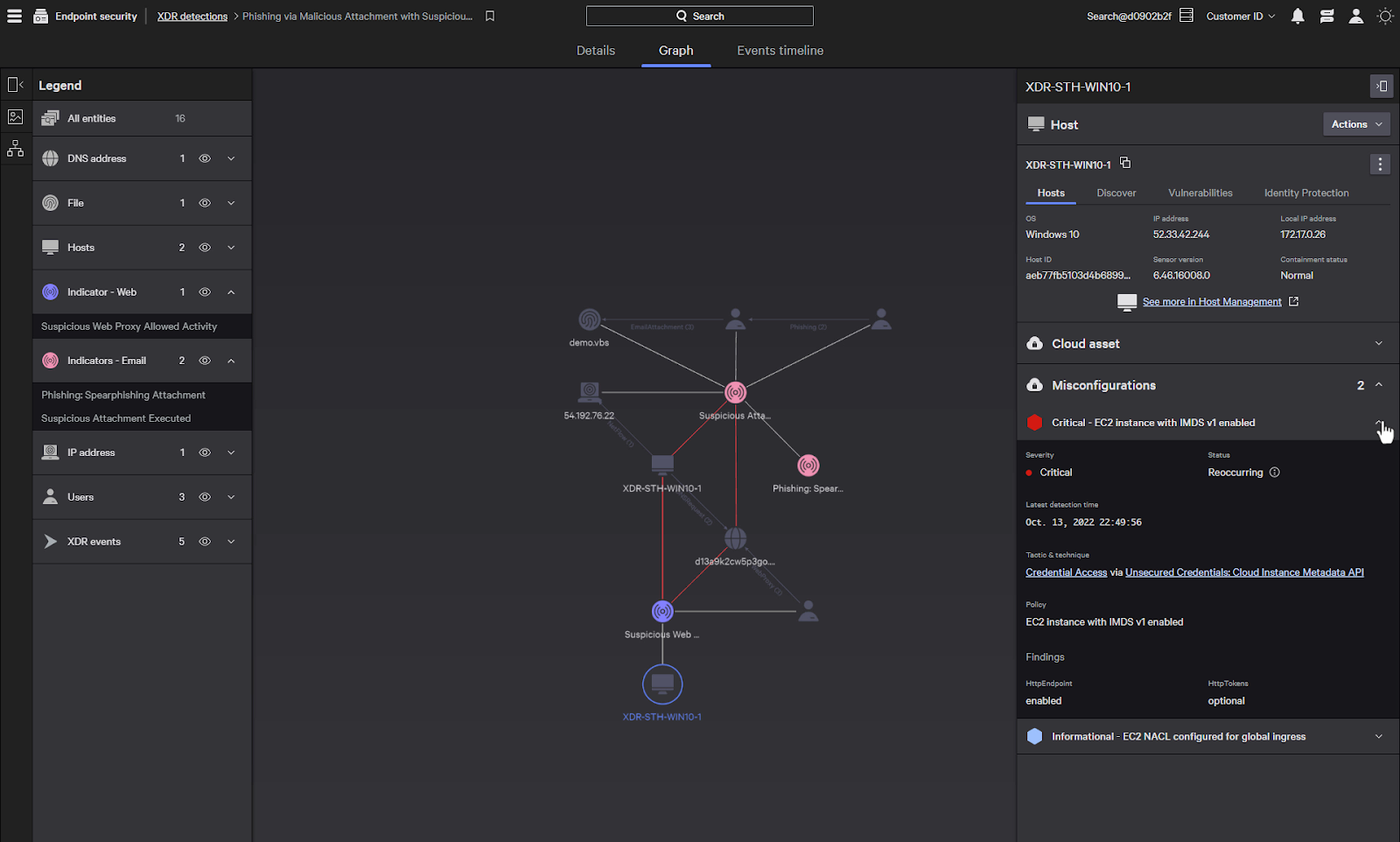
The three dots give us multiple actions we can perform on the host. We can connect to the host to run remote commands and perform searches on the host, as well as pivoting to other views about the host such as asset graph and logon info.
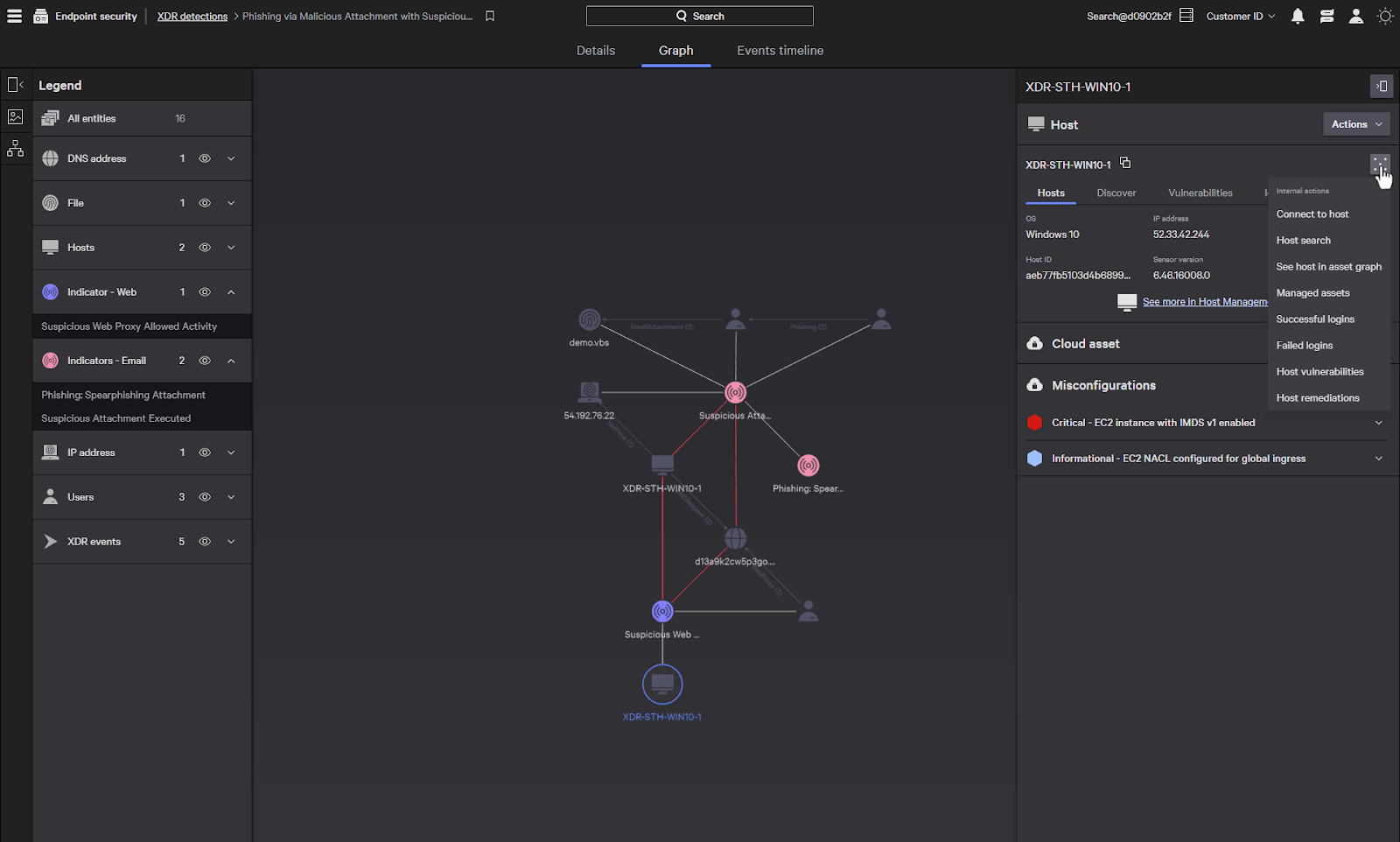
We can also perform a network containment of the host to prevent further lateral movement or communications with external entities, such as a remote command and control server.
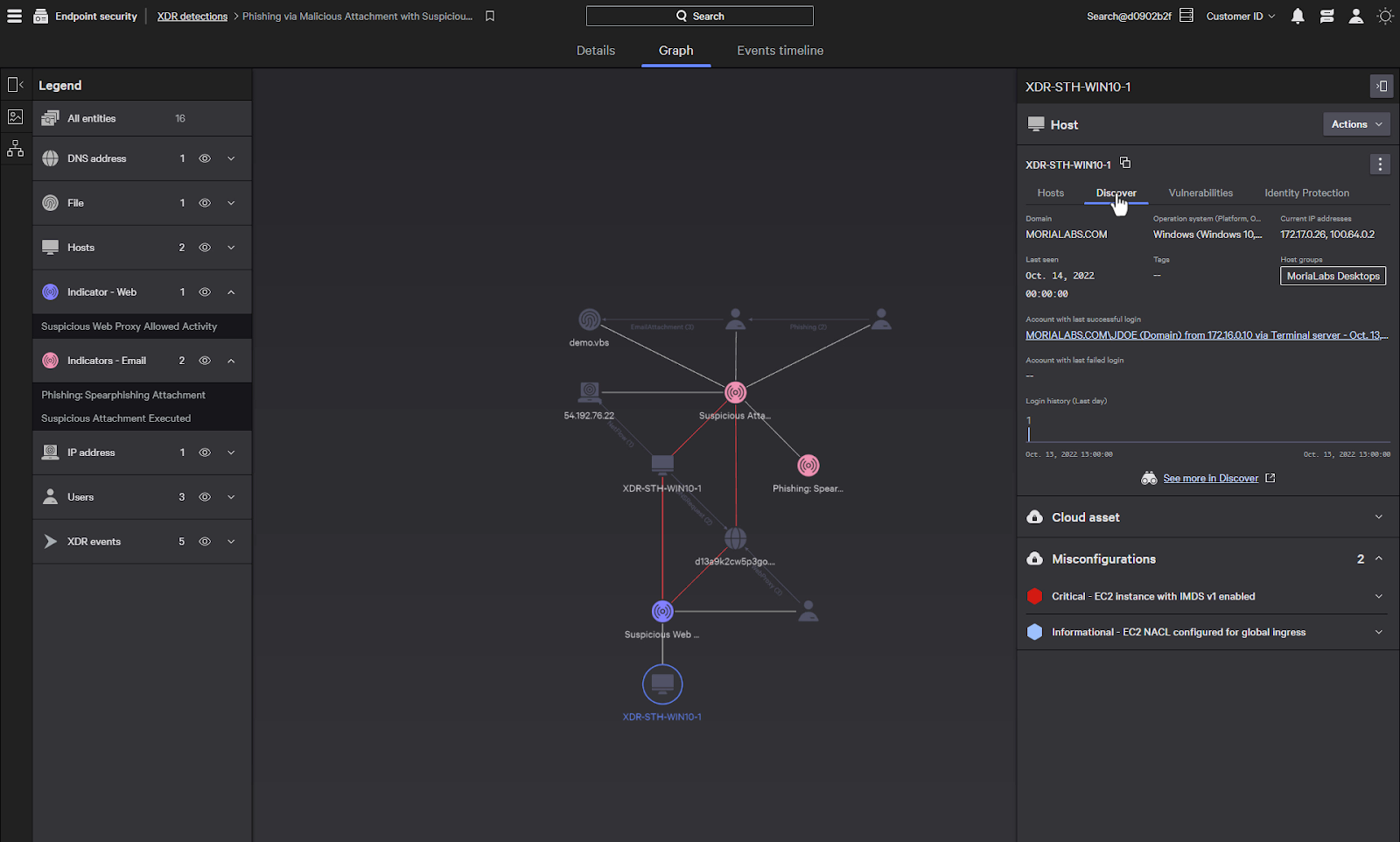
Also associated with the host is Discover information that provides IT hygiene that allows you to inventory systems, applications, and users.
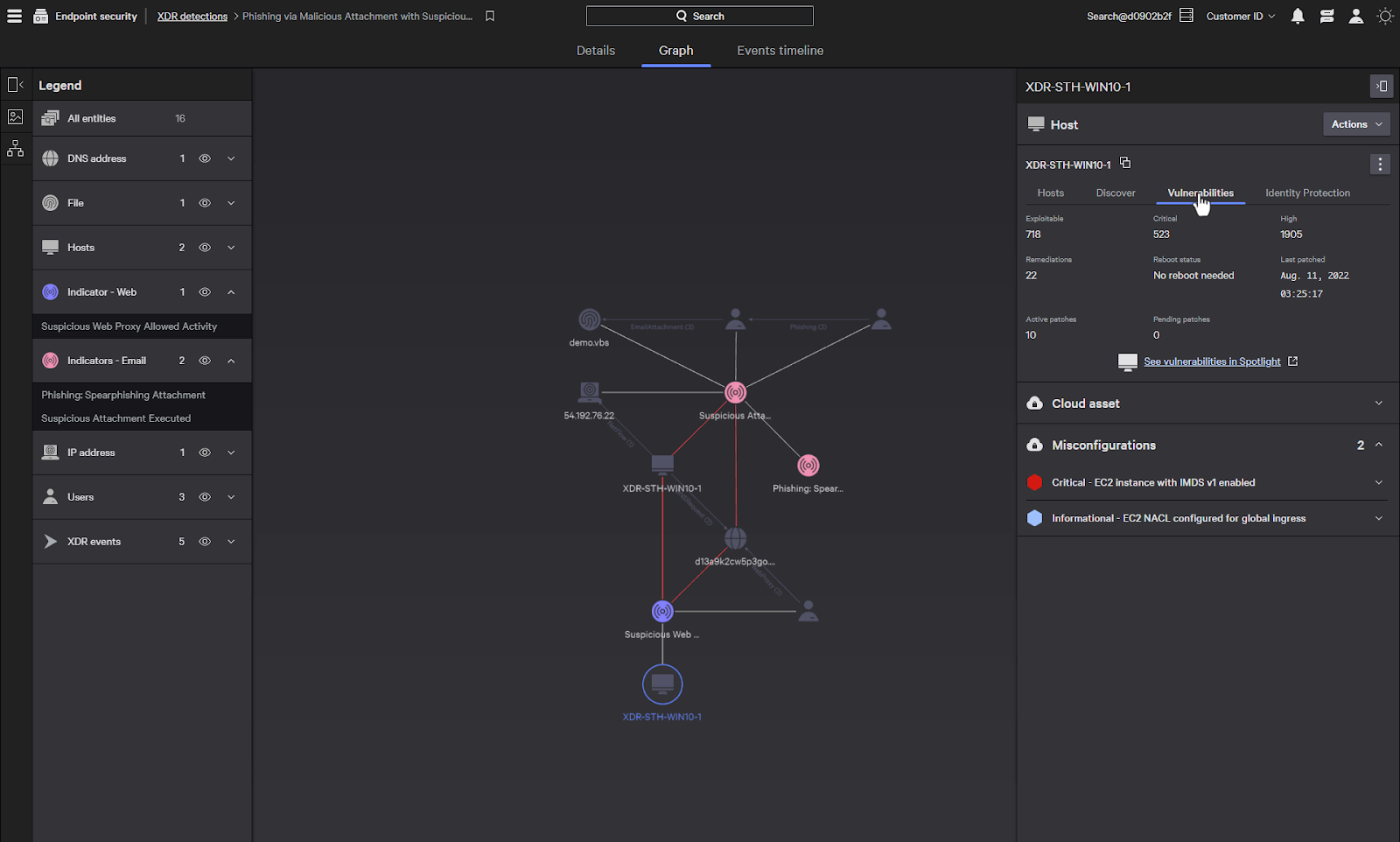
Under vulnerabilities, it displays an overview of the vulnerability information of the system. A pivot directly to Spotlight shows a detailed view and allows for easy patching of the system.
CrowdStrike Falcon Identity protection is also integrated directly with Falcon XDR.
Compromised identities are one of the leading causes of breaches,
So identifying risks and threats to a user’s identity can help avert attacks such as credentials being stolen and leveraged to gain access to the environment.
Now let’s take a look at some of the XDR events.
Clicking on the email attachment event brings up details of the email from Mimecast.
Even if endpoint security can detect the execution of a malicious email attachment, it would have a hard time providing the details of the originating email.
But with Falcon XDR, it has enriched the detection with the attributes of the email, including data such as the sender and recipients.
This could help us find the scope of the attack by identifying all the recipients that have received an email from this sender.
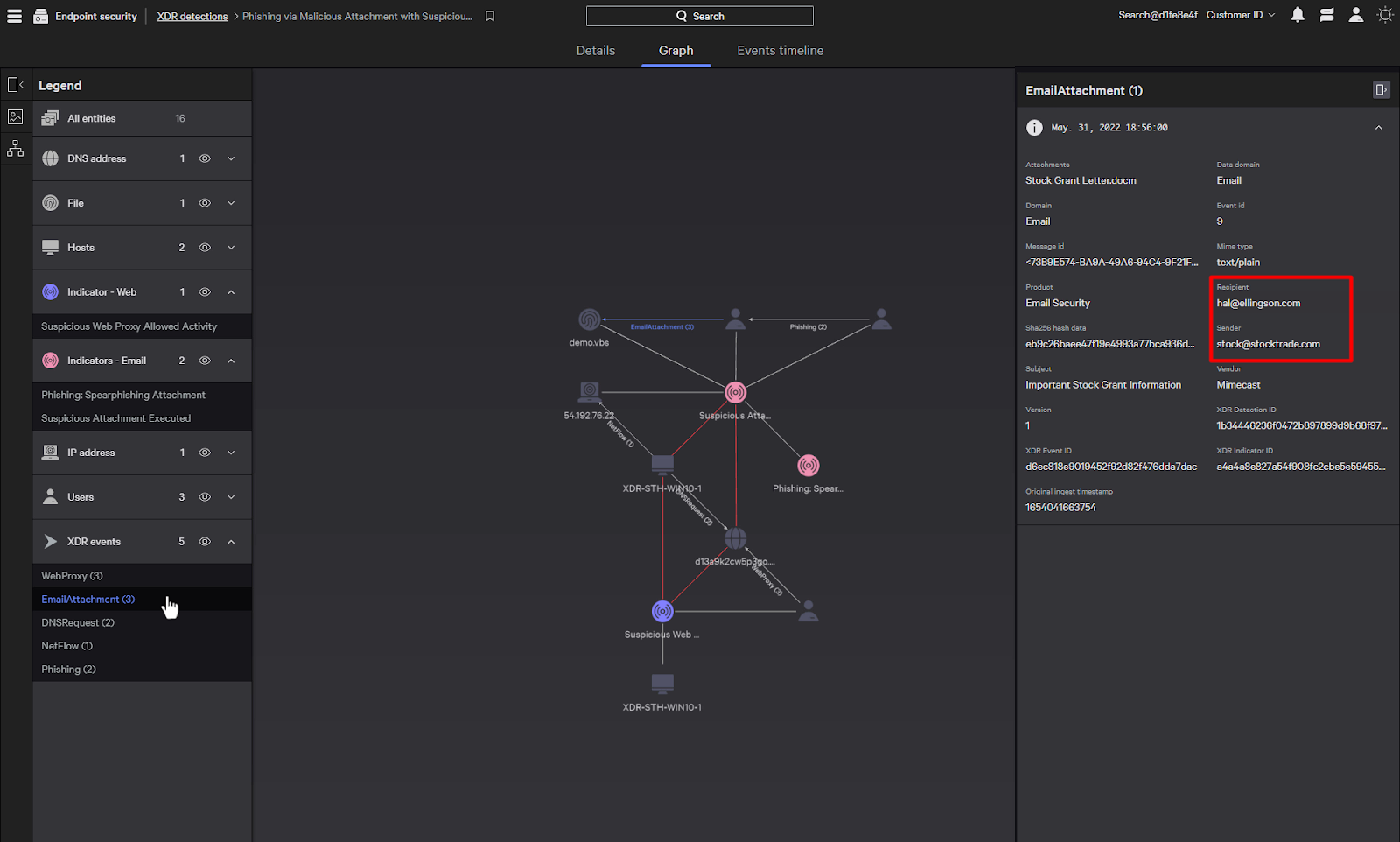
And from there, we could take additional precautionary steps such as verifying that no one else had executed the attachment or detect future emails from the sender.
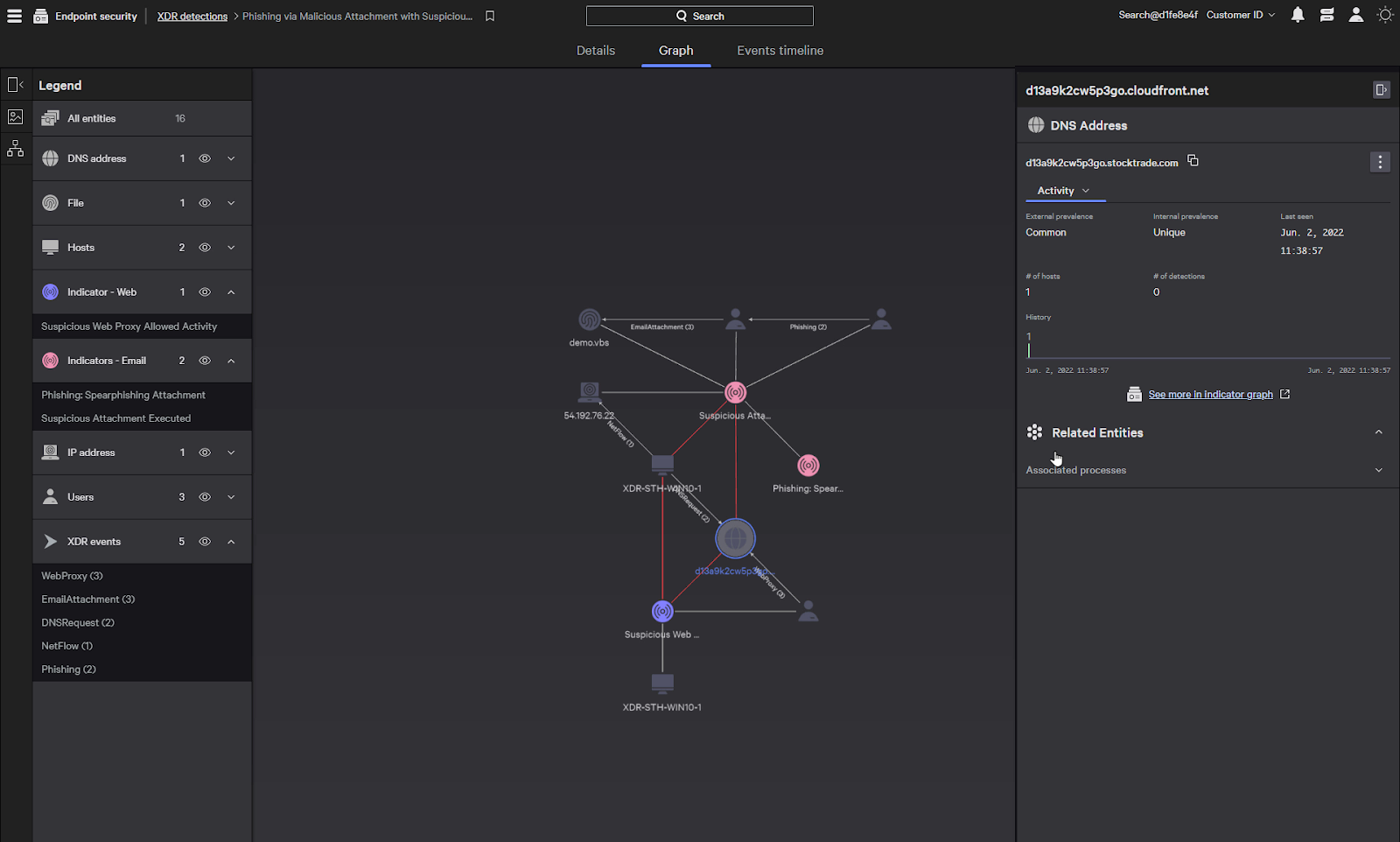
We also see a domain that the system reached out to. When we click on it, it’ll show additional details of the domain from the host.
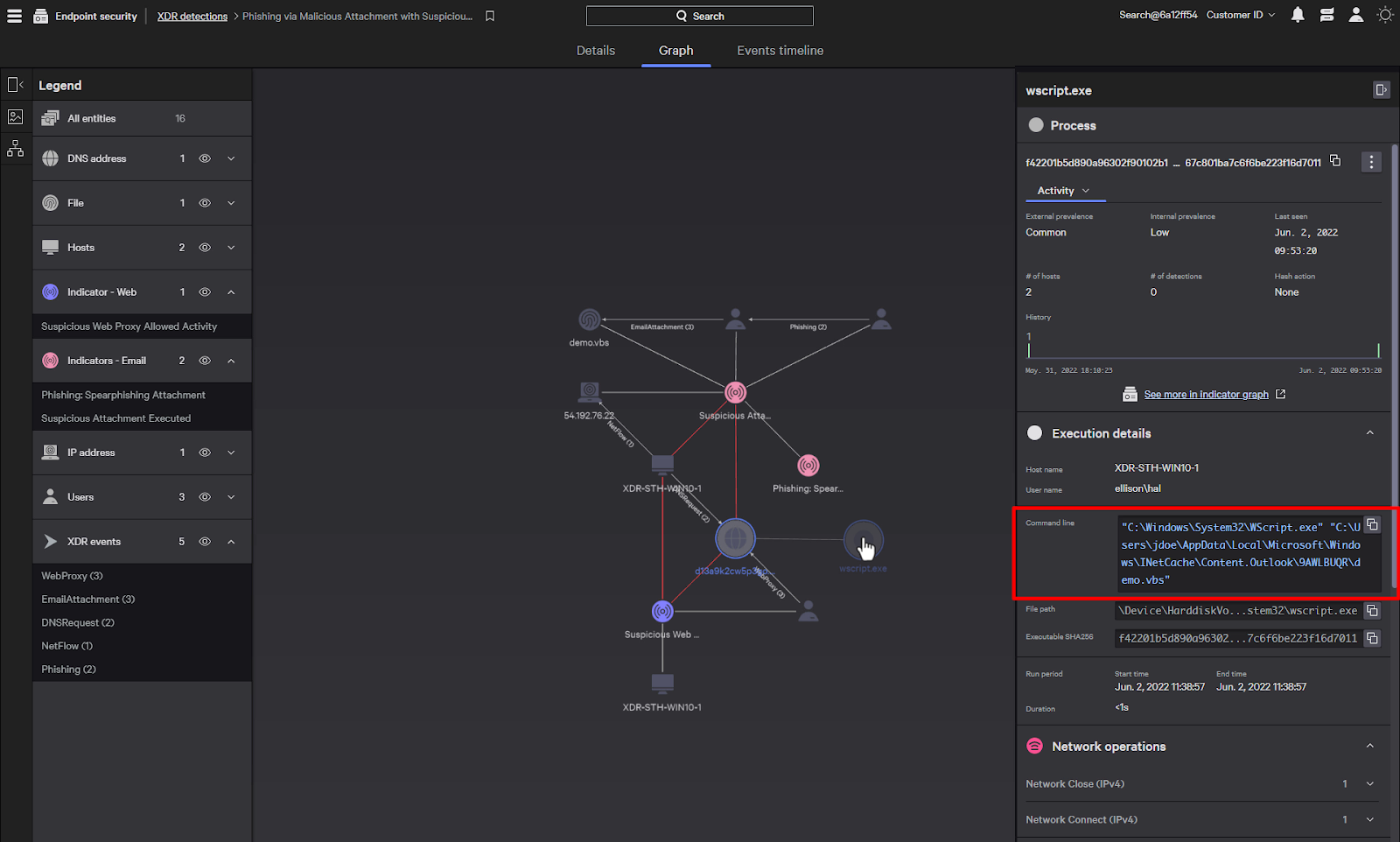
Here’s a list of all the processes running on the host that have communicated with the domain. We can add these additional data elements to the graph to further investigate the process tree.
Clicking on the new process element can provide details such as the full command that was executed or the genealogy of the process, like its parent or children processes.
Next, let’s take a look at our web proxy events provided by Zscaler.
Those events lead to this remote system.
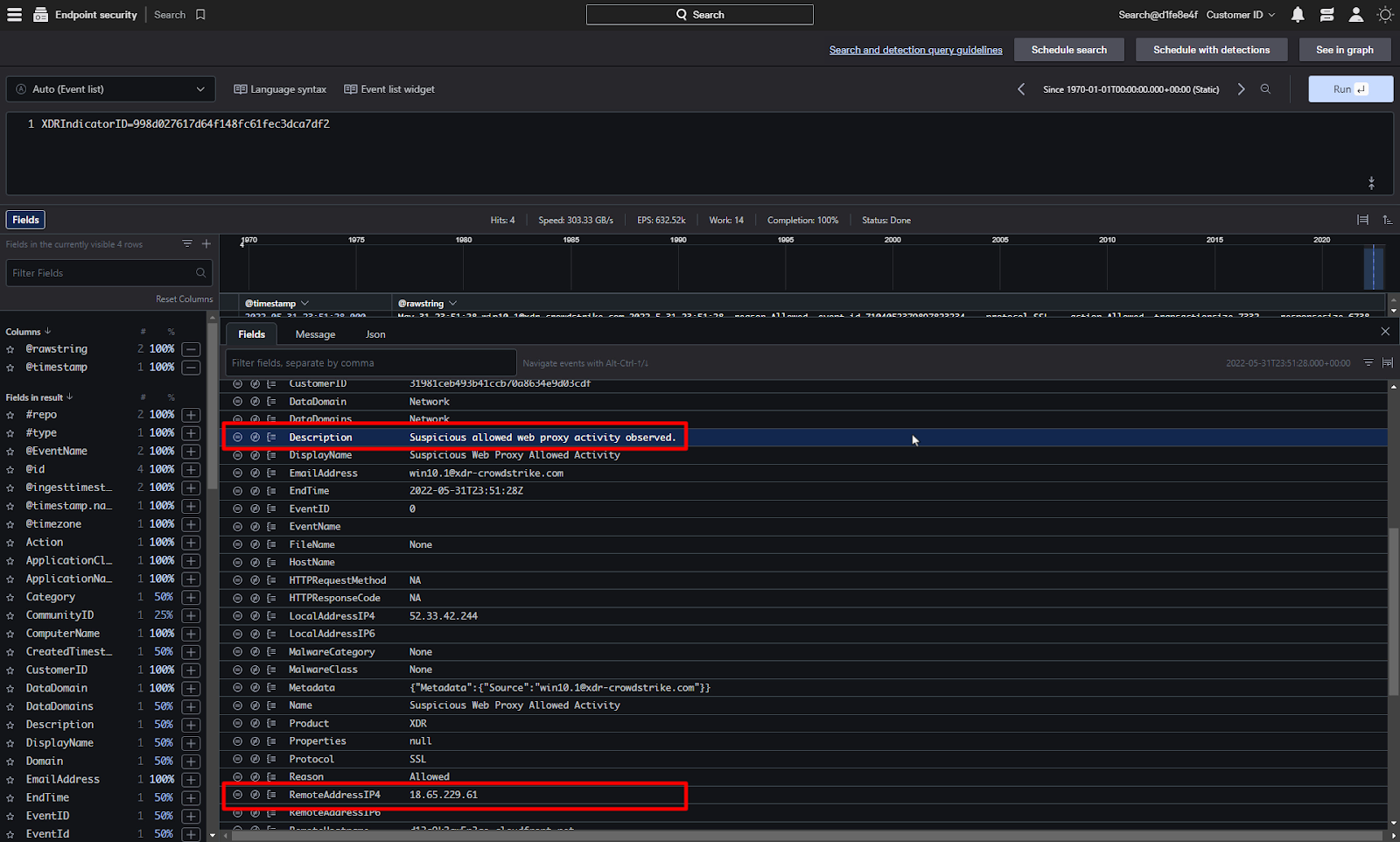
The IP address associated with the remote server was identified by the indicators as being suspected of connecting to a command and control server. We can see the actual event message with the See Event Details.
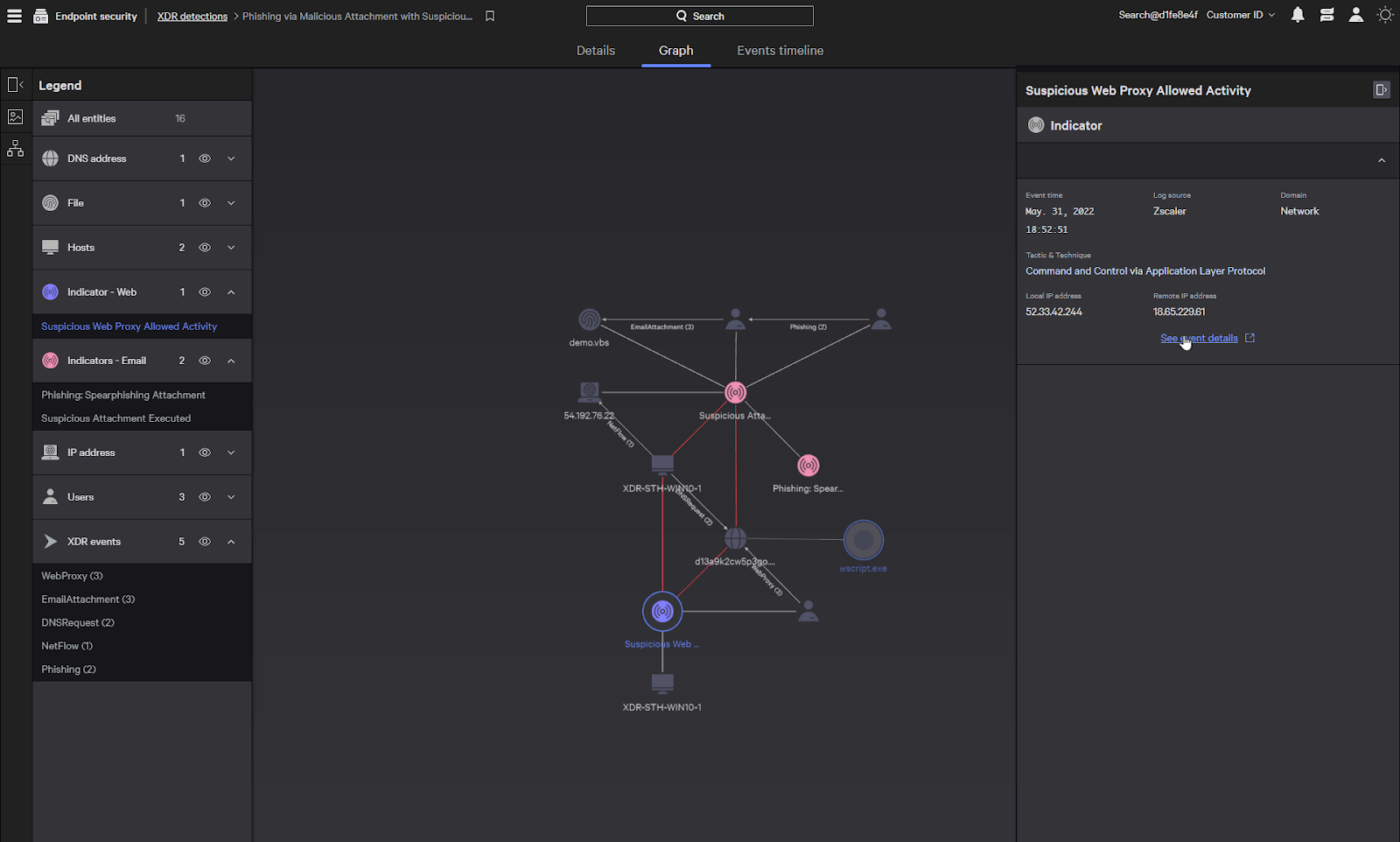
This will bring us directly to the associated events in XDR search.
The event data from the various security devices can be seen here in its RAW form, but we can also select an event to see it as an organized table.
Falcon Insight XDR aligns the data to an XDR data schema to simplify correlation. IP Addresses or file hashes will be aligned across all security devices. This allows for CrowdStrike to use its wealth of security expertise to detect threats leveraging all the intelligence data available.
This event shows that there was suspicious activity detected by the web proxy going to this remote IP Address.
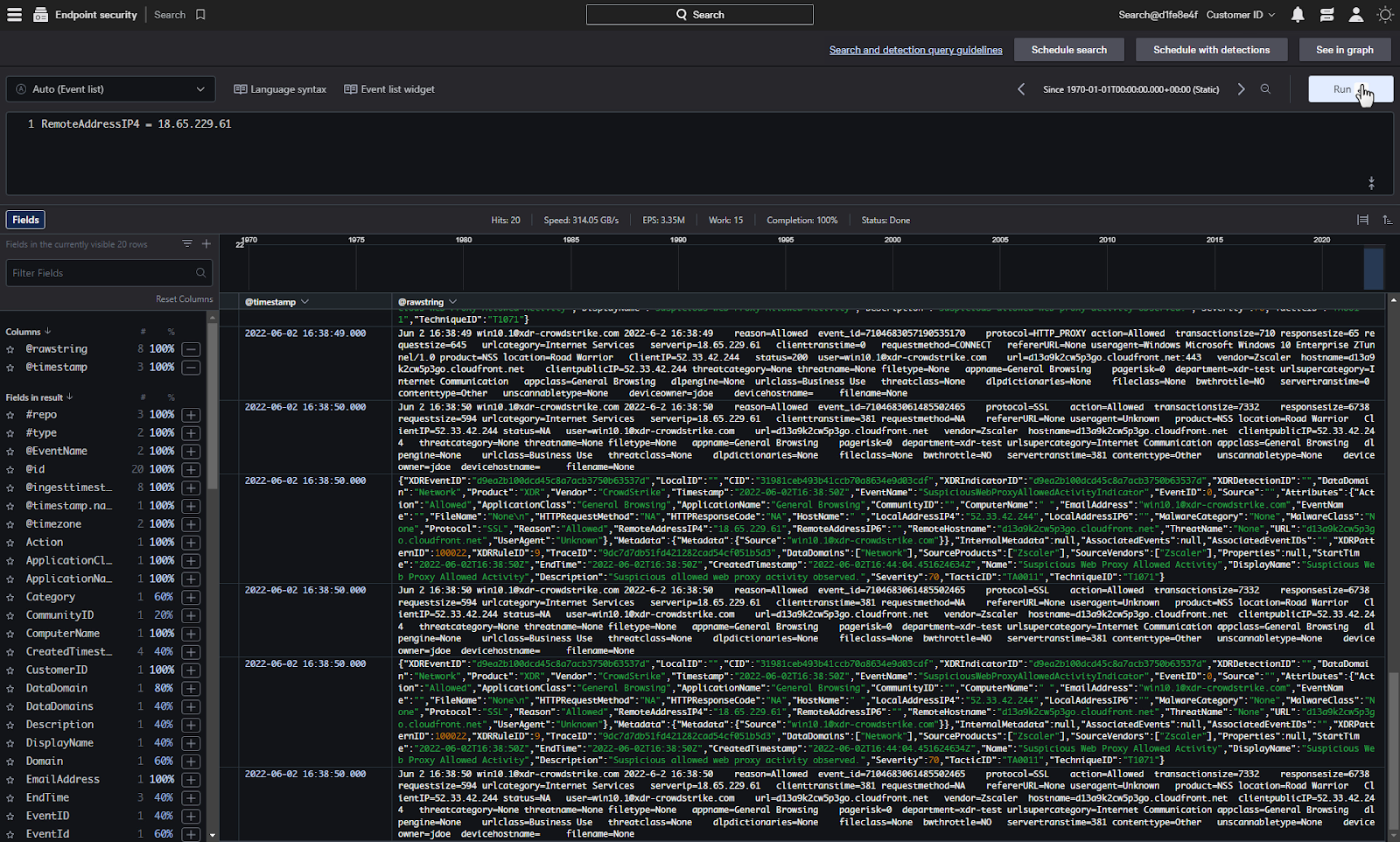
Now, let’s say that we want to find any other communication with this suspicious address going forward and create a detection automatically, we can dynamically modify the search by clicking on this icon.
This will put the search criteria for the address up top into our search bar.
Now we just need to remove the XDR indicator string and viola, we’ve got a search pattern for any hosts connecting to the suspicious IP address.
To create a detection, all we need to do is click on the XDR detection button, which will automatically populate the XDR query creation screen.
Now we just need to give it a name, select a severity, and we can also provide it with an optional MITRE tactic and technique.
Aligning to MITRE can help provide context for the detection when it’s viewed later.
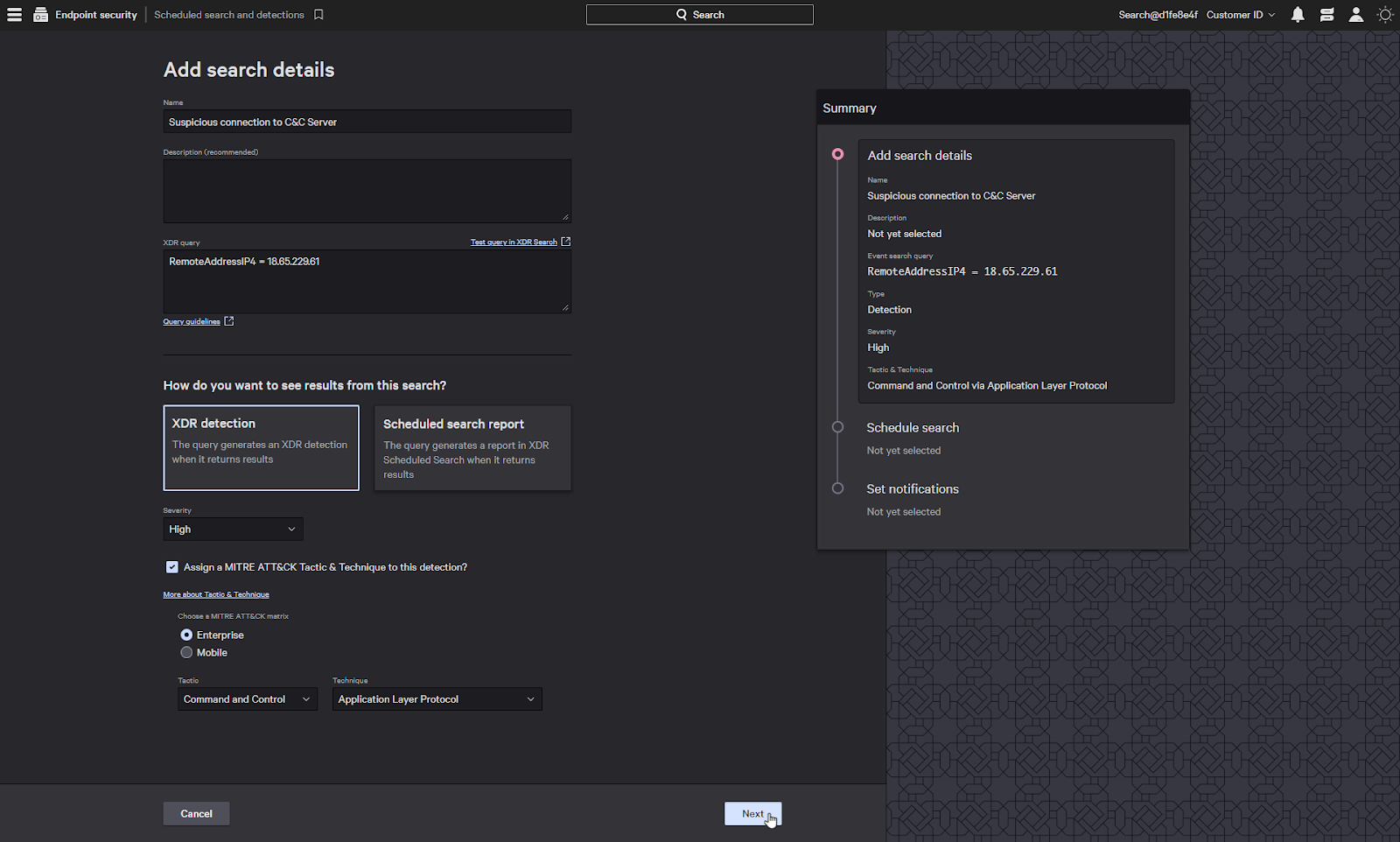
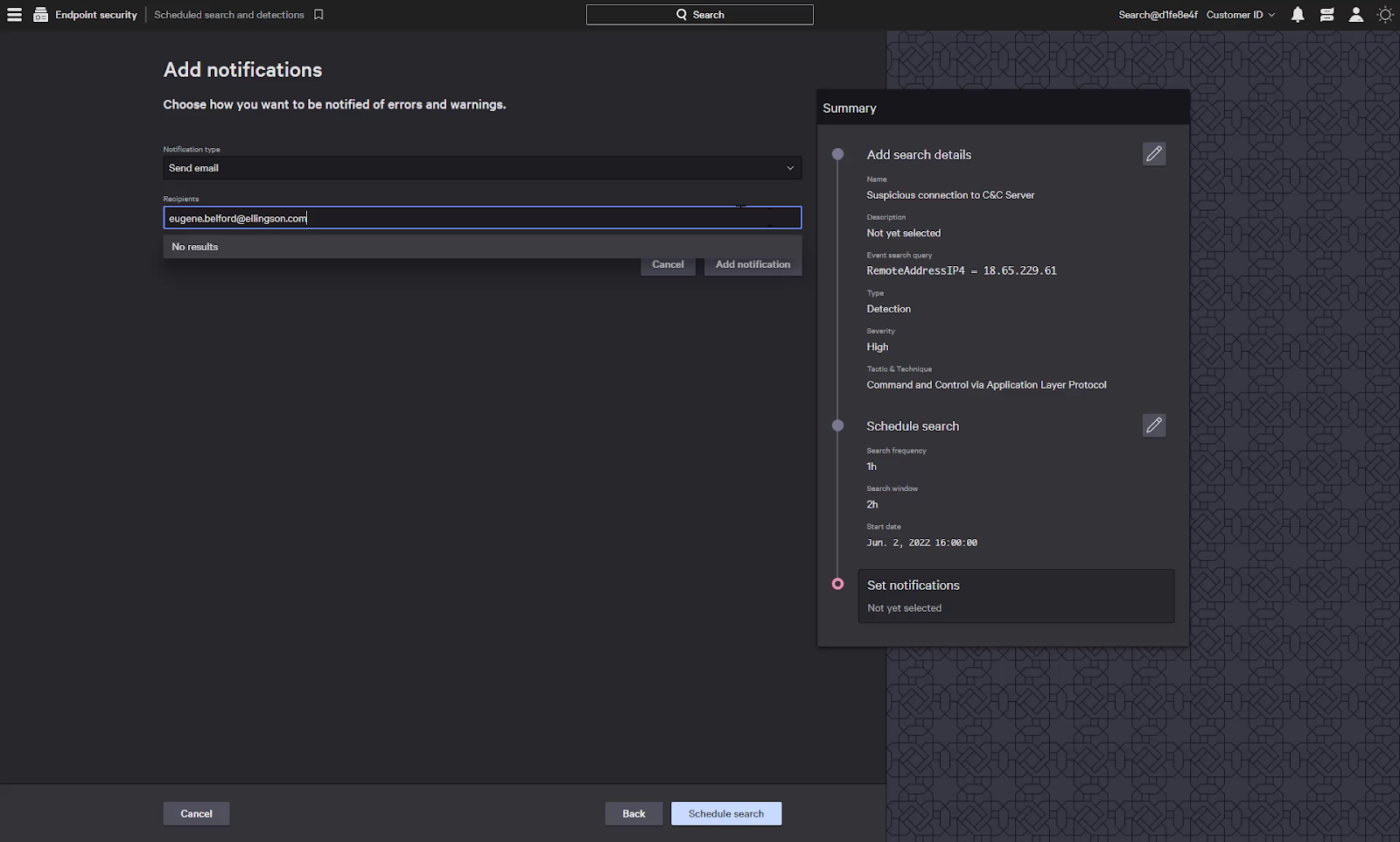
Next we can provide it with a schedule, and finally select a notification type.
When a detection is created, we can send an email or utilize a third party communication platform such as Teams or Slack.
We’ll just put in an email address and click add notification.
Conclusion
After that, we just need to click Schedule search and we’re all done. Any new connections to that suspicious IP address will notify us and create an XDR detection.
Falcon XDR improves our ability to detect threats by bringing together security devices across multiple domains into a single platform. CrowdStrike does all the work to align the data and provide the detection intelligence, which strengthens your security posture and stops breaches.