How to Manage USB Devices

The greatest minds in cybersecurity are at Fal.Con in Las Vegas, Sept. 18-21.
Register now to build skills at hands-on workshops and learn from skilled threat hunters.
Introduction
This document will outline how to use Falcon Device Control to create and enforce USB device policy in your environment to minimize the attack surface and risk of incidents.
Video
This video provides a demonstration of the Falcon Device Control configuration as well as the USB device visibility available with Falcon Insight dashboards. Falcon Prevent customers can also access similar visibility options via the Activity app.
Device Control Policy Options
Falcon Device Control enables customers to use their existing management platform and lightweight agent to establish and enforce policies for USB devices on both Mac and Windows devices. The policies and options can be in the Endpoint Security section under USB device control.
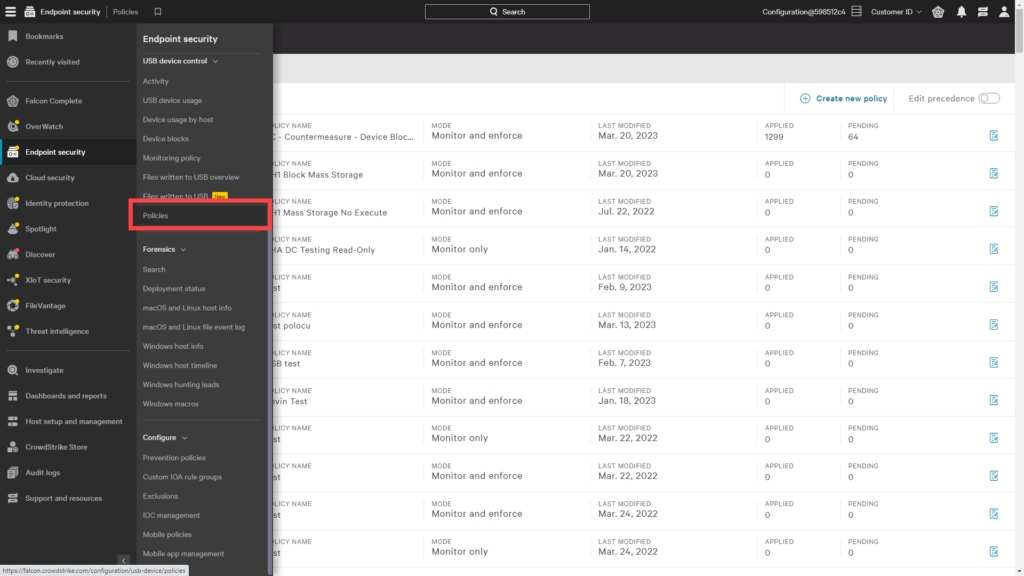
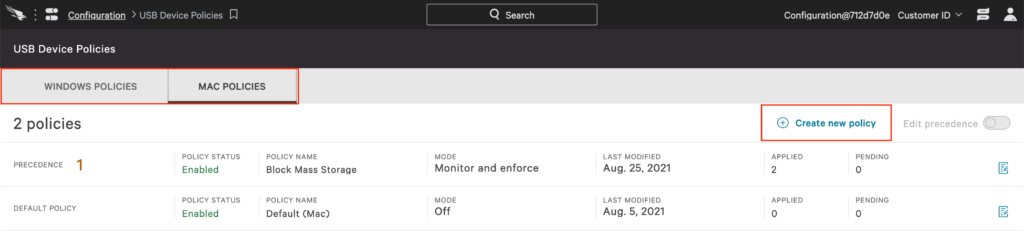
From the policy list, you can choose to create a Windows or Mac policy, to edit an existing policy, or create a new policy. I’ll follow the path of creating a new policy.
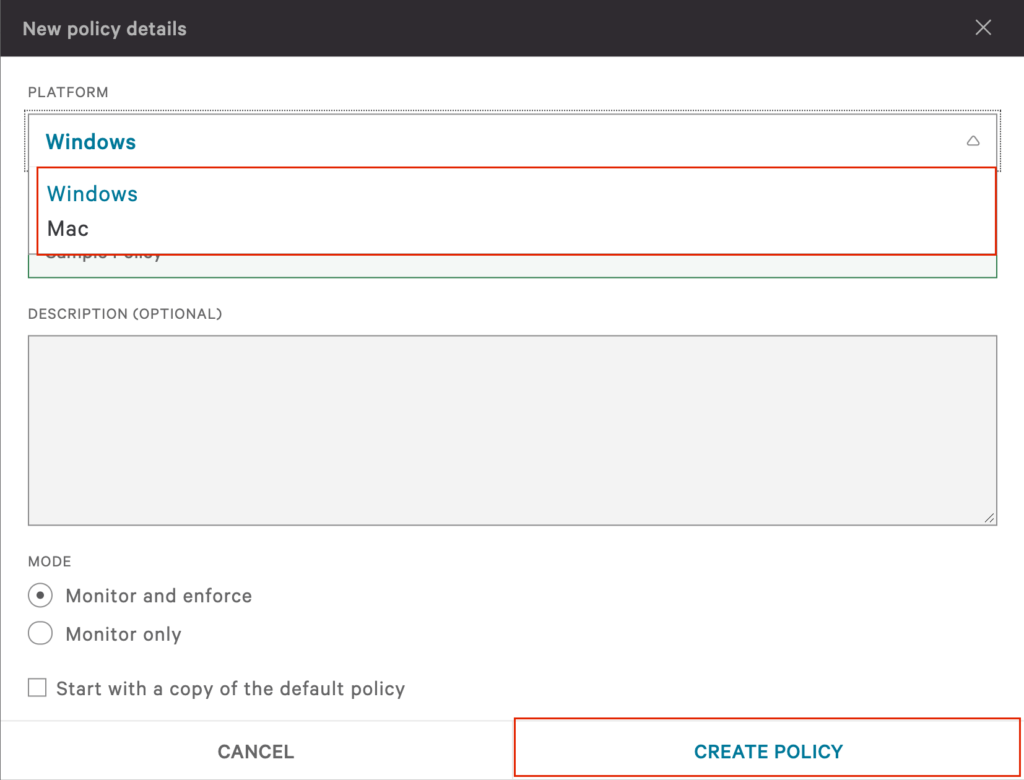
Within each policy, you are presented with a list of different USB device classes. This gives you the granularity to define different policies for different types of devices. Device classes include imaging, printers and mass storage. For mass storage, you will see four options available. “Read, write and execute” gives users full access. For mass storage, “Read and write only” is often used to prevent the auto-execution of unwanted programs.
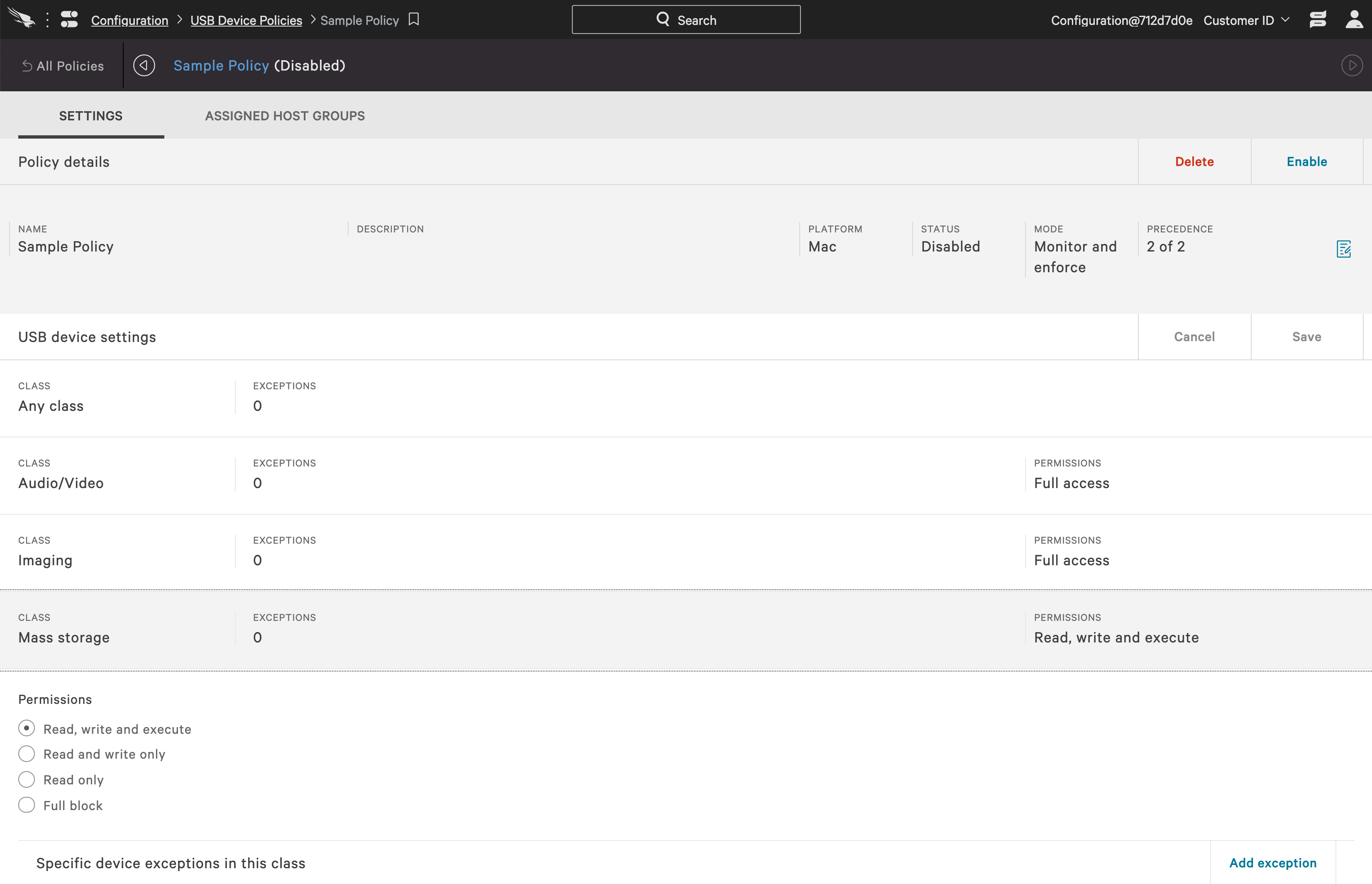
Within the policy for each class, you also have the option to define exceptions. These exceptions can be done for specific devices or in larger groups using vendor and product information. This allows you to provide necessary functionality while maintaining control over user access. It is also very helpful when enforcing specific corporate standards.
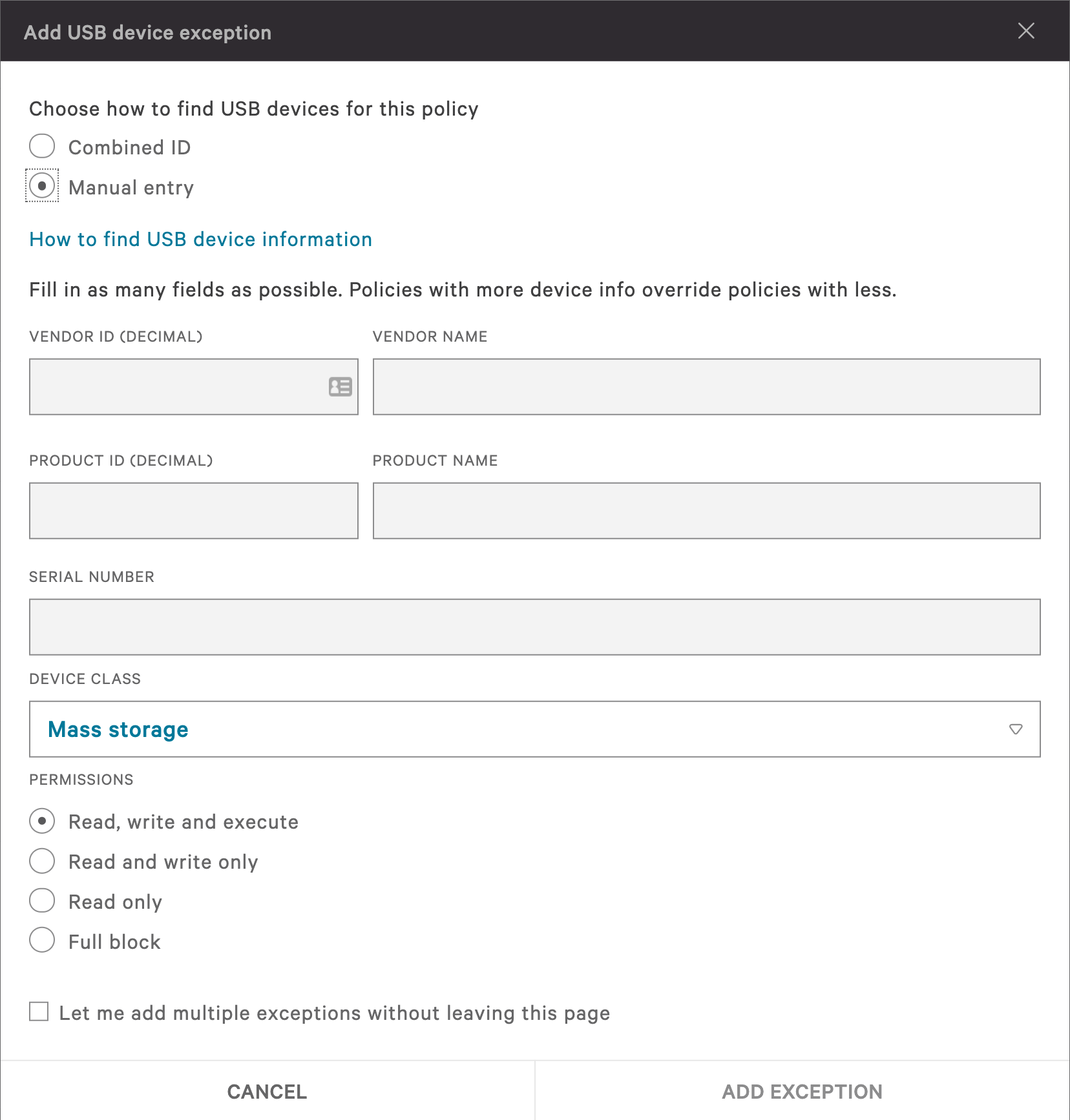
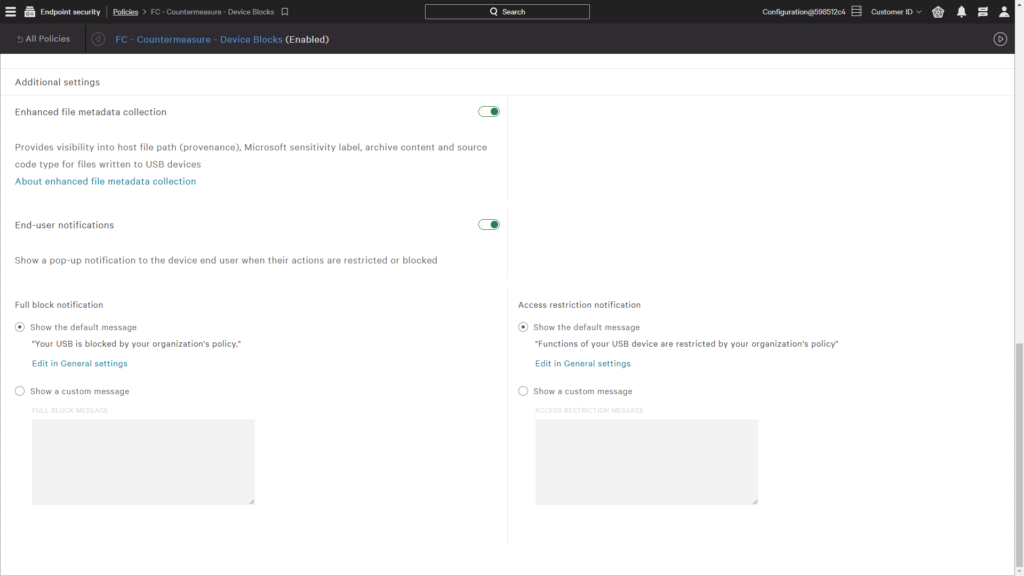
For Windows policies, CrowdStrike USB Device Control is able to provide enhanced file metadata collection. This allows the Falcon Agent to leverage machine learning to classify source code written to a USB device, provide the provenance of a file, identify data sensitivity labels, and view the contents of archived files.
This visibility enables you to investigate potential data exfiltration events.
After a policy is created assign that policy to a group for simpler management and automatic assignment. For CrowdStrike customers check out the full details in the USB Device Policy guide in the console.
Conclusion
Falcon Device Control provides the ability to establish, enforce and monitor policies around your organization’s usage of USB devices.


