Leveraging Identity Data to Stop Attacks with Falcon Next-Gen SIEM

As adversaries increasingly use stolen credentials and identity-based techniques to launch crippling attacks, CrowdStrike has developed a comprehensive approach to detect and stop these threats. CrowdStrike Falcon® Identity Protection offers the industry’s first unified platform for identity protection and endpoint security, proactively stopping hybrid identity-based threats across Entra ID, Okta, Active Directory, and other identity providers.
Now, CrowdStrike Falcon® Next-Gen SIEM enables customers to get even more value out of the Falcon platform by ingesting third-party identity data and strengthening their defenses against identity-based attacks.
Falcon Next-Gen SIEM empowers teams to detect, investigate, and respond to identity-based attacks while meeting compliance requirements. By analyzing identity data, SOC analysts can identify authentication methods, login attempts, user activity patterns, and anomalous behavior. It swiftly detects compromised accounts, unauthorized access attempts, and insider threats by correlating identity data with other logs. When deployed with Falcon Identity Protection, Falcon Next-Gen SIEM delivers comprehensive, real-time threat detection and prevention.

This blog post shows how easy it is to ingest identity data with Falcon Next-Gen SIEM and offers step-by-step instructions to defeat identity-based threats.
Maximize Your 10GB/Day Plan by Onboarding Identity Data
Falcon Next-Gen SIEM transforms security operations to stop breaches by bringing together data, AI, workflow automation, and threat intelligence on one platform with one console and one lightweight endpoint agent.
To accelerate SOC transformation, Falcon Insight customers can ingest up to 10 gigabytes of third-party data per day at no additional cost, and experience the power and performance of Falcon Next-Gen SIEM. The 10GB/day offering is available today to the first wave of Falcon Insight customers and it will be released in waves to remaining customers over the next several weeks.
Make the most of your 10GB/day plan by ingesting high-value data, such as identity logs, into the Falcon platform to stop identity based threats. You can onboard identity data using a number of out-of-the-box integrations with identity solutions which include Okta, ForgeRock, Ping and Microsoft Event Hubs. Next-Gen SIEM offers an expanding array of data connectors which support a broad set of log sources, while an HTTP event collector (HEC) allows ingest of any type of data using prebuilt or custom parsers.
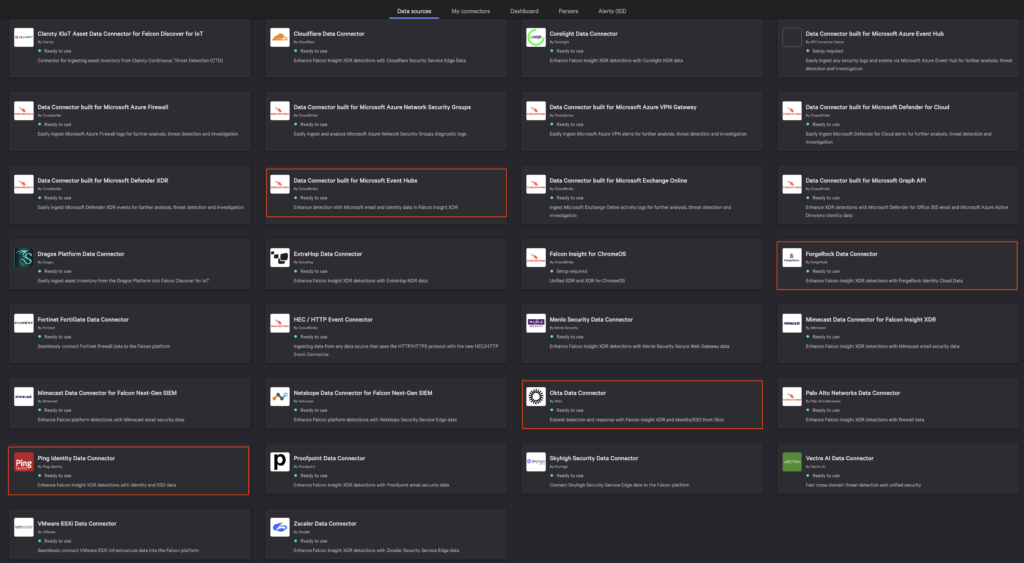
For this blog we will focus on the Okta data connector, data ingestion can be set up in just minutes. Start by generating an API token in the Okta console; see the Falcon Next-Gen SIEM documentation for step-by-step instructions.
Next, create a new connector in the Falcon console by navigating to Next-Gen SIEM > Log management > Data onboarding and select the Okta Data Connector.
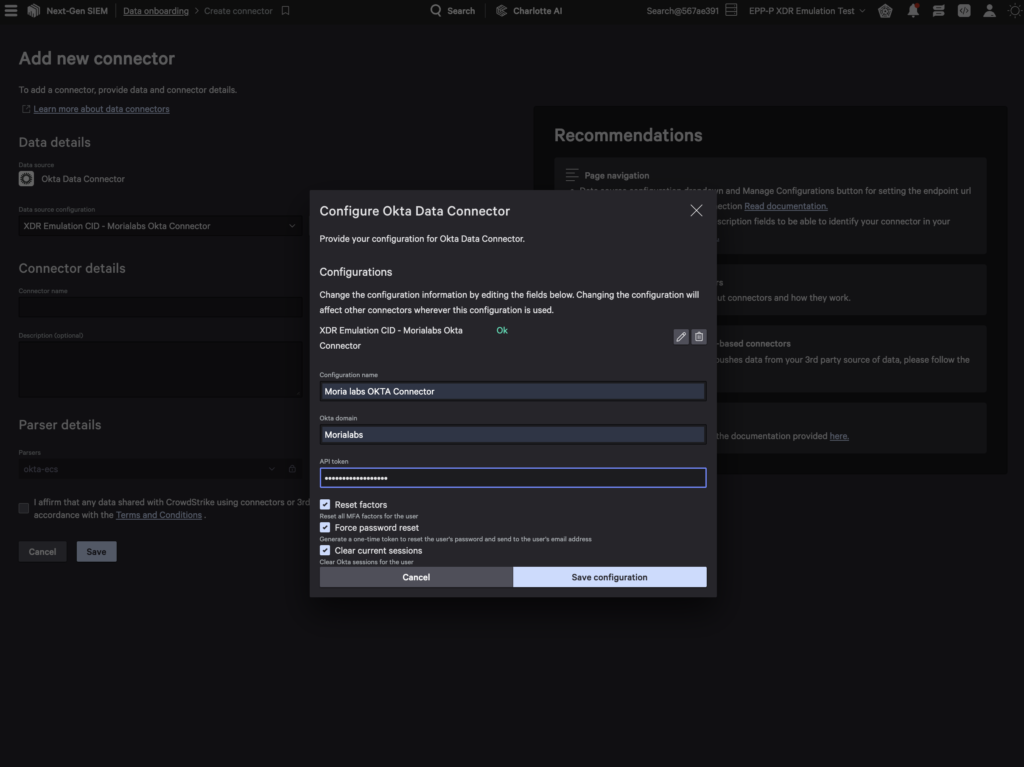
Enter the generated API key, and Falcon Next-Gen SIEM will automatically connect to Okta and start ingesting data. Check out Falcon Next-Gen SIEM technical documentation for more detailed information on how to onboard data.
Defeating an Identity Attack with Falcon Next-Gen SIEM
To illustrate how Falcon Next-Gen SIEM helps combat Identity-based threats using Okta logs, let’s consider a scenario where an advanced adversary targets your organization with the intent of gaining access to as much data as possible. They have successfully gained access to a previously dormant service account with administrative privileges through a purchase made on the underground web. This account leverages multi-factor authentication, and in turn requires the user that is tied to this account to verify any authentication attempts through a secondary device, such as a mobile phone.
The threat actor begins by making multiple attempts at logging in to the following user account:
- us_service_a_vpn@morialabs.com
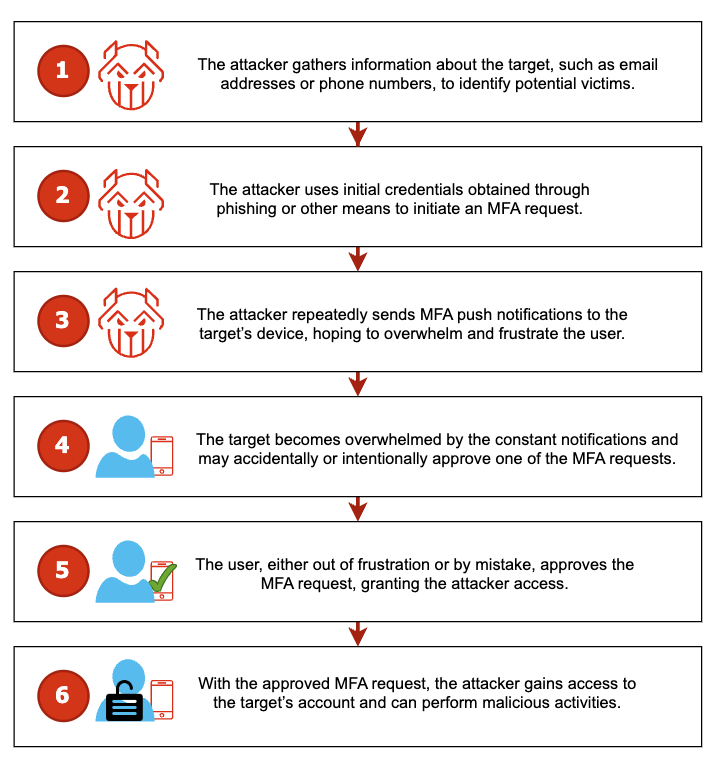
In total, 10 login attempts in quick succession were observed, with failed outcomes in all instances. Eventually, however, the victim grew tired of seeing the notifications and decided to accept the incoming request in order to prevent being distracted/annoyed by these requests. In doing so, it led to a successful login by the threat actor to the targeted account.
This successful login was made through a
The notion of sending numerous attempted MFA requests to an end user, with the intent of having them ultimately accepted out of convenience is an attack vector known as MFA fatigue. More information about MFA fatigue may be viewed here.
MFA Fatigue Attack
After successfully logging in, the user quickly accesses the administration portal through the same known proxy. After accessing the administrator portal, the threat actor proceeds to create the following new user:
- Owen Lancaster (olancaster@protonmail.com)
Finally, the threat actor grants this new user with administrative privileges, allowing the threat actor to gain further access into the compromised environment in order to steal intellectual property.
Detecting Malicious Activity
Okta Multiple Failed Authentication Attempts
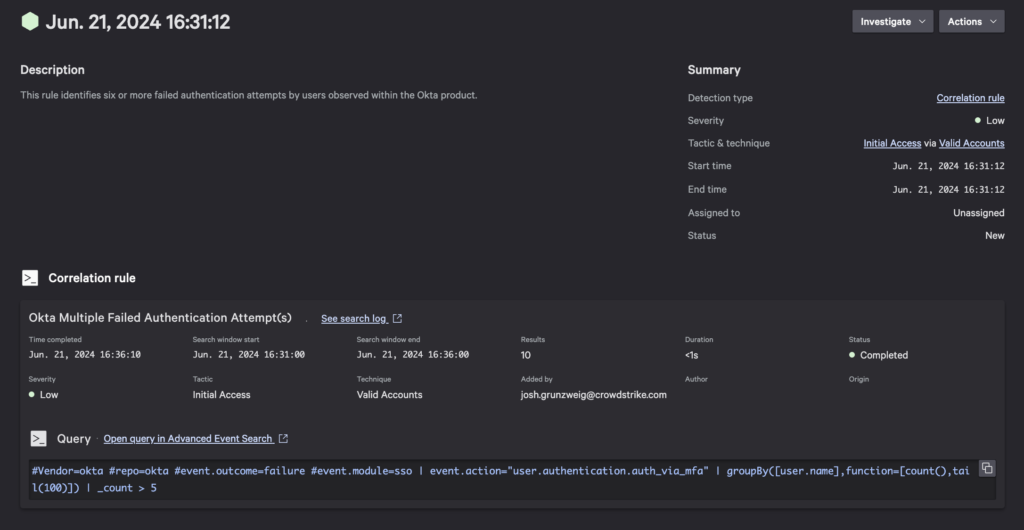
Upon making the numerous unsuccessful attempts, a custom correlation rule looking for more than 5 failed login attempts is triggered.
Okta Successful Authentication Attempt(s)
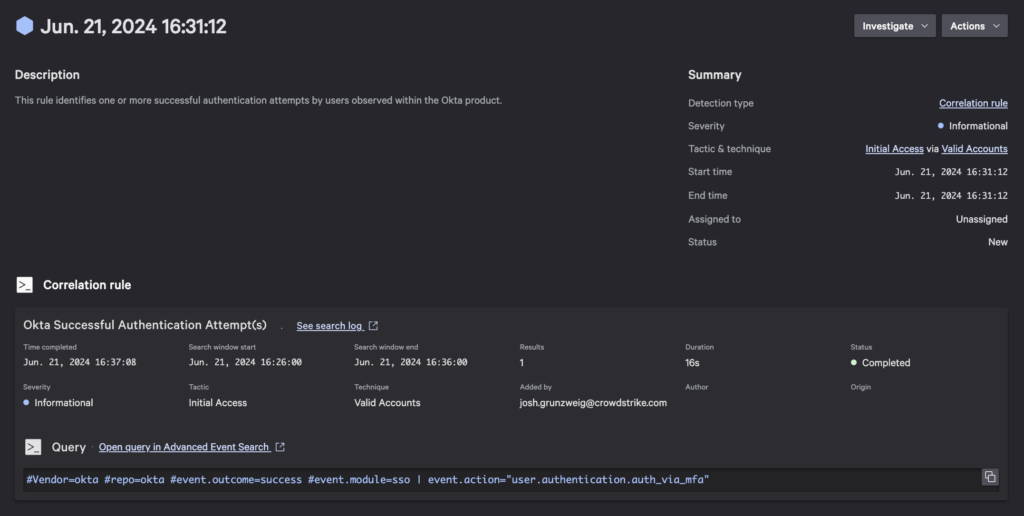
An informational alert, as nothing malicious is ultimately taking place, this correlation rule highlights instances when any user successfully logs into the Okta portal.
Okta Successful Authentication Attempt Via Proxy
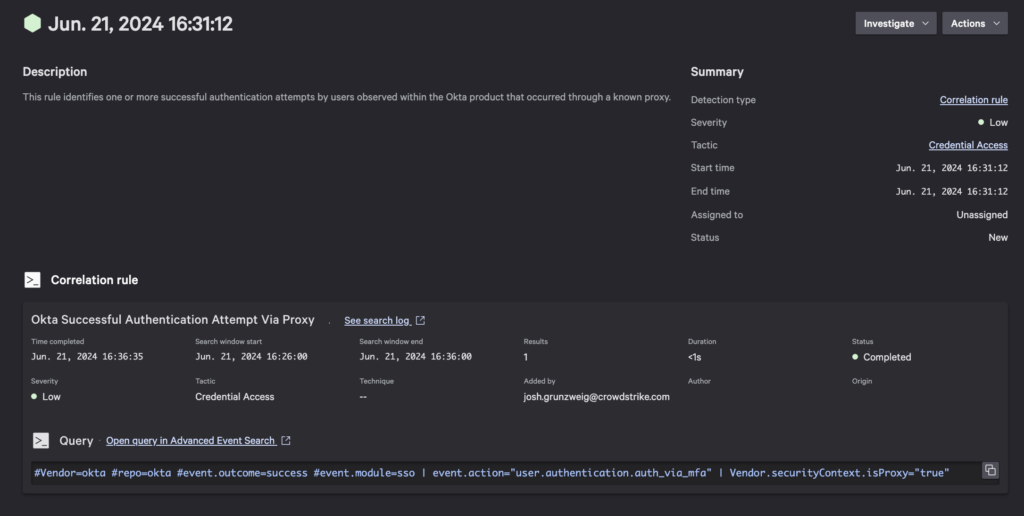
This correlation rule seeks out instances when a user logs into Okta via a known proxy, and may provide evidence that malicious activity may be taking place.
Okta Administrator Portal Accessed Via Proxy
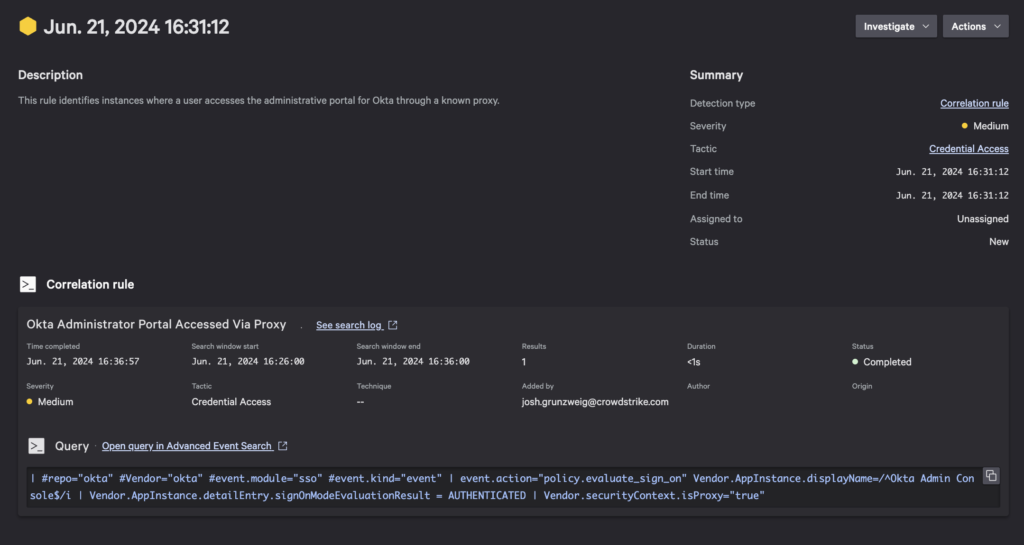
This rule aims to perform similar checks as the previous correlation rule, but specifically seeks out instances where individuals are accessing the Administrator portal via a known proxy.
New Okta User Created
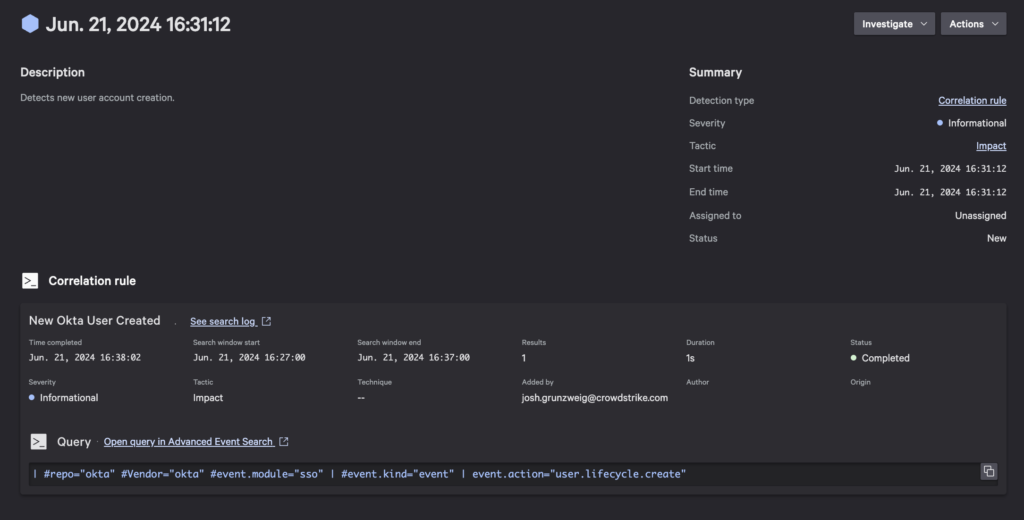
An informational alert, as nothing malicious is ultimately taking place, this correlation rule highlights instances when any new user is successfully created within Okta.
Okta Admin Role Assigned to an User or Group
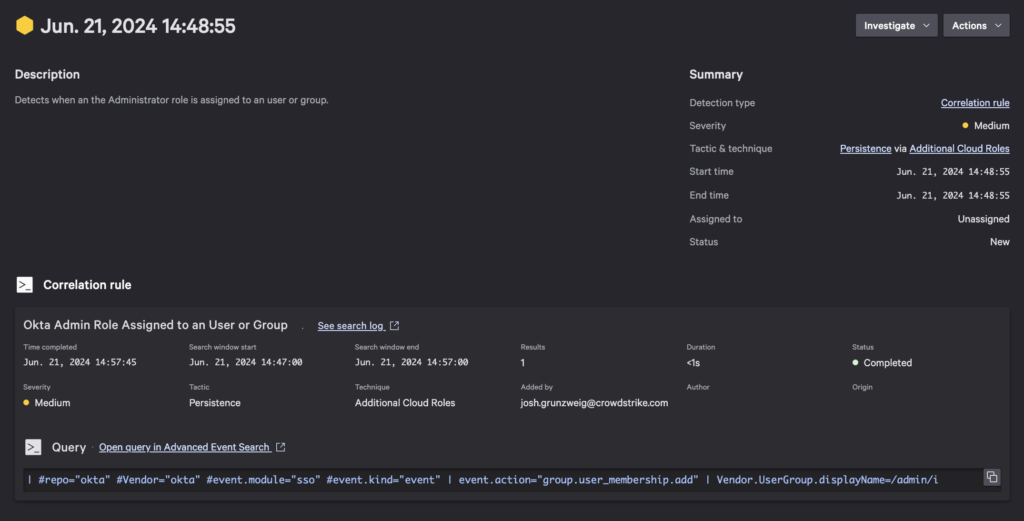
Certainly suspicious, this rule aims to identify when a user is assigned administrative privileges within Okta.
Combining Defenses
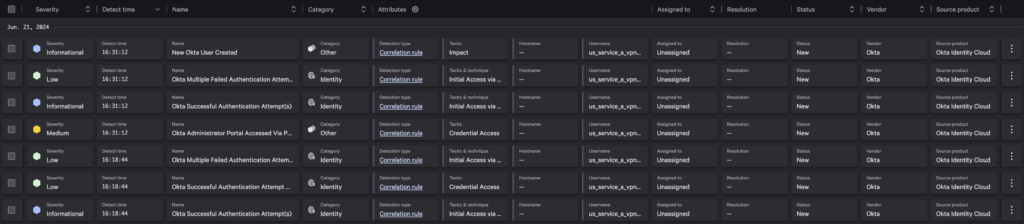
By aggregating all of these disparate detections together, we can easily understand that they are related based on the user that is being impacted. As a result, we can select all of these detections and build out a new Incident from them.
Incident Response
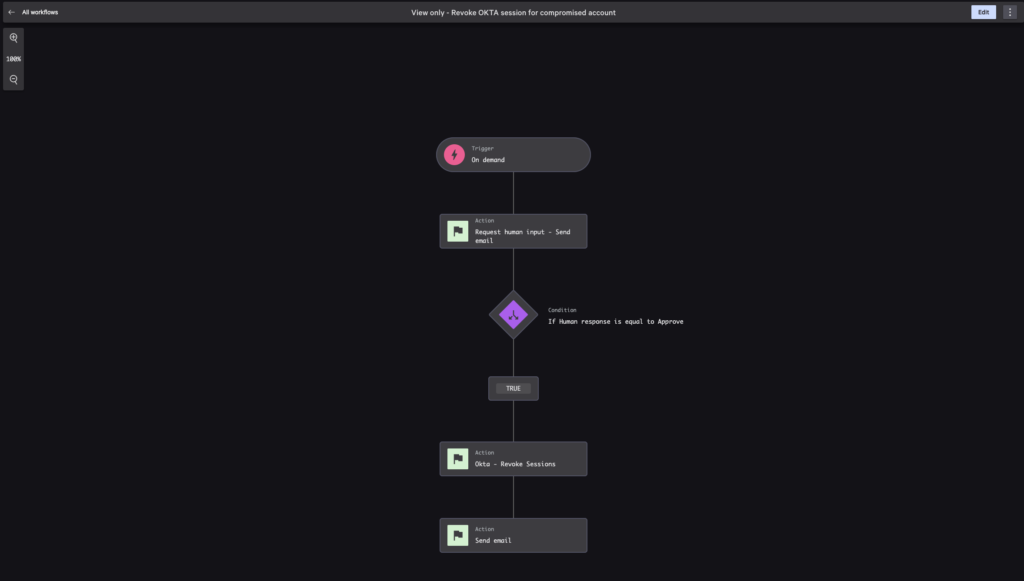
With Falcon Fusion SOAR, we can easily isolate the compromised account and prevent further malicious activity using workflow automation.
Fusion SOAR allows response at machine speed, upgrade to a paid Falcon Next-Gen SIEM subscription and leverage automated workflows and apply policies that remediate the most common identity-based attacks, such as clearing session tokens in the event that a user’s session has been compromised. With Okta, we can also execute a playbook to automatically revoke access, reset MFA factors and force a password reset — a process that could take dozens of hours per week of analyst time if performed manually.
We can build a workflow by simply selecting the trigger, defining the conditions and configuring the actions. Falcon Fusion SOAR workflows can be triggered automatically based on a detection, on-demand when immediate response is necessary, or scheduled for routine tasks and assessments.
In this scenario, the workflow is triggered on-demand. If the identified account has been compromised, the workflow gathers the user details and sends an email to a senior engineer for review. If the senior engineer approves, the Okta session will be reset and a password reset will be requested. If not, the Okta user session remains active, and an email detailing the actions taken is sent.
Additionally, Falcon Fusion SOAR offers numerous out-of-the-box playbooks that can be customized to fit your organization’s requirements and technology stack.
Falcon Next-Gen SIEM offers unmatched efficiency in stopping attacks relating to identities by accurately detecting threats, visualizing high-risk activity in live dashboards, automating repetitive tasks, and streamlining investigations. With Falcon Next-Gen SIEM, threat detection and response has never been easier.
If you’re a Falcon Insight customer, you can extend the visibility and protection of the Falcon platform to third-party data with the 10GB/day plan. Discover how you can achieve up to 150x faster search performance and up to 80% lower cost than legacy SIEM solutions with Falcon Next-Gen SIEM. Speak to your CrowdStrike account representative to learn how you can modernize your SOC with the next generation of SIEM technology.
Additional resources:
- Check out technical documentation: See the Falcon Next-Gen SIEM User Guide, including information about third-party data ingestion.
- Start onboarding data today: Take the Next-Gen SIEM fundamentals course (CrowdStrike University subscription required) and watch these Next-Gen SIEM intro videos.
- Watch demo videos: Learn how to detect, investigate and stop threats with Falcon Next-Gen SIEM by viewing fast-paced demos.
- Reached your 10GB daily limit? Contact us to upgrade your subscription and experience Falcon Next-Gen SIEM without constraints.