Public cloud services and cloud assets are agile and dynamic environments. Close oversight of these assets is a critical component of your asset management and security practices.
While it’s important to understand the relationships and potential vulnerabilities of your cloud assets, the practice of managing these systems is complicated by the ever-changing nature of cloud environments. Any changes in these environments can be invoked by a variety of staff members — site reliability engineers (SREs), DevOps, cloud architects, compliance teams, security teams and the cloud services providers (CSPs). Without situational awareness, it can be difficult to make good decisions about remediation and organizational risk.
As organizations move to a cloud-first posture, users need a contextual view of cloud assets and how these assets are connected to each other. This contextual view is vitally important to security teams that want to quickly assess the potential risk of any security breach and understand the potential risk to other cloud assets. Take the CrowdStrike Cloud Security Challenge with a free Cloud Security Health Check
Visualize Cloud Risk and Compliance with CrowdStrike Cloud Security
With the integration of the CrowdStrike® Asset Graph, CrowdStrike Cloud Security delivers powerful asset inventory and visualization features that strengthen your cloud security posture through risk mitigation and compliance enforcement.
Here are three ways that CrowdStrike Cloud Asset Visualization features helps you improve and strengthen your cloud security posture:
1. Create a Holistic View of Cloud Asset Inventory
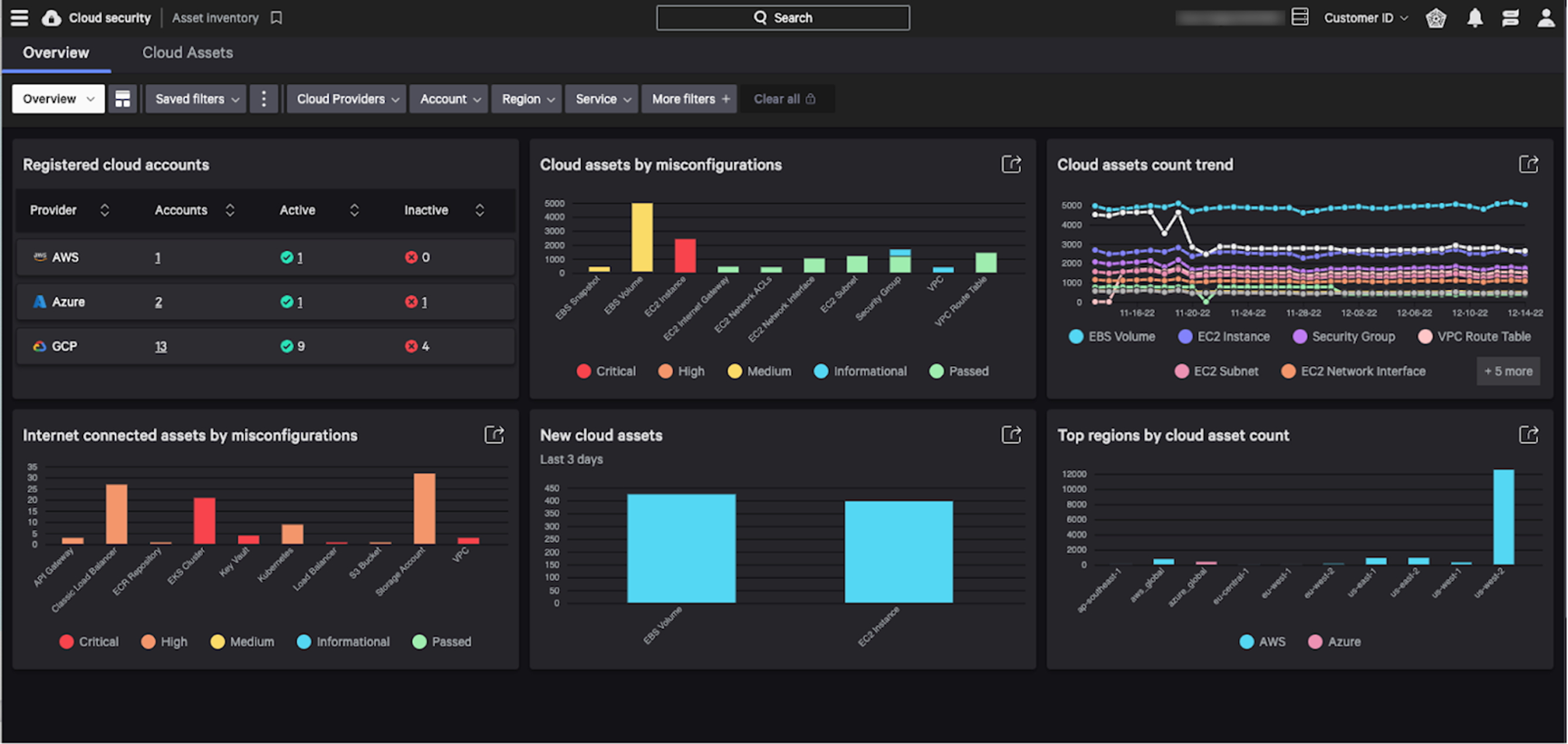
The Cloud Asset Overview Dashboard provides a holistic view of your cloud asset inventory.
This dashboard includes top counts, trends, detections, misconfigurations and other details across multiple public cloud environments (i.e., AWS, Azure, GCP). Additionally, you can drill down and filter to review specific asset information details within the Cloud Assets table.
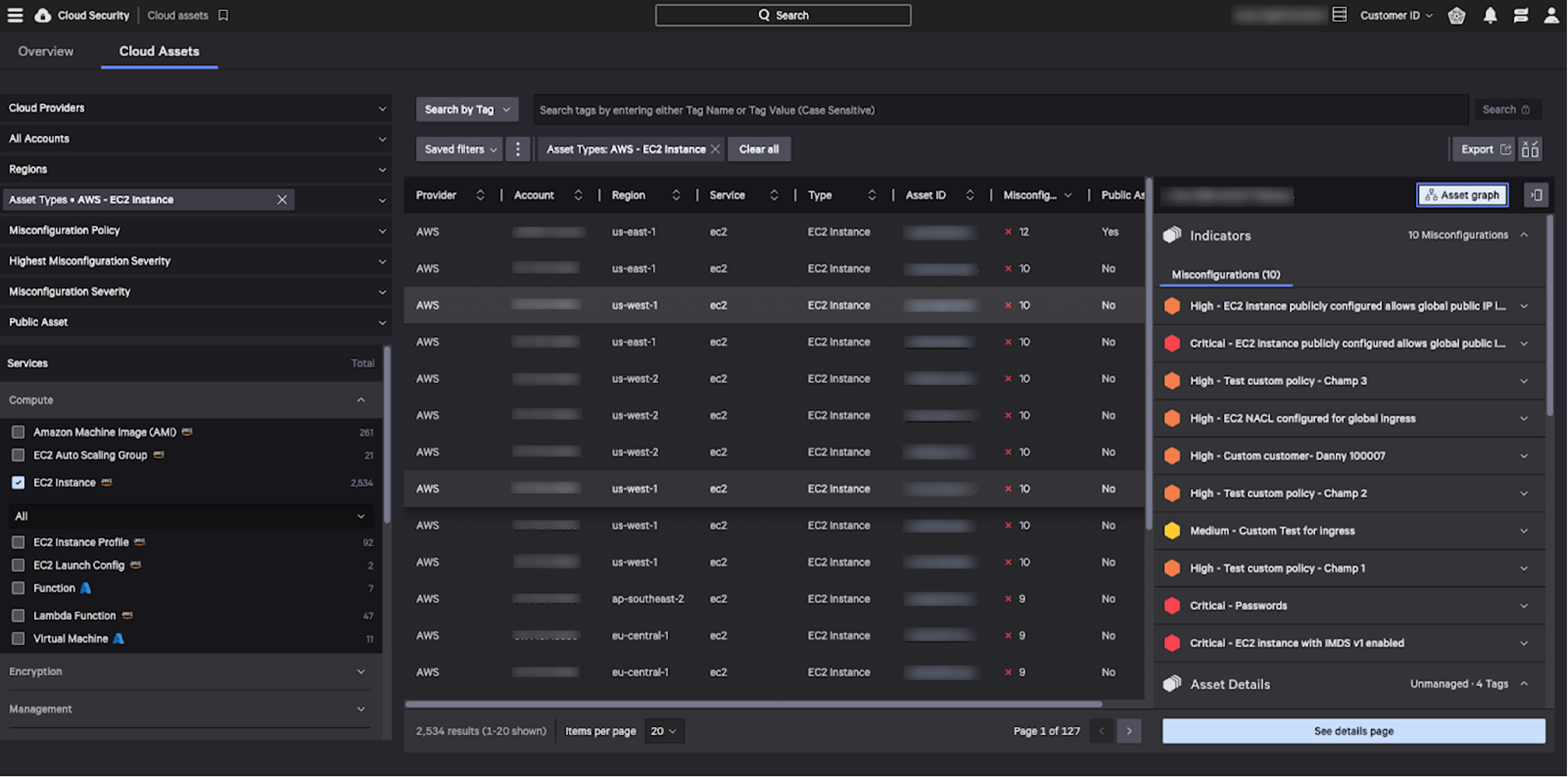
The Cloud Assets table provides a comprehensive asset inventory, covering all cloud assets/services from AWS, Azure and GCP and showing the risk posture from an asset-centric view. Users can:
- Investigate all cloud assets in one place and each asset’s security posture
- Save filters (including cloud “tags”) to focus on assets that are designated for monitoring
- Define and save filters to focus on what matters most to your organization
2. Gain Context Between Cloud Assets and Their Risk Exposure
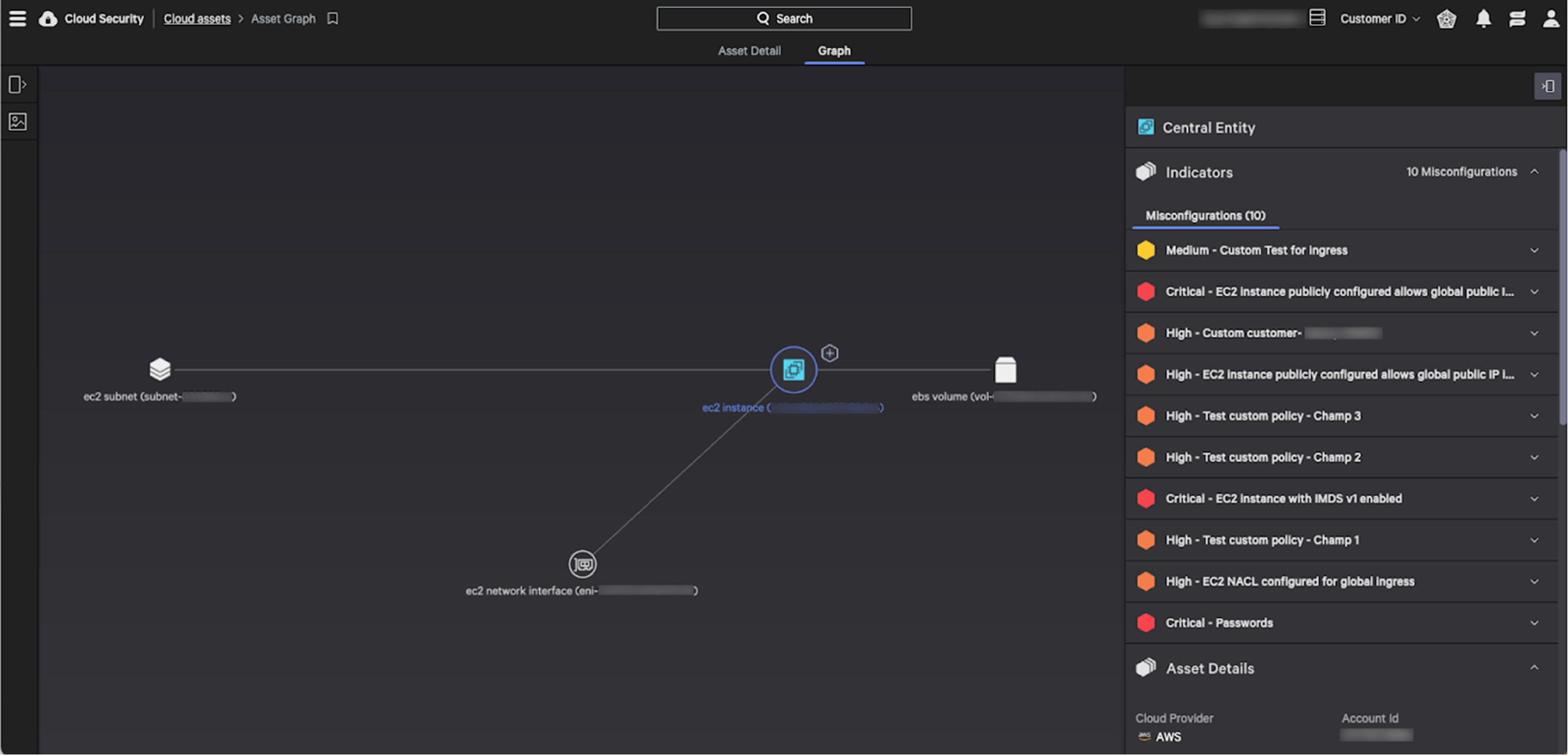
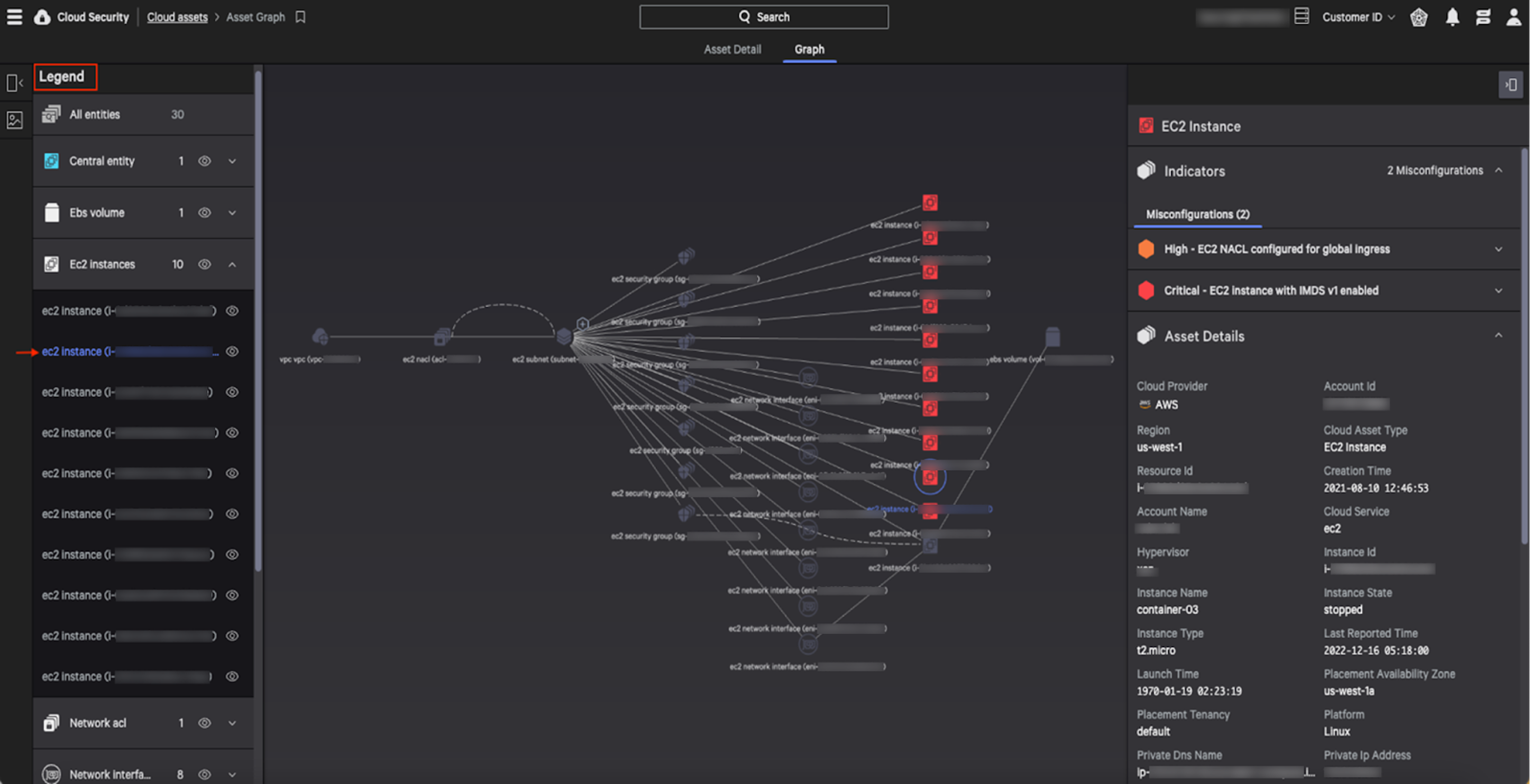
The Cloud Assets Graph tracks the relationships between cloud assets and shows their associated risk exposure to give you the context needed to reduce risk and close gaps in your posture. Using this graph, you can visualize misconfigured or insecure assets and take remediation and preventive actions on these assets as well as any connected cloud assets. From the Cloud Asset table, you can open the Asset Graph view to visualize the asset context:
This Asset Graph displays the selected cloud asset and its connections to other assets:
- The cloud asset you are investigating is the circled “central entity” in the graph.
- The asset details panel for the central entity is open when you first access the graph.
- Lines to other assets in the graph indicate relationships between those assets and the central entity.
- A dotted line between assets indicates that one asset is an asset type that defines a configuration for the other asset.
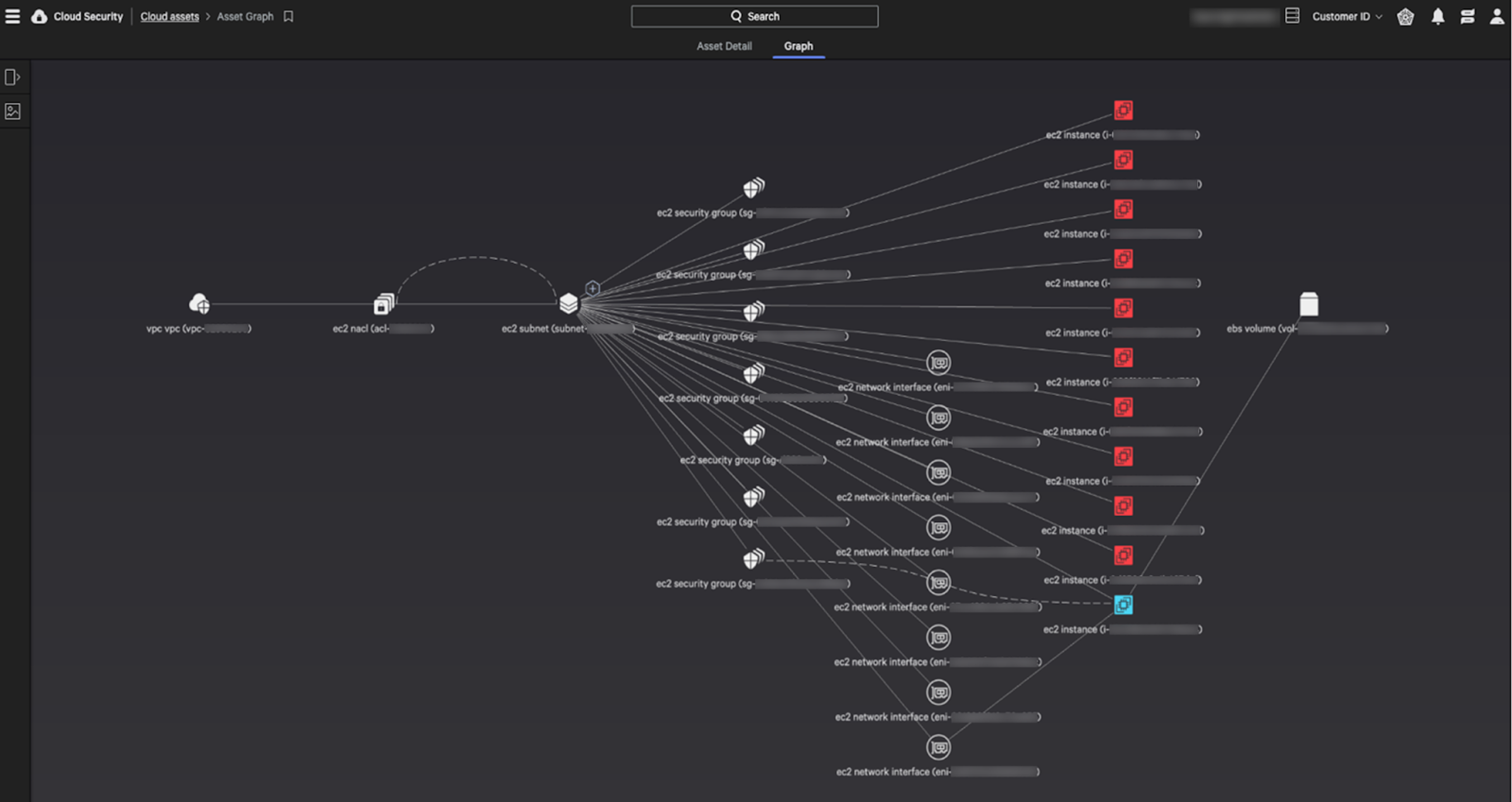
Next, you can expand the graph by clicking on the plus sign to view adjacent assets connected to the central entity:
This expanded view provides a comprehensive graph of all assets connected to the central entity and any indicators of misconfigurations (IOMs) associated with those adjacent assets (e.g., assets with critical IOMs are highlighted in red) Finally, enabling the Legends option (toggle) will provide the ability to highlight another asset and detail IOMs associated with that particular asset. Additionally, you can “hide” specific asset classes and focus on just a single type (e.g., show only EC2 instances or security groups).
3. Get Context on Cloud Breaches and Enforce Compliance
By gaining a full understanding of how every cloud asset is connected and getting context on their associated and compounded risk, security teams have the information required to identify cloud risk scenarios — and see how a breach would affect the broader environment.
For example, incident response (IR) teams need to understand the security breach context to develop effective recommendations for remediation and prevention. The IR team can visually review a detection “in context” of the system to understand the implications of potential lateral spread of the breach across other cloud assets.
At the same time, corporate governance and compliance teams can use this information to understand the specific compliance state (e.g., NIST, PCI, CIS) of the cloud assets and applications that utilize these assets.
Managing your cloud environment starts with a full understanding of the relationships and connections between your cloud assets. With the integration of Asset Graph and powerful new visualization features, CrowdStrike Cloud Security provides the comprehensive view and insight needed to fully evaluate the health and security of the entire cloud ecosystem and protect your cloud assets.
Additional Resources
- Cloud-conscious adversaries are on the rise. Join us for CrowdStrike’s Cloud Threat Summit to learn more about modern cloud threats and the innovations we’re developing to fight them.
- To learn more about the cloud threat landscape, download “Protectors of the Cloud: Combating the Rise in Threats to Cloud Environments.”
- Learn how you can stop cloud breaches with CrowdStrike unified cloud security for multi-cloud and hybrid environments — all in one lightweight platform.
- Build, run and secure cloud-native applications with speed and confidence using Falcon Cloud Workload Protection.
- Visit the Falcon Cloud Workload Protection Complete product webpage to see if a managed detection and response solution for cloud workloads is right for your organization.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)