Hybrid working models have increasingly become the normal way of doing business. Employees are working from anywhere, users and their devices are moving on and off the office network, and many applications once hosted in data centers are now moving to public clouds or being replaced with software as a service (SaaS).
With the erosion of the corporate network perimeter and increased employee access to sensitive information from remote locations, corporate endpoints are left out in the wild and are often difficult to monitor for suspicious activity. Organizations need to protect the user-to-application connectivity from end to end, regardless of where users are connecting from. If an incident occurs, security teams need maximum context and minimal complexity to understand the full extent of a threat and be able to react rapidly with surgical precision from anywhere in the world.
To fend off and respond to today’s most advanced threats, CrowdStrike and Zscaler together are delivering more efficient and more effective outcomes for security teams by providing an integrated end-to-end security solution — from endpoint to application — in a way that gives analysts a real-time view of a device’s security posture and provides access to critical applications via flexible policies.
Zscaler is a key partner in the CrowdXDR Alliance, jointly delivering on extended detection and response (XDR) use cases that require robust visibility and response capabilities beyond the endpoint and across all key security domains in today’s enterprises. Zscaler’s partnership and purpose-built XDR integration with CrowdStrike represent a seamless, first-of-its-kind workflow between the two solutions.
Joint Zscaler and CrowdStrike customers now have unparalleled, extended endpoint and network visibility across their entire enterprise to more effectively correlate diverse sets of data sources. This critical correlation cuts down the time needed to detect suspicious behavior and conduct the necessary investigations with full context. When new indicators and events are ingested, regardless of origin, CrowdStrike and Zscaler together can effectively turn these weak signals into concrete threat detections to anchor security operations.
Step 1: Comprehensive Visibility Across Applications and Endpoints
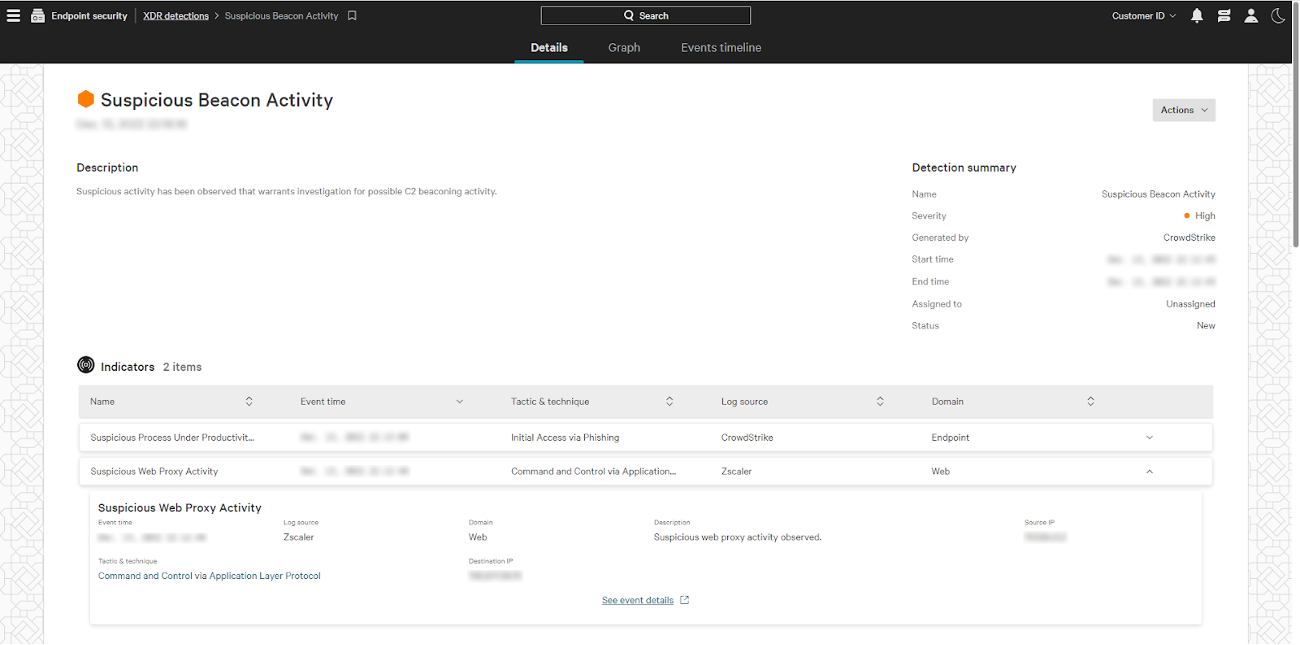
CrowdStrike offers a purpose-built XDR integration with Zscaler that funnels the most relevant security data at enterprise scale, achieving critical network and cloud application visibility.
Infusing network telemetry from Zscaler into CrowdStrike Falcon® Insight XDR provides enhanced context for security analysts, speeding the ability to detect and investigate the most advanced attacks directly from CrowdStrike’s unified command console.
Step 2: Cut Through the Noise and Detect Advanced Threats
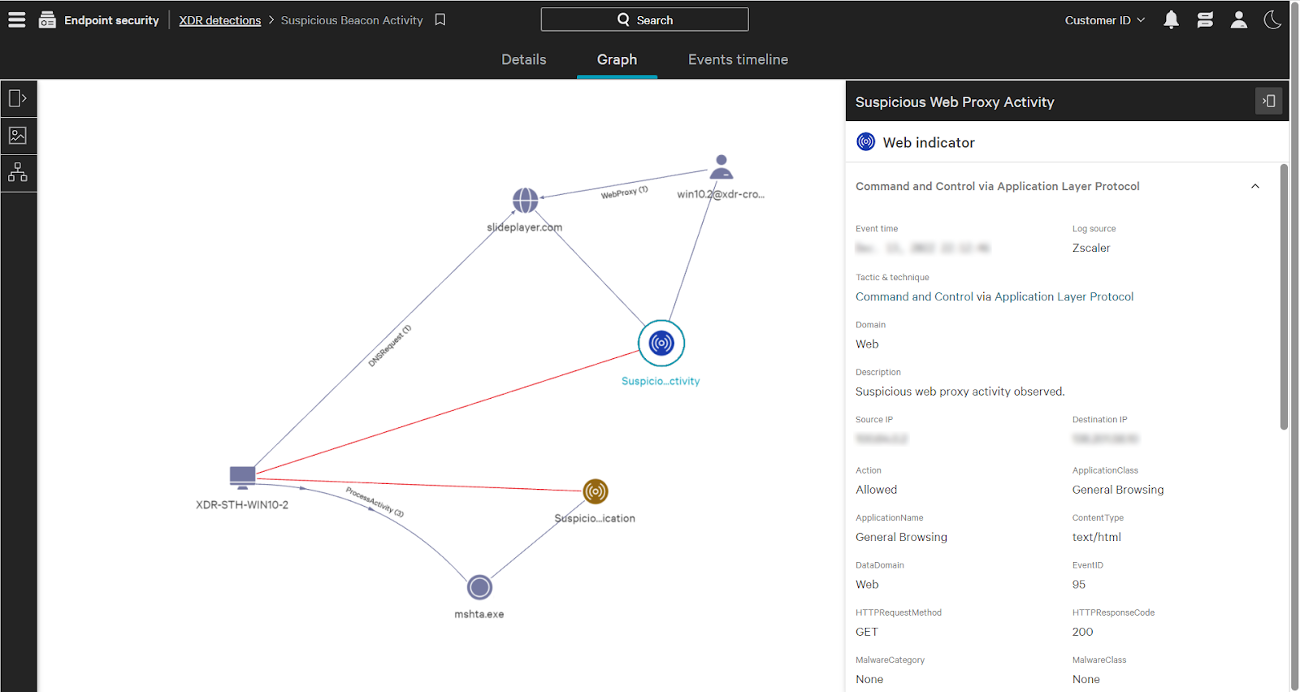
Effective XDR solutions need to do more than simply aggregate data. XDR needs to paint the full correlated picture of an attack with telemetry from across the security ecosystem.
Falcon Insight XDR leverages the security events from Zscaler to generate meaningful and actionable security insights as well as speed up proactive threat hunting. By simplifying an overwhelming amount of raw telemetry to a curated set of the most relevant and impactful cross-domain data, Falcon Insight XDR generates novel, net-new detections based on all of the CrowdStrike and third-party telemetry available from top solutions like Zscaler for the clearest possible picture of an attack.
This bidirectional, cross-platform sharing with Zscaler of threat intelligence, increased visibility and automatic workflow helps organizations increase the timeliness and effectiveness of overall threat detection. In addition, Zscaler enables administrators to initiate both orchestrated and manual containment requests to the CrowdStrike Falcon platform to prevent lateral movement from a compromised host in real time.
Step 3: Initiate Zscaler Response Actions Directly Within the Falcon Console
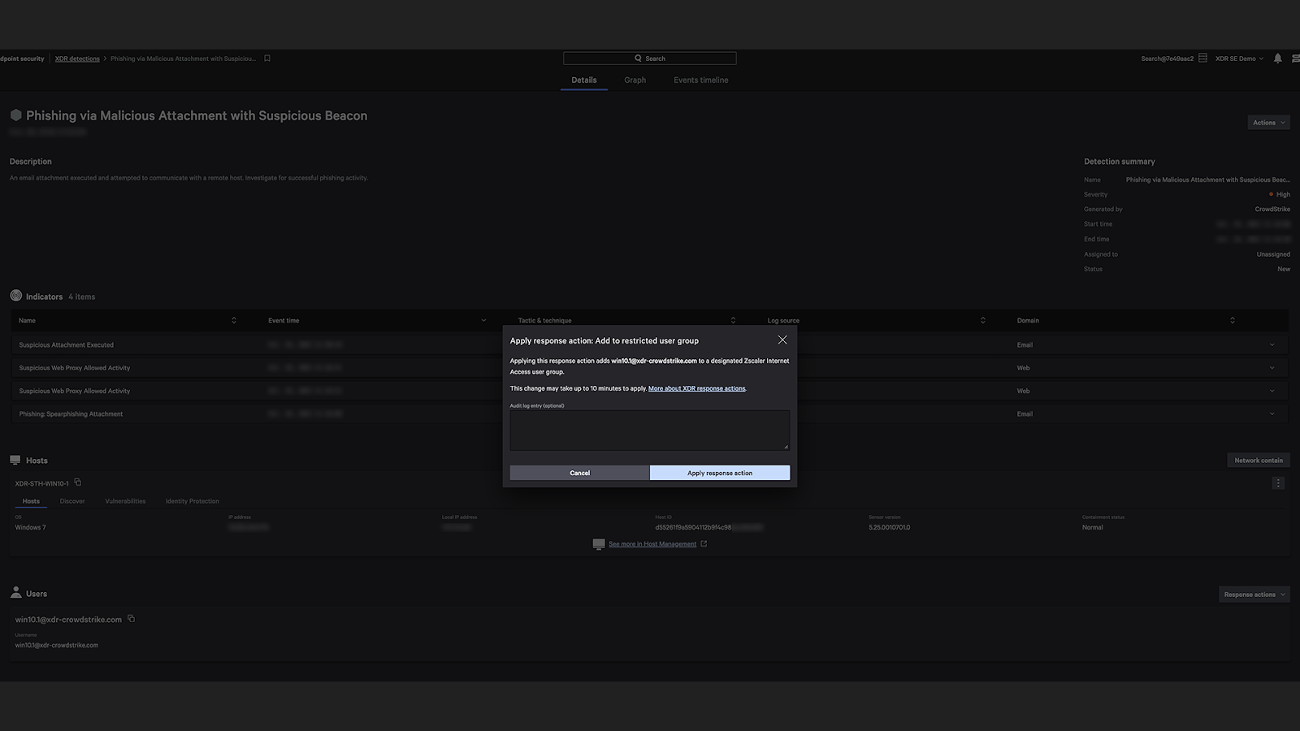
Customers can respond to threats immediately by leveraging Zscaler response actions directly within the Falcon console.
Based on newly detected threats or suspicious activity found within Falcon Insight XDR, customers can trigger direct response actions from detections or leverage CrowdStrike Falcon® Fusion workflows to automatically change user group membership and apply adaptive access control policies to limit or prevent access to critical information through the Zscaler Zero Trust Exchange.
Integrating these workflows helps apply more comprehensive Zero Trust policies to protect systems without compromising the flexibility that users need to stay productive, reacting with more granularity based on the severity and confidence of the threat detection from CrowdStrike. Delivering third-party response actions alongside XDR telemetry and detections provides analysts maximum context for response, saving valuable time when every second counts.
Watch a demo of CrowdStrike Falcon XDR in action.
Additional Resources
- Learn more about CrowdStrike Falcon Insight XDR and the CrowdXDR Alliance.
- See for yourself how the industry-leading CrowdStrike Falcon platform protects against modern threats like ransomware. Start a 15-day free trial today.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)