Identity Protection – Getting Started with Policies

Summary
In this resource you will learn how to create CrowdStrike Falcon Identity Protection policy rules that stop threats. This resource is intended as an introduction to policies in Falcon Identity Protection.
The Problem
Attackers increasingly target identity. CrowdStrike’s Global Threat Report found that 80% of attacks involve compromised credentials. Instead of kicking down a door, with valid credentials they can simply use the key. With valid credentials, attackers can skip stages of the attack lifecycle and reach their end goals even faster.
Adversaries obtain valid credentials in a variety of ways: social engineering, purchasing credentials on dark web marketplaces, and more.
The Value of Falcon Identity Protection
Regardless of how threat actors obtain credentials, you need the capabilities to stop the malicious use of valid credentials.
CrowdStrike Falcon Identity Protection stops modern identity attacks in real time with automation, by using a rich policy engine. Policies are highly customizable so you stop threats without stopping your business.
Enforce Resources
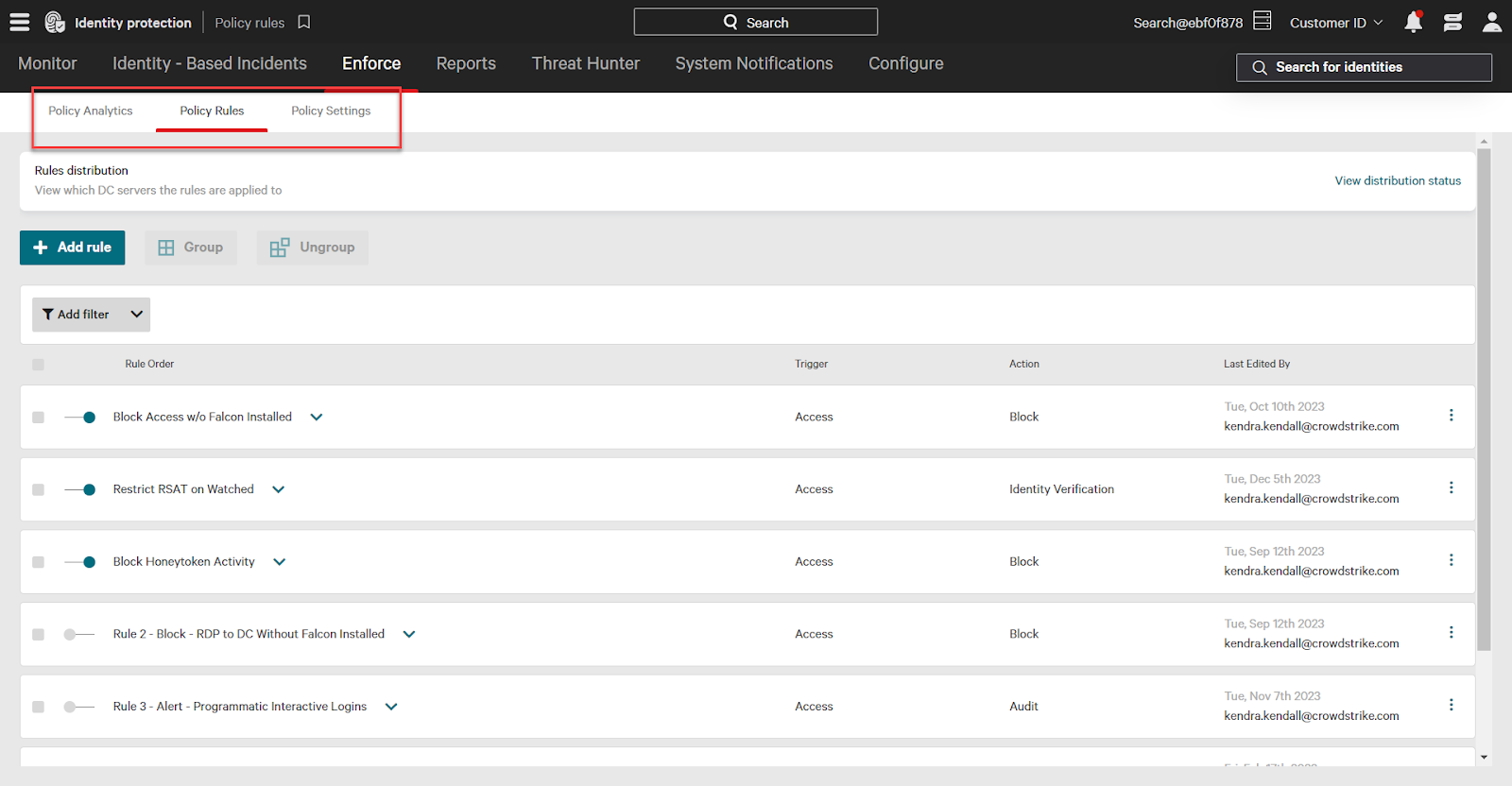
Policies are managed under the Enforce tab in identity protection. You can also use the main menu to navigate to any of the pages under the enforce category.
Under the Enforce category are three pages:
- Policy Analytics: this page gives visibility into executions of your rules. When they happened, on what devices, and their status.
- Policy Rules: use this page to create, edit, and manage your rules.
- Policy Settings: this page is used to manage global policy settings such as action on MFA timeout, DC server distribution status, and more.
Creating Policy Rules
Navigate to the Policy Rules tab. Using the main menu, click Identity Protection -> Policy Rules.
Let’s build out an identity protection rule as an example. Keep in mind that rules are highly customizable, so you can create rules that best fit your environment’s needs.
Adversaries often use unmanaged devices in an attempt to circumvent prevention. With Falcon Identity Protection, this activity can still be stopped. We’ll create a rule to block remote desktop access to domain controllers when the source does not have Falcon installed.
On the Policy Rules page, click add rule to begin. Enter a name for your rule. In this case the rule name will be “Block RDP to DC from Unmanaged”. It’s useful to summarize what the rule does in the name to easily understand its purpose when the rule executes.
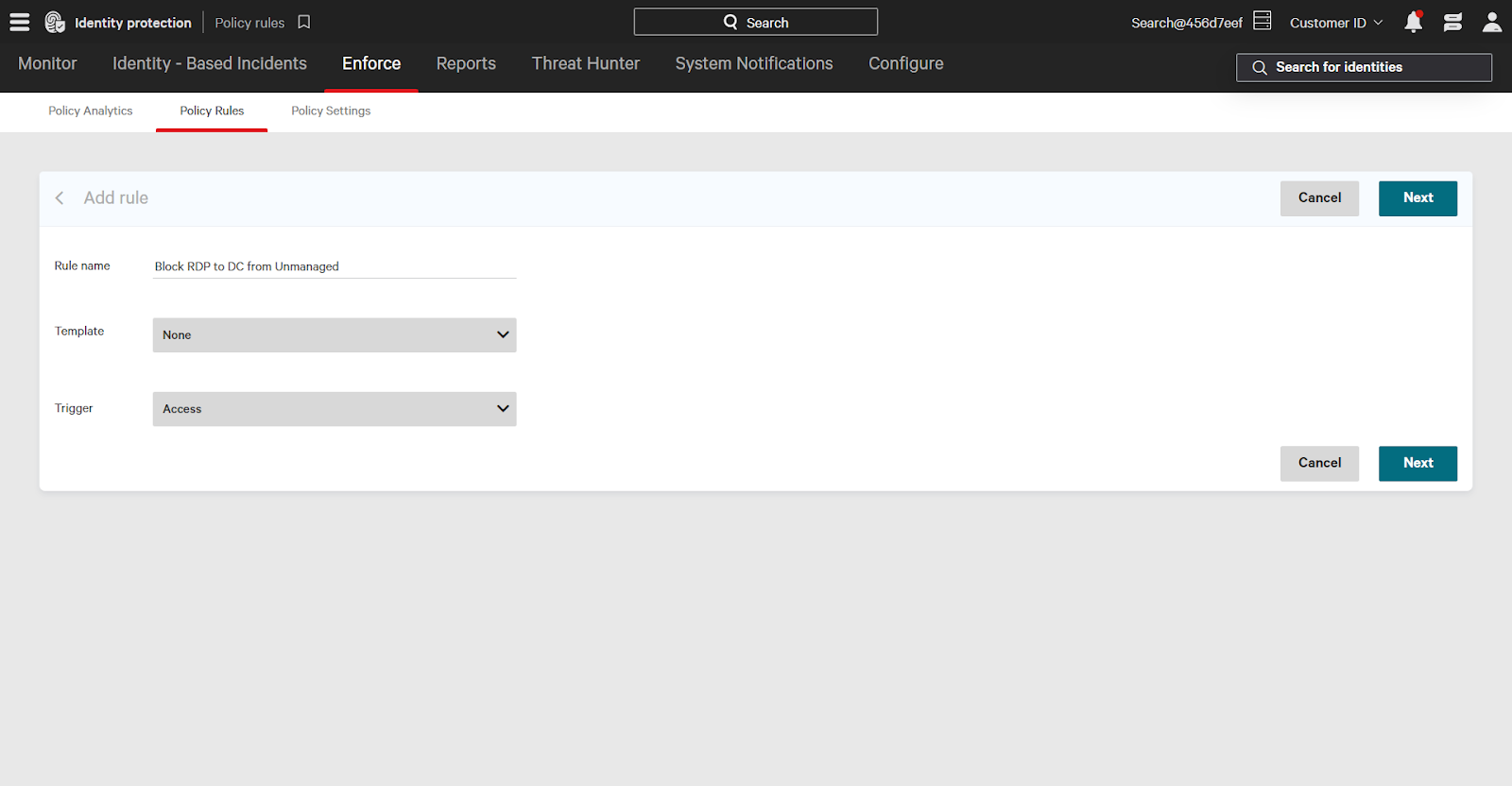
The Template dropdown are prebuilt rules around common use cases, such as anomalous authentication. Use the template rules to immediately start protecting against identity threats in your environment.
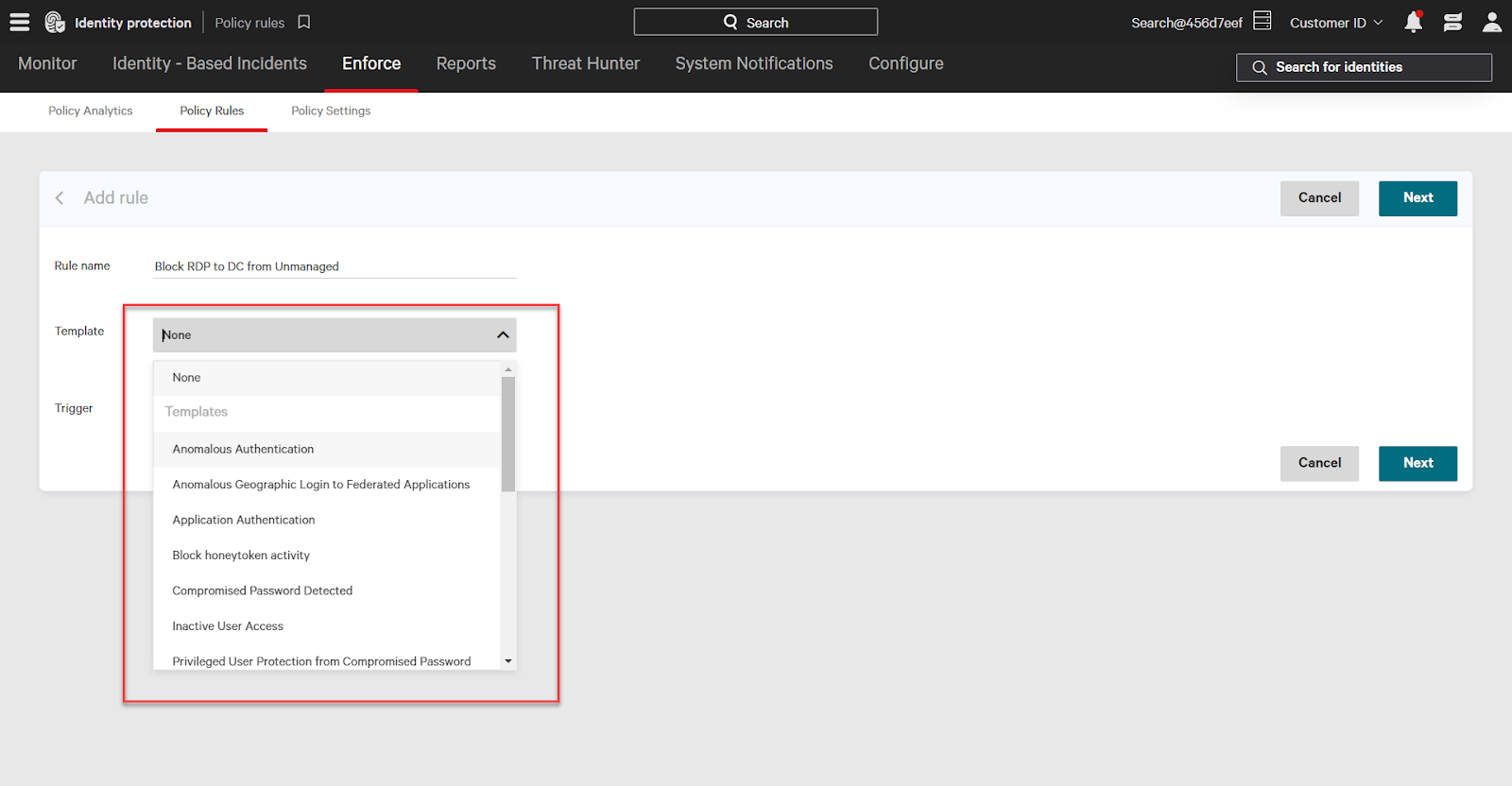
Next, select a trigger for the rule. The trigger determines when the rule will run. For our example rule the trigger will be access. Other triggers include:
- An account event, such as a compromised password
- An identity detection occurring
- An authentication to a federated service like Office 365
After selecting a trigger click next to continue rule creation.
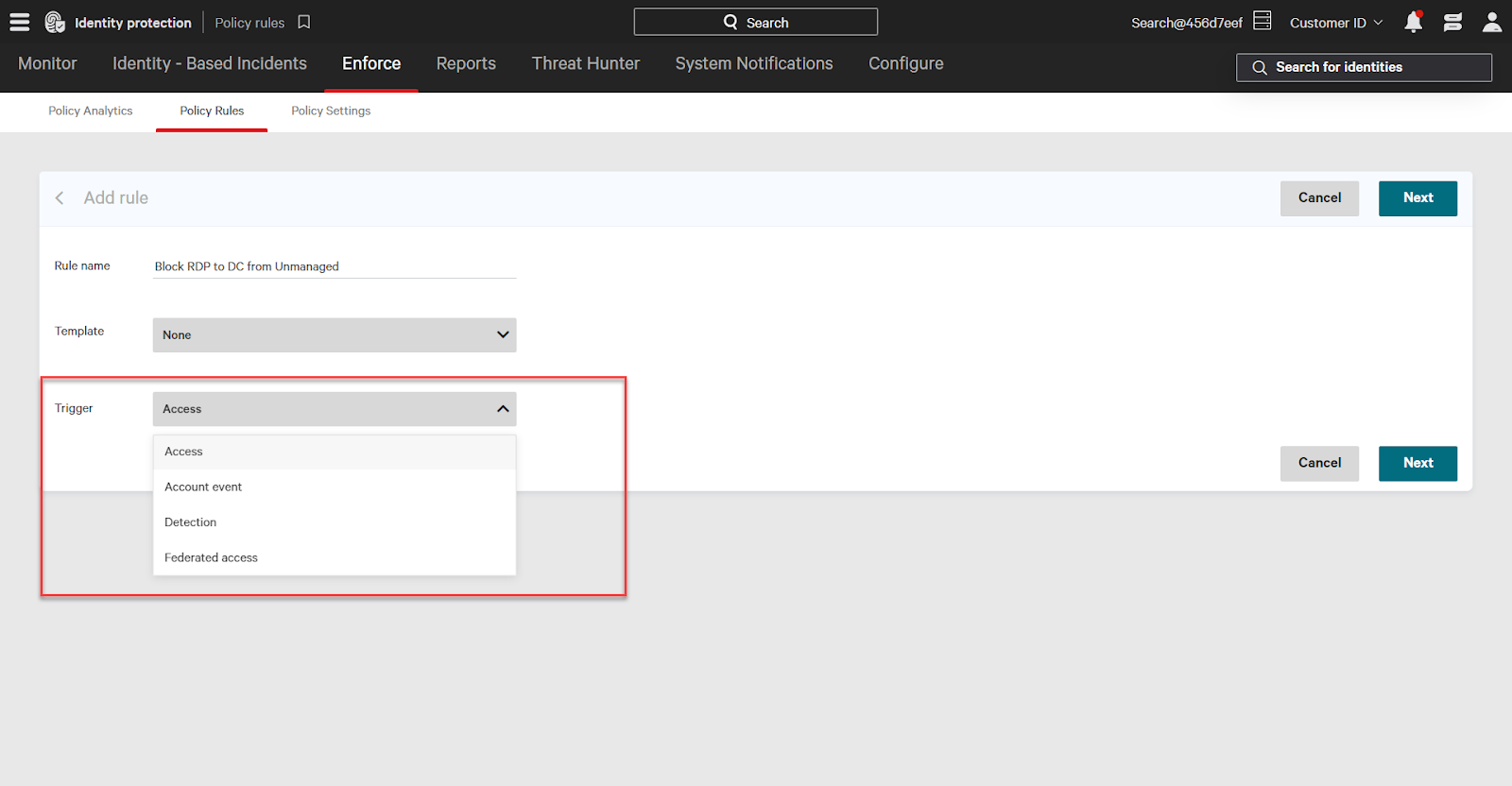
Next, add conditions. The conditions must be met for the policy rule to run. To add more rule conditions, click the Add Rule Condition button. To remove a condition, click the trash on the right.
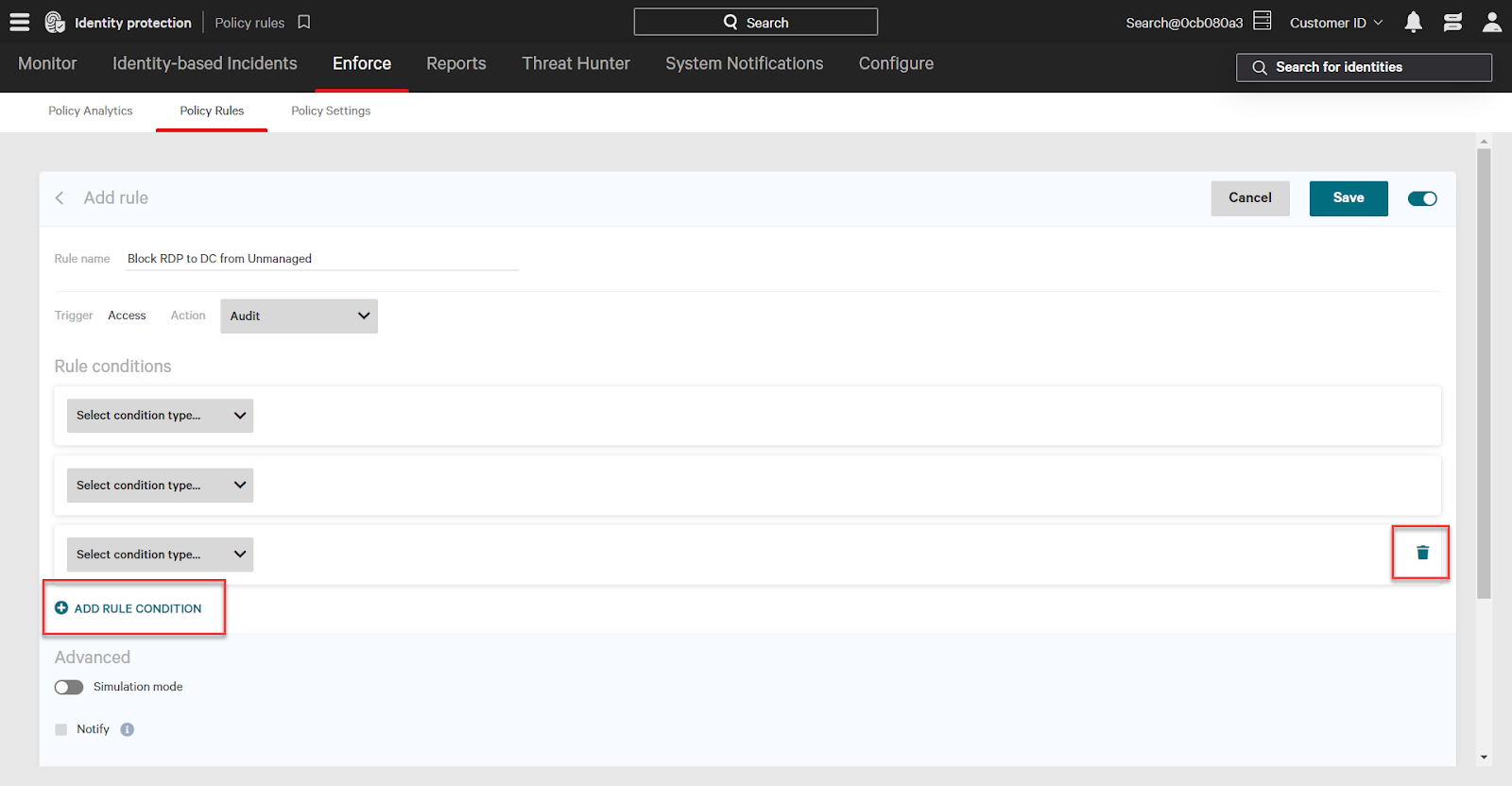
Click the Select condition type dropdown, and select the type of condition to add. Then, in the second dropdown, choose the include or exclude option. Finally, in the last dropdown, select the options for the selected type (ex: access type options include RDP, authentication, web authentication). Some condition types allow you to input your own options as well by typing into the textbox/dropdown.
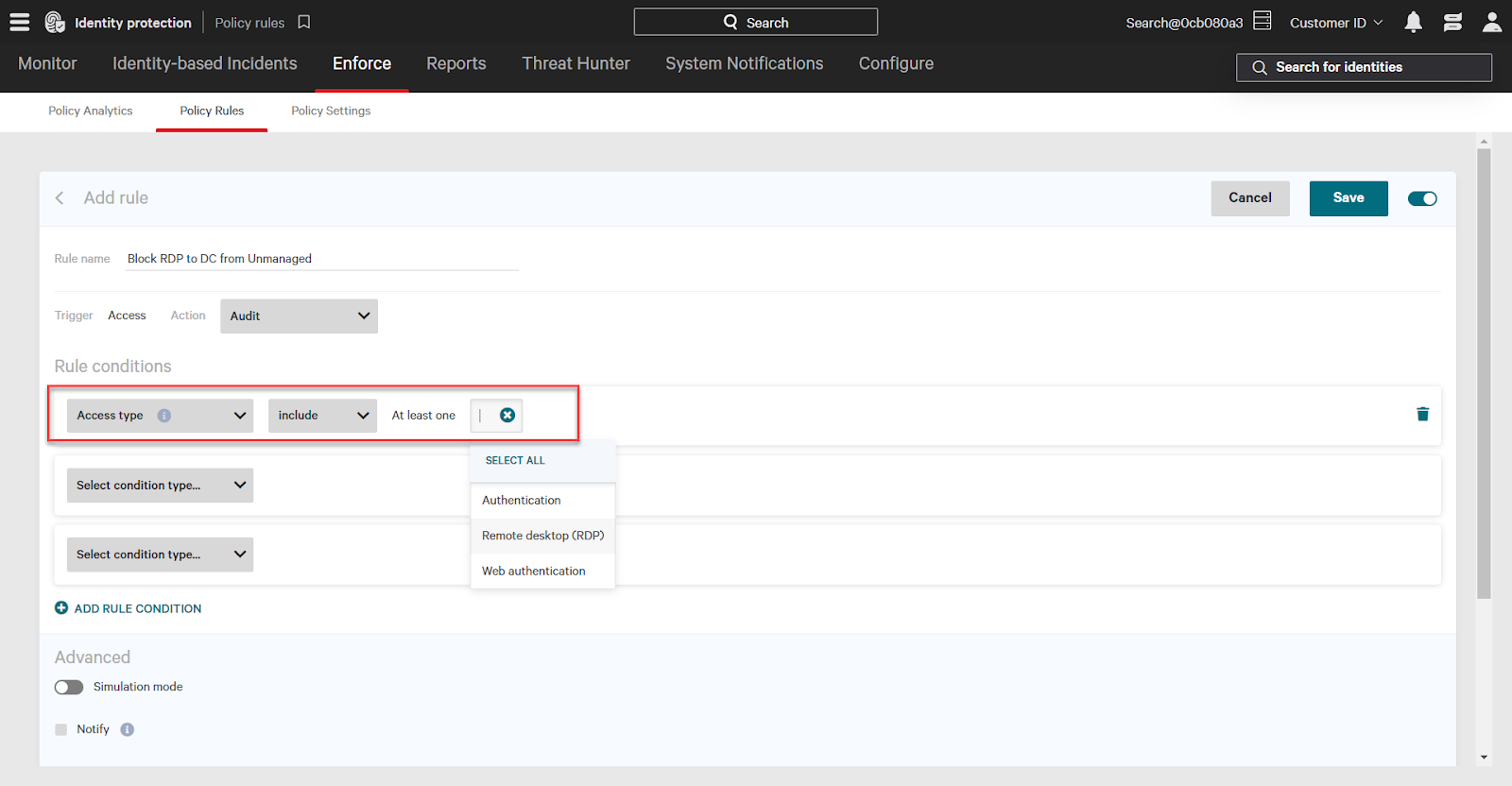
For the example policy rule, we want to:
- Block a specific type of access: RDP
- From a specific source attribute: one that does not have Falcon installed
- To a specific type of destination: domain controllers.
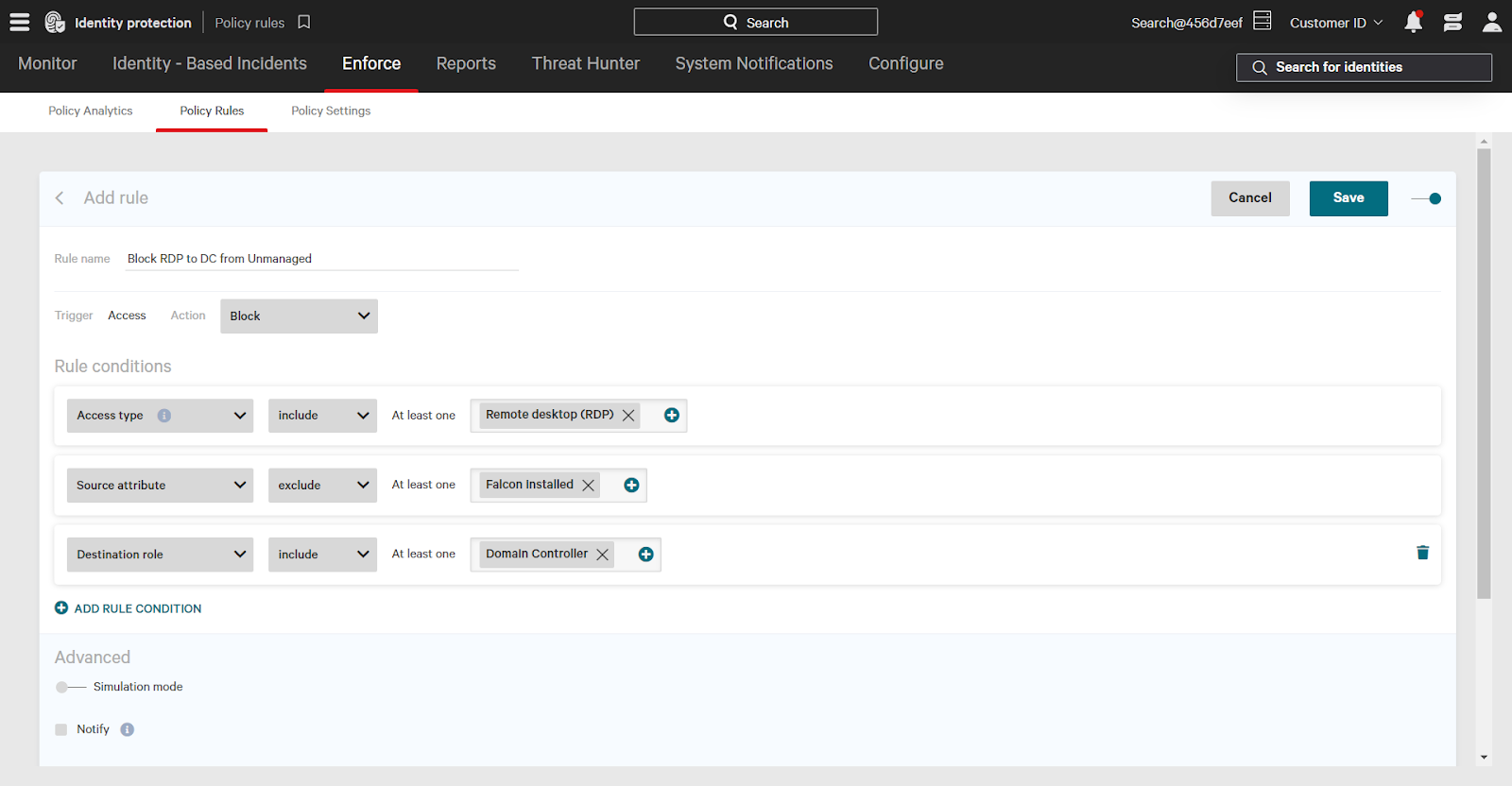
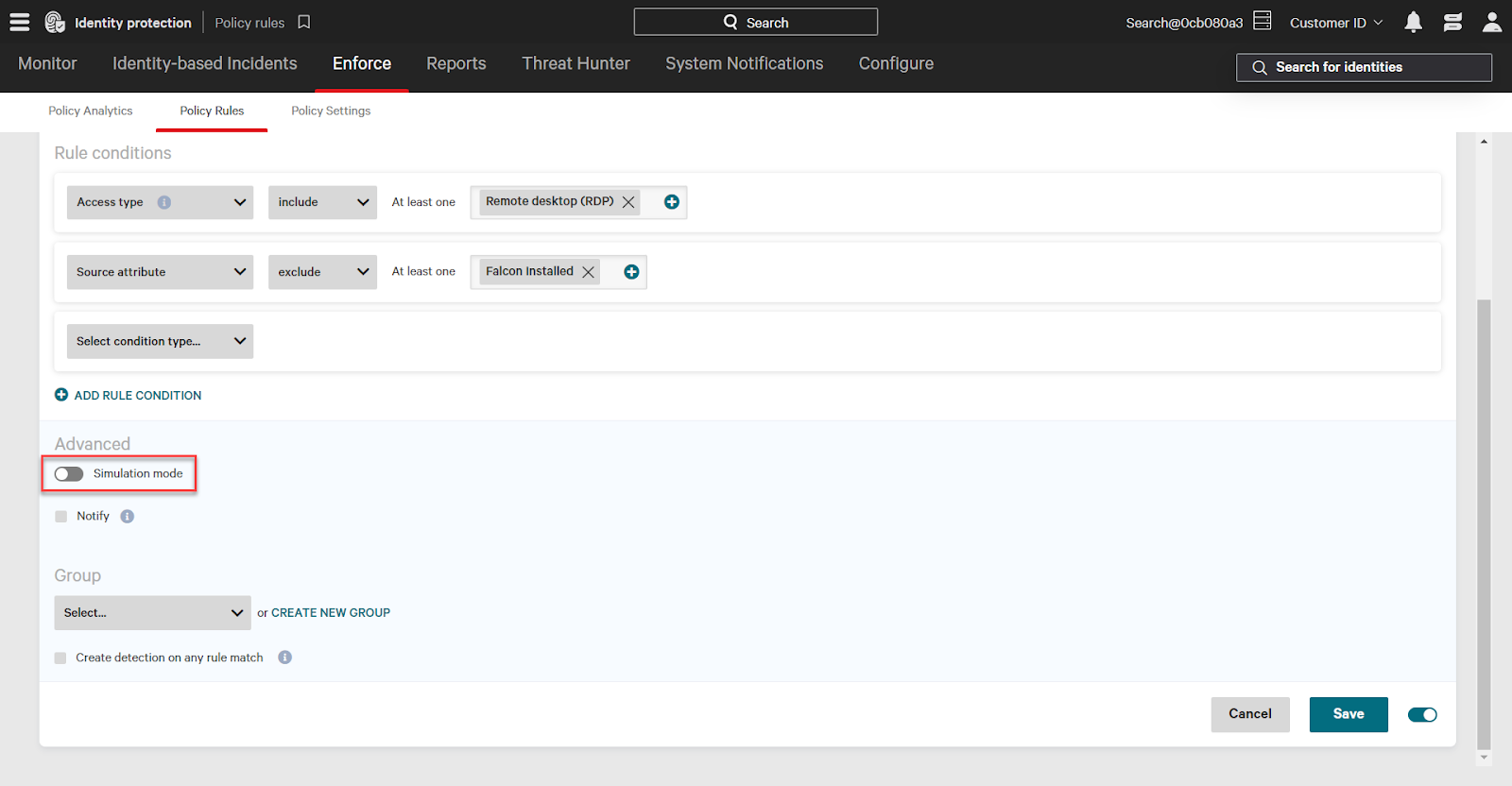
At the bottom of the page are Advanced Settings. Here, you turn on the simulation mode settings. Simulation mode will not trigger enforcement, but will show up in the policy analytics page so you can understand the impact of the rule.
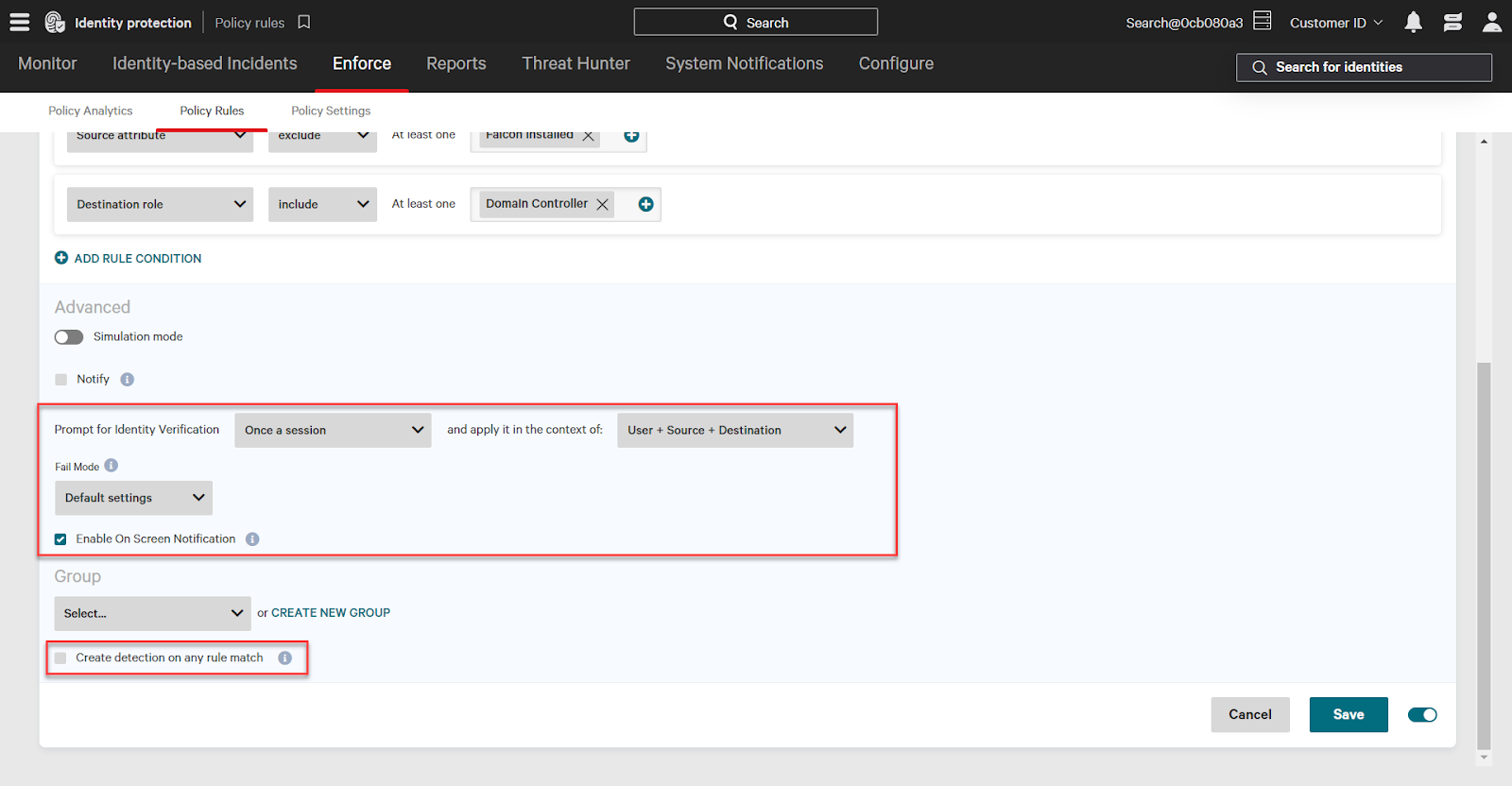
There are also additional settings to create an identity detection when a policy rule executes. And, for identity verification actions, you can choose additional settings for when to prompt MFA (ex: every time, every hour) and more.
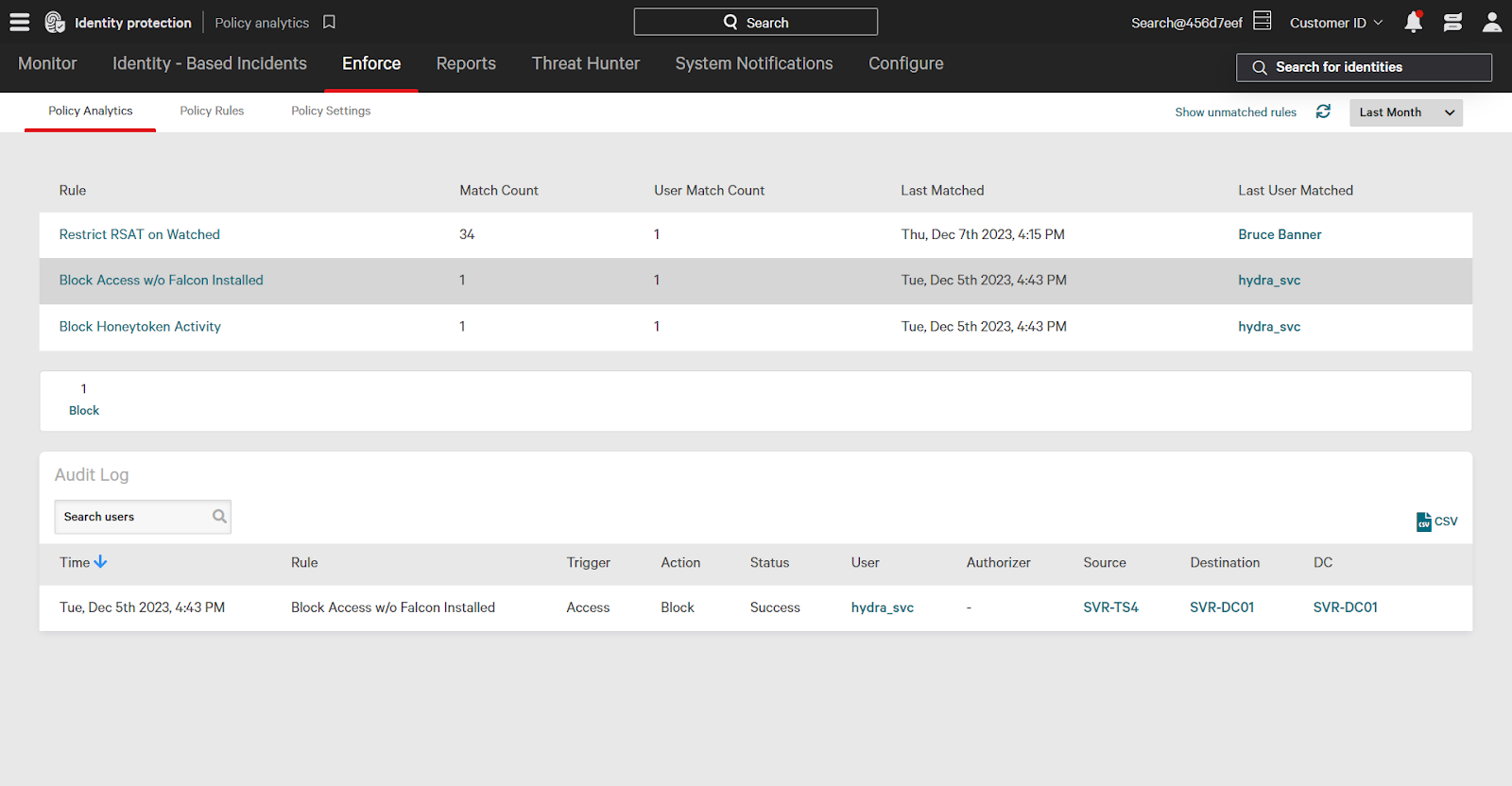
Using Policy Analytics
Use the Policy Analytics page to view rule executions. Click a rule to filter executions. For example, selecting the “Block RDP to DC from Unmanaged” rule will filter results to just that rule.
This confirms that the example rule successfully executed and blocked access to the domain controller.
Conclusion
CrowdStrike Falcon Identity Protection stops attacks in real time with automation, by using a rich policy engine that can enforce conditional access policies and can also block unauthorized access or enforce Multi-factor authentication to ensure real-time protection.