Exposure Management – Creating Configuration Assessment Rules

Creating Configuration Assessment Rules
Summary
In this guide, you’ll learn how to create custom configuration assessment rules for your assets.
Investigating Misconfigured Asset with FEM
Falcon Exposure Management by CrowdStrike proactively pinpoints misconfigured assets, a crucial factor in tightening an organization’s security framework. The platform emphasizes swift identification and rectification of configuration flaws through thorough assessments, enabling a fortified cybersecurity defense and risk mitigation.
Configuration Assessment Dashboard
Click the menu button within the Falcon UI, select Configuration Assessment under the Exposure Management tab.
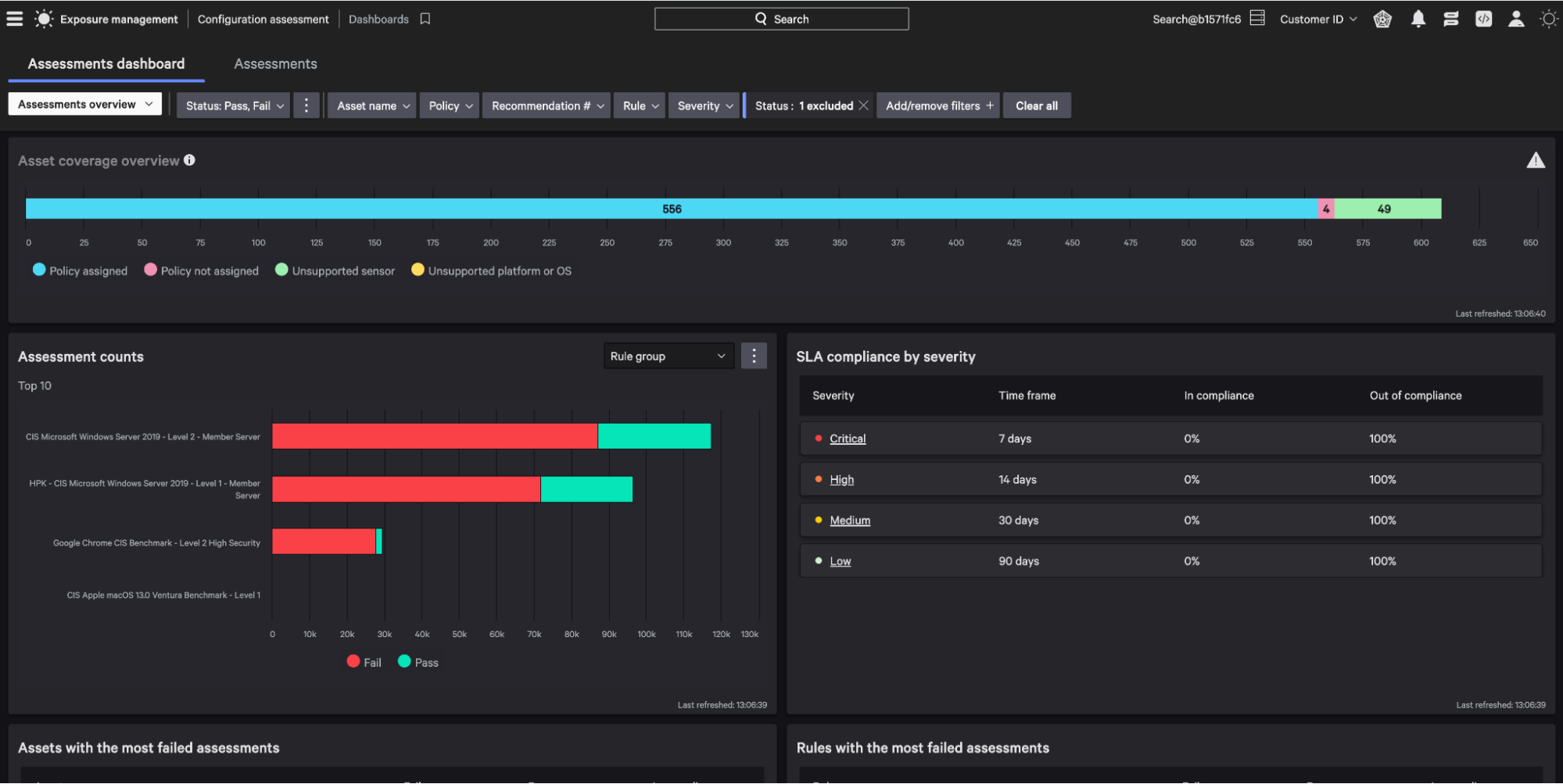
Start creating your configuration rules by pivoting to the Rule groups tab within the Falcon Menu.
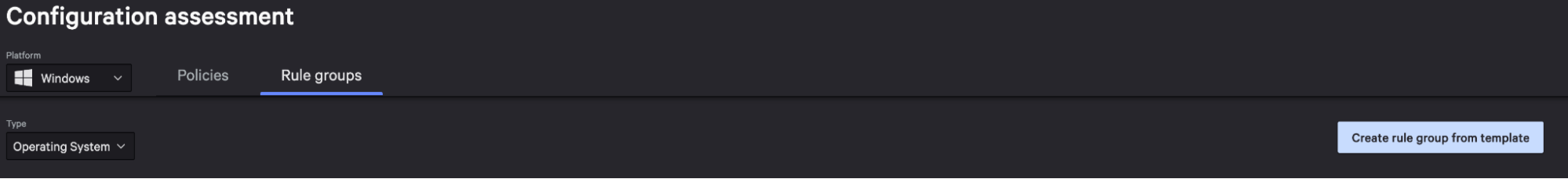
Rule Group Templates
Rule Group: A collection of rules that provide recommendations for security requirements. You can modify the rule groups CrowdStrike provides based on existing standards published by third-party authorities.
Here, you have access to templates of CIS standards to track common configuration requirements. Select a template for modification and click Continue then Create.
Rename your rule group using the Edit icon.
Next, select a rule section. In this example, choose the “Account Lockout Policy”.
Rule Group Editing
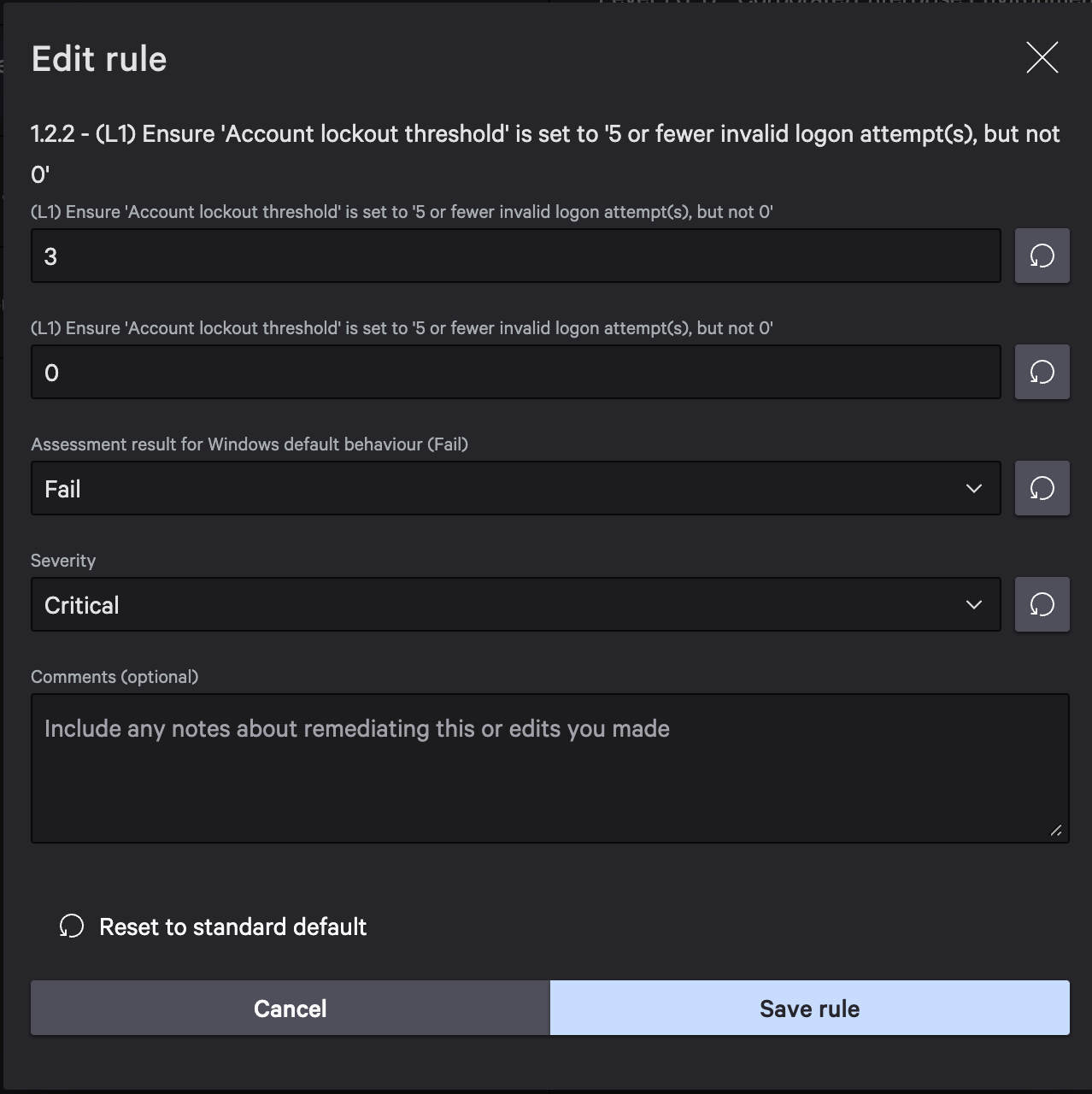
Within the details, you will find the recommended configuration for this rule. At the moment, all assets susceptible to this rule must allow 5 or fewer invalid login attempts. To make an adjustment, select edit rule.
In addition to the lockout count, the assessment result and severity can both be adjusted.
Change lockout count to 3 and select “Save Rule”.
Create Policy
Next, you must create a custom policy to add this newly created rule group to. From the Falcon menu, select Policies then Create Policy.
After inserting your Policy name, refer to the rule group you created when selecting your platform.
In this case, we will select Windows and click “Create Policy”.
Policy Assignments
In order to initiate your newly created policy, you must assign a specific host group. In this example, choose the FEM Systems – Golden Template.
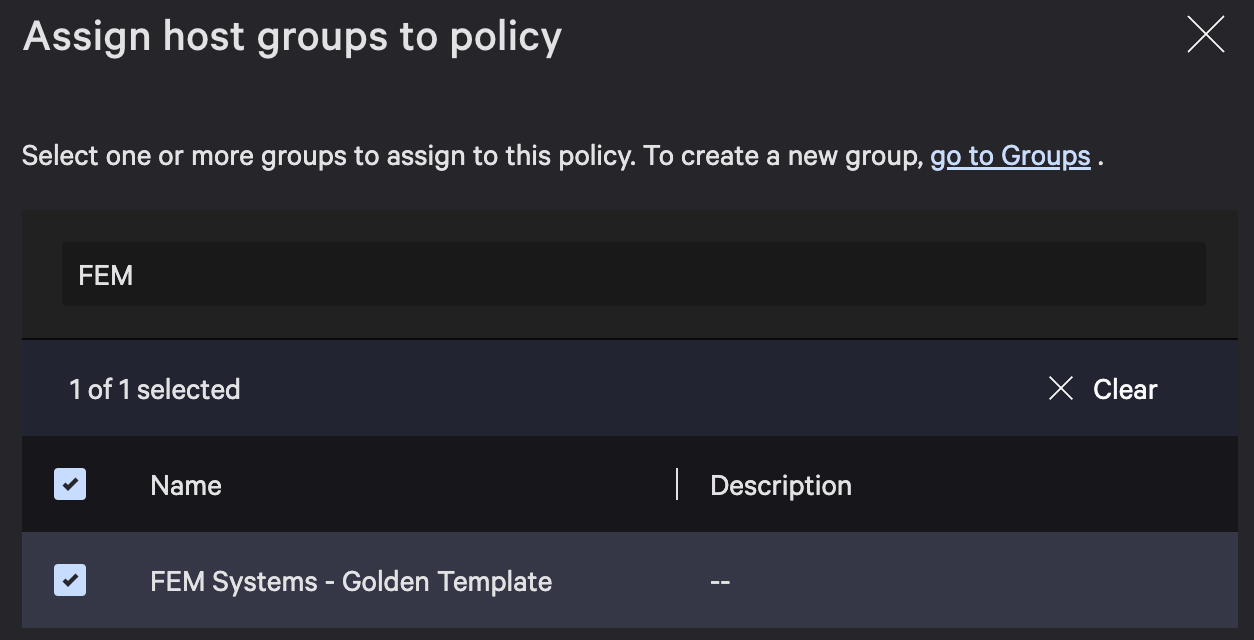
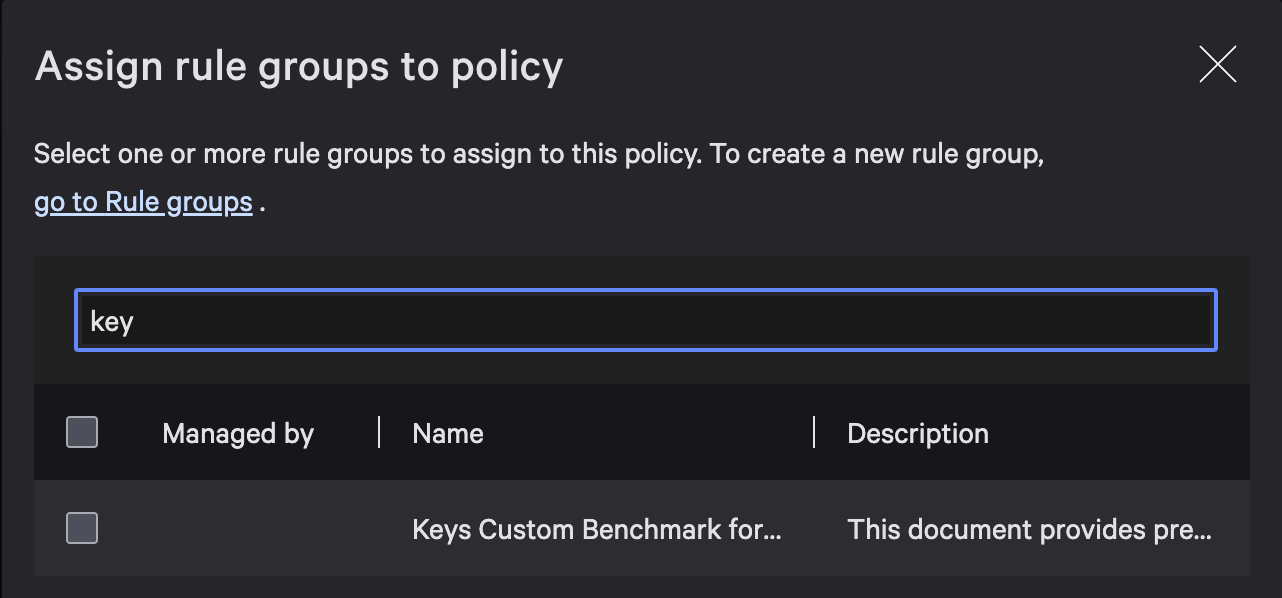
Next, select “Assign rule group”, locate your customized benchmark, and click “Assign rule group”.
For your final step, enable your new policy. Click Enable policy.
Conclude
With Falcon Exposure Management’s Configuration Assessment Rules, organizations are empowered to proactively detect misconfigurations, bolstering cybersecurity and ensuring compliance. The process involves navigating the Falcon dashboard to create and modify rules aligned with CIS standards, customizing policies, assigning host groups, and activating the policies. This vigilant approach effectively shields systems against cyber threats while adhering to regulatory standards, thereby enhancing organizational security posture.