Identity Protection – Threat Hunting

Summary
In this resource you will learn how to proactively threat hunt with CrowdStrike Falcon Identity Protection.
The Problem
Attackers increasingly target identity. In 2023, CrowdStrike saw a 583% increase in Kerberoasting attacks alone. Instead of kicking down a door, with valid credentials they can simply use the key. With valid credentials, attackers can skip stages of the attack lifecycle and reach their end goals even faster.
The Value of Falcon Identity Protection
CrowdStrike Falcon Identity Protection enables you to proactively threat hunt identity events. Falcon’s easy-to-use search makes threat hunting easy – so you can quickly find events of interest and ultimately stop breaches.
Using Threat Hunter
Using the main menu, navigate to the Identity Protection -> Threat Hunter. The Threat Hunter page shows all identity events that have occurred.
Identity events include:
- Access events (ex: RDP)
- User account events (ex: password changed)
- Identity detection (ex: honeytoken activity)
…among many more.

Use filters at the top of the screen to narrow your search. Filters can be layered for specific threat hunting queries and are available under 5 different categories:
- Event Types: authentication type, service, user account events, and more
- General: sort order, time zone, and more
- Identity: username, department, privileges, attributes, and more
- Source Endpoint: endpoint name, group, OU, attributes, and more
- Destination: destination name, group, privileges, attributes, and more
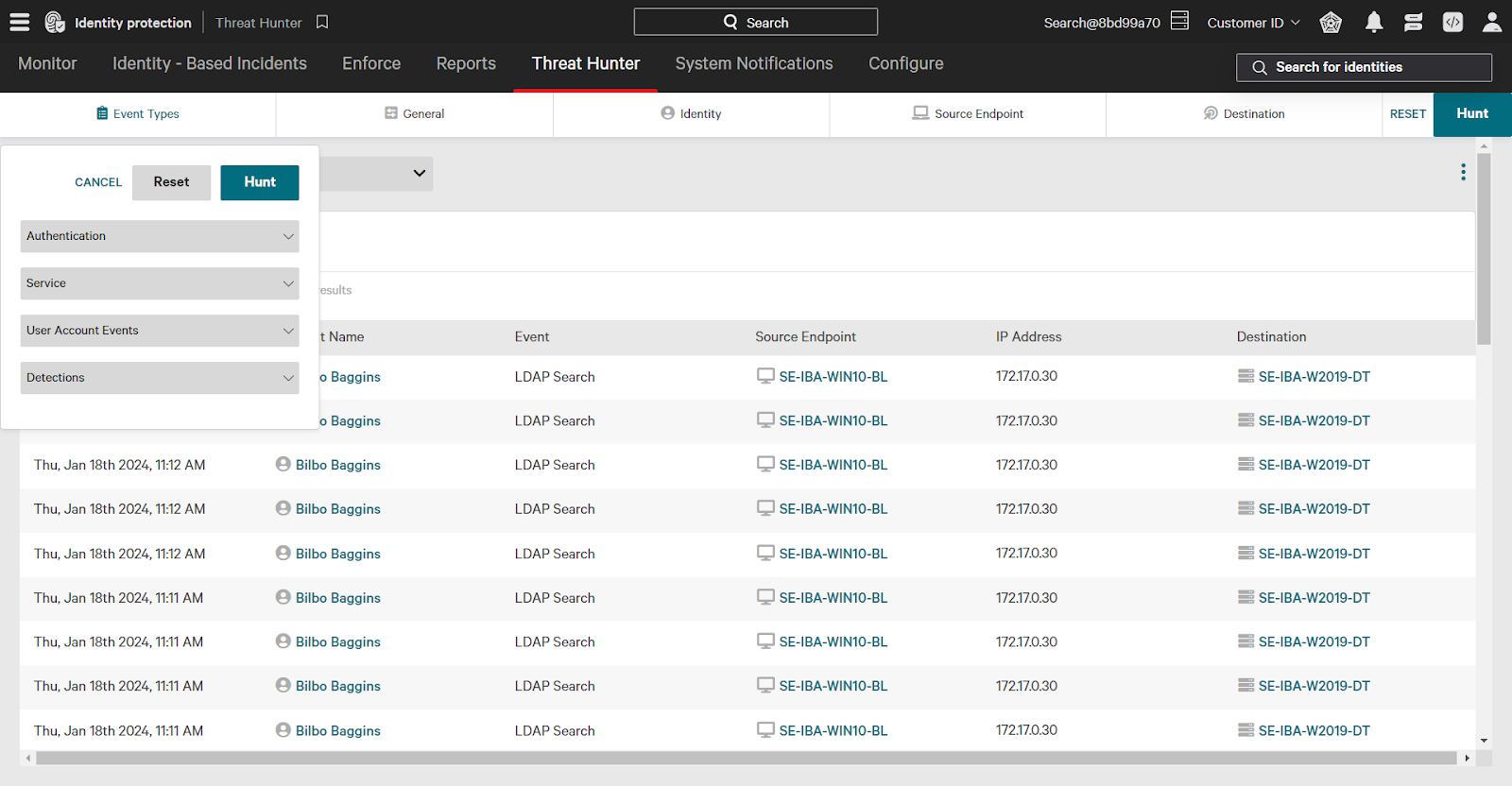
Building a Threat Hunter Search
One common use case for threat hunting is looking for unusual activity. Let’s build out a search looking for programmatic accounts with unusual access events as an example. A programmatic, non-human account would be unlikely to use a service like remote desktop for access. This is just one example of a threat hunting search.
Falcon Identity Protection classifies identities automatically, assigning them attributes such as programmatic, human, etc. Use these attributes to filter threat hunting results – or even create policy rules.
Using the Identity filter, click the checkbox next to programmatic. This will filter results to only events involving a programmatic source identity.
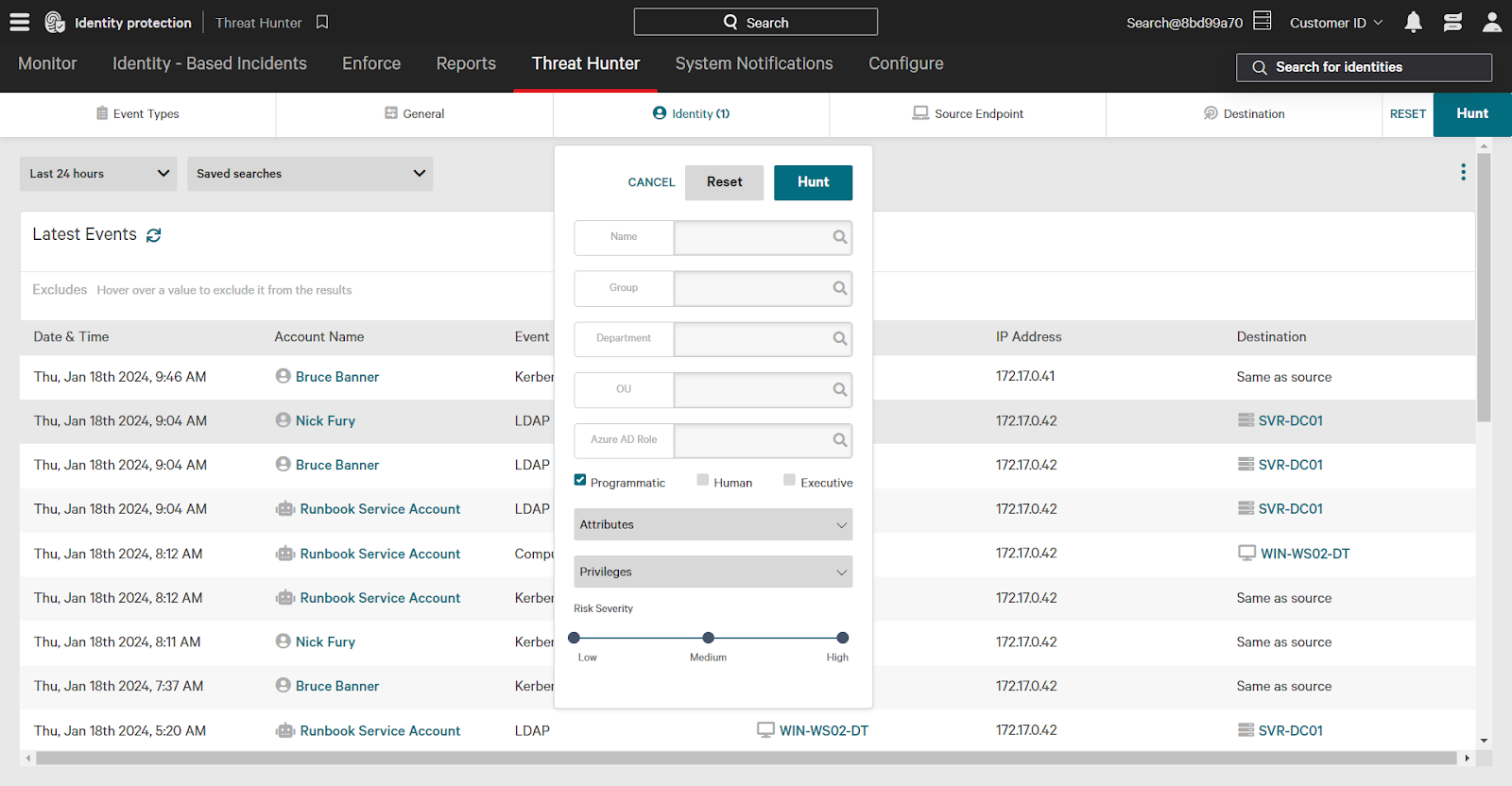
Next, using the Event Types category, click the Service dropdown to expand options. Then, select the checkbox next to Remote Desktop (RDP).
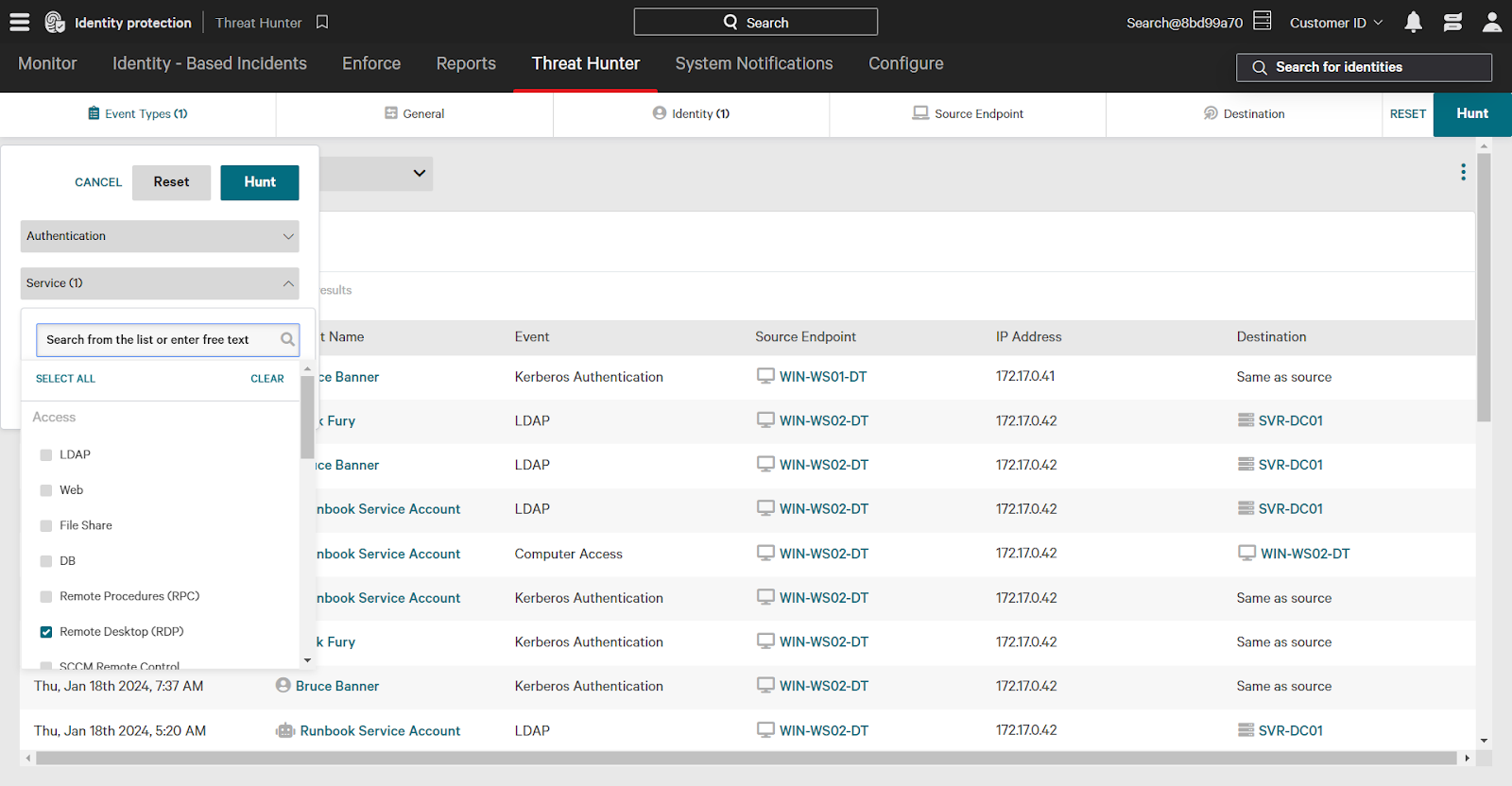
Finally, change the time filter to 7 days. Note that you can also filter by a custom time frame to investigate a specific time range of events.
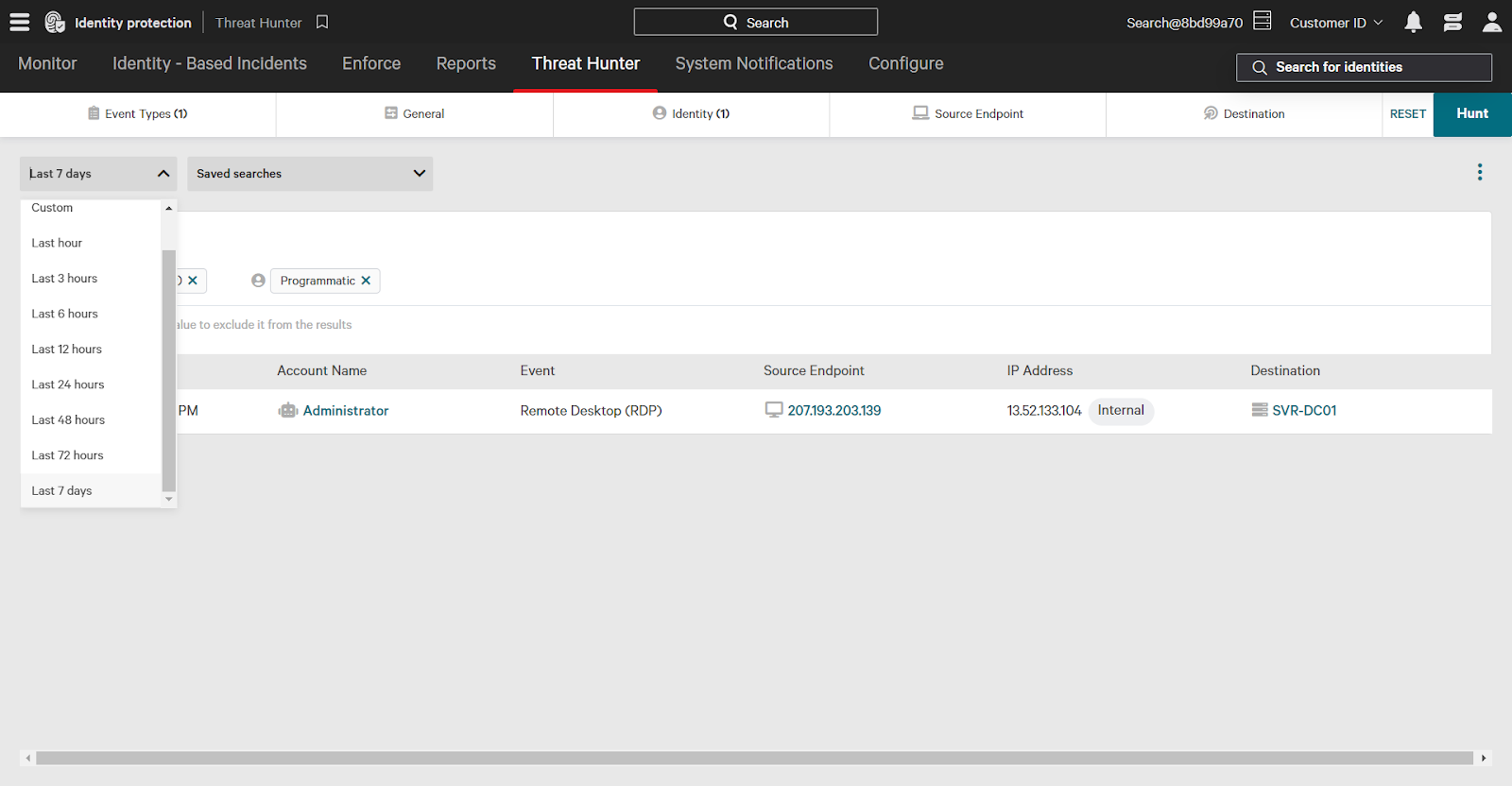
When finished adding filters, click Hunt in the upper right corner to apply filters and see results.
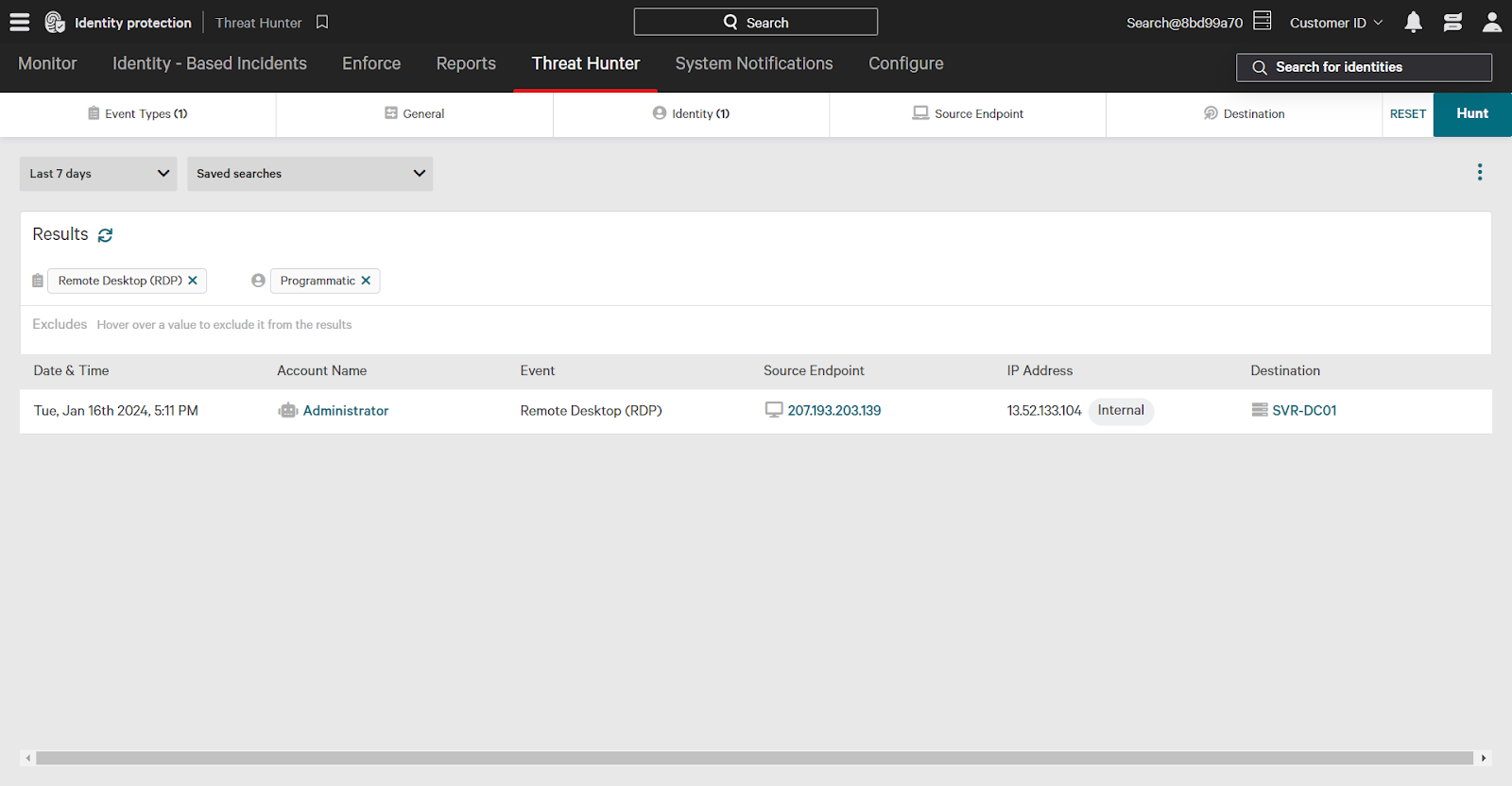
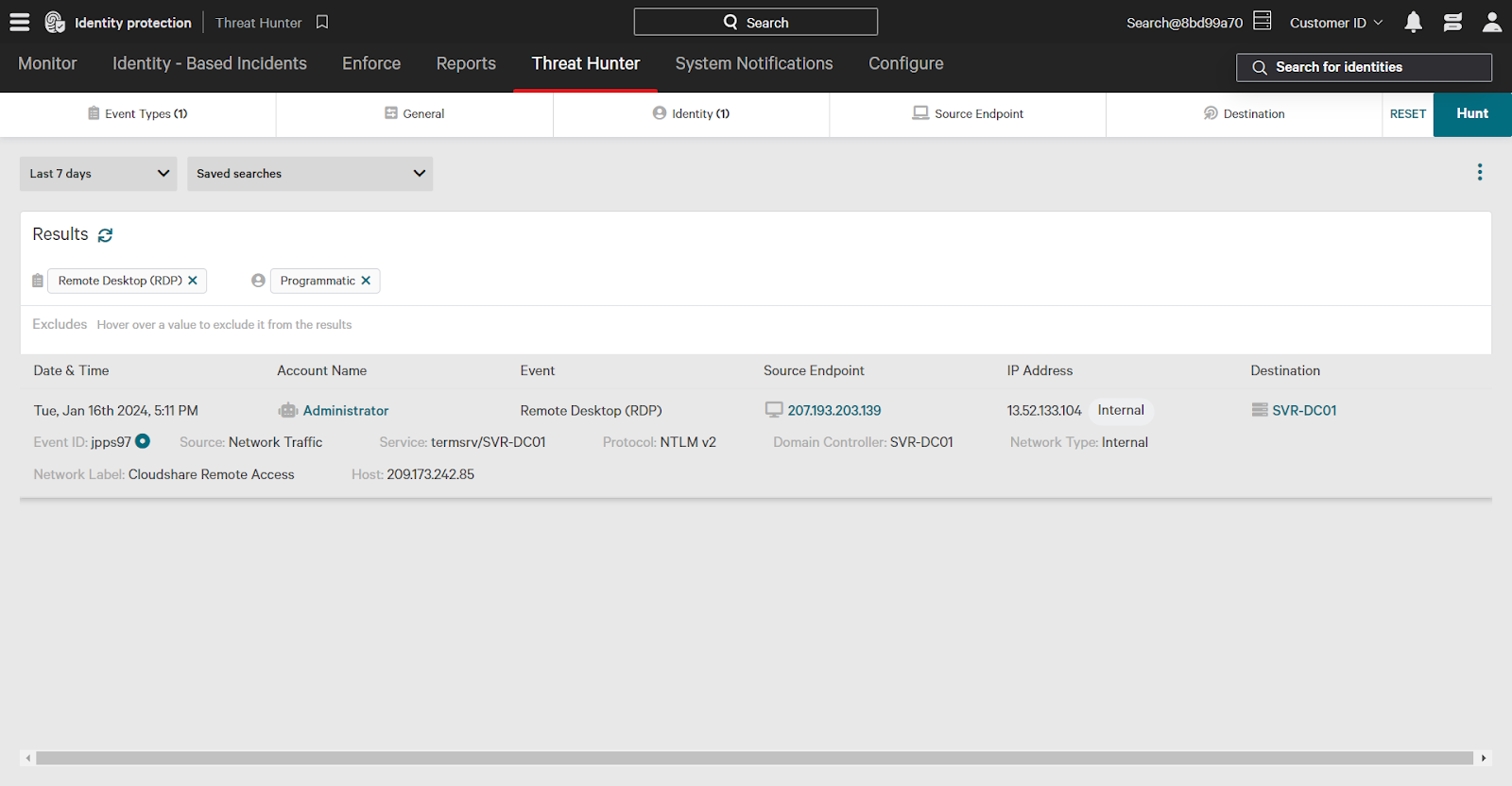
Investigating Events
When investigating in Threat Hunter, click an event to expand additional detailed information such as protocol, source, and service used.
In this example, a programmatic account named Administrator accessed a domain controller via remote desktop.
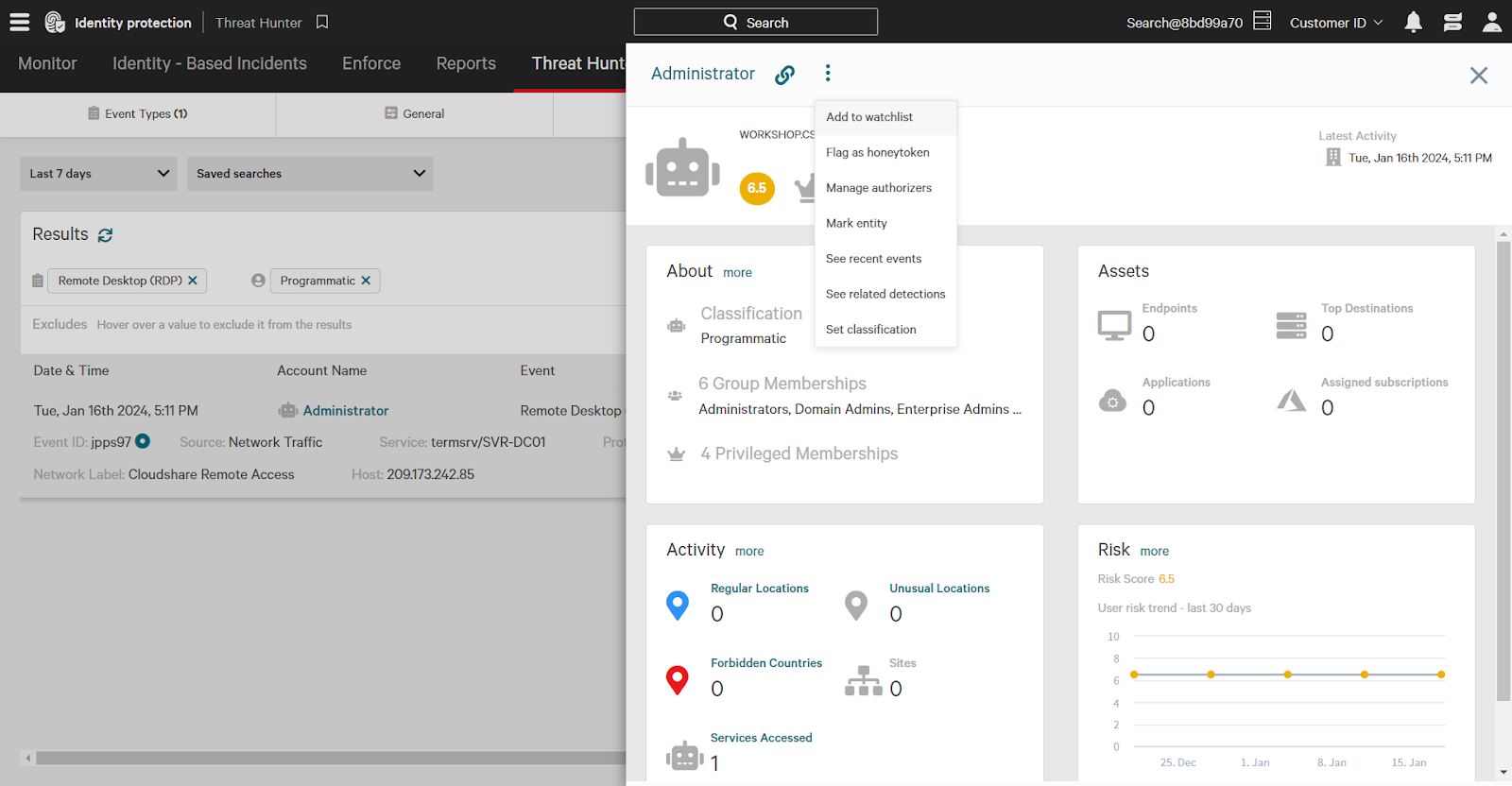
Quickly take action on entities like users and endpoints from the Threat Hunter page. For example, clicking the Administrator account expands additional information. Click the three dots next to the entity name to expand action options, such as adding to the watchlist. A watched entity indicates greater risk; the “watched” attribute can be used in policy rules.
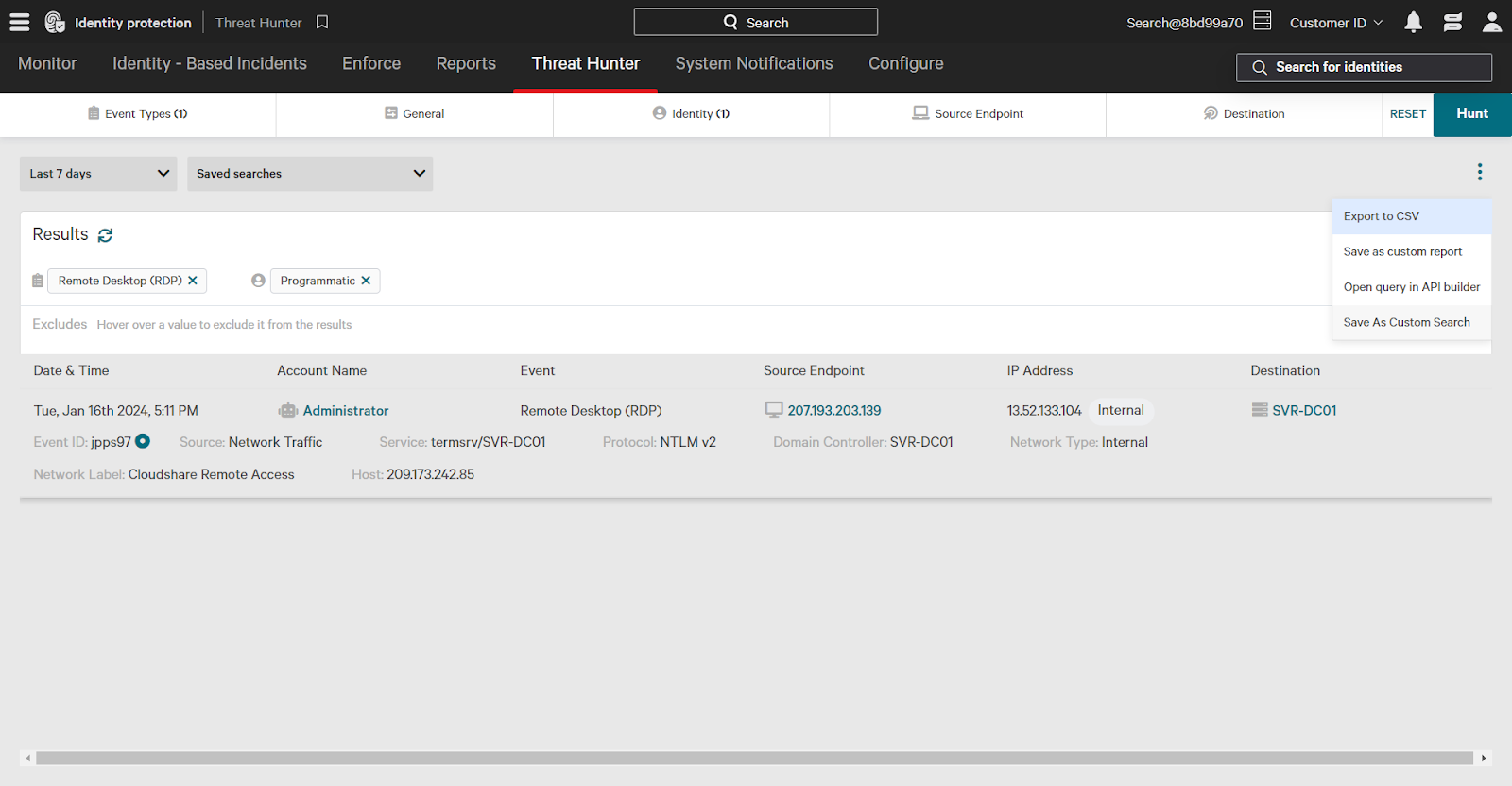
Saving Threat Hunter Searches
You may have Threat Hunter searches that will be frequently reused for future investigations. Save a search by clicking on the three dots and then click Save As Custom Search.
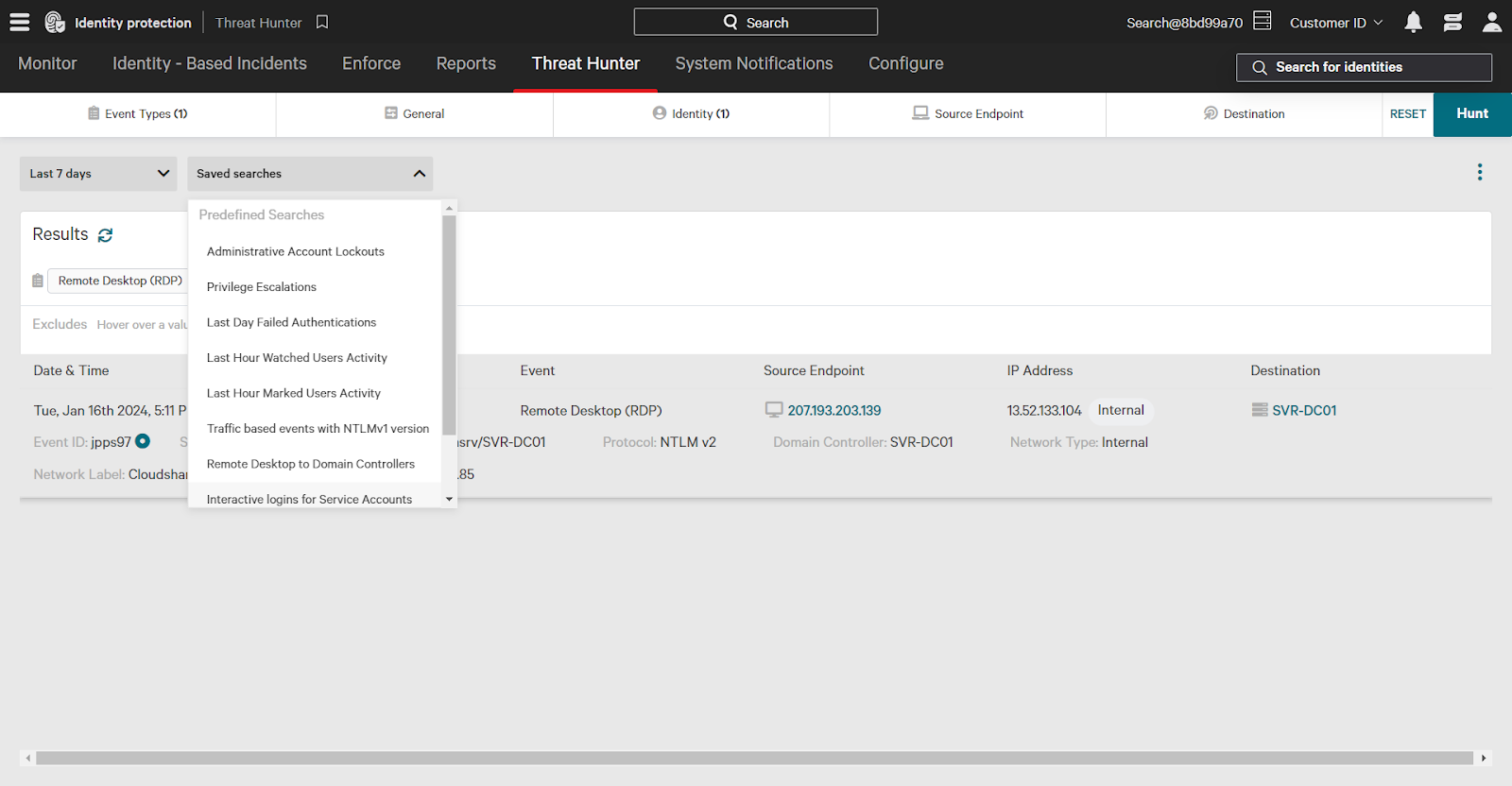
To use a saved search, click the Saved Searches dropdown and select your search from the dropdown.
Conclusion
CrowdStrike Falcon Identity Protection provides you with robust, simple to use proactive threat hunting capabilities with visibility into your entire identity environment.