Hunting Weaponized Chrome Extensions with Falcon for IT

As cyber threats grow more sophisticated, maintaining visibility and control over all endpoints in your environment is more critical than ever. Weaponized Chrome extensions have emerged as a new avenue for attackers, making them a priority target for detection and mitigation. Leveraging CrowdStrike Falcon for IT, security and IT teams can streamline the process of identifying and neutralizing malicious extensions, all while maintaining a unified approach to IT operations and cybersecurity.
Why Focus on Weaponized Chrome Extensions?
Malicious Chrome extensions can:
- Act as conduits for data exfiltration
- Execute malicious scripts within the browser
- Provide attackers with persistent access to user credentials and sensitive data
Given their potential impact, these extensions must be swiftly identified and removed. CrowdStrike Falcon for IT provides a powerful and intuitive platform to hunt these threats across Windows, macOS, and Linux endpoints.
Key Resources for Understanding the Threat
To effectively address the risk of weaponized Chrome extensions, several key resources provide valuable context and intelligence:
- CrowdStrike Tech Alert on 12/27 outlines the scope of the threat and actionable guidance for detection.
- Counter Adversary Operations Report published on 12/26 provides a detailed analysis of recent adversary activities involving malicious extensions.
By leveraging these resources alongside Falcon for IT, organizations can stay informed and prepared to combat these evolving threats.
The Power of Falcon for IT
CrowdStrike Falcon for IT is designed to unify security and IT operations. With its advanced live asset query capabilities and seamless integration into your existing workflows, Falcon for IT empowers teams to:
- Gain real-time visibility into endpoints
- Automate IT hygiene and compliance tasks
- Address vulnerabilities and misconfigurations quickly
For tackling weaponized Chrome extensions, Falcon for IT offers a precise, scalable, and real-time method to remediate endpoint risk before it can be exploited.
Hunting Weaponized Chrome Extensions
Step 1: Gathering Intelligence
Start by referencing known suspicious Chrome browser extensions. This list, often provided in advisories or community forums, includes the unique extension IDs of known-bad extensions.
Step 2: Leveraging Falcon for IT
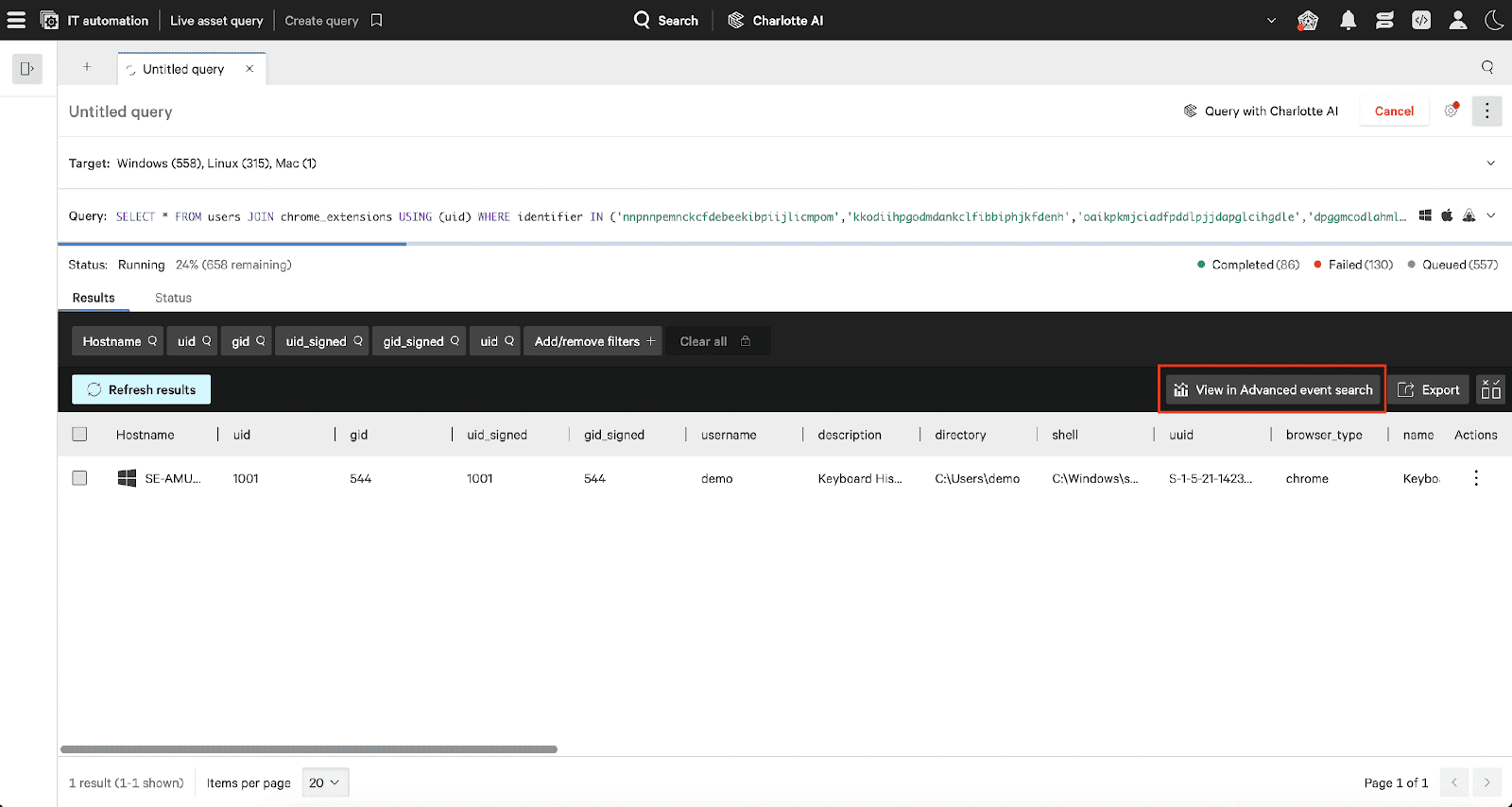
1. Access Live Asset Query: Navigate to IT Automation > Live Asset Query in Falcon’s interface. Falcon for IT enables real-time inspection of your endpoints for immediate visibility into potential impact.
2. Input osquery Syntax: Use the following query to detect malicious extensions across platforms:
SELECT * FROM users
JOIN chrome_extensions USING (uid)
WHERE identifier IN ('list_of_extension_ids');
Replace list_of_extension_ids with the specific IDs from the Appendix or other known malicious browser extensions.
Example:
SELECT * FROM users
JOIN chrome_extensions USING (uid)
WHERE identifier IN
(‘nnpnnpemnckcfdebeekibpiijlicmpom’,
‘kkodiihpgodmdankclfibbiphjkfdenh’,
‘oaikpkmjciadfpddlpjjdapglcihgdle’,
‘dpggmcodlahmljkhlmpgpdcffdaoccni’,
‘acmfnomgphggonodopogfbmkneepfgnh’,
‘mnhffkhmpnefgklngfmlndmkimimbphc’,
‘cedgndijpacnfbdggppddacngjfdkaca’);
3. Select Platforms: Ensure the query covers Windows, macOS, and Linux by selecting the relevant platforms in the interface.
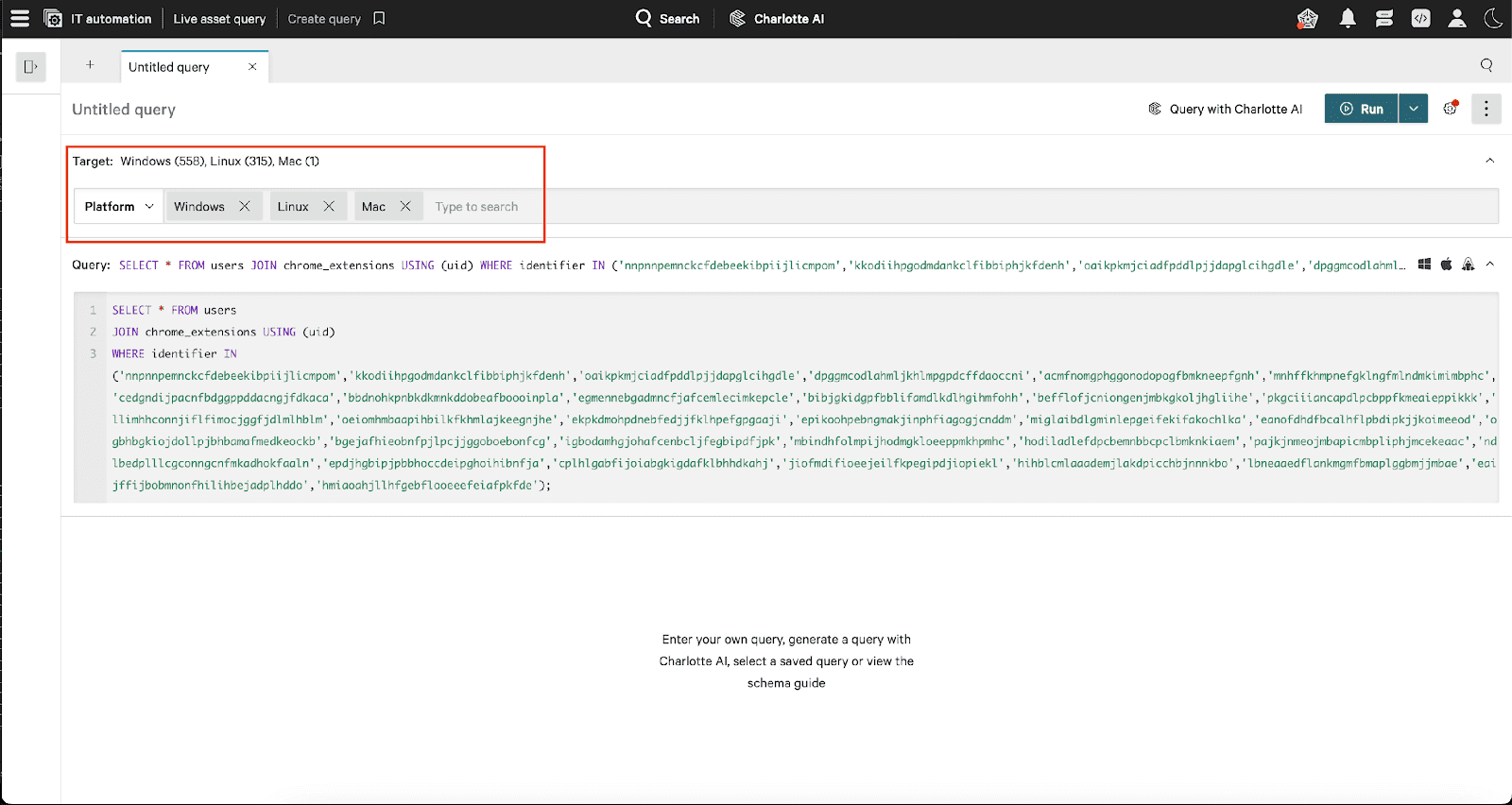
4. Run the Query Execute the query to scan live endpoints. Falcon for IT will immediately return results for any matches.
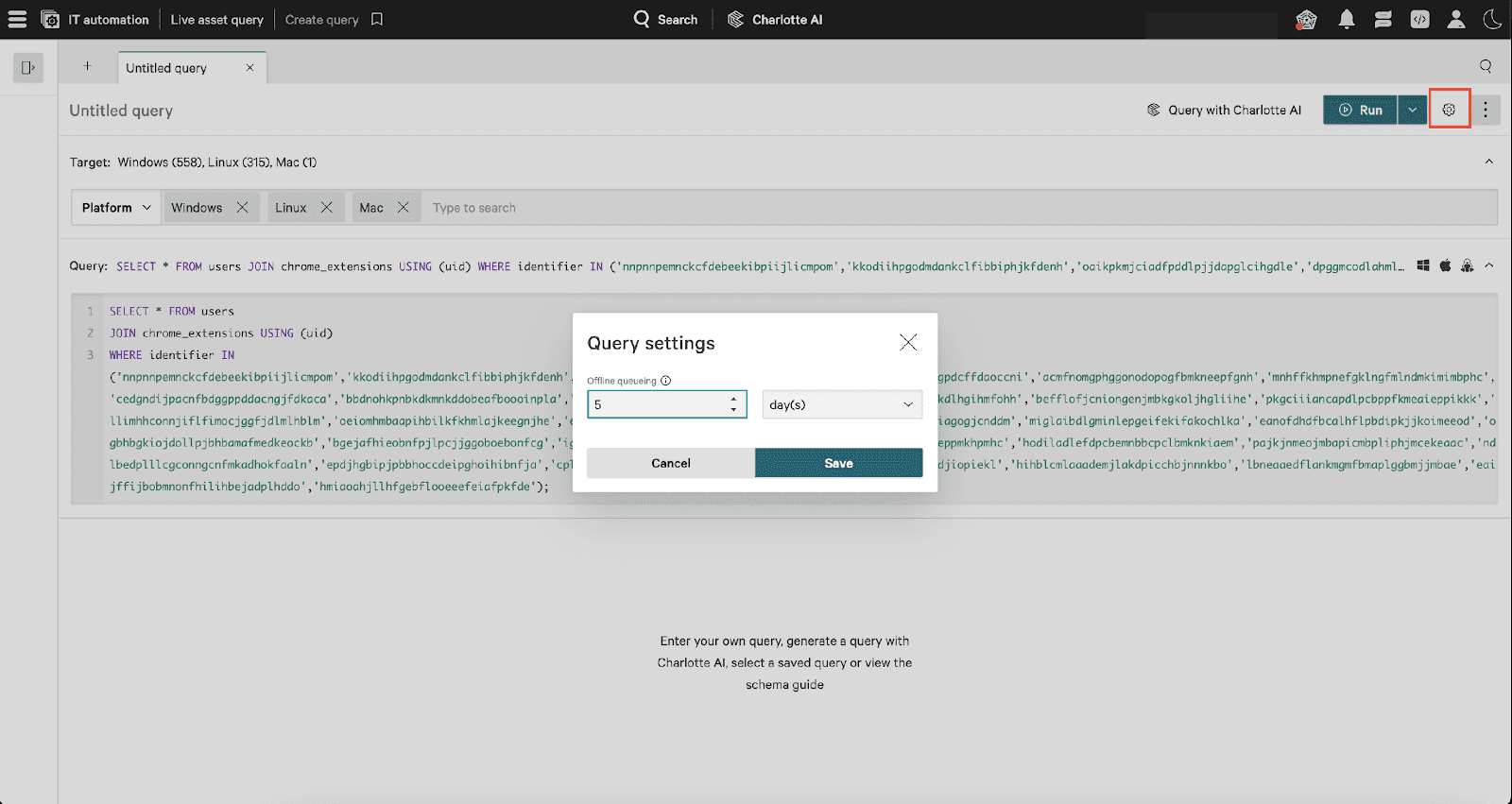
Step 3: Managing Offline Endpoints
Falcon for IT’s offline queuing feature ensures offline assets are scanned as they come online. To enable this, adjust the gear settings to queue the query with an expiration period.
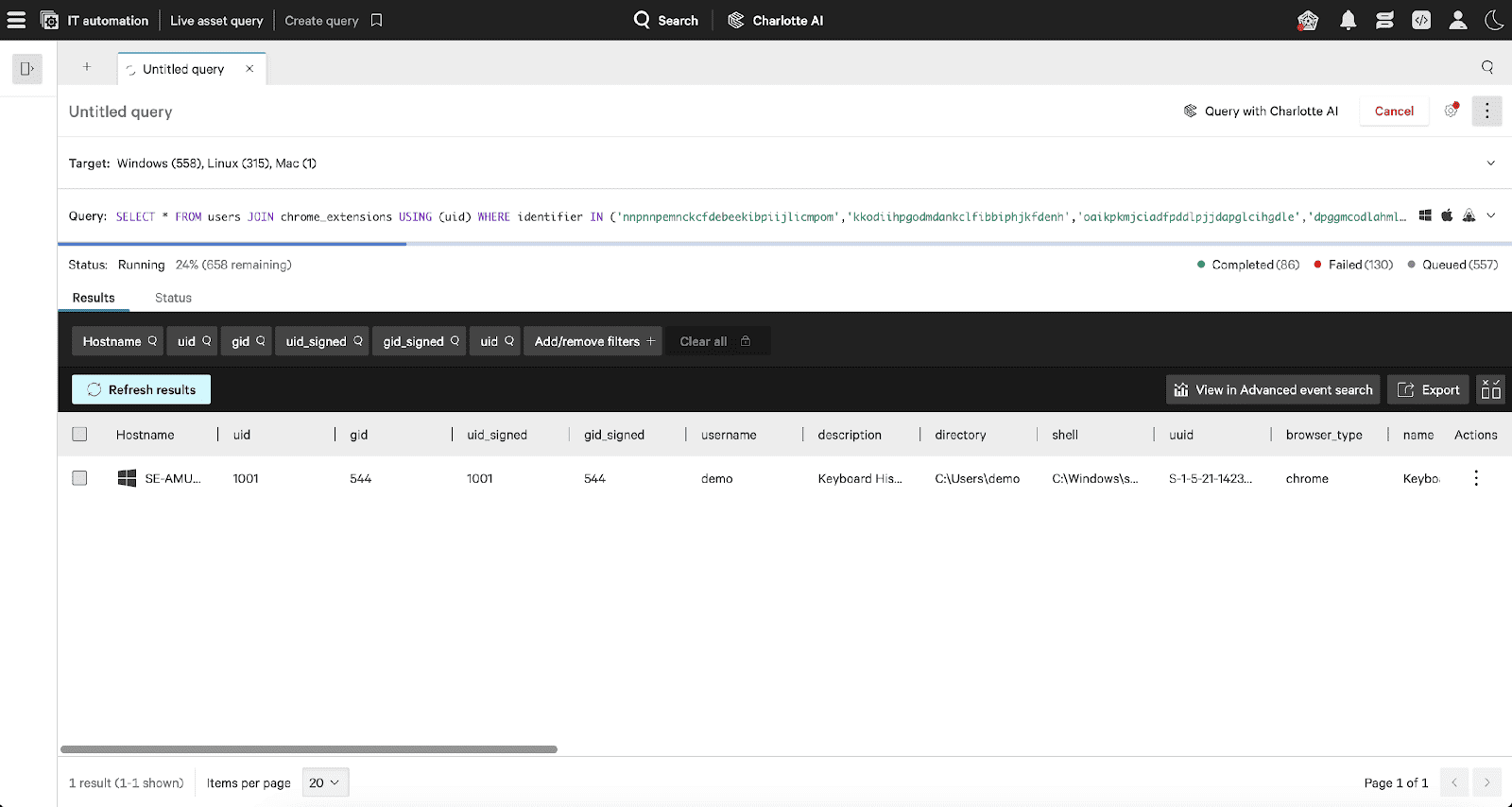
Step 4: Analyzing Results
Falcon for IT allows for results to be viewed in the Live Asset Query interface or within Falcon Next-Gen SIEM for additional context.
1. Viewed directly within the Live Asset Query interface
2. Exported to Next-Gen SIEM for further analysis
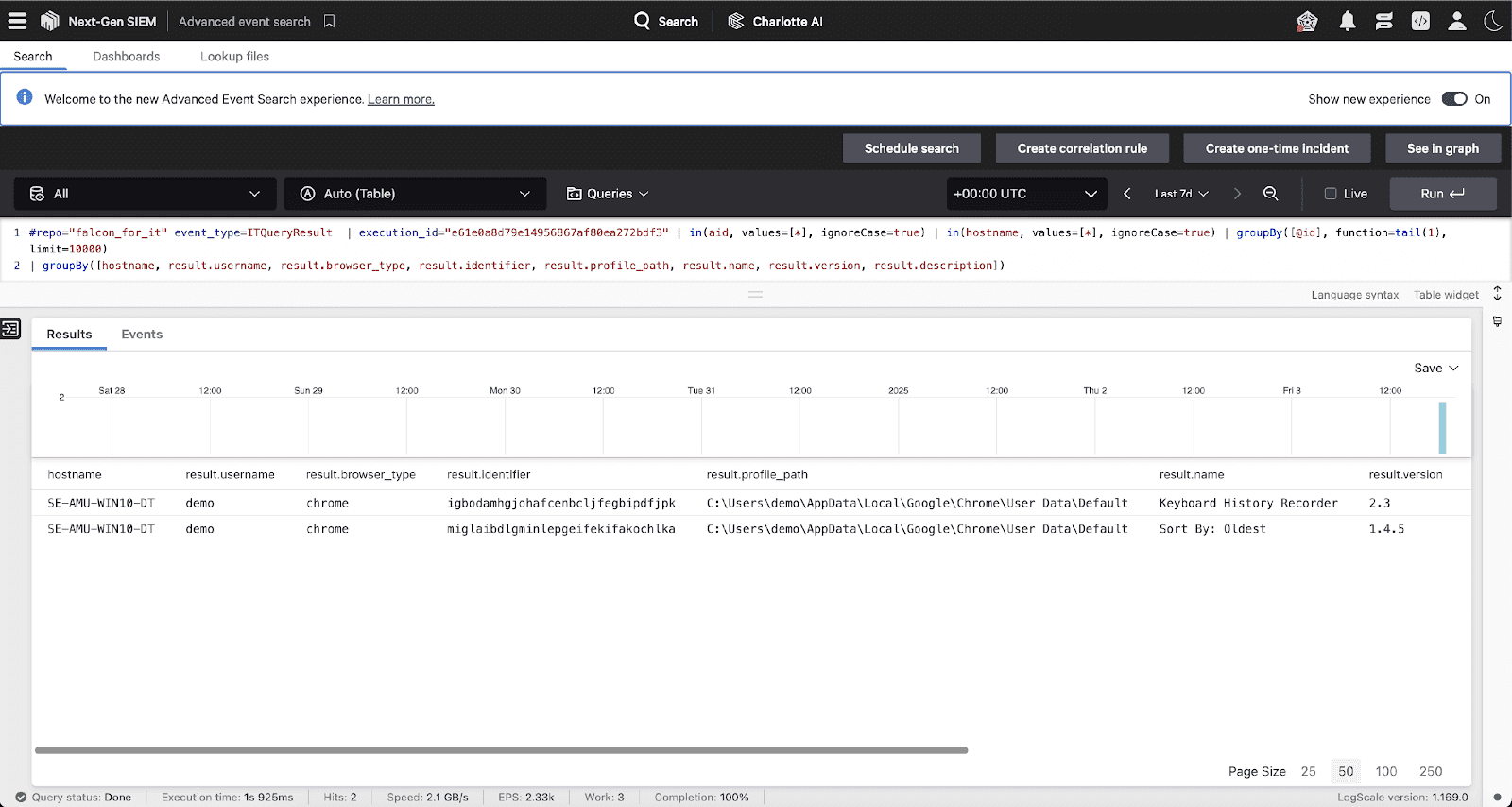
To aggregate and manipulate results in Next-Gen SIEM, add a grouping command to your query, such as:
[ prepopulated query is here ]
| groupBy([hostname, result.username, result.browser_type, result.identifier, result.profile_path, result.name, result.version, result.description])
The “Live” box next to Search can be selected to have the results updated in real time as the Falcon for IT query executes across your fleet.
Step 5. Remediation with Falcon for IT
Once weaponized Chrome extensions are identified, swift remediation is critical to maintaining security and compliance. Falcon for IT simplifies the remediation process by enabling security and IT teams to:
- Remove Malicious Extensions: Streamline the removal of malicious extensions using Falcon for IT Quick Actions & Automated Tasks.
- Monitor and Verify Compliance: Continuously track endpoints to ensure all malicious extensions have been removed and compliance standards are met.
These steps, powered by Falcon for IT, ensure that organizations can respond effectively and minimize the impact of Chrome extension-based threats.
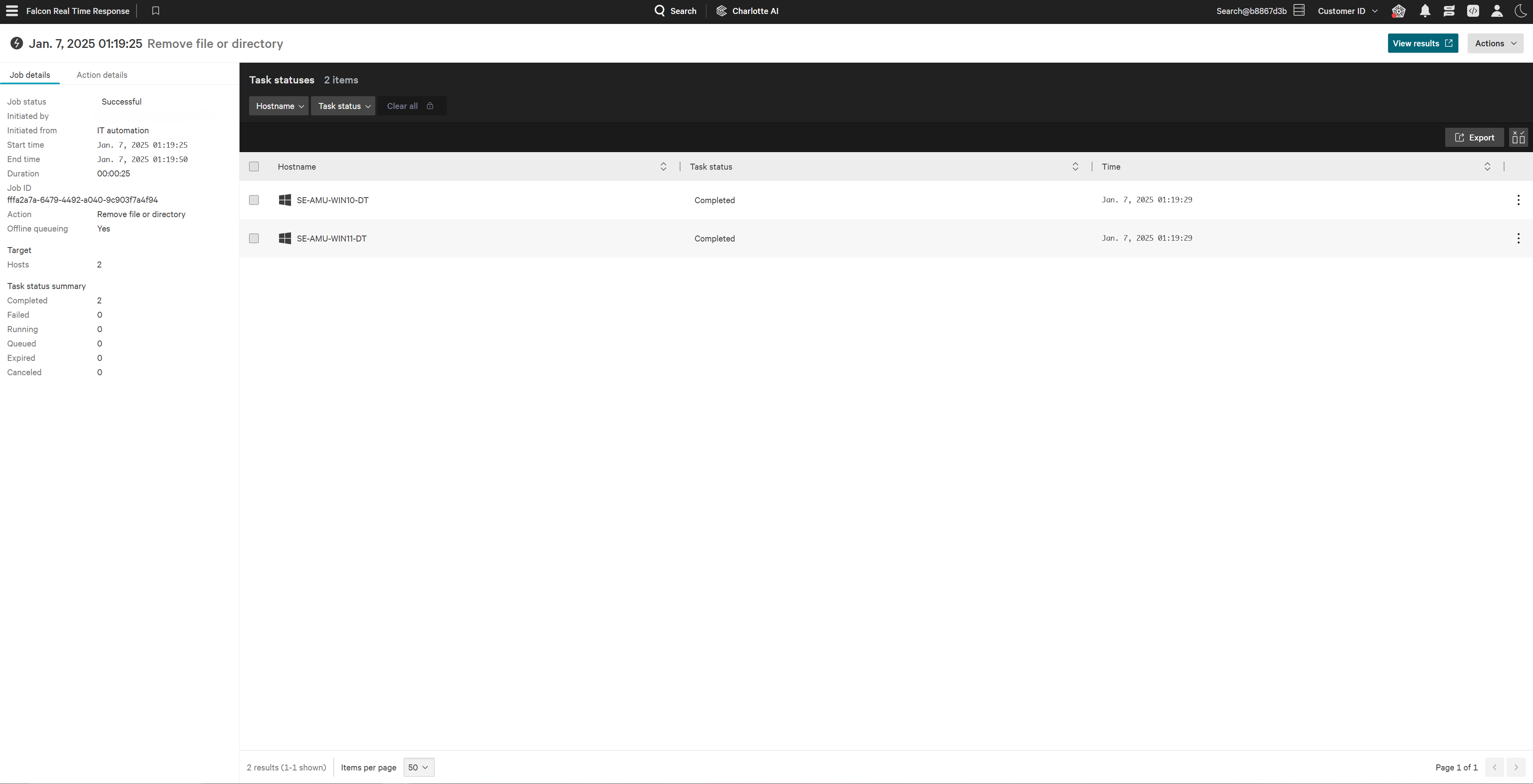
1. Select all endpoints that require the removal of the malicious browser extensions. Select the Actions Drop Down and navigate to Quick Actions.
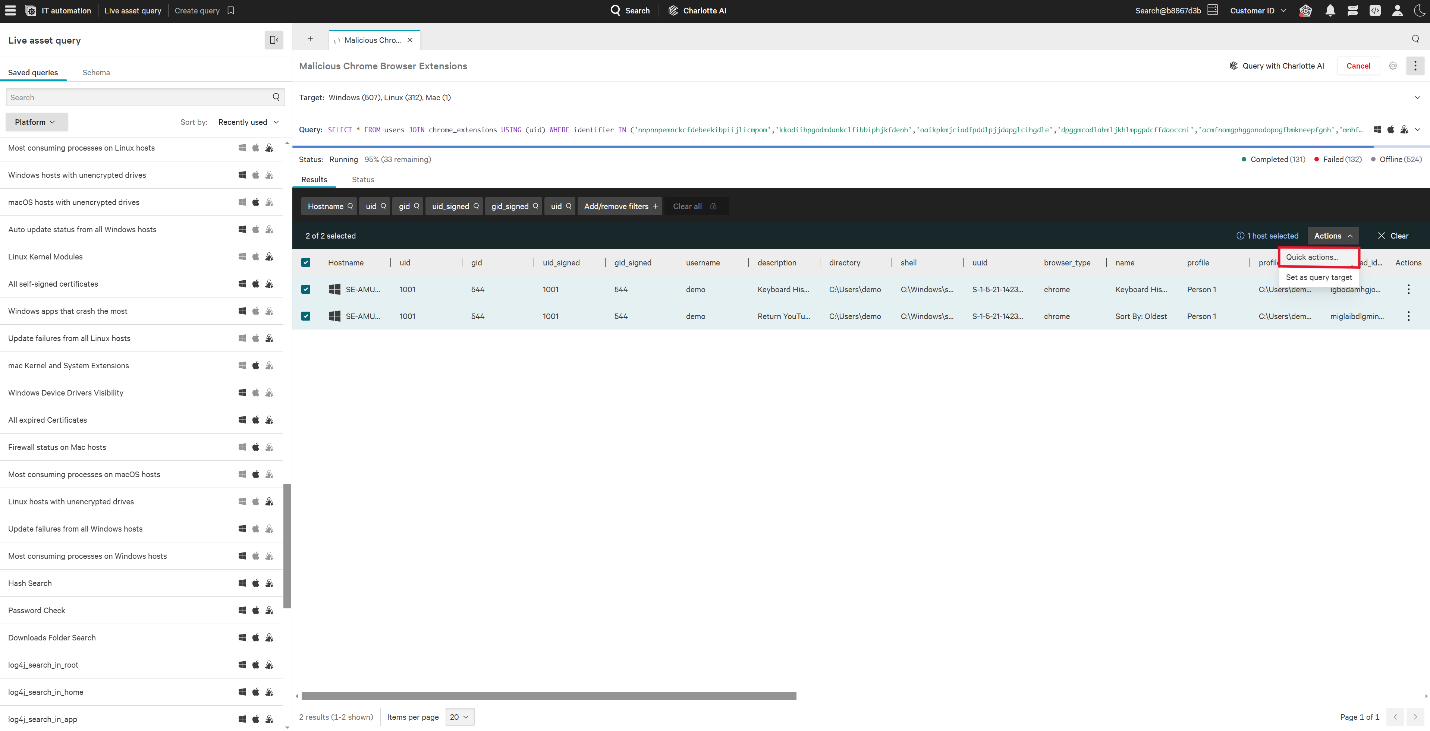
2. Utilize Falcon for IT’s real-time Quick Actions to deploy an action, which removes the malicious extension directory, uninstalling it from Google Chrome.
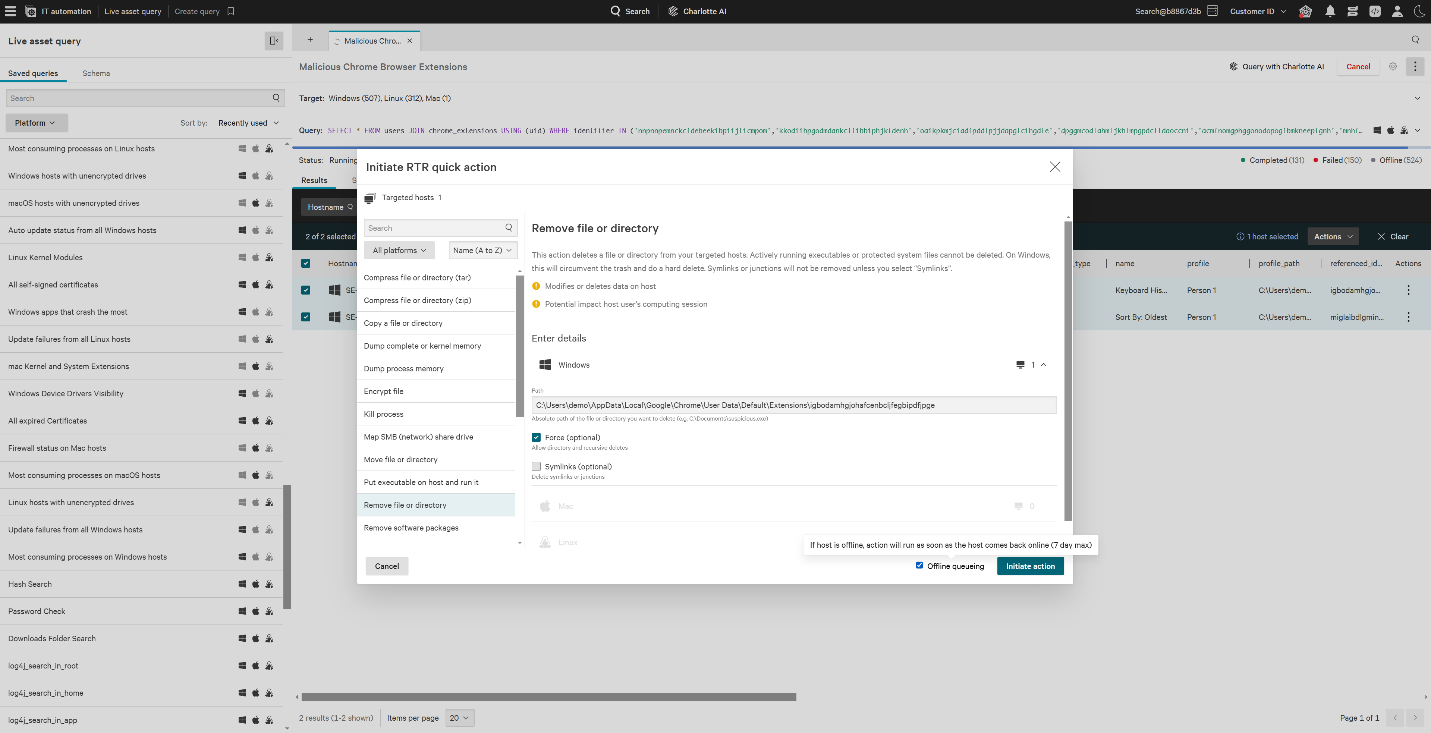
3. Confirm successful remediation by checking the Job Details pane, which offers real-time visibility into the progress and status of each action deployment.
Advantages of Falcon for IT over Traditional Methods
Falcon for IT provides unparalleled capabilities for malicious Chrome extension detection and remediation with:
- Real-time Visibility: Immediate insight into current device states
- Cross-Platform Support: Full coverage across Windows, macOS, and Linux
- IT and Security Integration: Unified platform to manage both security and IT operations
- Proactive, At-Scale Remediation: Utilize Falcon for IT to understand your exact exposure and execute immediate remediation with real-time validation.
Conclusion
Weaponized Chrome extensions represent a growing threat that requires a proactive and scalable response. CrowdStrike Falcon for IT offers a cutting-edge solution for detecting and mitigating these emerging and zero-day threats in real-time alongside scalable remediation workflows. By integrating IT and security operations, organizations can ensure their environments remain secure, compliant, and efficient.
Start leveraging Falcon for IT today to stay ahead of emerging threats. Learn more about Falcon for IT.