Identity Protection – Identity and Recon Integration

Summary
In this resource you will learn how CrowdStrike Falcon Identity Protection and Intelligence Recon work together to protect against exposed credentials.
The Problem
Access Brokers are threat actors who sell credentials. Since 2022, CrowdStrike has seen a 147% increase in this activity.
How do you know if your credentials are compromised by access brokers?
The Falcon Platform
CrowdStrike Falcon Intelligence Recon exposes cybercrime activities – by monitoring dark web activity and exposed data in real time.
Using the power of a unified platform, Recon automatically notifies identity protection of exposed credentials – which can be used to enforce controls such as MFA or password resets.
Sending Exposed Credentials to Identity Protection
Let’s walk through an example of sending exposed credentials to identity protection. A recon notification informs me of exposed data.
This fictitious company, “travel airlines”, has had their data exposed by LockBit. The eCrime adversary BitWise spider, who are infamous for their use of LockBit, are correlated to this exposure event.
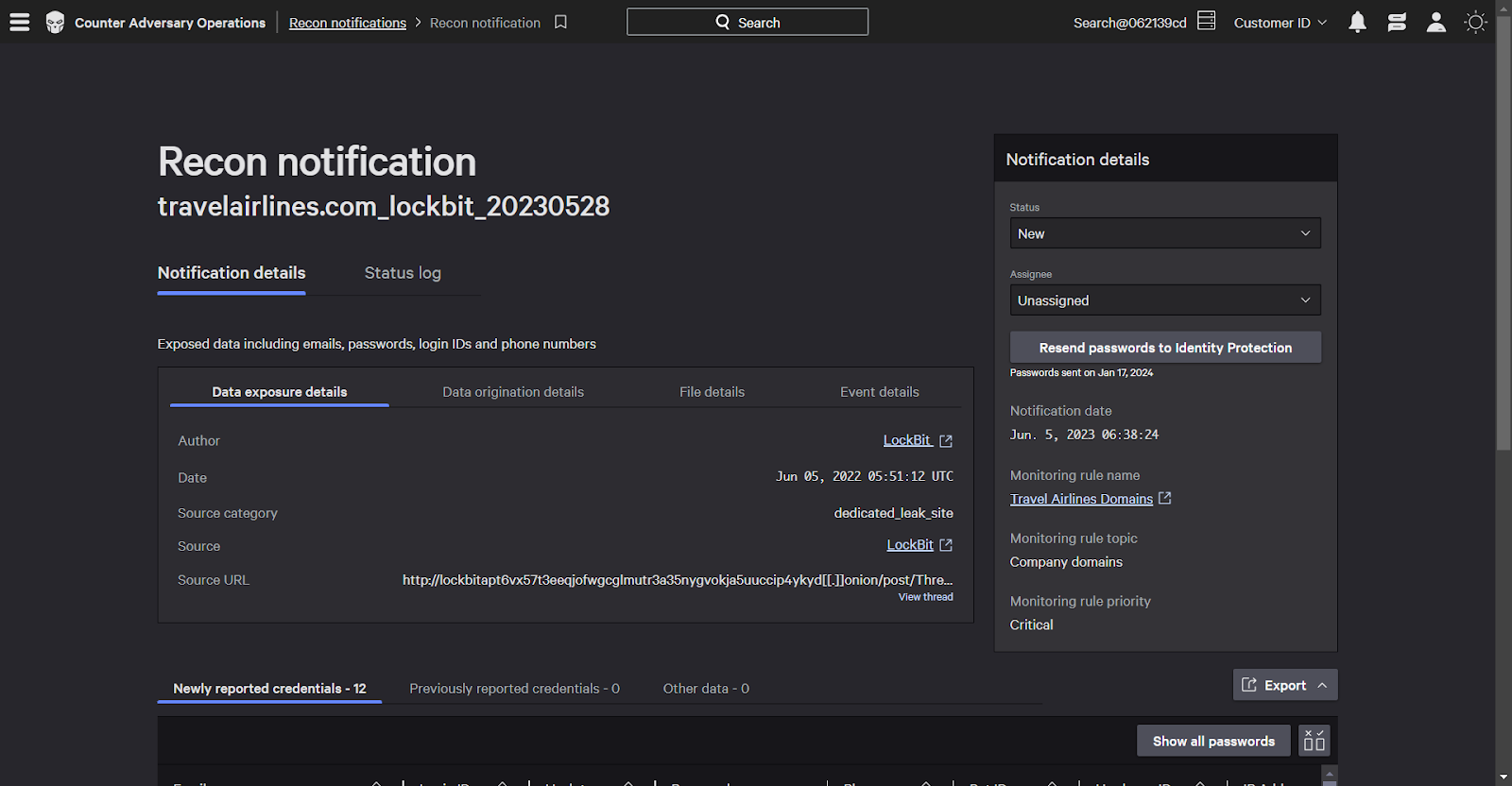
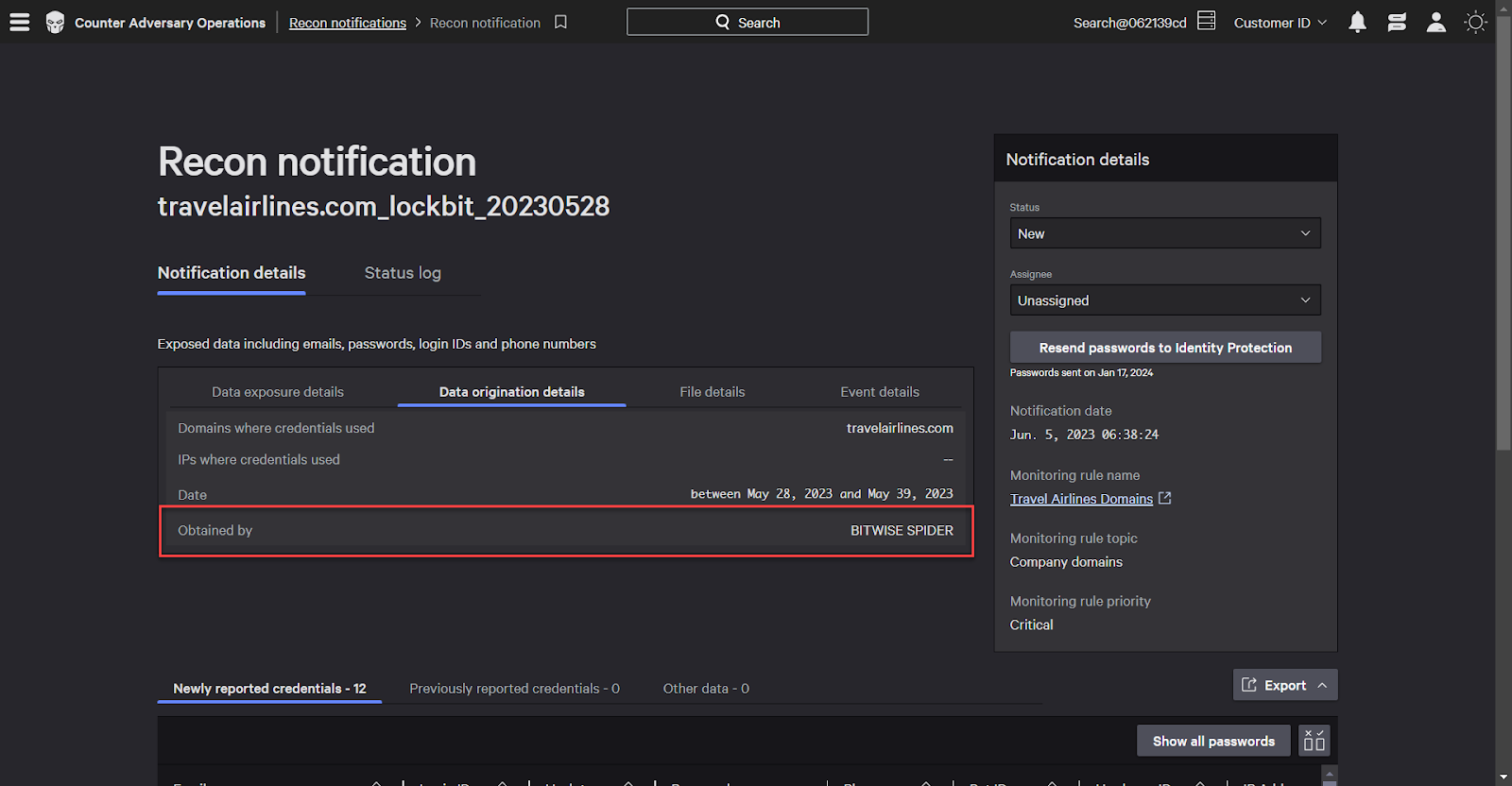
Listed below is a table of exposed data. A number of identities, including usernames, passwords, and more have been compromised.
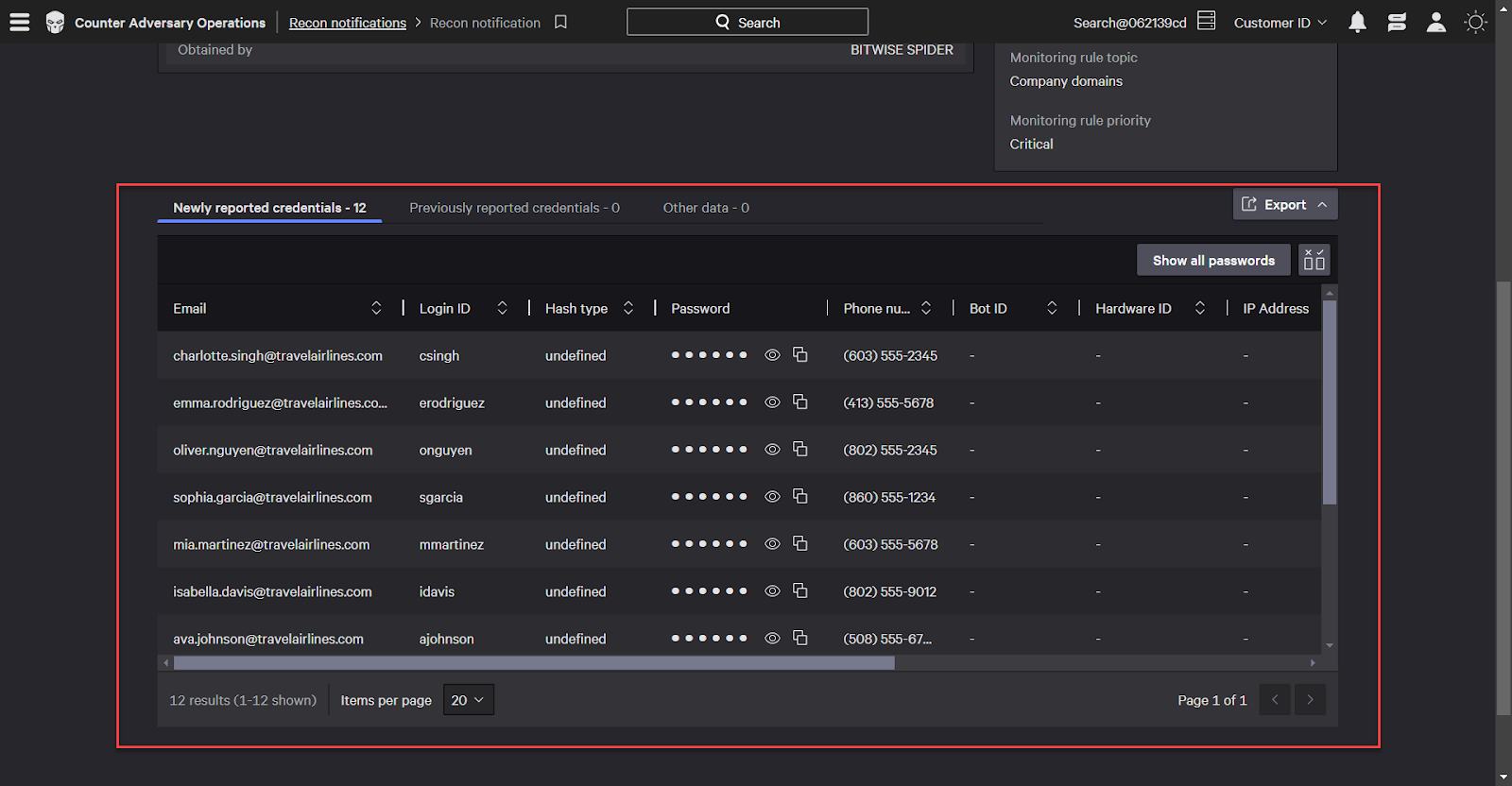
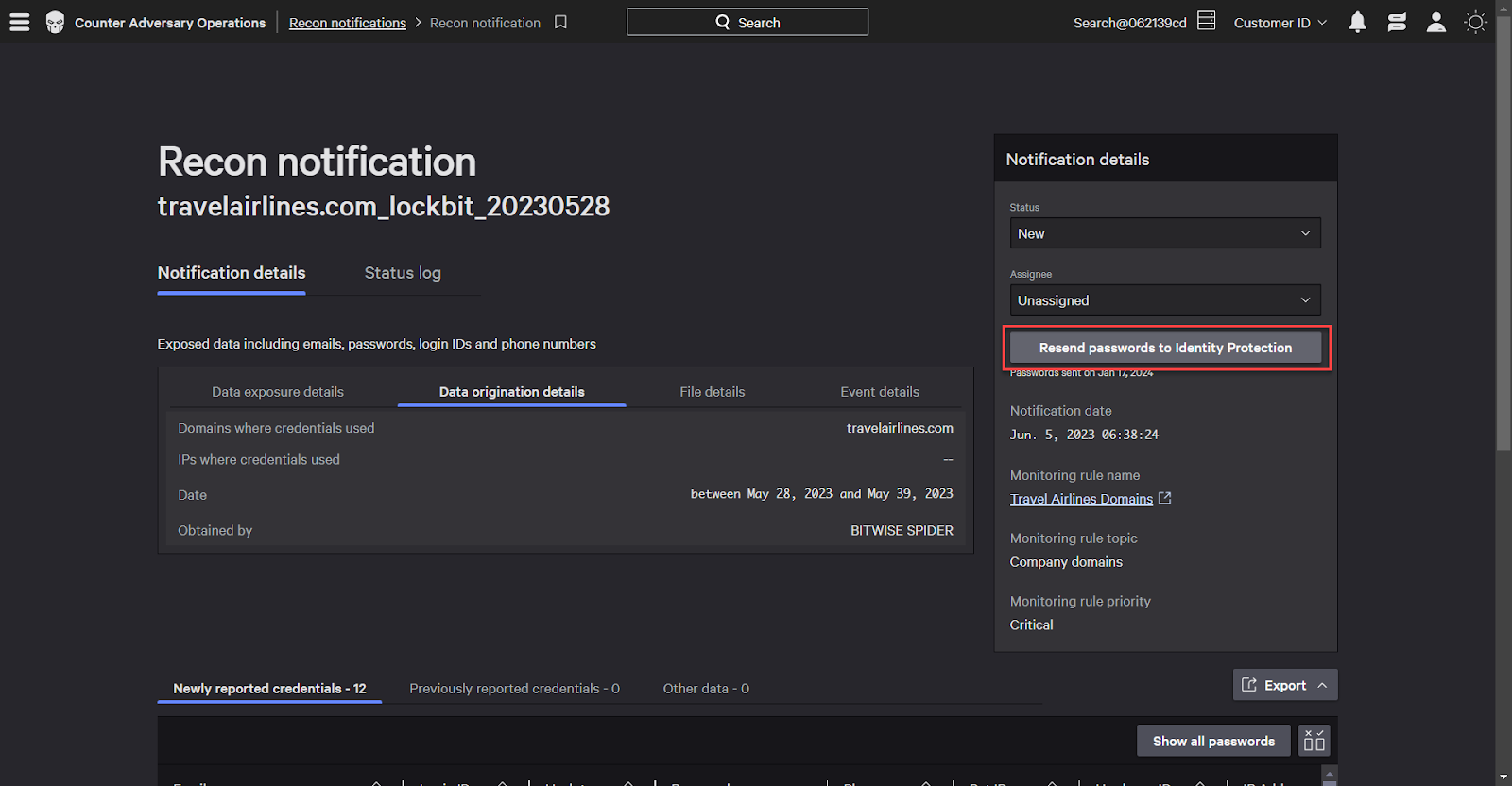
Click the Send Passwords to Identity Protection button to mark these accounts as having a compromised password in identity protection.
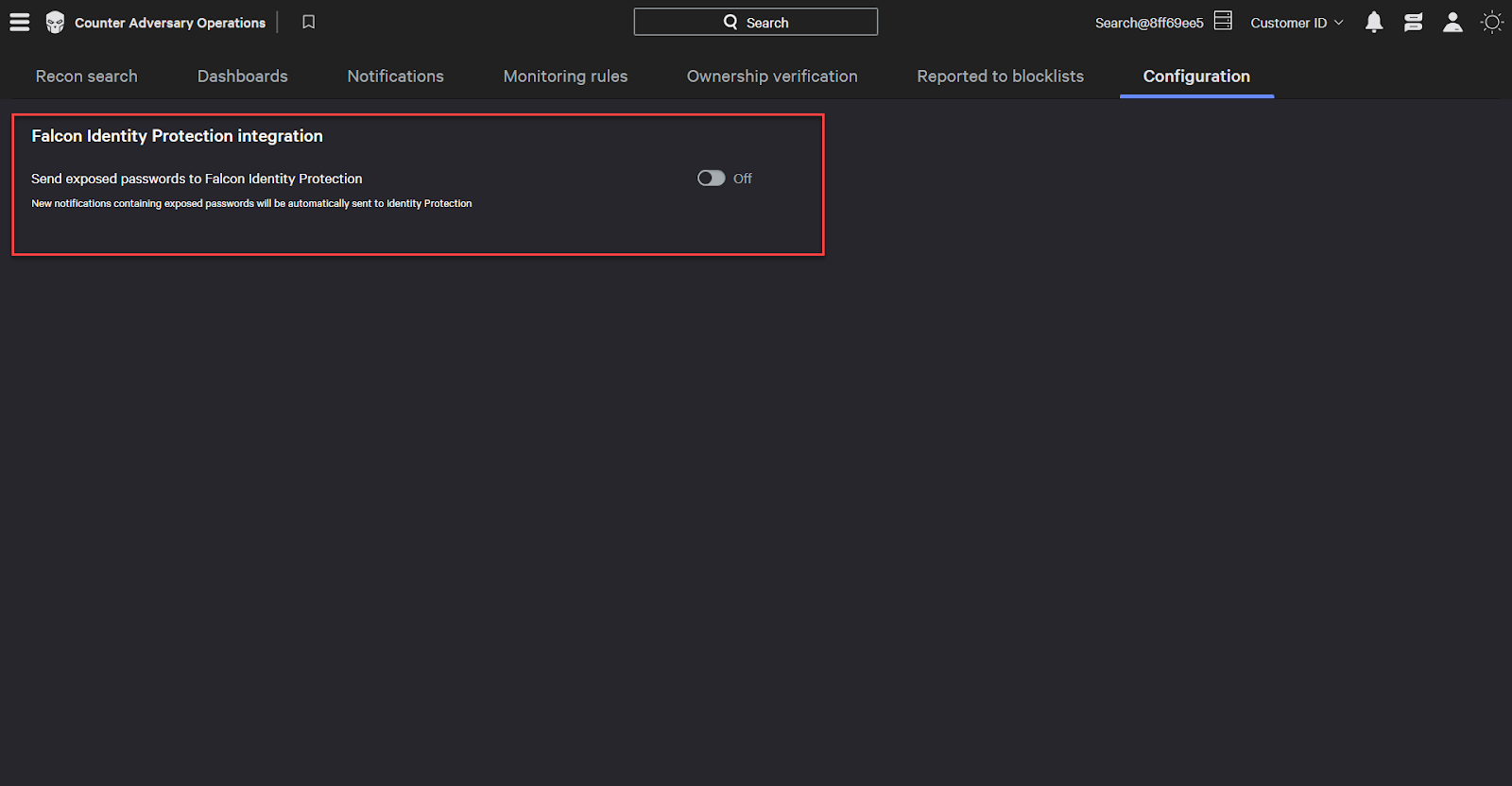
You can also automatically send any exposed passwords to identity protection. In the Configuration tab for Recon, click the toggle to automatically send any exposed password to Falcon Identity Protection.
Stop Adversaries from Leveraging Stolen Credentials
In Identity Protection, these accounts will be marked with the compromised password attribute. This also increases the risk level for the compromised identity. Compromised passwords are denoted by the unlocked lock icon when viewing entities.
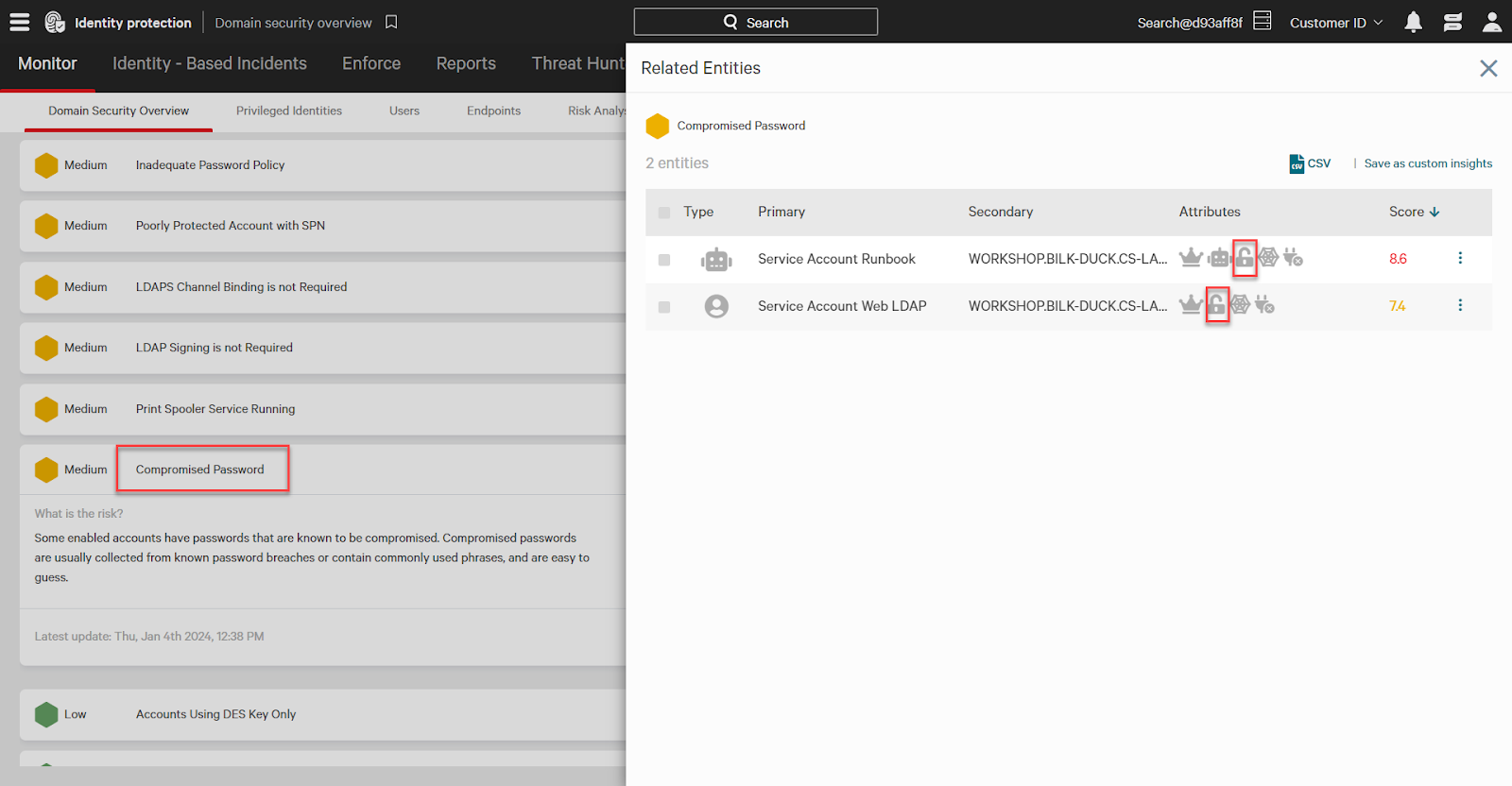
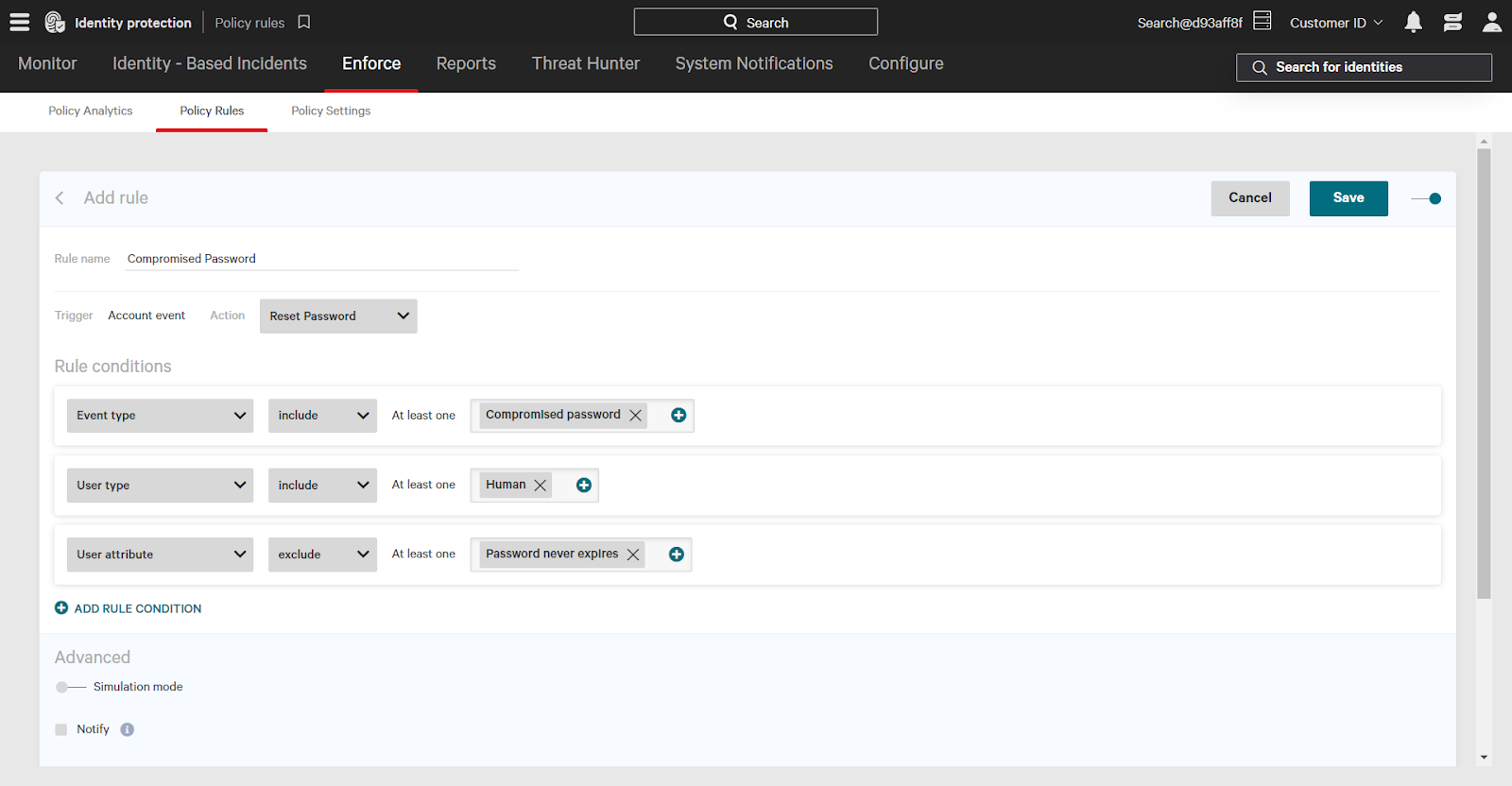
Using identity protection policies, such as the OOTB “Compromised Password” rule, will automatically require the affected user to change their password at their next login.
Identity policies are highly customizable. Use the compromised password attribute to lock down access to critical resources, enforce identity verification, and much more.
Conclusion
CrowdStrike’s unified Falcon Platform gives you comprehensive protection and visibility. Use Recon and Identity Protection to get real-time visibility into data breaches, and take action to stop attackers from leveraging exposed credentials.