Harnessing Email Data to Stop Phishing Attacks with Falcon Next-Gen SIEM

Phishing is a formidable–and financially devastating–threat costing organizations $4.76 million USD per breach on average. With a simple, deceptive email, adversaries can masquerade as trusted entities, tricking even savvy individuals into handing over their credentials and other sensitive information. Whether it’s a duplicitous link or a crafty call to action, phishing remains one of the most insidious cybersecurity threats, leveraging a vulnerability that can’t be patched: human nature.
CrowdStrike Falcon® Next-Gen SIEM helps security teams detect and stop email-based attacks. By analyzing email security logs, SOC analysts can identify unusual attachments, malicious links, or email addresses to uncover attacks and speed up investigations. Email data allows analysts to trace the root cause of an attack, identify compromised accounts, and understand attackers’ methods.
This blog post demonstrates how simple it is to ingest data with Falcon Next-Gen SIEM. Then, it explains how to detect and counter phishing threats with Falcon Next-Gen SIEM, Falcon Fusion SOAR, and email data from Abnormal Security.
Maximize Your 10GB/Day Plan by Onboarding Email Data
Falcon Next-Gen SIEM transforms security operations to stop breaches by bringing together data, AI, workflow automation, and threat intelligence on one platform with one console and one lightweight endpoint agent.
To accelerate SOC transformation, Falcon Insight customers can ingest up to 10 gigabytes of third-party data per day at no additional cost, and experience the power and performance of Falcon Next-Gen SIEM. The 10GB/day offering is available today to the first wave of Falcon Insight customers and it will be released in waves to remaining customers over the next several weeks.
Make the most of your 10GB/day plan by ingesting high-value data, such as email security logs, into the Falcon platform to stop email-based threats. You can onboard email data using out-of-the-box integrations with email security solutions from Abnormal Security, Mimecast, and Proofpoint. An expanding array of data connectors support a broad set of log sources, while an HTTP event collector (HEC) lets you ingest data using prebuilt or custom parsers.
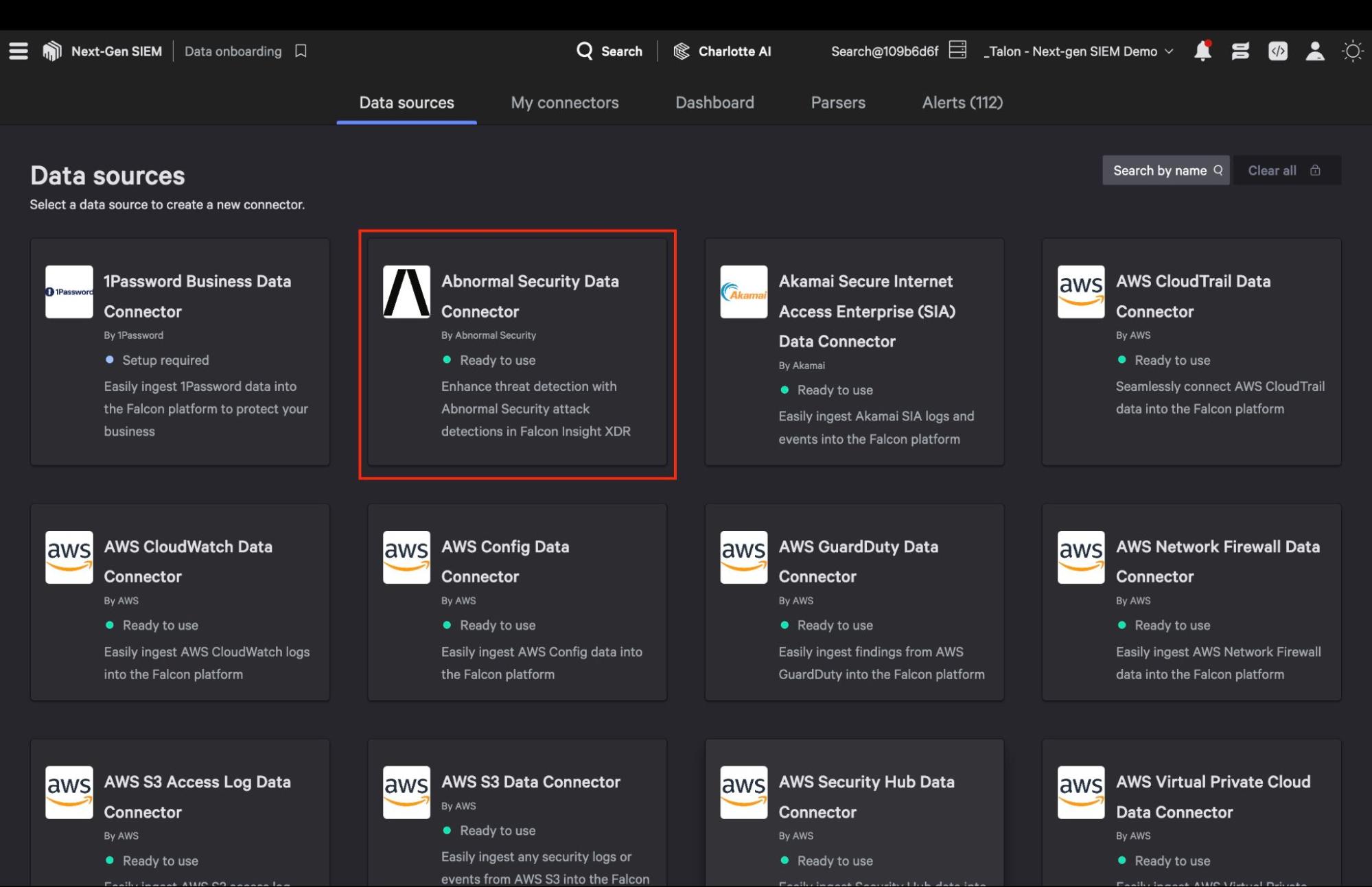
With Abnormal Security, data ingestion can be set up in just minutes. Start by generating an API token in the Abnormal administrator console; see the Falcon Next-Gen SIEM documentation for step-by-step instructions.
Next, create a new connector in the Falcon console by navigating to Next-Gen SIEM > Log management > Data onboarding and select the Abnormal Security Data Connector.
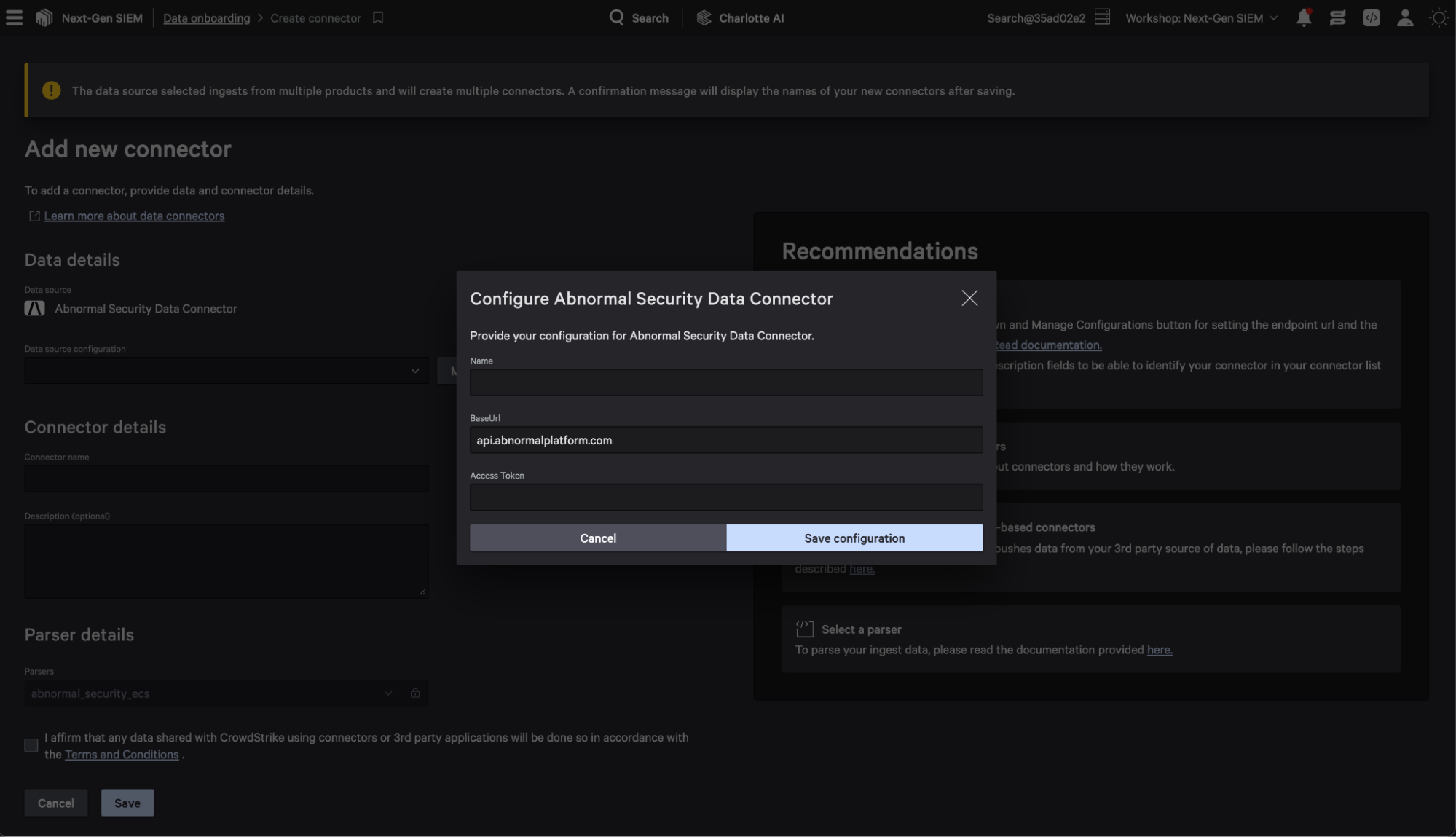
Enter the API key you generated, and Falcon Next-Gen SIEM will automatically connect to Abnormal and start ingesting data. Check out Falcon Next-Gen SIEM technical documentation for more detailed information on how to onboard data.
Defeating a Targeted Email Attack with Falcon Next-Gen SIEM
To illustrate how Falcon Next-Gen SIEM helps you combat email-based threats, let’s consider a scenario where an advanced adversary targets your organization–in this example, a high-interest think tank. The adversary’s primary goal is to infiltrate your organization and gather insights. The advanced persistent threat (APT) poses as a US-based reporter inquiring about a fabricated threat assessment, targeting an employee at your think tank. Let’s explore the details of the attack:
First, the threat actor builds out a payload containing the following files within it.
- Malicious LNK (shortcut) file that will execute the included malware if run
- Malware packaged as a side-loaded DLL
The malware is bundled into the following file and hosted on a remote web server.
- Annual_Threat_Assessment_of_the_US_Intelligence_Community.pdf.iso
Then, the threat actor crafts the following email to target a member of your think tank.
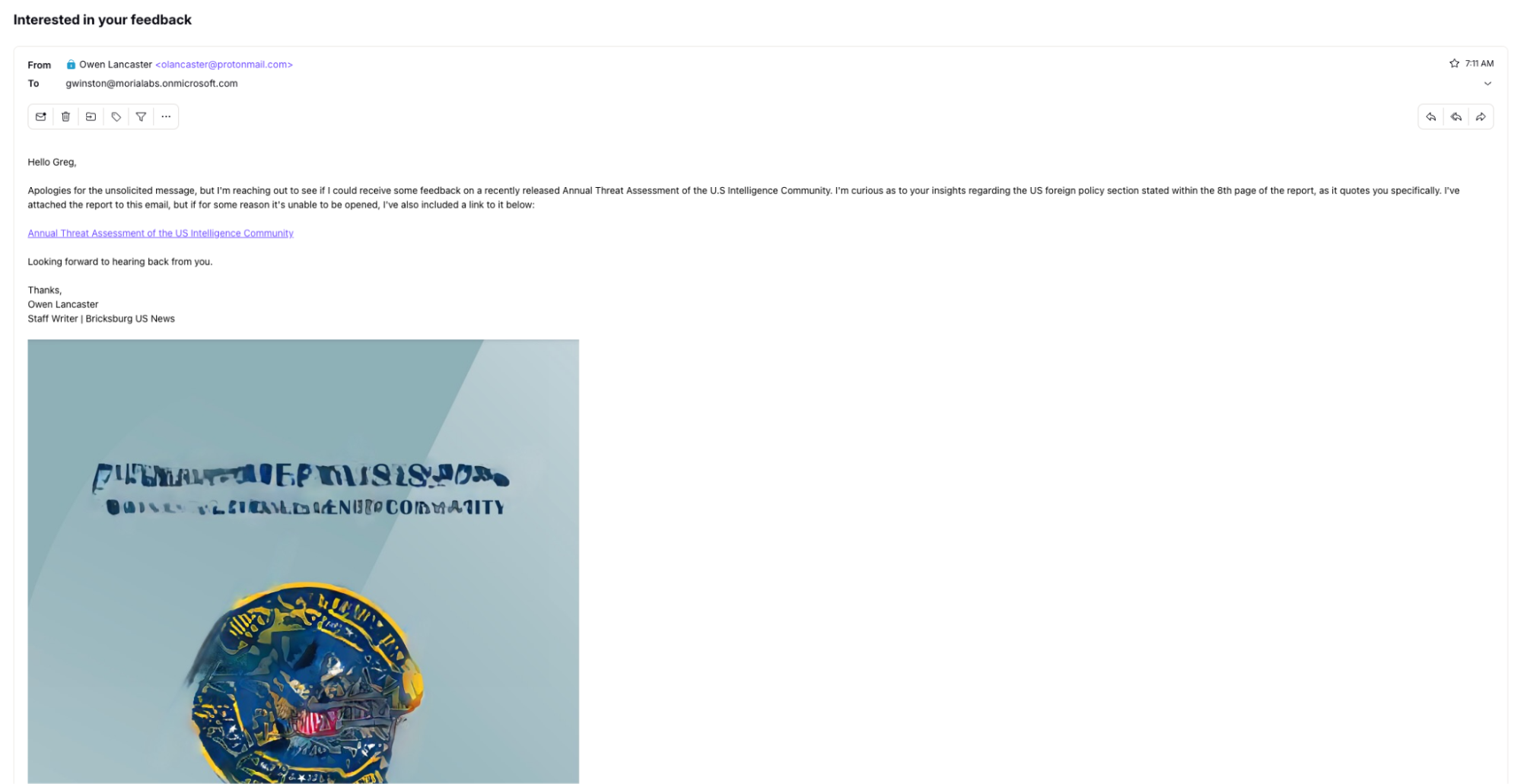
This email attempts to entice the victim into opening the included link, as the purported included document appears to be malformed. The embedded URL points to the following link.
- http://goijosijdfouhofejwoijfoijoixyz[.]xyz/files/64019238/Annual_Threat_Assessment_of_the_US_Intelligence_Community.pdf.iso
Upon receiving this email, the victim clicks the malicious link, launching a new Chrome browser.
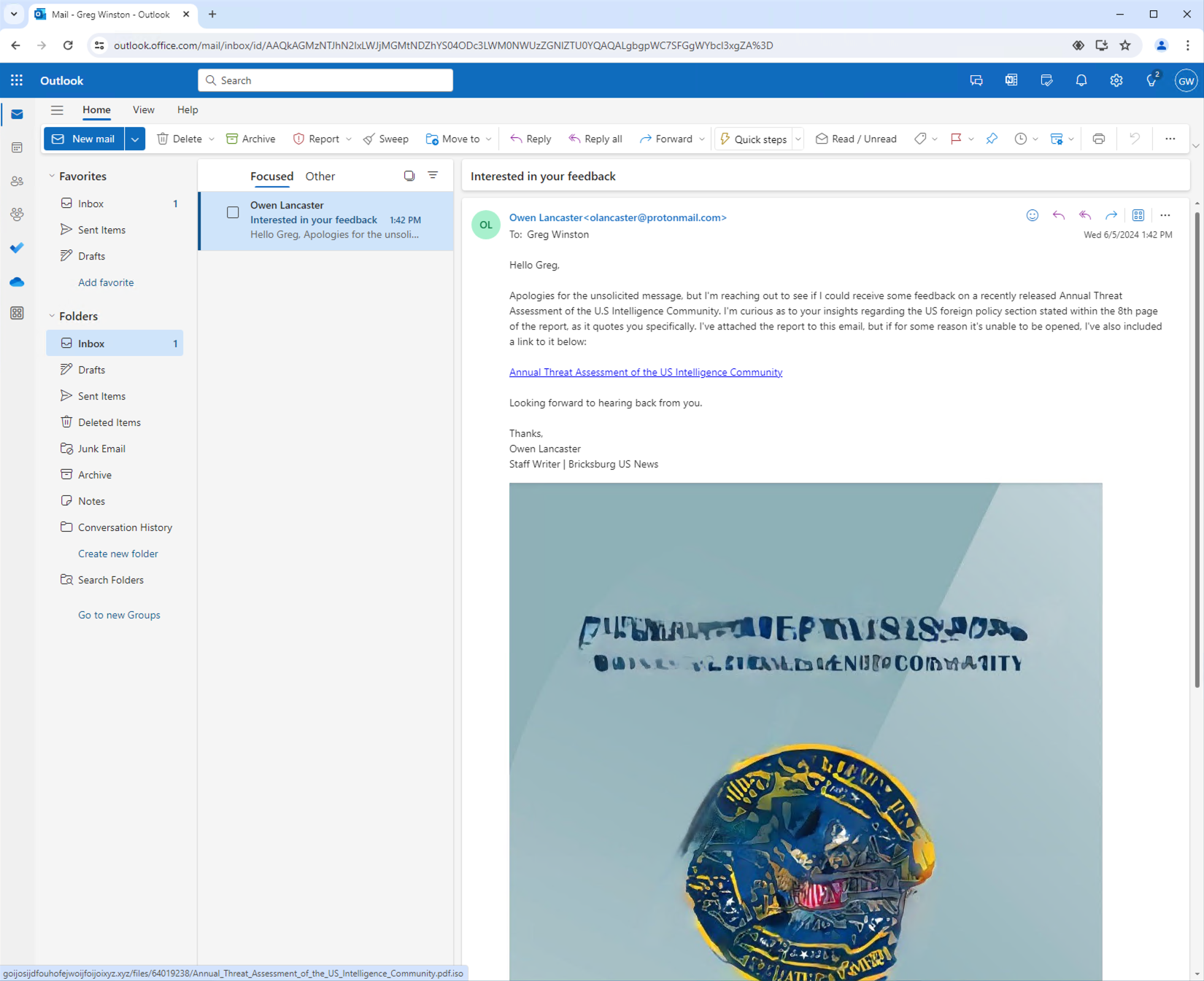
Detecting Malicious Activity
Behind the scenes, multiple third-party security products are monitoring the attack and generating detections. Your organization’s Abnormal Security platform examines the email message and flags it as suspicious.
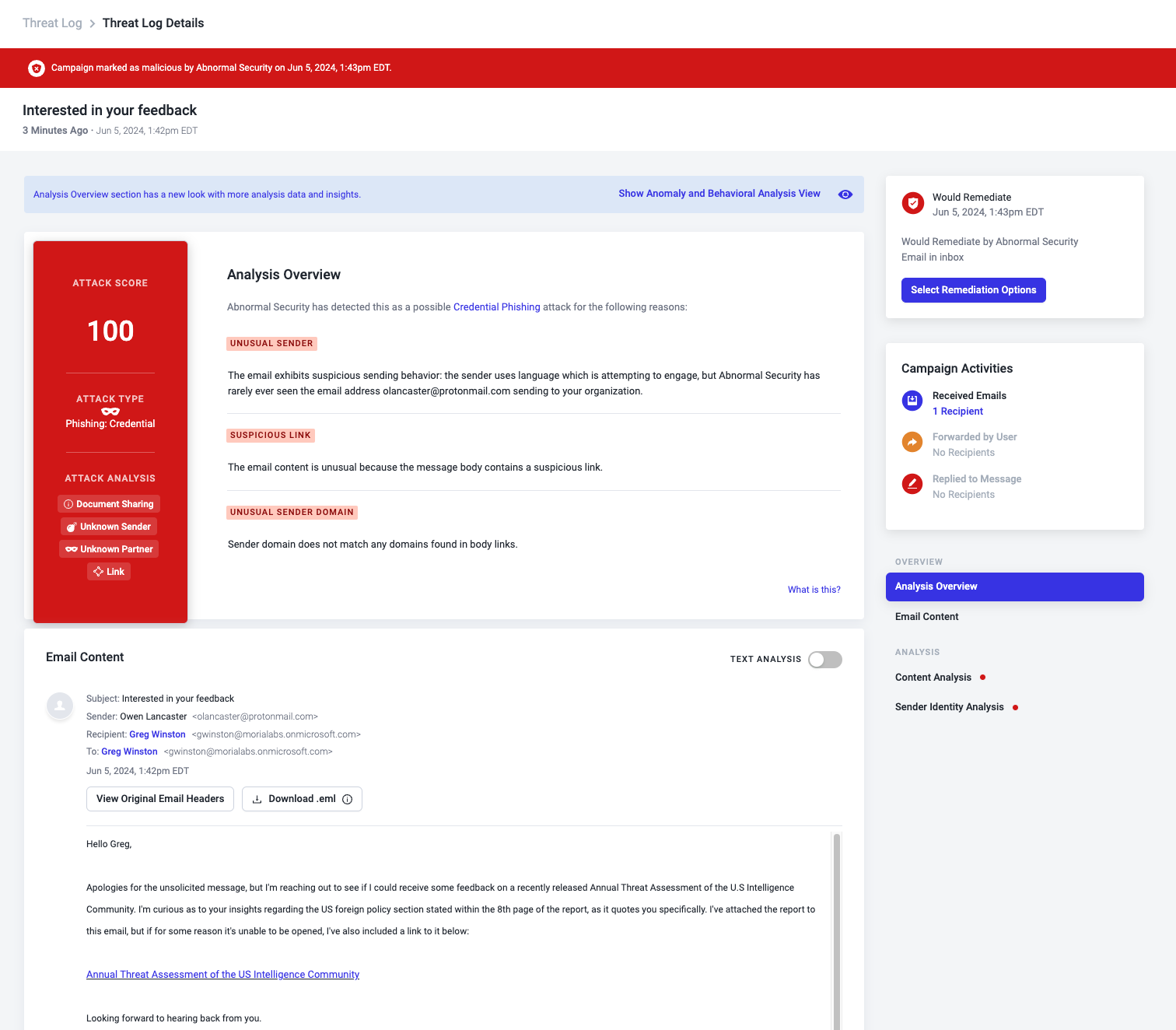
Using AI machine learning models, it identifies unique or otherwise notable strings within the email and flags them for your security analyst.
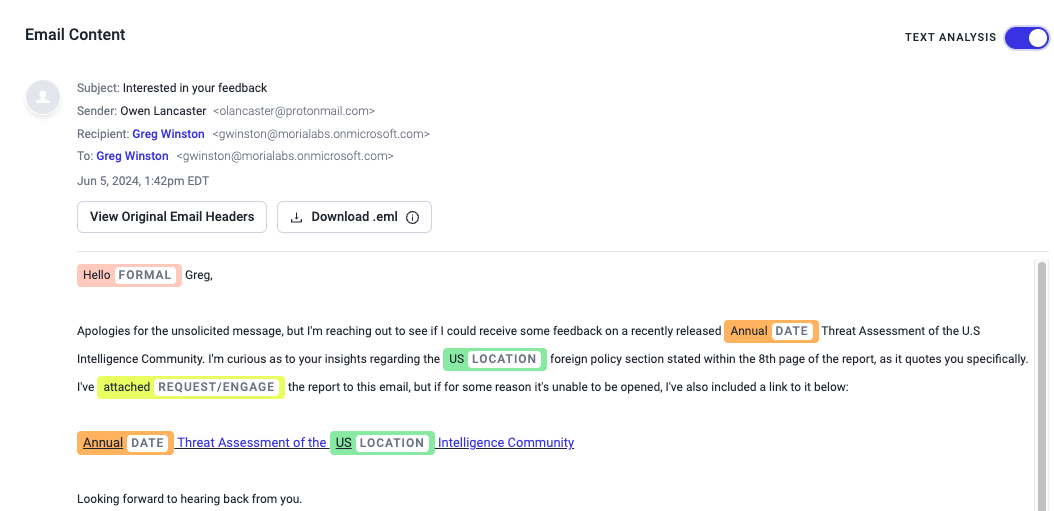
Once the email data is forwarded from Abnormal Security to CrowdStrike Falcon Next-Gen SIEM, you can view it in Advanced Event Search. This will be retained in the platform for 7 days with the 10GB/day plan, and can be stored for months or years with an optional Falcon Next-Gen SIEM subscription. Your security analysts can query the data using the intuitive and flexible CrowdStrike Query Language.
In addition to collecting email data, your team is ingesting Falcon telemetry from your endpoints. This telemetry provides visibility into DNS activity.
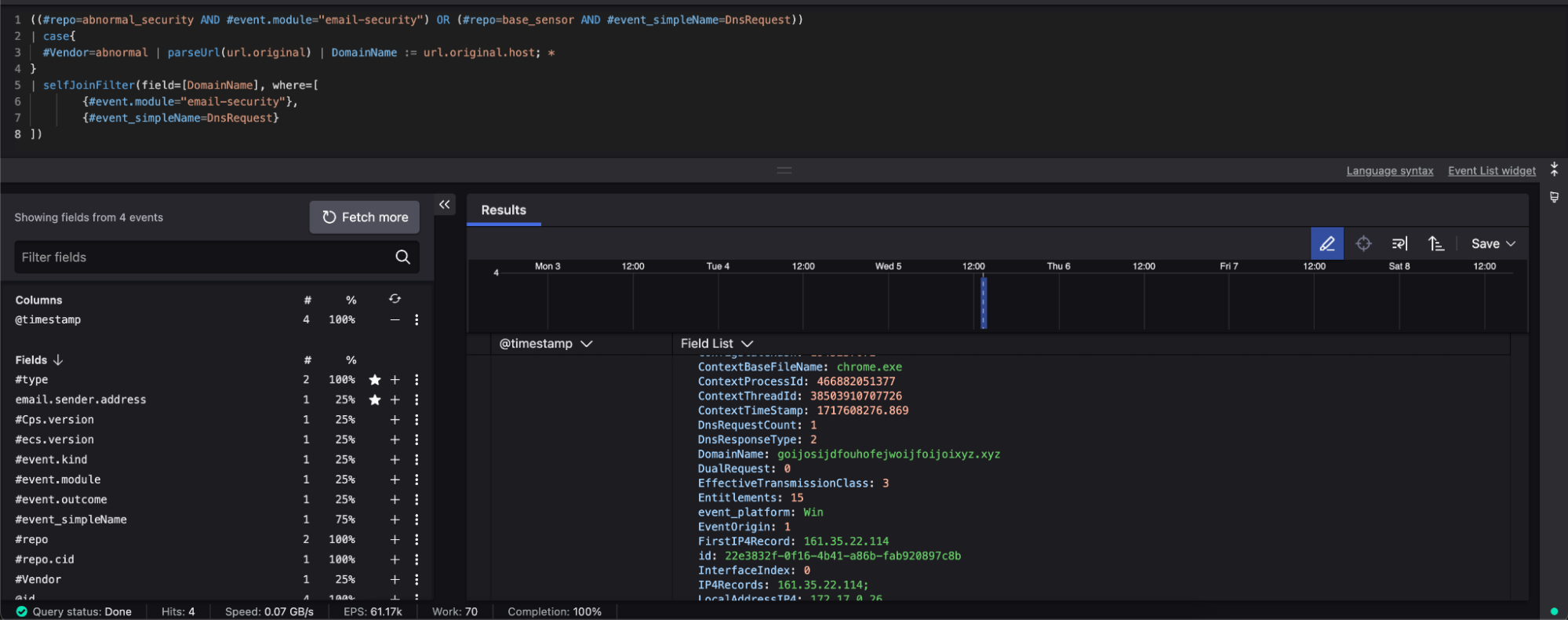
By combining these two datasets, you can identify instances where a domain from a flagged email has been accessed. Enrich your findings with CrowdStrike threat intelligence and known indicators of compromise. To detect future threats and generate high-fidelity alerts, create a new correlation rule indicating malicious activity.
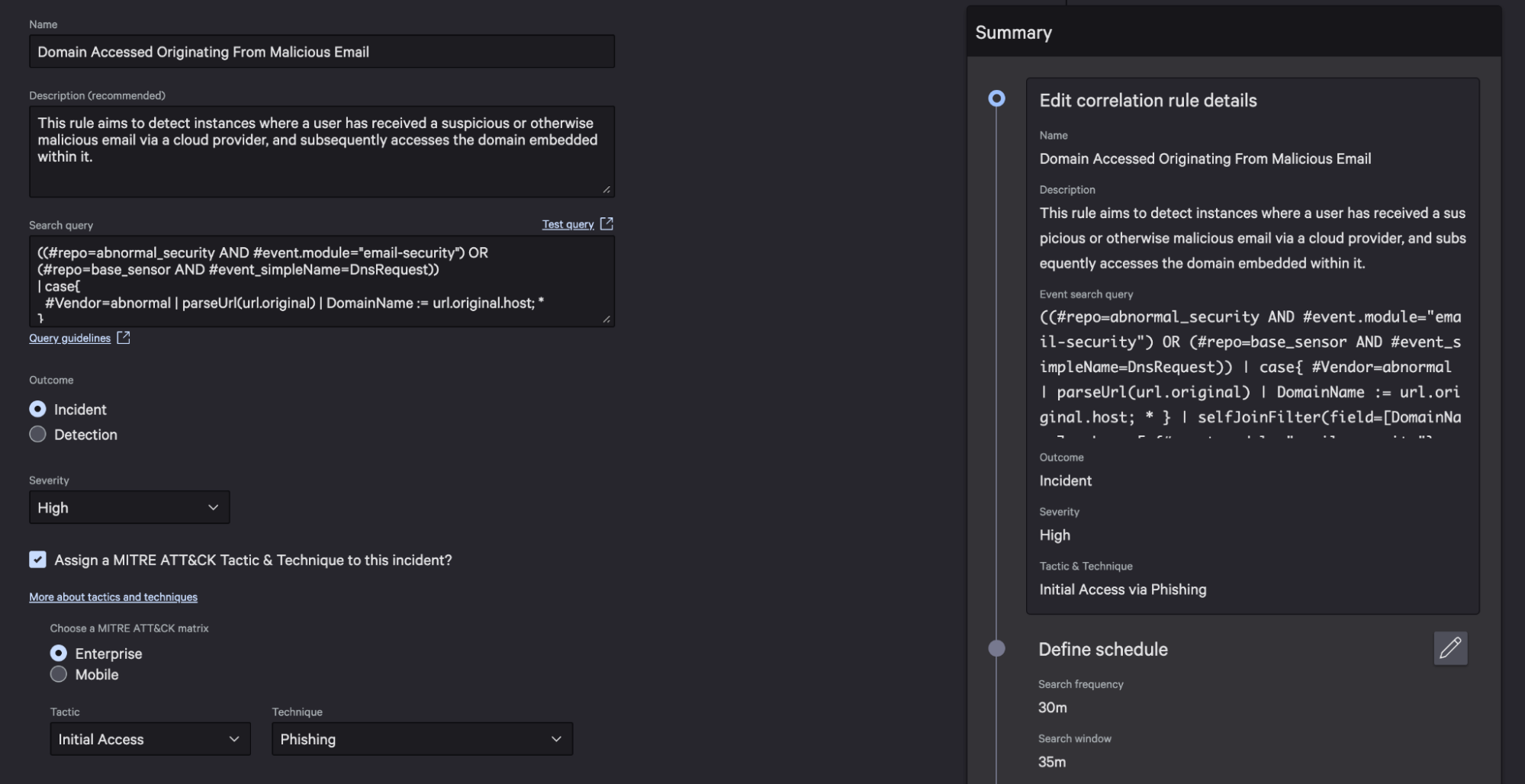
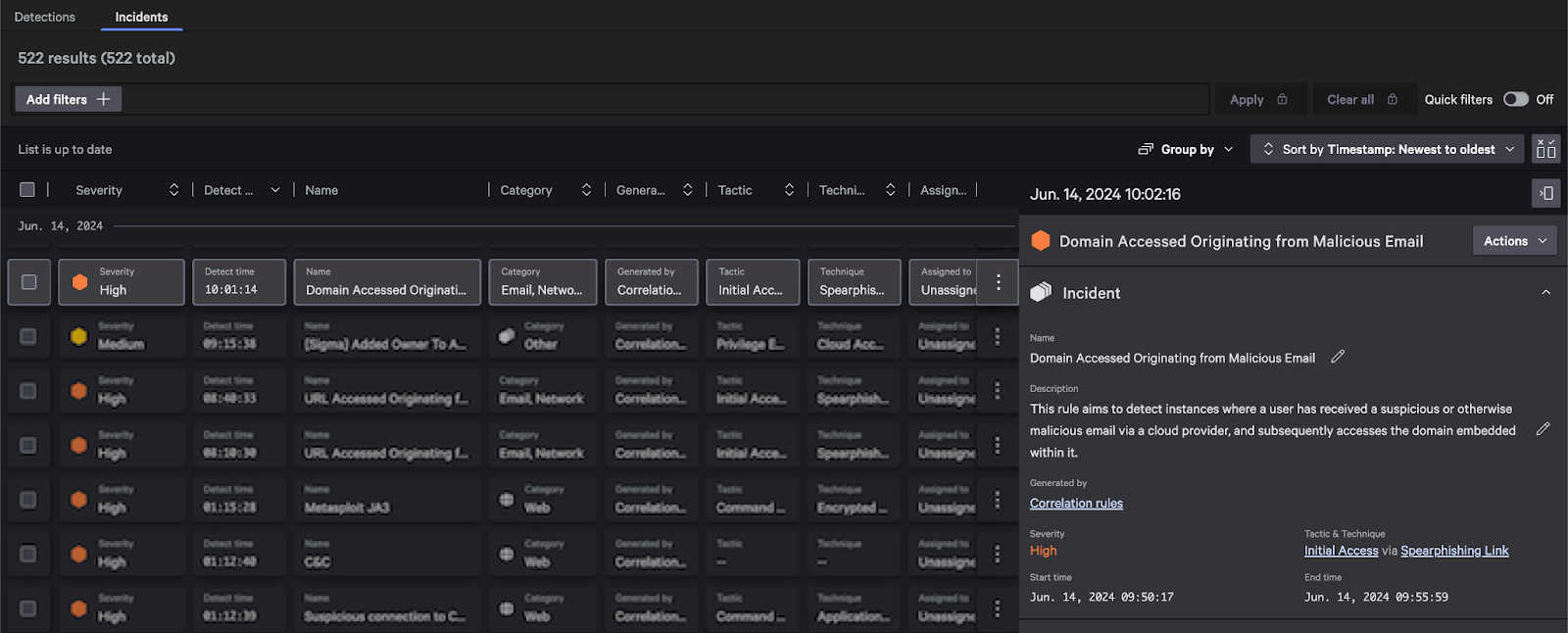
This correlation rule generates an alert when the victim attempts to access the domain included in the malicious email.
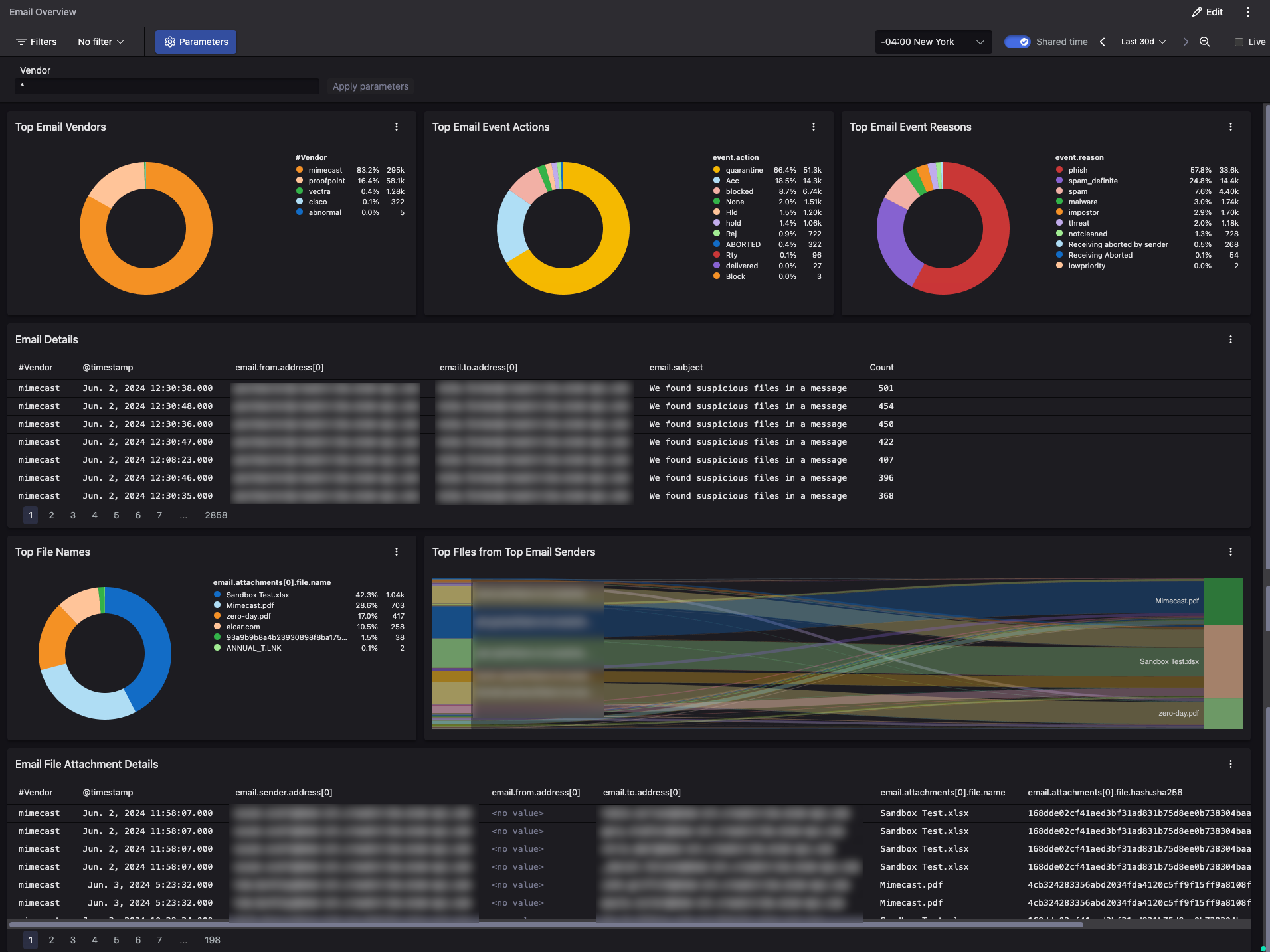
Data Visualization
You can visualize email data with custom and pre-built dashboards in Falcon Next-Gen SIEM. A versatile dashboard builder lets you select from a broad spectrum of visualization chart options and use advanced queries to create tailored dashboards.
Threat Investigation
The Incident Workbench visualizes the attack in a graph view, providing context about the entities involved. It lists key details such as users, senders, recipients, and host information.
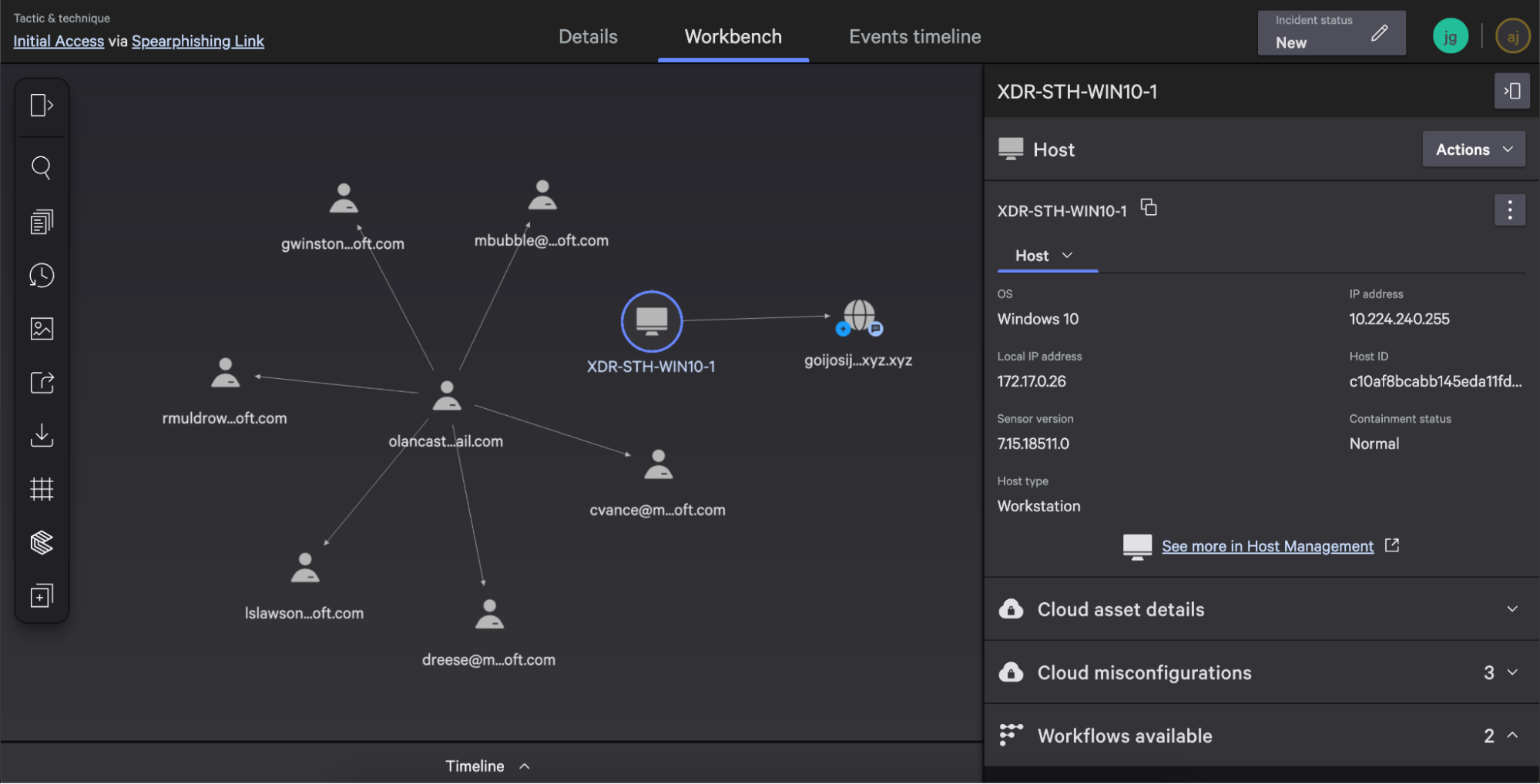
Your team can quickly understand relevant email information by viewing incident details.
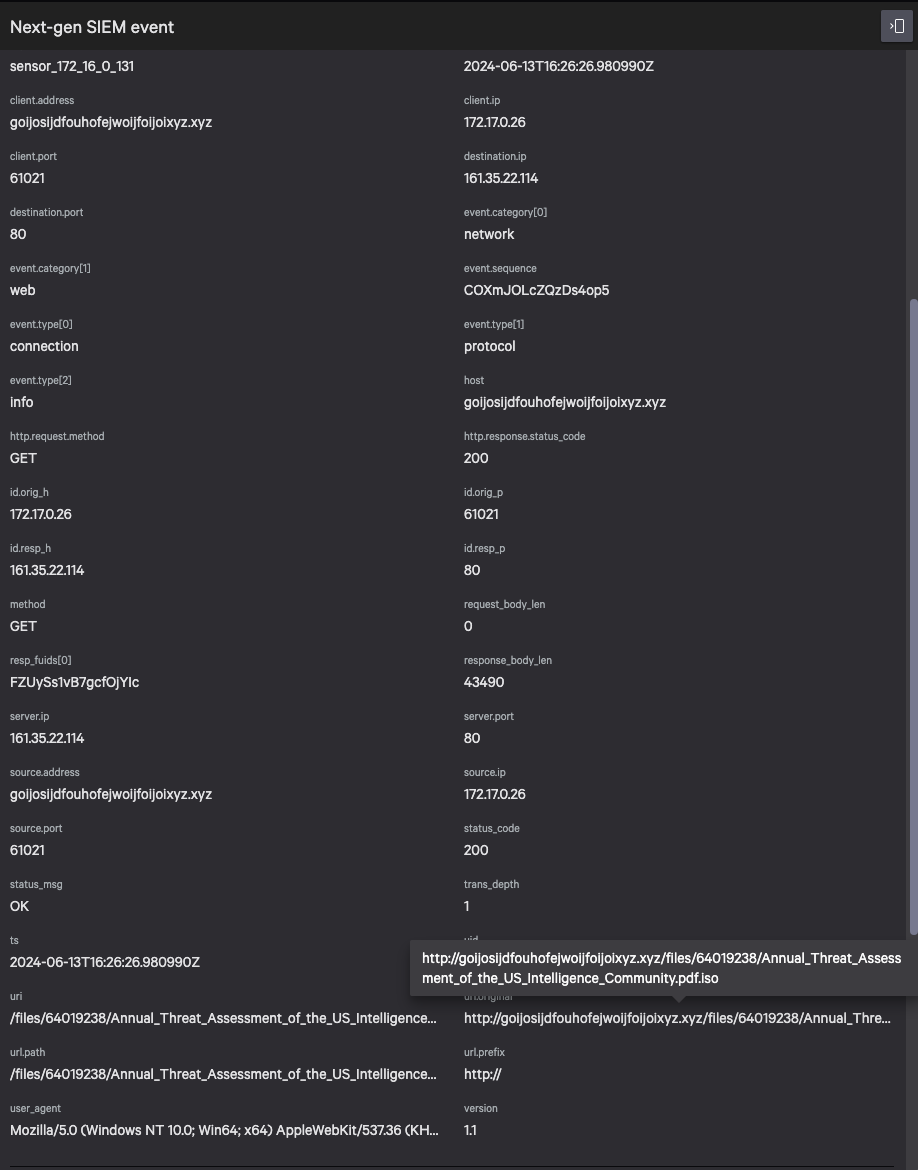
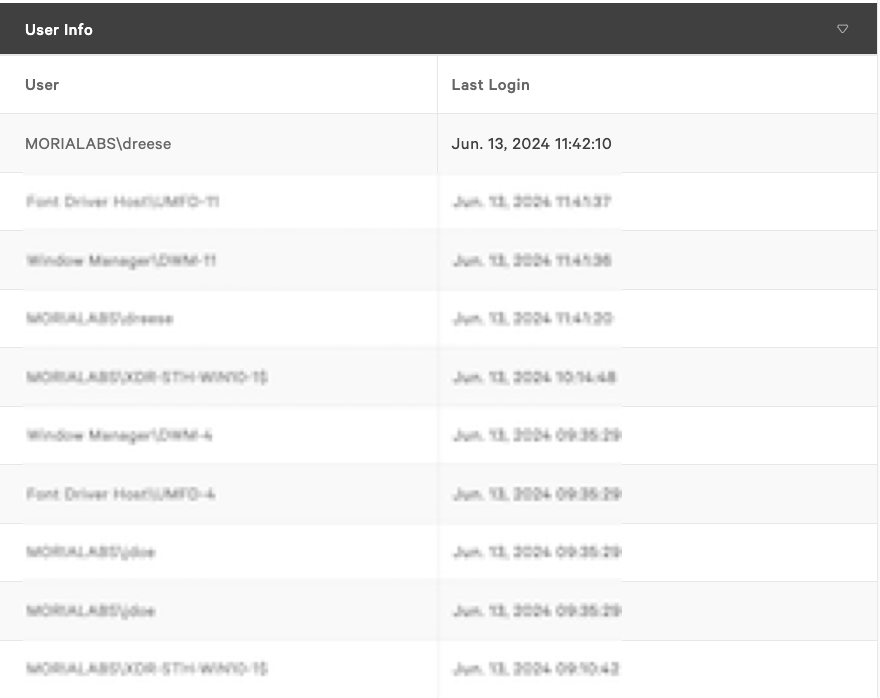
By pivoting on the host communicating with a remote server, you can identify the last logged-in user responsible for this network activity.
Incident Response
With Falcon Fusion SOAR, you can easily isolate the compromised host and prevent further malicious activity using workflow automation.
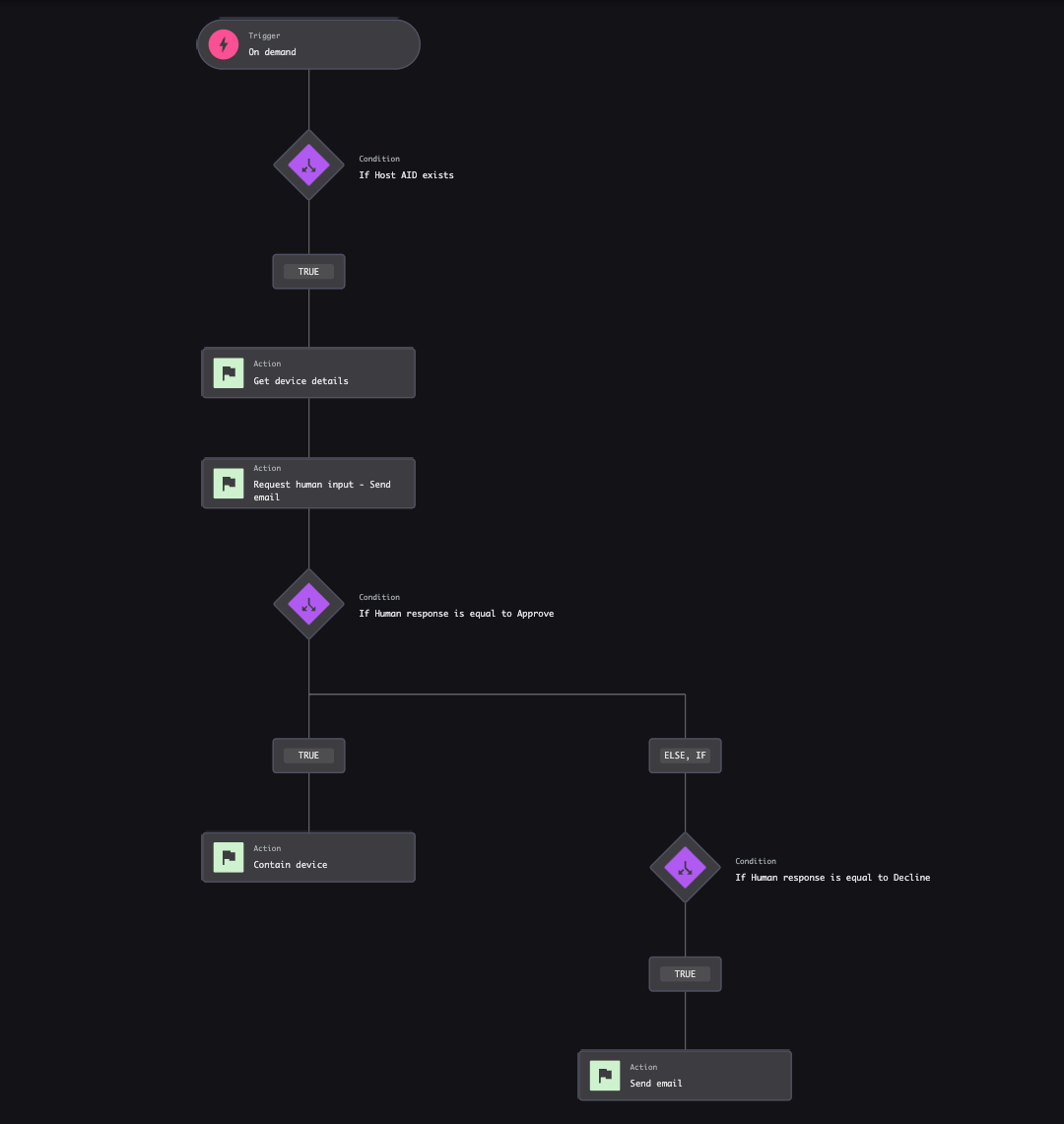
You can build a workflow by simply selecting the trigger, defining the conditions and configuring the actions. Falcon Fusion SOAR workflows can be triggered automatically based on a detection, on-demand when immediate response is necessary, or scheduled for routine tasks and assessments.
In this scenario, the workflow is triggered on-demand. If the “Host ID” condition is met, the workflow gathers the device details and sends an email to a senior engineer for review. If the senior engineer approves, the device will be contained. If not, the device remains uncontained, and an email documenting the actions is sent.
Additionally, Falcon Fusion SOAR offers numerous out-of-the-box phishing playbooks that can be customized to fit your organization’s requirements and technology stack.
In this scenario, multiple employees at your organization were targeted, and one reported the email as a “phishing email.” Your security team leveraged a new out-of-the-box phishing playbook template included in Falcon Fusion SOAR. Note that this playbook is not available with the 10GB/day plan; it requires the purchase of a Falcon Next-Gen SIEM subscription.
The phishing playbook template triggers upon receiving a phishing email notice from Microsoft 365. If the condition is met, the workflow writes to the log repository and initiates the investigation process. It enriches the data by searching all email components, submitting the URL for sandbox detonation, and conducting file hash lookups using VirusTotal.
If VirusTotal confirms malicious indicators, the workflow will call on the threat graph to kill the process. If the sender domain is suspicious, then the workflow has the capability to update third-party tools like Proofpoint. For risky URLs and IP addresses, the workflow will create custom IOCs to start a retroactive search.
Falcon Next-Gen SIEM offers unmatched efficiency in stopping phishing attacks by accurately detecting threats, visualizing high-risk activity in live dashboards, automating repetitive tasks, and streamlining investigations. With Falcon Next-Gen SIEM, threat detection and response has never been easier.
If you’re a Falcon Insight customer, you can extend the visibility and protection of the Falcon platform to third-party data with the 10GB/day plan. Discover how you can achieve up to 150x faster search performance and up to 80% lower cost than legacy SIEM solutions with Falcon Next-Gen SIEM. Speak to your CrowdStrike account representative to learn how you can modernize your SOC with the next generation of SIEM technology.
Additional resources:
- Check out technical documentation: See the Falcon Next-Gen SIEM User Guide, including information about third-party data ingestion.
- Start onboarding data today: Take the Next-Gen SIEM fundamentals course (CrowdStrike University subscription required) and watch these Next-Gen SIEM intro videos.
- Watch demo videos: Learn how to detect, investigate and stop threats with Falcon Next-Gen SIEM by viewing fast-paced demos.
- Reached your 10GB daily limit? Contact us to upgrade your subscription and experience Falcon Next-Gen SIEM without constraints.