Identity Protection – Addressing Password Risk

Summary
In this resource you will learn how CrowdStrike Falcon Identity Protection detects and protects against password-based risk.
The Problem
Attackers frequently target identity. CrowdStrike’s Global Threat Report found that 80% of attacks involve compromised credentials. Instead of kicking down a door, with valid credentials they can simply use the key. With valid credentials, attackers can skip stages of the attack lifecycle and reach their end goals even faster.
The Value of Falcon Identity Protection
CrowdStrike Falcon® Identity Protection gives you real-time visibility into compromised password and password risk. In this article you’ll see how to view, and ultimately mitigate these risks to stop threats.
Finding Identity Risk
Using the main menu, navigate to the Identity Protection -> Domain Security Overview. The Domain Security Overview shows overall risk for the selected domain.
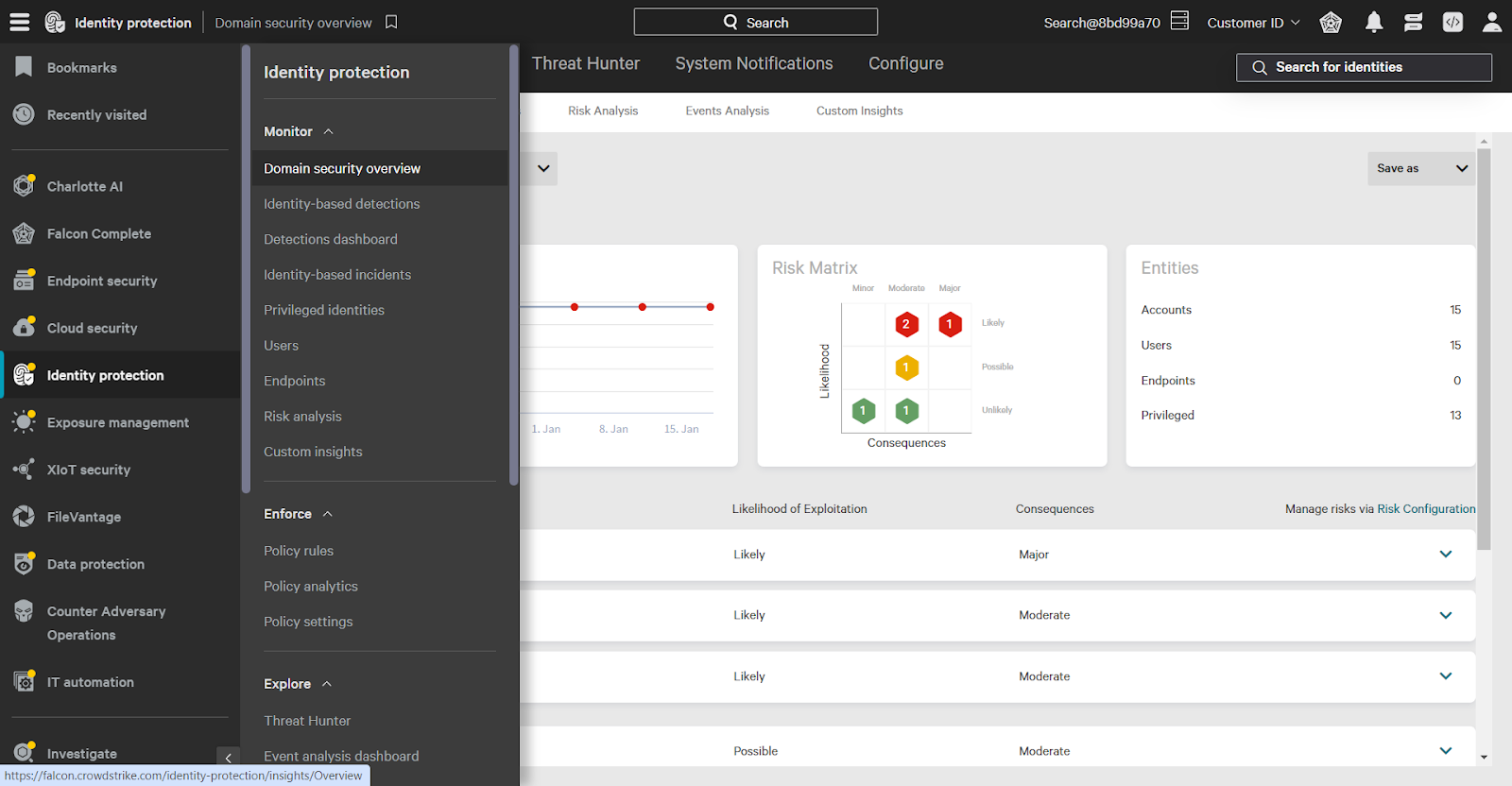
If any password-based risks are present you can find them on this page. A few of the password risks Falcon Identity Protection detects are:
- Duplicate Passwords
- Compromised Passwords
- Inadequate password policy
…and more.
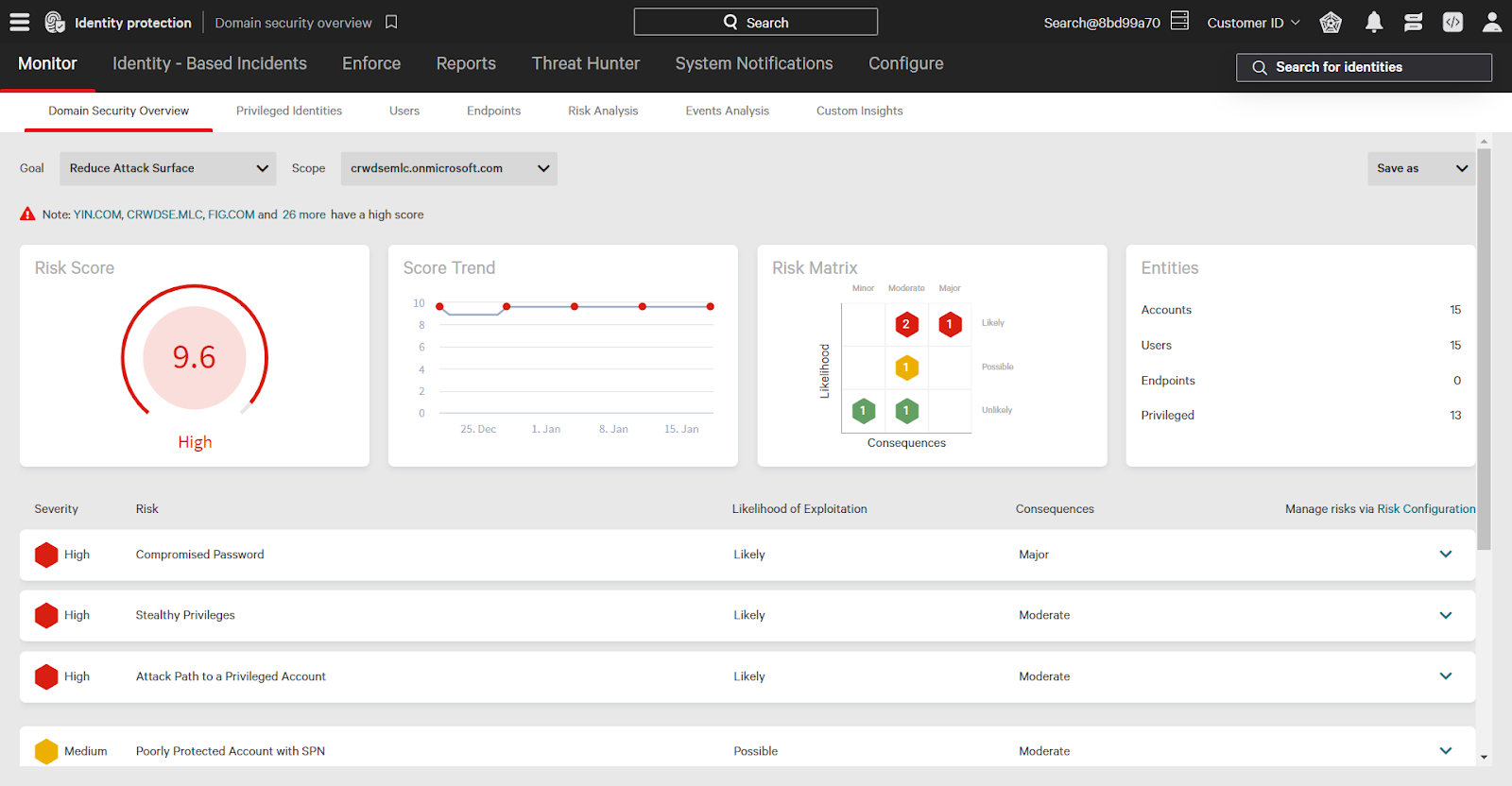
Let’s dive further into the duplicate password risk. Clicking a risk displays additional information on what that risk is, its consequences, and how to resolve it.
Duplicate passwords are passwords reused between two (or more) accounts. If one of these shared passwords is compromised, this reuse allows adversaries to easily move laterally.
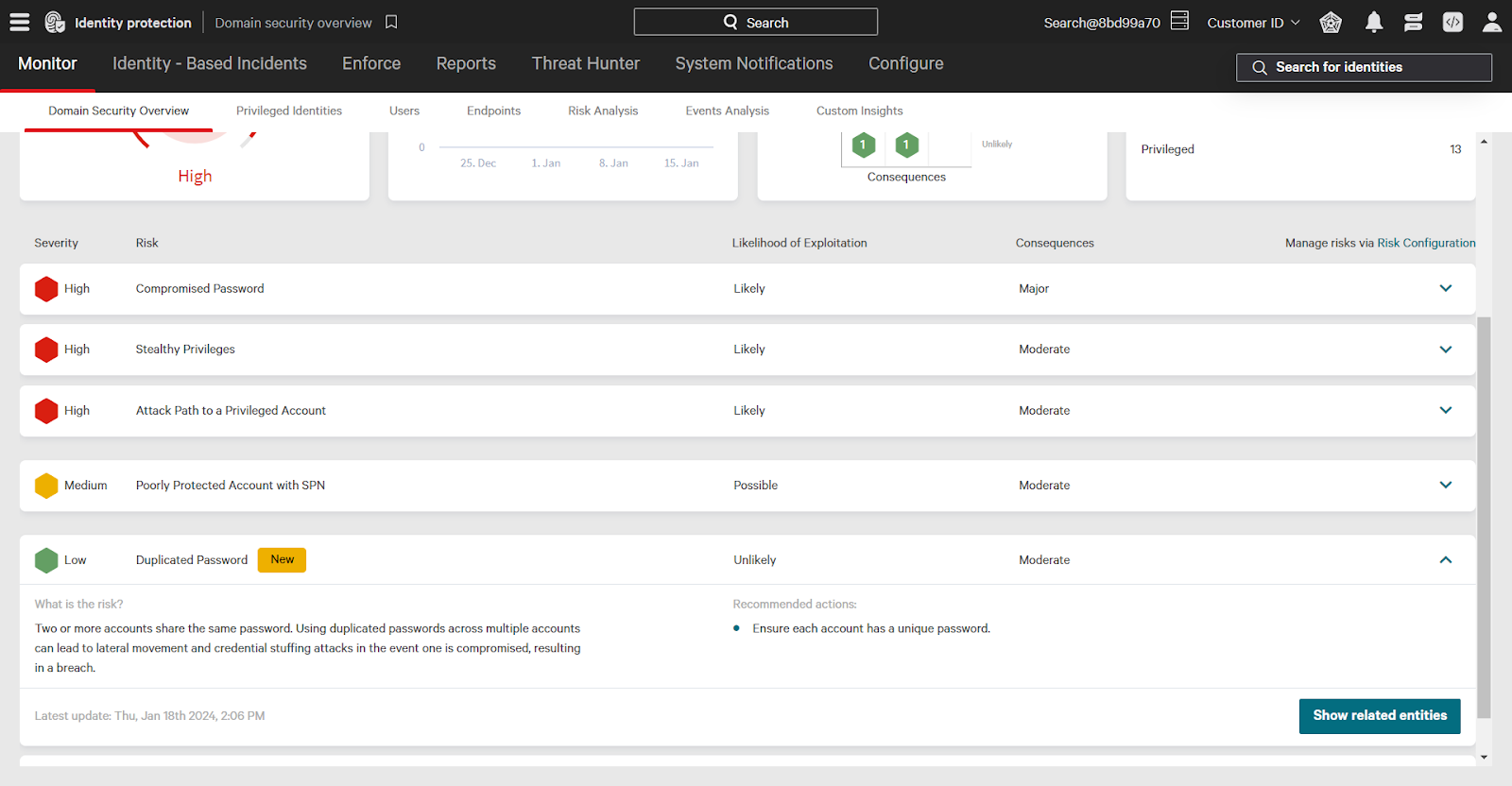
Use the Show Related Entities button to see which accounts have this risk. By selecting an individual account, and viewing that account’s risk, you can see what accounts are using the same password.
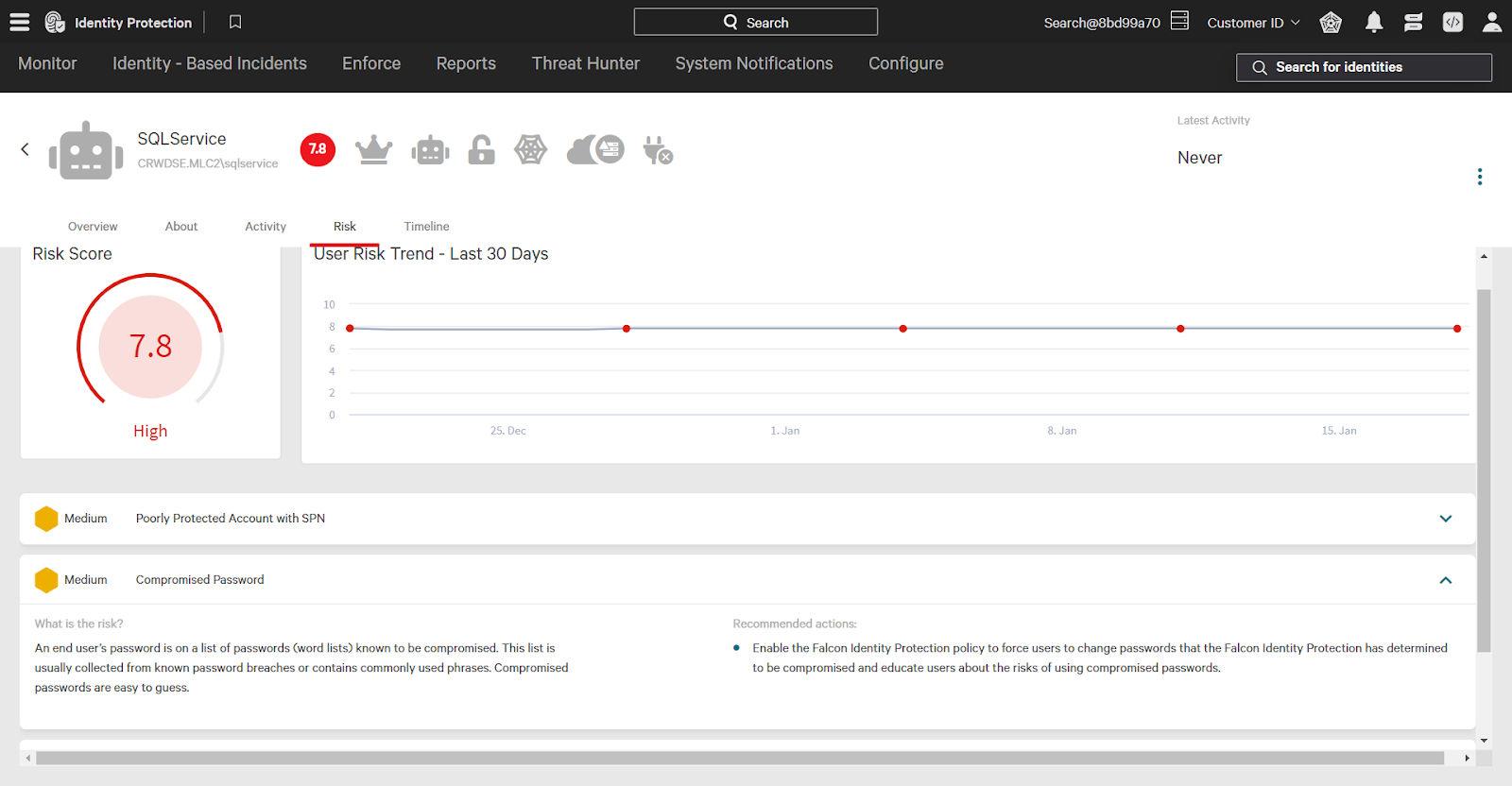
In this example, the SQLService account shares a password with two other users: Joca Brasil and AppUser.
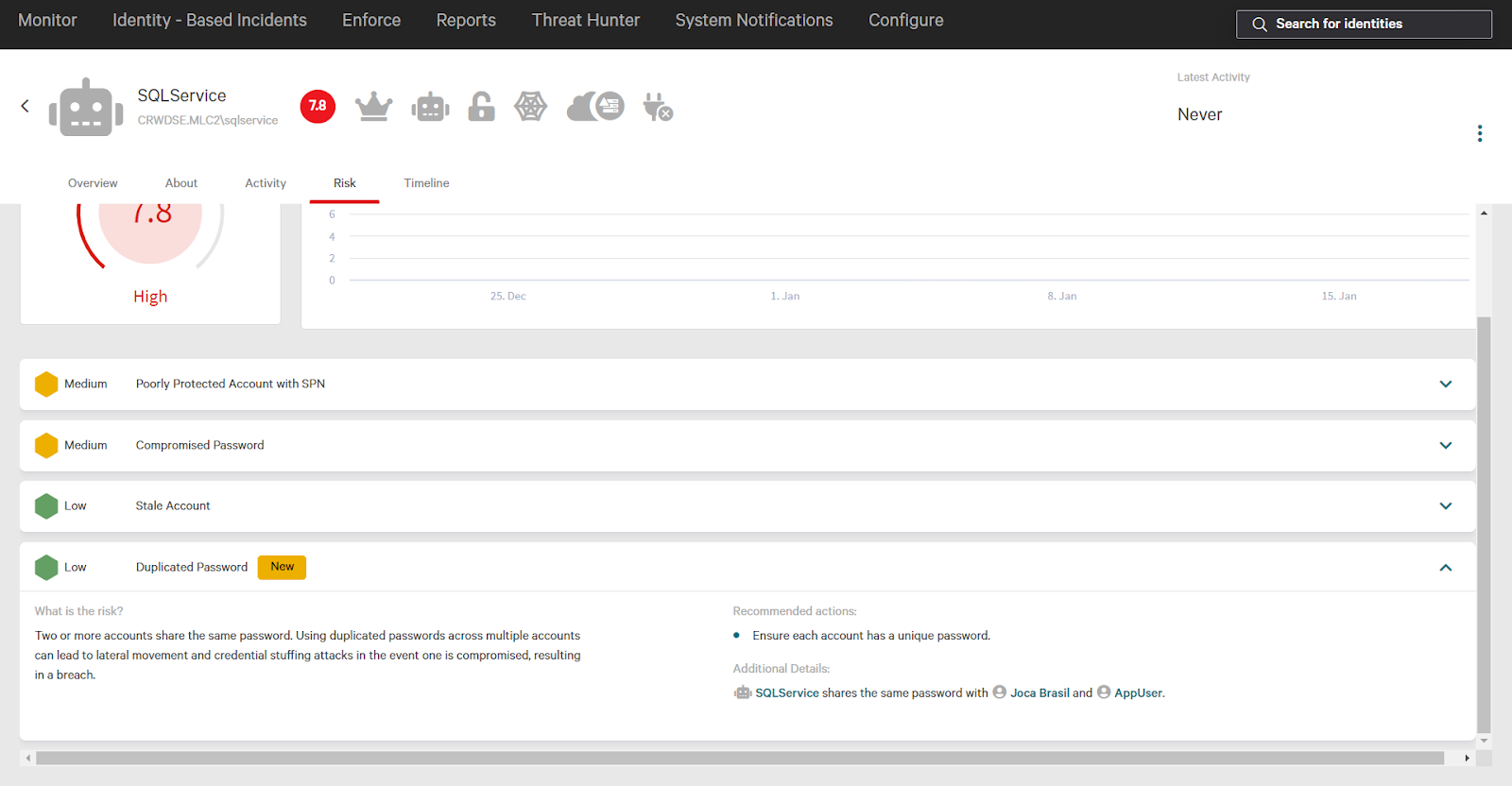
This account has another password risk: a compromised password. Selecting that risk expands additional information.
CrowdStrike detects compromised passwords with an integration to the HaveIBeenPwned dictionary. This contains compromised, or breached data including passwords. In the next section you’ll see how Falcon Identity Protection can automatically reset compromised passwords.
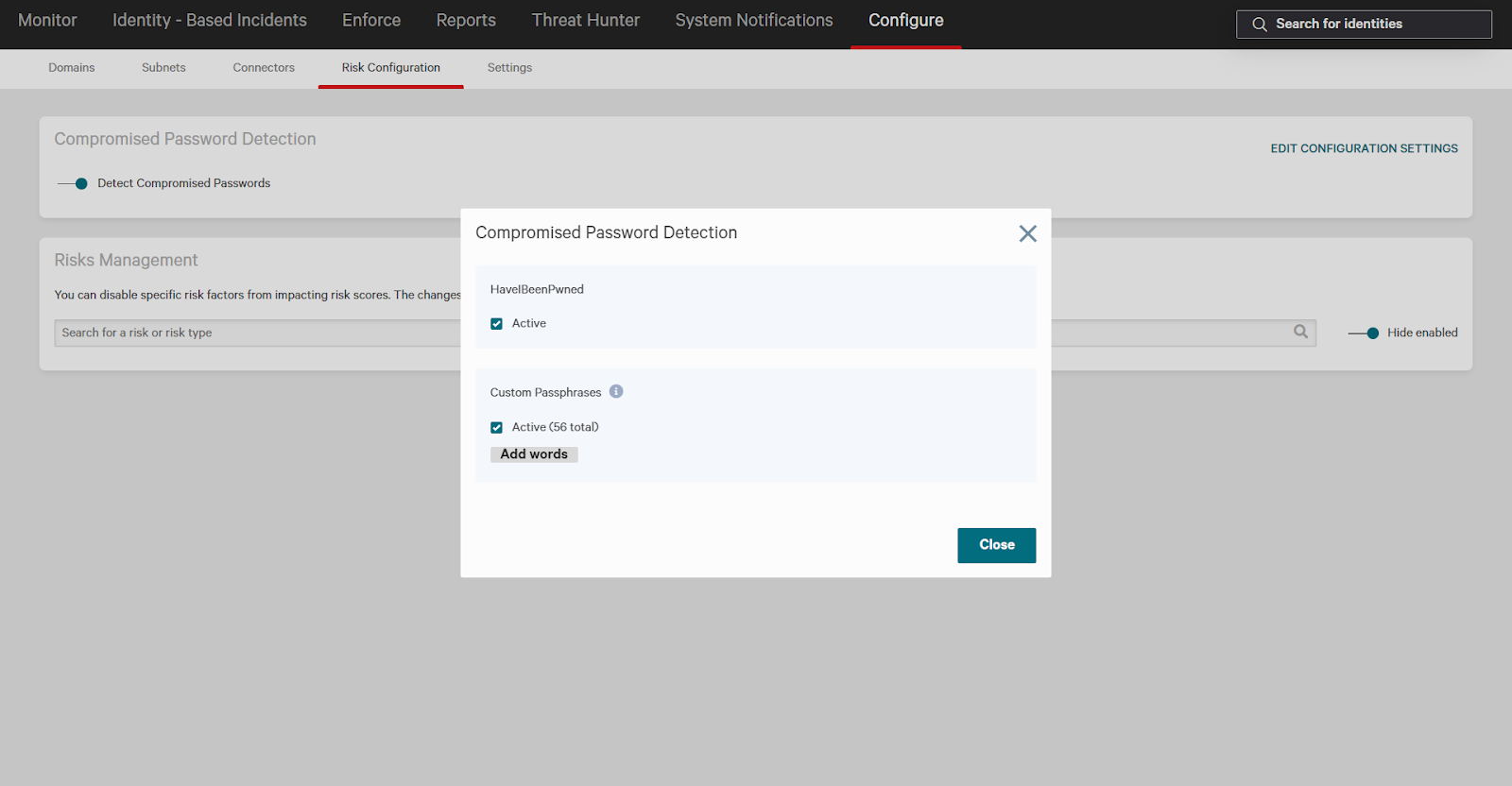
In Identity Protection, under the Configure -> Risk Configuration tab, you can add custom passwords and phrases to the compromised password dictionary.
Click edit configuration systems for compromised password detection. You can add additional phrases by uploading a text file with each phrase on a single line. Some examples of custom passphrases to include are: company name, local sports teams, and so forth.
Click edit configuration systems for compromised password detection. You can add additional phrases by uploading a text file with each phrase on a single line. Some examples of custom passphrases to include are: company name, local sports teams, and so forth.
Responding to Identity Risk
Use identity policies to stop adversaries from taking advantage of compromised accounts. The out-of-the-box policy template Compromised Password Detected, for example, requires users to reset their password on next login.
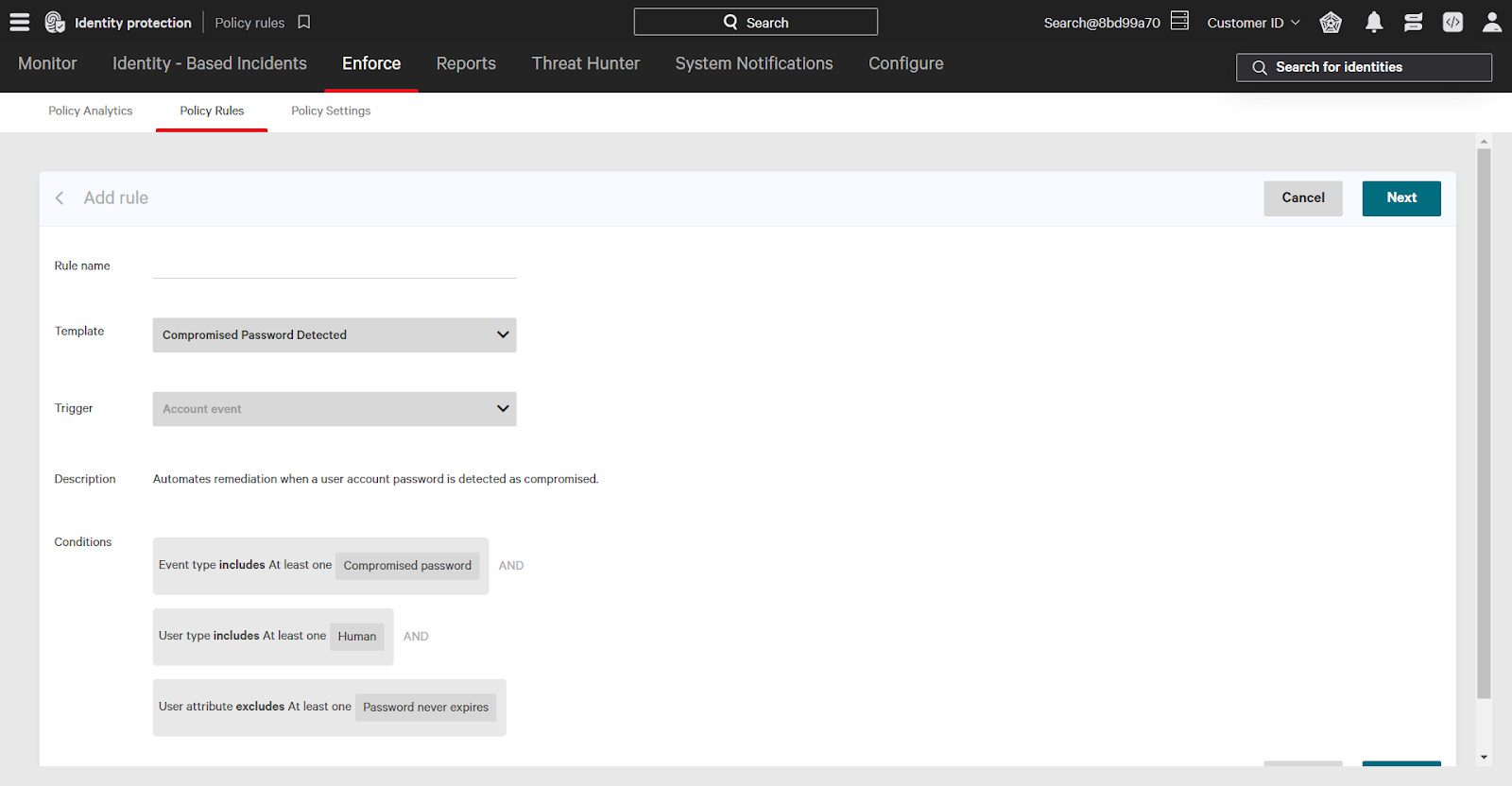
Compromised password is an attribute that you can use to create various custom identity policies that stop threats. One example of this is blocking access to critical resources for accounts with compromised passwords. Use Identity Protection policies to create highly customizable rules that best suit your environment.
Conclusion
These are just a few of the ways Falcon Identity Protection secures your identity environment against threats. Stop the malicious use of valid credentials with CrowdStrike Falcon Identity Protection.