Formbook is a tool that has been available for purchase from criminal forums for several years — 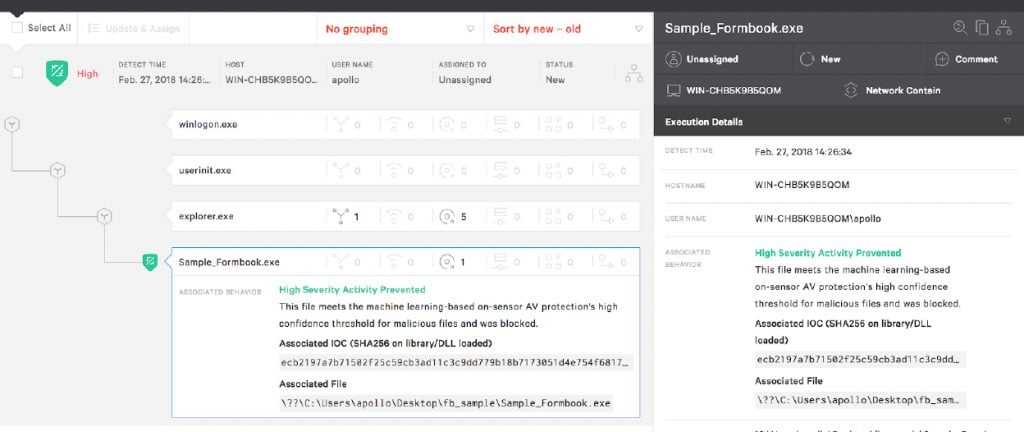 As the screenshot shows, Falcon endpoint protection is able to prevent the main Formbook process as soon as it is launched. Therefore, the steps of injection and information theft don’t have a chance to occur because the main process is blocked immediately upon launch.
CrowdStrike Falcon® Intelligence™ customers can find ongoing information about Formbook via the Falcon Intelligence portal.
Learn more about Falcon OverWatch™ proactive threat hunting, part of the CrowdStrike Falcon® Platform.
As the screenshot shows, Falcon endpoint protection is able to prevent the main Formbook process as soon as it is launched. Therefore, the steps of injection and information theft don’t have a chance to occur because the main process is blocked immediately upon launch.
CrowdStrike Falcon® Intelligence™ customers can find ongoing information about Formbook via the Falcon Intelligence portal.
Learn more about Falcon OverWatch™ proactive threat hunting, part of the CrowdStrike Falcon® Platform.
it’s used to steal information from a victim’s environment. Recently CrowdStrike® Falcon Intelligence™ observed a significant increase in criminal malware campaigns delivering Formbook payloads. Given the widespread nature of this activity, the CrowdStrike malware hunting team has gathered information to help security analysts hunt for Formbook activity in their own environments. These hunting leads are applicable to a variety of endpoint sensors.
What is Formbook?
Generally, Formbook is classified as an information-stealing and form-grabbing tool that offers keylogging, clipboard data gathering, screen capturing and password grabbing from email clients and browsers, as well as data extraction from HTTP/S forms and requests. The family name is derived specifically from Formbook’s form-grabbing capabilities — it is also known as “Private Balloon.” Formbook is often distributed via phishing emails that contain malicious attachments, which can consist of a macro-enabled lure document such as an Excel spreadsheet, a Word document, a PDF file or an Archive file — including a zip, rar, ace, or iso file containing a payload. While this appears to be the most recent delivery of choice, other mechanisms, such as malicious links, may replace lure documents in some campaigns; the choice of distribution method is determined by the operating actor. When launched, the Formbook payload injects itself into an existing process with the intention of providing hooks to various available functionalities. This can allow the malware to perform activities such as logging keystrokes, gathering clipboard data and extracting data from HTTPS sessions. Formbook also has the ability to receive remote commands from a C2 (command and control) server that include shutting down and rebooting a system, downloading and executing files, and stealing cookies and passwords. On installation, Formbook sets values in the following registries to establish persistence:- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\<copy location>
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run\<copy location>
- HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\<copy location>
- HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run\<copy location>
- %ProgramFiles%
- %Temp%
- %Appdata%
The payload written is a second copy of Formbook.
Hunting for Formbook
Formbook has several interesting behaviors that analysts can use to search for activity in their environments. The malware injects malicious code into an existing explorer.exe process when it launches. However, injection into explorer.exe alone is usually not enough to identify malicious activity, as several benign processes will also inject into explorer.exe. Following injection into explorer.exe, the malicious code randomly chooses an application from a static list, launches the selected application in suspended mode, copies itself in the address space of the suspended process, and then resumes the thread. Therefore, all the information stealing and form grabbing occurs from the context of the newly spawned legitimate process.Depending on the process chosen to host the malicious activity, it can appear suspicious. The following is a list of potential processes:
svchost.exe, msiexec.exe, wuauclt.exe, lsass.exe, wlanext.exe, msg.exe, lsm.exe, dwm.exe, help.exe, chkdsk.exe, cmmon32.exe, nbtstat.exe, spoolsv.exe, rdpclip.exe, control.exe, taskhost.exe, rundll32.exe, systray.exe, audiodg.exe, wininit.exe, services.exe, autochk.exe, autoconv.exe, autofmt.exe, cmstp.exe, colorcpl.exe, cscript.exe, explorer.exe, wwahost.exe, ipconfig.exe, msdt.exe, mstsc.exe, napstat.exe, netsh.exe, netstat.exe, raserver.exe, wscript.exe, wuapp.exe, cmd.exe
Using an endpoint security solution, an analyst may search for an application from the list above. For example, “netstat.exe” is launched in suspended mode under an explorer process that has been injected with malicious code. Since an application like netstat.exe is rarely launched in suspended mode, this could signal malicious behavior. Another good example is lsass.exe, which is typically never launched under explorer.exe suspended. While the application itself might appear benign, the ancestry of the process and the creation flags (e.g. suspended) are important indicators of malicious activity. On the other end of the spectrum, searching for svchost.exe launched in suspended mode under explorer.exe is likely to produce false positives. However, in any given environment, mileage may vary, depending on the applications that are present. In general, all the files in Formbook’s static list of targets — except for explorer.exe — reside in C:\Windows\System32. Launching any file from C:\Windows\System32 in suspended mode can be deemed suspicious, and in addition to potentially identifying Formbook activity, it may also help uncover other malicious behavior. Once executed, the malware spawns cmd.exe to delete itself from disk. Specifically, this process is spawned from the randomly chosen aforementioned child processes. Malware occasionally displays this self-deletion behavior to aid in remaining undetected. Once the malware has established persistence, an analyst can also search for the registry keys mentioned above launching an application from one of the listed environment variables. In some environments, very few legitimate applications will create similar registry keys, making ASEP value updates a good sign of potentially malicious activity. Another interesting side effect of Formbook’s technique of launching a random process from a list of potential candidates is the lack of expected command line arguments. In most cases, those processes should launch with some kind of arguments to instruct the application to do something. Looking for processes that are launching without arguments, or with anomalous or repeated arguments, can result in uncovering interesting malicious activity. Importantly, before Formbook gains persistence, it has to successfully arrive on the host, and phishing attacks generally have texture that analysts can search for. Details of potential dropping techniques can be found in this blog on blocking PowerShell downloads. It also should be noted that the technique used by the attacker will vary from one campaign to the next.How CrowdStrike Falcon® Protects Against Formbook
The latest version of Formbook (Formbook 3.8 aka Private Balloon) demonstrates that malware is ever-evolving and becoming more widely available to threat actors with varying levels of sophistication. However, the CrowdStrike Falcon® platform can help you mount a powerful defense against adversaries who are leveraging Formbook. The picture below demonstrates how Falcon detects and prevents Formbook. As the screenshot shows, Falcon endpoint protection is able to prevent the main Formbook process as soon as it is launched. Therefore, the steps of injection and information theft don’t have a chance to occur because the main process is blocked immediately upon launch.
CrowdStrike Falcon® Intelligence™ customers can find ongoing information about Formbook via the Falcon Intelligence portal.
Learn more about Falcon OverWatch™ proactive threat hunting, part of the CrowdStrike Falcon® Platform.
As the screenshot shows, Falcon endpoint protection is able to prevent the main Formbook process as soon as it is launched. Therefore, the steps of injection and information theft don’t have a chance to occur because the main process is blocked immediately upon launch.
CrowdStrike Falcon® Intelligence™ customers can find ongoing information about Formbook via the Falcon Intelligence portal.
Learn more about Falcon OverWatch™ proactive threat hunting, part of the CrowdStrike Falcon® Platform.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)




















































