Identity Protection – Use Falcon Fusion to Connect EPP and IDP

Summary
In this resource you will learn how CrowdStrike Falcon Identity Protection detects and protects against password-based risk.
The Problem
Modern threats rarely target identity or endpoint alone. You need comprehensive coverage of adversary tradecraft – and a platform that is truly unified in protection and response.
The Value of the Falcon Platform
CrowdStrike’s Falcon Platform offers the only unified platform for identity protection and endpoint security.
Events that occur on the endpoint should inform identity protection – and vice versa. You can use Falcon Fusion automation to accomplish this.
Creating a Fusion Workflow
Start by going to the Falcon Fusion page. Using the main menu, click Fusion Workflows -> All Workflows.
Falcon Fusion is a security orchestration, automation, and response capability that is purpose built for the Falcon Platform. Using Fusion, you can build automated workflows with no-code logic. Fusion can be used for automation across, and beyond, the Falcon Platform.
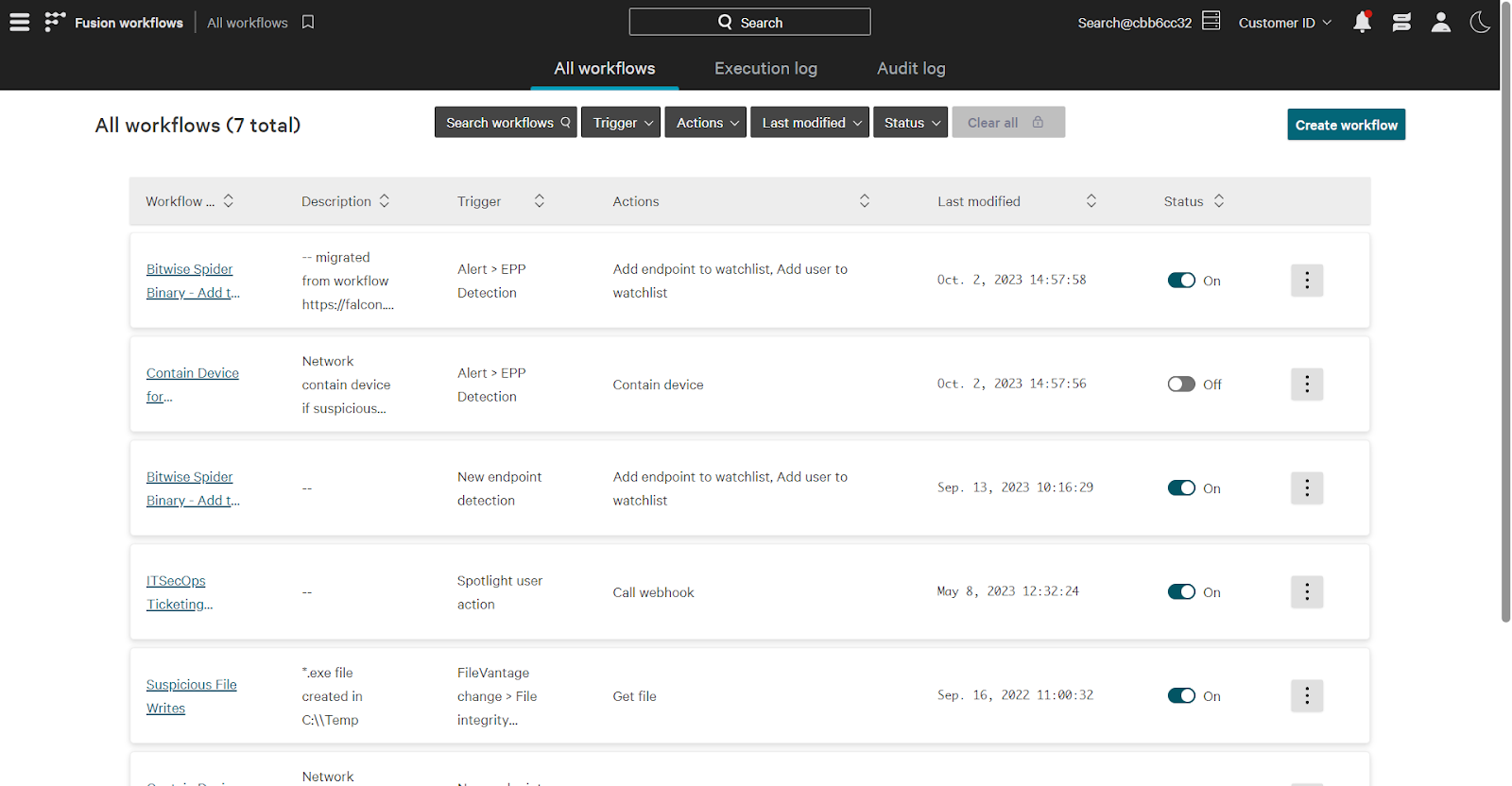
Let’s build out a workflow connecting endpoint and identity protection. Consider the following scenario:
A user receives a phishing email and opens up the attachment. Unknown to them, in the background, that email launches a script that invokes mimikatz, used to steal credentials. The involved endpoint (WIN-WS01-DT), and user (bbanner), are the target of credential access tradecraft. This makes the involved entities more risky from an identity perspective.
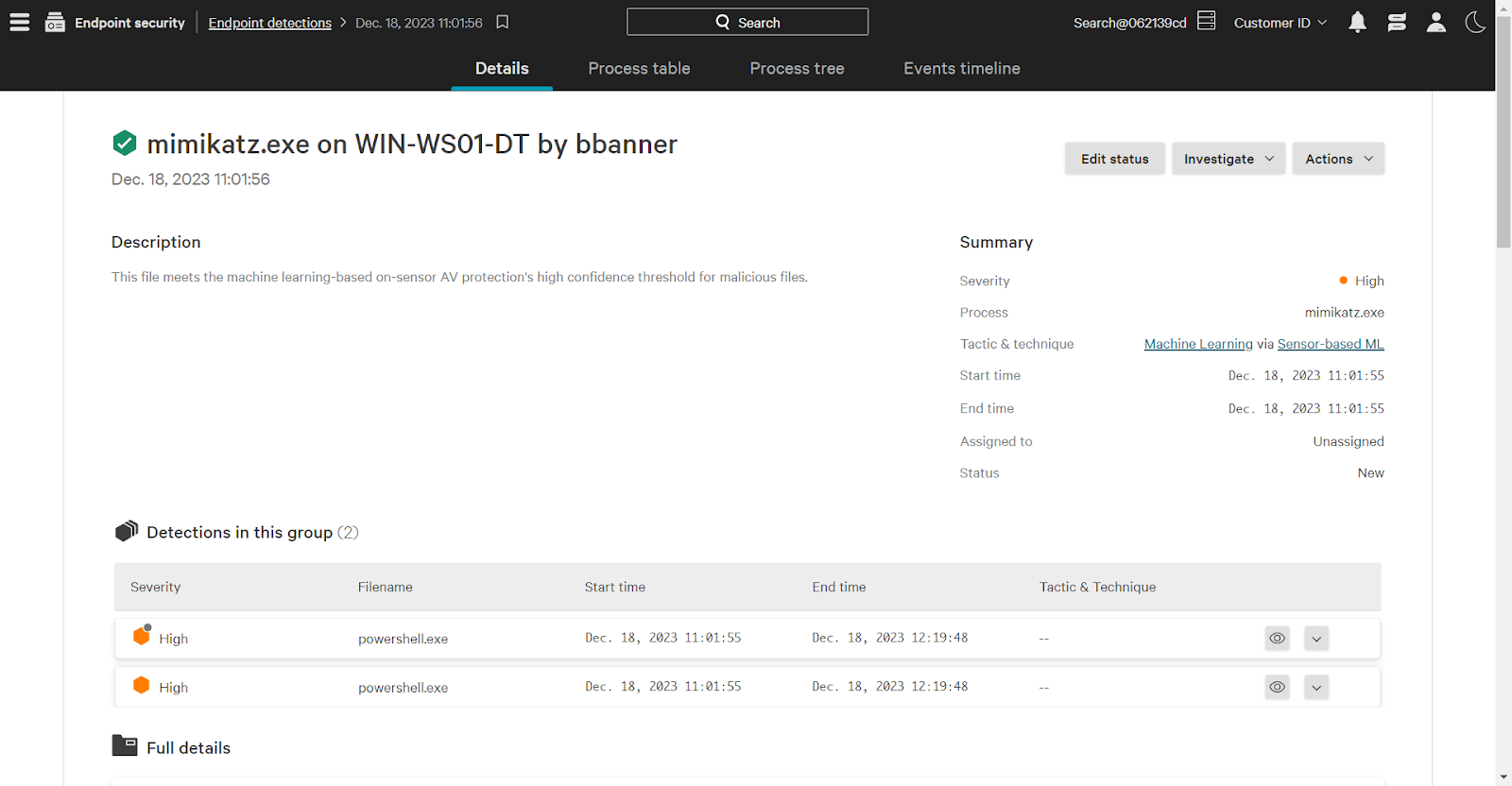
Falcon uses the “watched” identity attribute to indicate that risk. Using Falcon Fusion we will automatically assign the watched attribute. On the Fusion page, click Create Workflow to begin building.
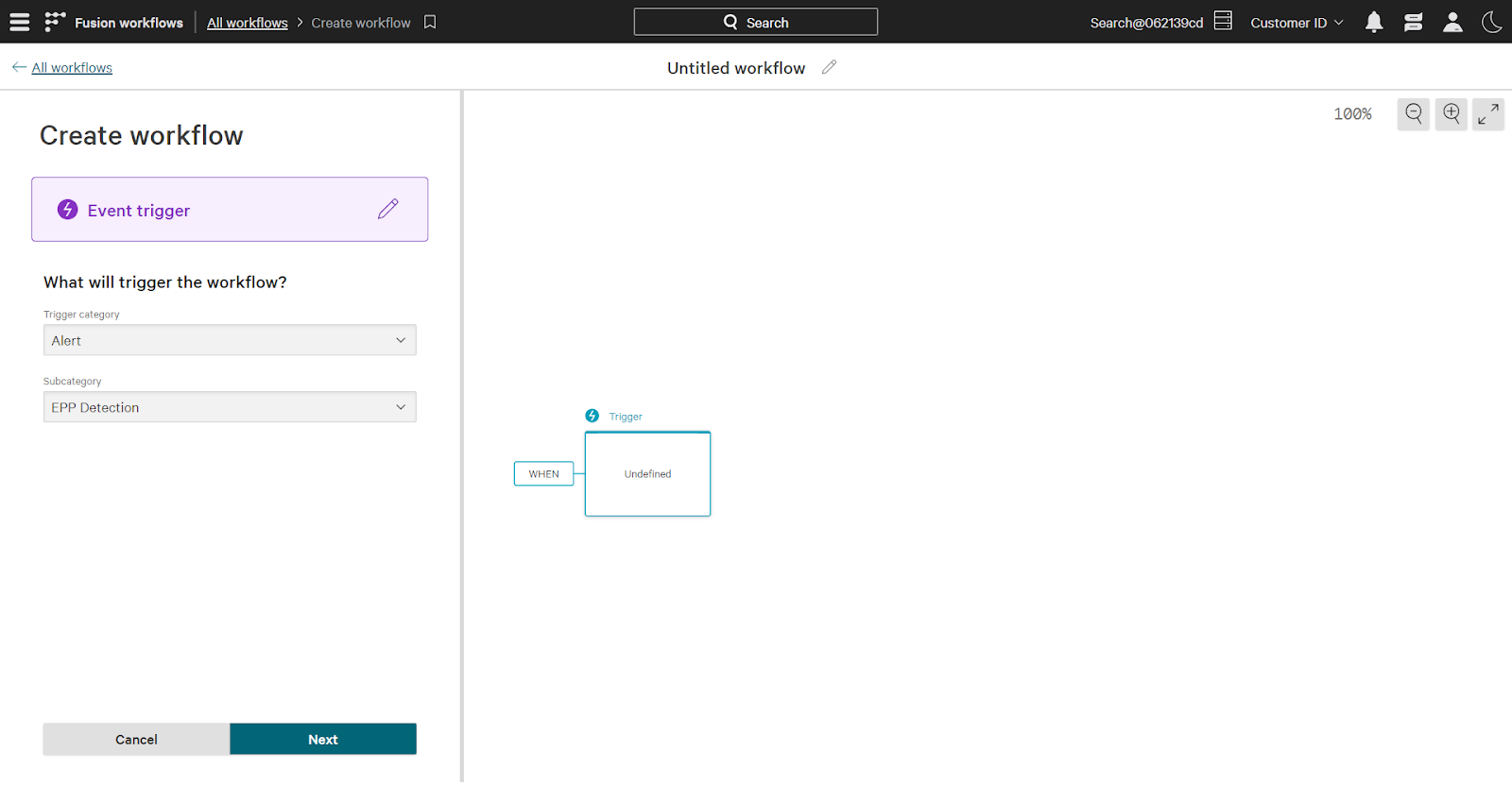
To begin, select a trigger that determines when the workflow runs. In this case, the trigger is a new endpoint alert, which falls under the “event” category.
Next, select conditions that must be met for the workflow to execute. This workflow should execute only when the new detection has “credential access” as a tactic.
Keep in mind that this is just one example. Add additional conditions to address specific automation use cases. For example, the technique condition could be added to limit the workflow to specific techniques such as “credential dumping” under the broader credential access bucket.
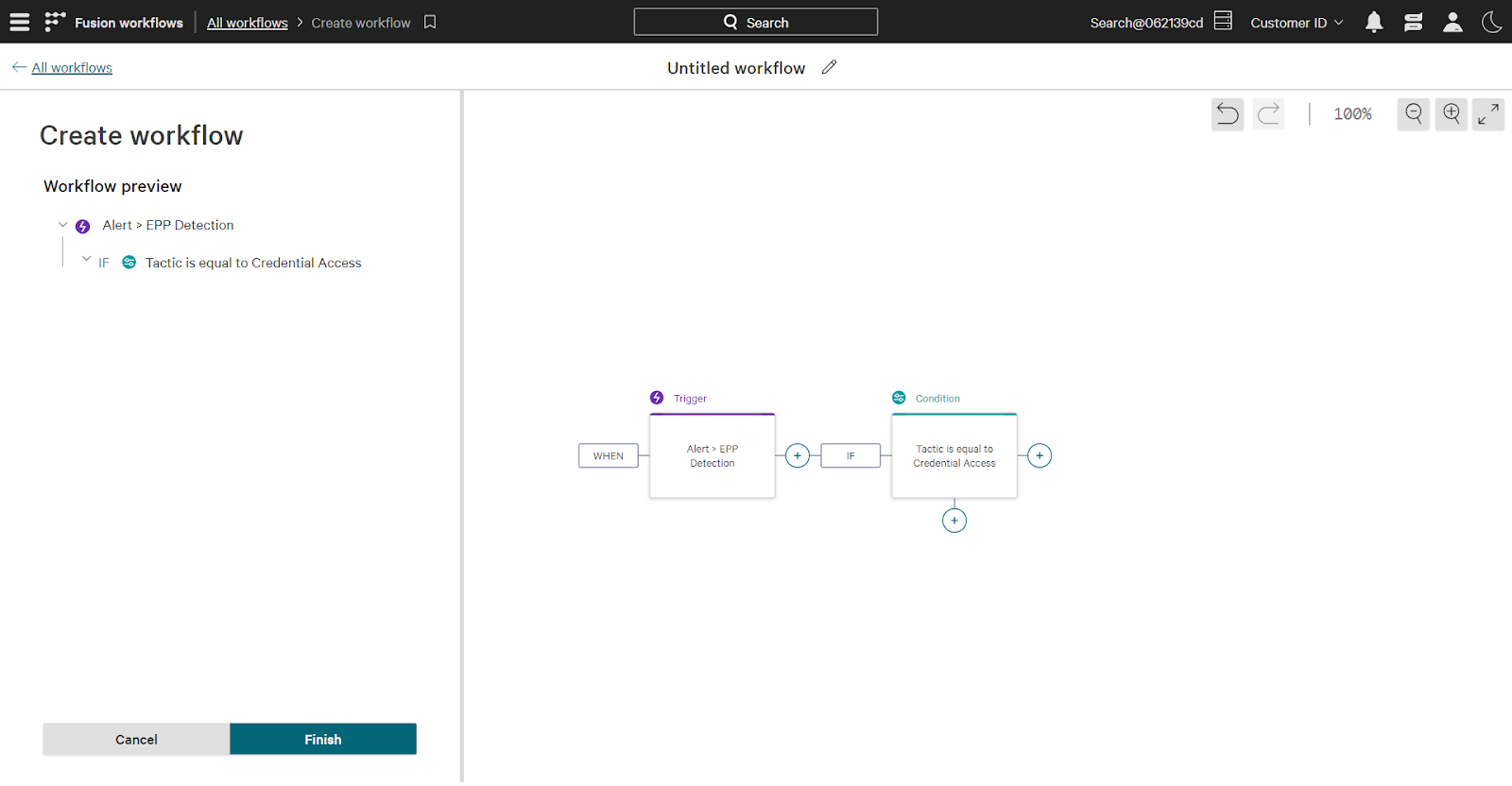
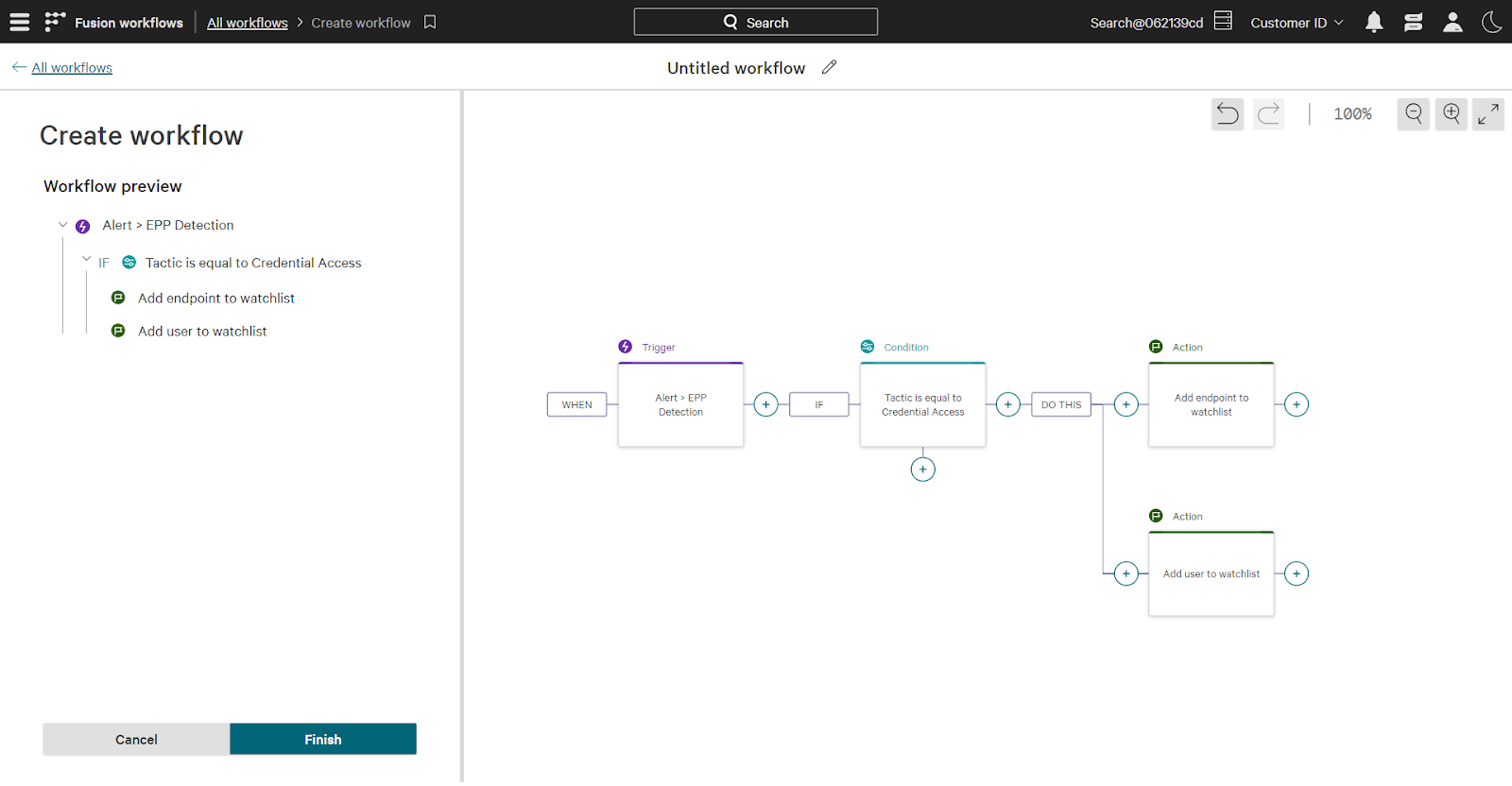
Finally, add actions to take once the workflow is triggered and conditions are met. For this workflow both the user and endpoint involved in this detection will be added to the identity watchlist.
To summarize the workflow: when a new endpoint detection occurs that includes the credential access tactic, both the involved user and endpoint are added to the watchlist.
Executing the Workflow
Now, running the same attack on the end user’s computer will trigger the workflow. Off screen, I’ve run mimikatz on the same endpoint.
The endpoint WIN-WS01-DT, and user bbanner both have the watched identity attribute, denoted by the binoculars icon.
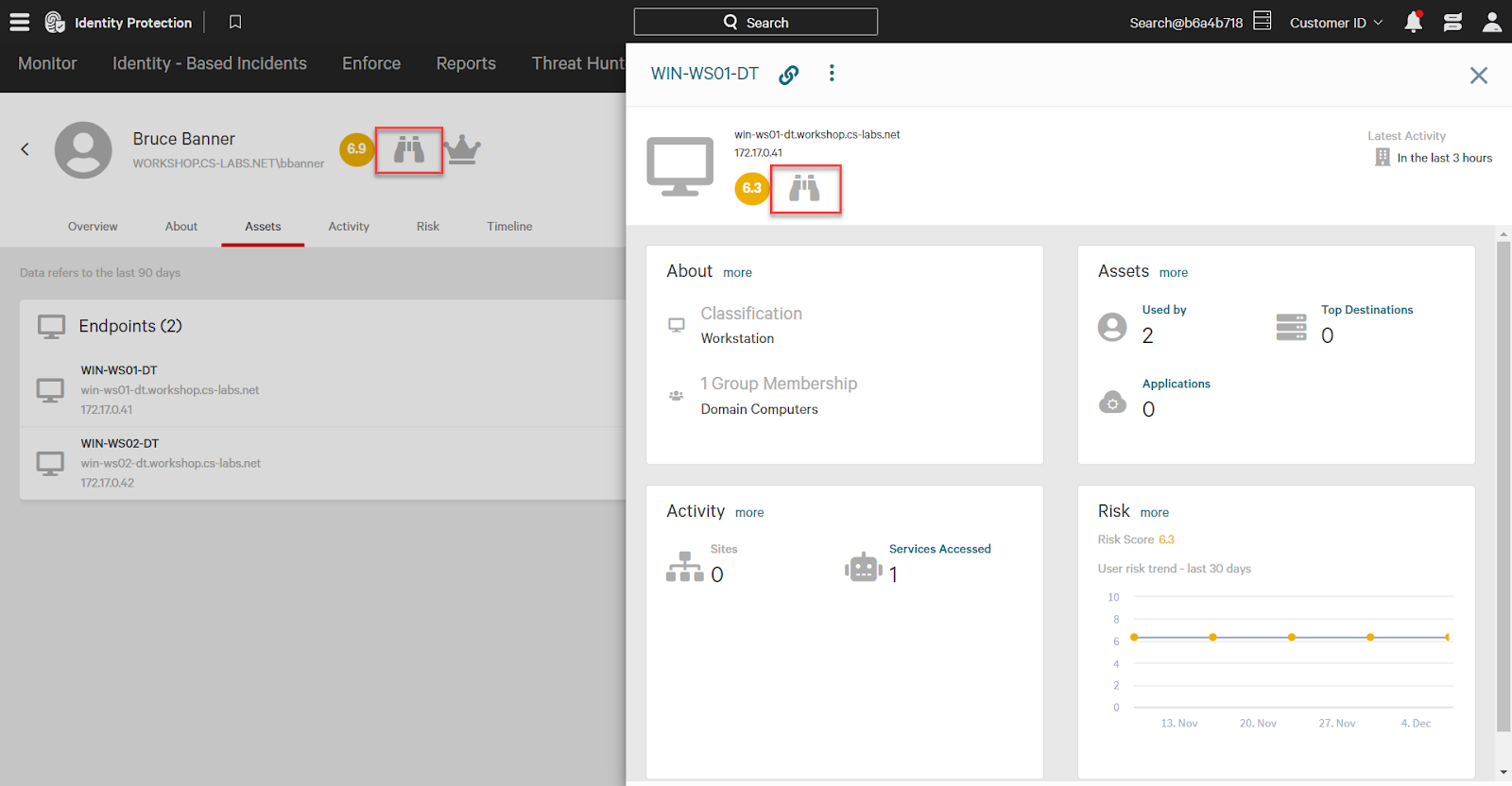
Using the Watched Attribute
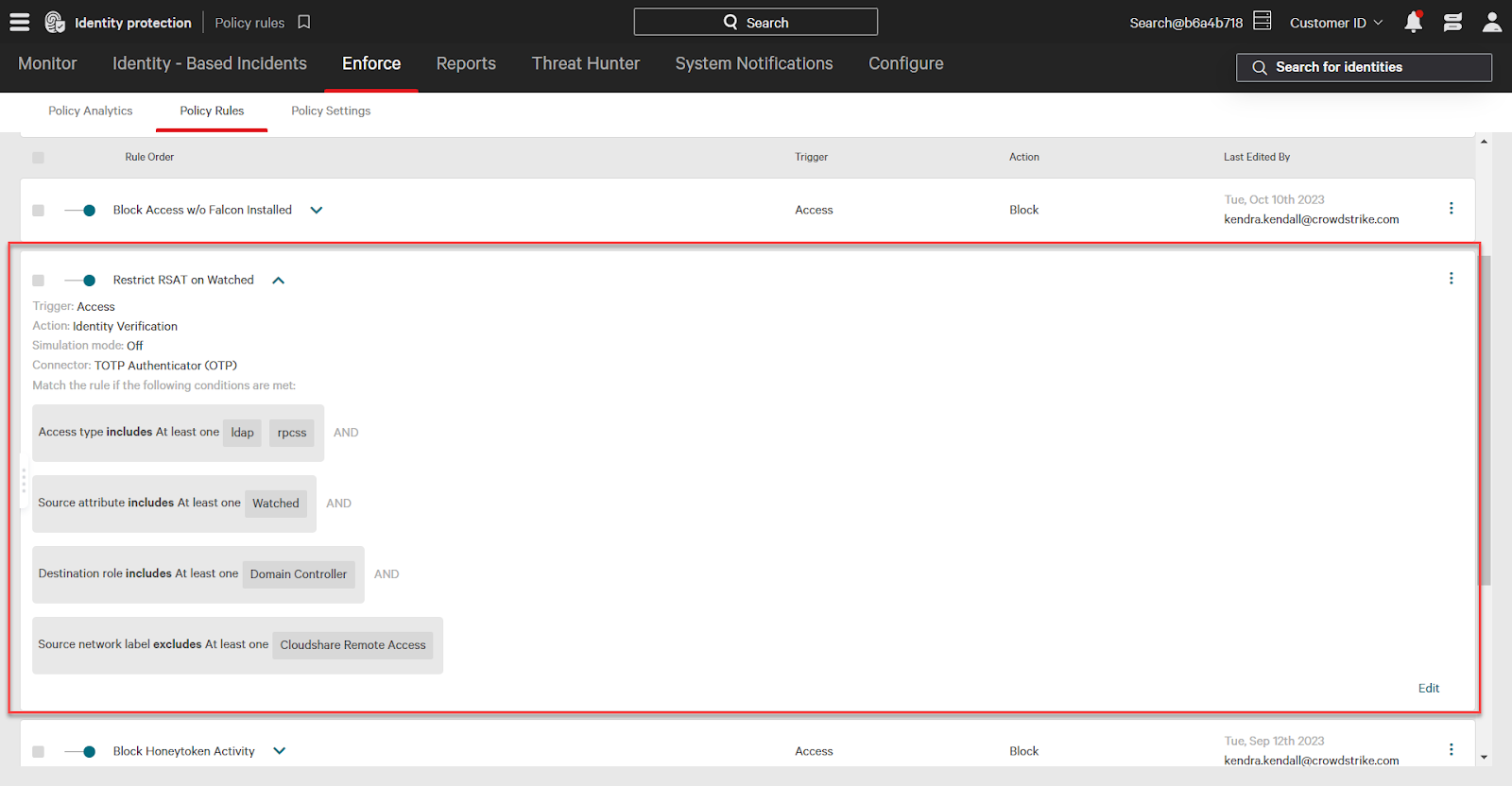
The watched attribute can be used in identity protection policies to lock down access to critical resources and more.
For example, this policy requires identity verification on the use of RSAT, or “remote server administration tool”, on domain controllers from watched assets.
Conclusion
The CrowdStrike Falcon Platform uniquely combines endpoint and identity protection for comprehensive visibility and protection against modern threats.
Use Falcon Fusion to automate actions across the Falcon Platform – including connecting endpoint and identity as seen in this demonstration.