Stealthy and Powerful
CrowdStrike frequently observes adversaries using valid account credentials across the attack lifecycle. In fact, credential dumping, an illegal way to obtain account credentials, is one of the most prevalent techniques observed by CrowdStrike® in its 2019 Global Threat Report. Obtaining credentials is extremely advantageous for attackers, allowing them to login remotely and easily gain access to systems and networks. Gaining credentials allows attackers to impersonate the account owner and appear as someone who has legitimate access, such as an employee, contractor or even a third-party supplier. Because the attacker looks like a legitimate user, this type of attack is extremely difficult for defenses to detect. Also, the absence of malware in these types of attacks leaves traditional defensive technologies, such as antivirus, powerless.
MITRE ATT&CK Framework
Once on a system via credential theft, the attacker has access to everything the account is entitled to, so it’s not surprising that attackers try very hard to obtain these credentials. The MITRE attack framework (ATT&CKTM) has identified 19 different credential access techniques used by adversaries. Falcon OverWatchTM, CrowdStrike’s team of proactive threat hunters, has observed that adversaries most often compromise users via phishing emails and then use brute force or credential dumping methods to obtain credentials. The heat map table below shows the credential access techniques used by attackers, with the darker cells indicating the relative prevalence of each method.
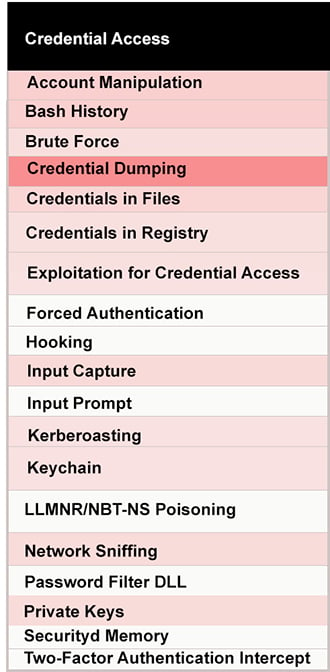 MITRE ATT&CK Heat Map of the Credential Access Techniques Used by Attackers
MITRE ATT&CK Heat Map of the Credential Access Techniques Used by AttackersA Wide Range of Applications
The access provided by stolen credentials is so powerful that attackers find ways to use them whenever possible, from malware and ransomware to targeted attacks. The ransomware Not Petya, for example, uses credential access to spread in a way that doesn’t require human intervention. Upon infection, it drops a credential theft module that extracts credentials on infected computers. It then uses the harvested credentials to connect and automatically spread to other computers across the network. Another nefarious malware, the TrickBot banking Trojan, is used to steal login credentials to banking sites. This modular Trojan contains a password-grabbing module called “pwgrab” that is used for credential harvesting. Trickbot sets the registry “UseLogonCredential” value to “1,” which configures the Windows operating system to store credentials as clear text in memory. Credentials can then be retrieved from memory using other credential-dumping tools. Out of all those techniques, CrowdStrike has observed that adversaries typically obtain credentials via successful phishing, brute force or credential dumping methods.
The following are
the latest and most prevalent:
- The attacker gained initial access to a domain controller by using remote desktop protocol (RDP) to login to the server with valid credentials.
- The adversary then copied Group Policy Preference (GPP) files, which can be mined for credentials and other information. They also used the Active Directory (AD) Explorer utility provided in Windows to save snapshots of the AD database for offline viewing.
- Later, the actor accessed a SQL server over RDP using valid credentials and deployed the ProcDump utility to dump memory from the LSASS process, providing the attacker with additional credentials.
- The attacker was also observed using a technique called Kerberoasting, which consists of using a valid Kerberos ticket-granting ticket to request one or more ticket-granting service tickets from the domain controller. Those tickets are of interest to an attacker because they may be vulnerable to offline brute-force attacks that can expose plaintext credentials.
How to Prevent and Detect Credential Access Attack Techniques
Use MFA
Multifactor authentication (MFA) is highly recommended to effectively thwart these techniques, because users are required to present more than one type of authentication — such as a combination of password, security token and/or biometric verification. This makes it much more difficult for adversaries to obtain and leverage credentials to gain access to the environment.
Implement IT Hygiene
An IT hygiene tool such as CrowdStrike Falcon® DiscoverTM provides visibility into the use of credentials across the organization to detect potentially malicious admin activity. The account monitoring feature allows security teams to check for the presence of accounts created by attackers to maintain access. It will also help ensure that passwords are changed regularly, so stolen credentials can’t be used forever.
Add Proactive Threat Hunting
True proactive threat hunting, such as Falcon OverWatch provides, enables hunting 24/7 for unknown and stealthy attacks that utilize stolen credentials and are conducted under the guise of legitimate users. These are the types of attacks that standard measures can miss. Employing the expertise gained from daily “hand-to-hand combat” with sophisticated advanced persistent threat (APT) actors, the OverWatch team finds and tracks millions of subtle hunting leads daily to validate if they are legitimate or malicious, alerting customers when necessary.
True Next-Gen Endpoint Protection is Key
Credential access is a popular technique used by attackers because it is highly effective. Organizations should take the threat of credential theft seriously and implement strategies to avoid victimization. These can include establishing multifactor authentication and employing a next-generation endpoint protection solution such as the CrowdStrike Falcon®® platform, which is designed to protect across the complete spectrum of attacks, including those that use stolen credentials.
Additional Resources
- Download the 2020 CrowdStrike Global Threat Report.
- Find out what third-party analysts and evaluators have to say about the Falcon platform by visiting the CrowdStrike Industry Validation webpage.
- Learn more about the MITRE framework in the white paper: “Faster Response with CrowdStrike and MITRE ATT&CKTM.”
- Test CrowdStrike next-gen AV for yourself: Start your free trial of Falcon Prevent™ today.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































