Exposure Management – Alerting and Response for Malicious Apps

Alerting and Response for Malicious Apps
Summary
In this guide, you’ll learn how to automate alerting and response actions for suspicious applications within your organization.
Investigating Misconfigured Asset with FEM
Organizations are increasingly vulnerable to sophisticated threats, underscoring the critical need for advanced alerting and response mechanisms for malicious applications. Traditional security measures often fall short in detecting and mitigating the stealthy maneuvers of malicious applications, leaving enterprises exposed to potential data breaches and extended recovery times.
Falcon Fusion and Falcon Exposure Management work in tandem to automate the detection and containment of suspicious applications, significantly enhancing cybersecurity responsiveness.
Create Application Group
Start by clicking the menu button within the Falcon UI, select Applications -> Dashboards under the Exposure Management tab.
Within the applications dashboard, you will find key metrics for your managed asset applications such as those most used, installed, and suspicious.
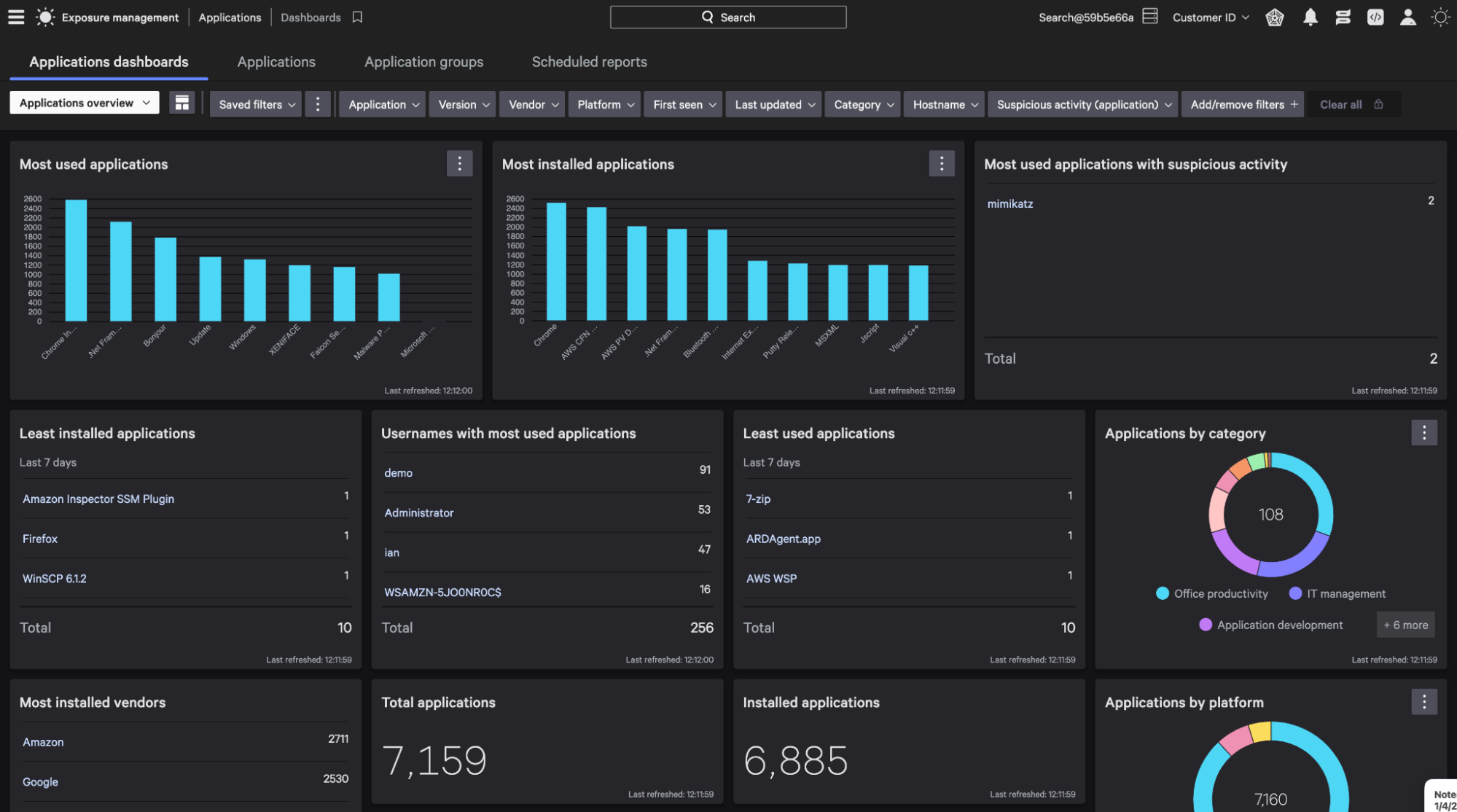
In this example, the application mimikatz, is the most used application with suspicious activity.
To begin creating an automated alert and response for mimikatz, select Application groups. Then “Create application group”.
Create Application Group (Modification)
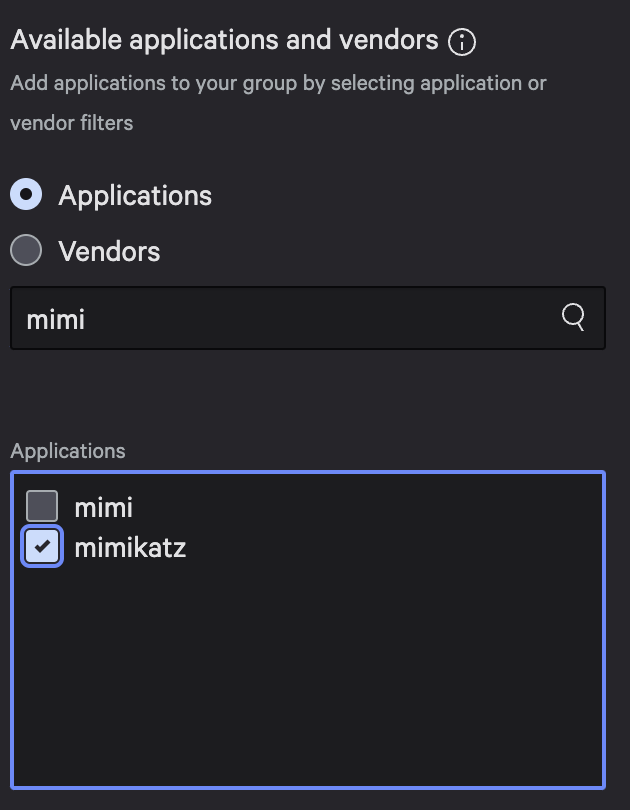
Next, provide a name for your application group. Select the specific application that you would like to populate the group.
In this example, we will look for the application mimikatz.
Fusion Playbook
With the application group in place, leverage Falcon Fusion to create a customized playbook for automated alerting and response for the mimikatz application.
Click the menu button within the Falcon UI and select Fusion Workflows.
Select Create Workflow, then Create workflow using playbook.
Playbook Modification
Next, set the trigger for the application installation asset management value.
Now select the trigger that sends an email notification when an unauthorized application is installed.
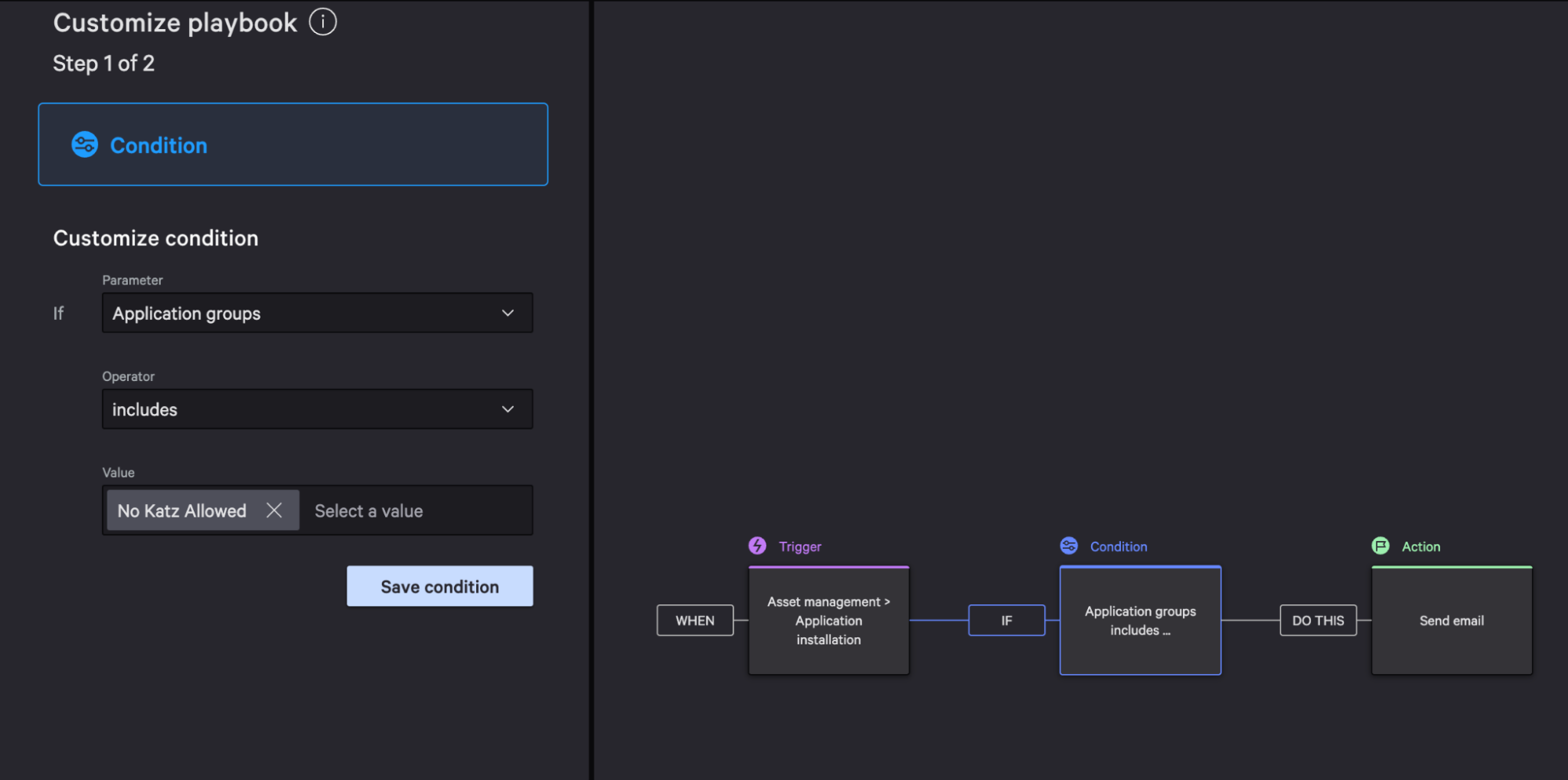
Select customize playbook.
Within the Condition, set the value to your previously created application group name. In this example, our value is No Katz Allowed.
Contain Device
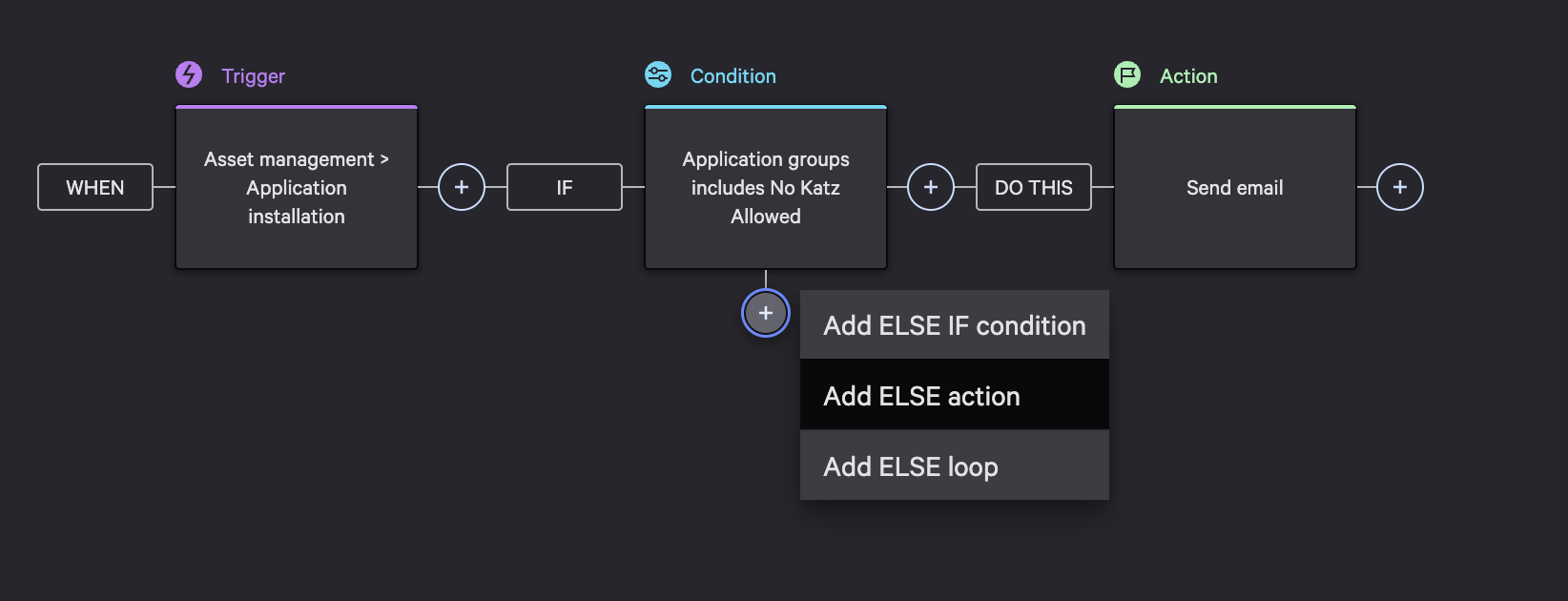
Next, select the plus symbol under the condition box on the workflow graph and select Add ELSE action.
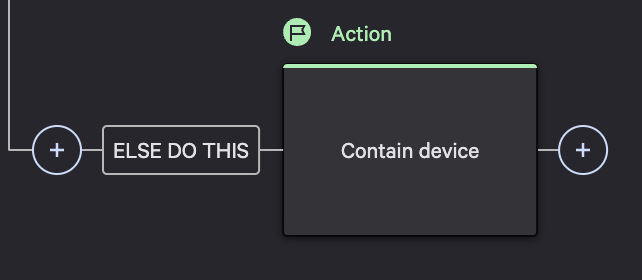
In this example response action, we will contain the device which will perform a containment action on a host to block all network activity.
Workflow Naming
As a final step, click finish, update your workflow name and set the status to on.
An alert and response action is now set for the mimikatz app on your managed assets.
Conclude
With Falcon Fusion and Exposure Management, you experience streamlined efficiency that reduces excessive alerts and automates response actions. This integration saves valuable time and effort for your IT teams, enhancing their focus and productivity.