As malware and its authors continue to evolve, deciphering the purpose of specific malware-driven attacks has become more challenging. While some malware still has a feature-specific design such as DDoS tools or spam bots, it is becoming increasingly common for malware to have multiple uses for different missions. Recent banking trojans for example are likely to support remote access, which is not typically required to deliver web injects and steal credentials. In some cases, the functionality of the malware suggests the actor’s intent: A sample of a malware family known to engage in spam campaigns is unlikely to have been used as part of a targeted espionage attack. Vice versa, a malware with pure surveillance functionality likely does not fit a botnet-like monetization technique that relies on large-scale distributed activities such as sending spam or denial of service. For example, short-term financial gain is a recurring motive for typical cybercrime actors while the theft of intellectual property and business information usually reflects a different kind of actor. Numerous examples of recent years highlight that the boundaries between commodity and targeted attack malware blur. Variants of Black Energy, a malware family known to have been used for distributed denial-of-service (DDoS) attacks around 2010 were then adapted for targeted attacks. While publicly well-known for its banking fraud and the distribution of additional malware such as Cryptolocker, the peer-to-peer-based Gameover Zeus botnet was leveraged to search for information regarding foreign intelligence services of Russia’s neighbouring countries. In short, some crimeware tools have turned into targeted attack malware and no longer allow a precise classification in either categories. Recently, CrowdStrike Intelligence investigated a case where the distinction between commodity cybercrime and targeted attack activity is difficult to make. This malware was written in JavaScript and relies on Windows Script Host (WSH) as the interpreter - a technique rarely seen before. By relying on a benign interpreter binary and obfuscated script code, the malware is likely to remain under the radar. The RecJS Case Recently, a malware family named RecJS caught our attention as it contains functionality that is typical for a Remote Access Tool (RAT), including file transmission, taking a screenshot, and command execution. While previous variants had a hard-coded Command-and-Control (C2) server IP address in the code, recent samples implement a Domain Generation Algorithm (DGA) to locate the C2 server. Stepping up from hard-coded C2 information to a DGA indicates a dedicated evasion interest by the operator, which made us curious to take a closer look at this malware. A sample of this malware family is a file named c700.gif with the MD5 hash eb6ef4a244b597ec19157e83cc49b436. Although the gif file extension suggests an image, the file is a 32-bit Windows Portable Executable (PE). Typically, a RecJS malware sample is deployed in the form of a Nullsoft Scriptable Installer (NSIS) binary that, when launched, extracts the required files (including the JavaScript code) and invokes the RAT. The payload files are stored in an embedded password-protected archive of the installer binary which is a technique often observed in order to defeat static unpacking. With the core of the malware being authored in JavaScript, it relies on the WSH interpreter wscript.exe that ships with Microsoft Windows operating systems. In effect, no custom binary needs to be launched, likely in an intention to reduce the chance of being detected by anti-virus. In addition, the JavaScript code is obfuscated and has whitespace removed. The obfuscation technique is particularly suited to evade static code analysis systems as it replaces variable and function names with innocuous names that are likely to be present in benign JavaScript code. This is extended with typical string obfuscation techniques that assemble sensitive strings such as parts of the DGA domains at runtime. All of these impede automatic malware classification. Bootstrapping Unpacking the embedded files takes place in several steps. First, the installer binary extracts from itself the 7-Zip compression utility, consisting of the 7-Zip executable (7z.exe) and a required library (7z.dll). Interestingly, the two files are not dropped as a whole, but in the form of multiple fragment files. Each of the two files is reassembled from these fragments using Windows’ copy utility. For example, the file 7z.dll is concatenated as follows:
copy /b 388f + 2c + 33 + c0952 + 2e8defc + 2e8def 7z.dll
In the second step, a password-protected archive is dropped and extracted using 7-Zip with the password bd250c2d9f9e23da6c69c042f0c48995. This archive contains the JavaScript RAT code and a benign screenshot helper binary. Due to the password protection, static extraction of the malicious code is non-trivial. Finally, the installer launches WSH to execute the RAT in the background:
wscript.exe /b /nologo /E:javascript <RAT_SOURCE_FILE> startup
To persist across reboots, the RAT creates a shortcut in the user's Startup folder named Windows Application Manager.lnk with the invocation command from above as target. Command and Control Once launched, the RAT downloads a configuration update from the C2 server, in this case via HTTPS, from https://qkmakein.endofinternet.net/related/?action=get_config&guid=<ID>&version=700. The C2 domain is generated using a time-seeded domain generation algorithm that yields a unique dynamic domain name every hour that is a subdomain of one of the following (all served by Dynamic Network Services, Inc.):
- isteingeek.de
- endofinternet.net
- servebbs.com
The subdomain part is generated from a set of 53 terms using a custom algorithm. Based on the current time, four items from the list of terms are derived and concatenated to form the subdomain that is prepended to one of the three domains provided above. The set of commands implemented by the RAT spans the following:
| Command | Description |
| screenshot | Take a screenshot and upload it to the C2 server |
| exec_js_module | Invoke JavaScript code with wscript.exe /b /nologo /E:javascript |
| debug_log | Upload a debug log to the C2 server |
| update | Update the RAT |
| download_and_exec | Download a binary from a provided URL and execute it |
| update_config | Update the RAT’s configuration |
| restart | Restart the RAT |
| die | Uninstall and terminate the RAT |
| uninstall | Alias for the command “die” |
| stop | Terminate the RAT (but leave startup link so that the RAT starts on the next boot) |
For the screenshot functionality, a helper binary named windrv.exe (MD5 hash 75fb0aecd2cfef2210495a4f3cab5bcf) is dropped in the same directory as the JavaScript code. It is used to take a screenshot that is uploaded to the C2 server. The helper binary is publicly available from the open source screenshot-cmd project with a filename of screenshot-cmd.exe. Relying on a publicly available tool to acquire a screenshot is clever as this binary is not flagged as malicious by anti-virus products. The screenshot helper tool can be used to capture the whole screen or a specific window. The malware gathers extensive system information including the username; domain name; amount of RAM memory; code page; Windows properties such as the architecture, OS version, install date, language, and Windows serial number; and installed anti-virus products. The malicious code contains what appears to represent a campaign ID, with this specific instance carrying a value of 700. This number is sent in the query string of C2 requests and is also present in the installer’s filename, which indicates that the binary was built for a specific campaign and that the operator is interested in campaign tracking. This malware exhibits typical RAT functionality. The command set is well suited to allow for remote access and rudimentary surveillance of specific targets. The initial beacon provides the operator with various system information that is helpful when deciding whether an infected system is of interest or just unintended bycatch. A screenshot can be taken when instructed to by the C2 server so that the operator also has a visual impression of the victim’s desktop. At this point, the functionality of the malware is clear: A typical remote access tool. While this functionality may be interpreted to indicate a targeted attack, it does not disclose the actor’s intent. Thus, the following section sheds light on the distribution of the malware and the victimology. Infection Vector and Victimology Variants of the RecJS malware are believed to have been distributed since at least April 2014. On 30 April 2014, a RecJS sample was dropped as part of a drive-by infection of visitors to webmasters.ru, a Russian forum dealing with web development topics. When browsing the main site, a CVE-2012-1723 exploit that leveraged a vulnerability in certain Java versions was served. This exploit triggered the download and execution of a RecJS installer binary with the filename s5b_484.exe. The C2 communication of this sample carries the campaign ID 484, which matches part of the dropper filename and indicates that it was specifically built for this campaign. The fairly broad drive-by infection strategy was originally associated with a cybercriminal business model that builds on scale rather than specific targets and is still extremely popular in the form of exploit kits. Consequently, the set of infected entities in a recent RecJS campaign is diverse in nature. While the infection vector of this campaign hints toward non-targeted cybercriminal activity, it is difficult to draw a precise conclusion at this point. Recently, sophisticated targeted attacks have increasingly relied on a web-based infection vector. In addition, it is possible that the infection vector has changed over time and may have been adapted depending on the target. Based on the source IP addresses of infected hosts, by far most of the victims are in Russia, with a tendency to its neighboring countries, including Ukraine, Poland, Kyrgyzstan, Romania, Serbia, Czech Republic, and Hungary. However, western countries are also prominently represented, e.g., the United States, the United Kingdom, Canada, Germany, the Netherlands, France, Australia, Austria, and Denmark. The following figure shows a heat map generated from unique source IP addresses with a syntactically valid C2 request. The set of source IP addresses may be biased due to IP churn. In order to filter out unlikely victims such as research systems, behavior which is atypical of a RecJS infection was removed. 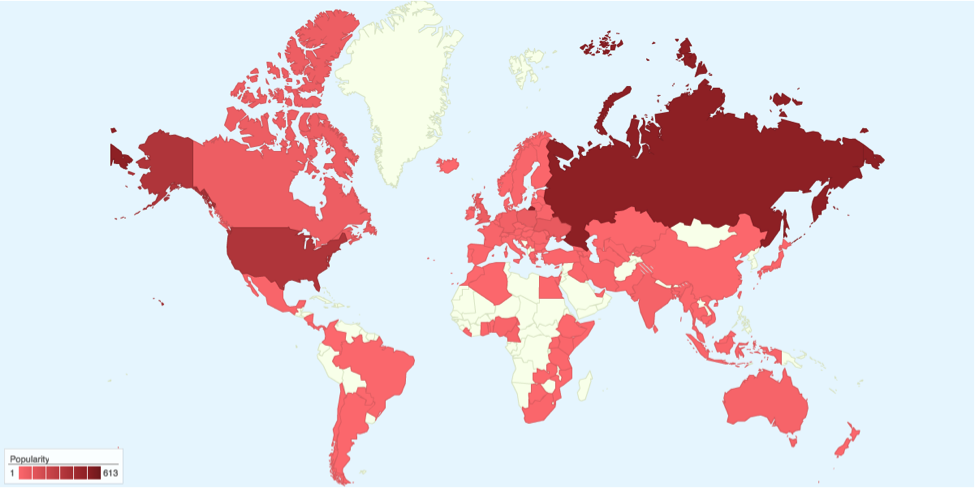 The regional distribution of victims with Russia ranking first aligns with the infection vector outlined above. In addition, past variants of the malware have been observed to communicate with the C2 servers 91.213.233.219, which is assumed to be located in Kyrgyzstan, and 178.57.218.189, which is located in Russia. Both suggest a nexus to the Russian-speaking area. Interestingly, a few high-profile targets have been identified, including government institutions, financial institutions, and entities in the education sector. Among the diverse set of victims, we spotted the ministry of foreign affairs of a European government, several banks, and the logistics base of the United Nations. Assessing the Actor’s Intent Incidents like this involving RecJS are a clear example that malware analysis alone hardly answers the question of the actor’s intent. Even with contextual information such as the distribution vector and victimology, there is no obvious explanation whether this is a targeted attack. Based on the broad infection strategy of the drive-by scenario and the comparatively small number of victims, the heavy ratio of high-profile to inconsequential victims is unexpected. The actor may have started out using a broad targeting without a specific victimology or monetization in mind: Once launched and depending on the infection success, those victims that appear suitable for a specific monetization technique may be capitalized. Alternatively, IT personnel such as web developers and administrators might have been targeted on purpose as outlined in the example above involving the drive-by infection of a webmaster forum. Infected systems could be leveraged to steal credentials for corporate infrastructures. These credentials may serve as a stepping stone to infiltrate the infrastructure of specific institutions or allow for targeted spear phishing. The challenge of attribution extends far beyond technical analysis, this is where the reverse engineer must see through the eyes of an intelligence analyst, making and testing hypothesis about the intentions of the actor. This is a difficult and often uncomfortable task for those who live in the binary space of code, one that the analysts at CrowdStrike deal with every day. For more information on the RecJS malware, feel free to contact us at intelligence@crowdstrike.com. If you think you are up to the challenge of analyzing the motivations of malicious adversaries, check our job listings to join the mission!
The regional distribution of victims with Russia ranking first aligns with the infection vector outlined above. In addition, past variants of the malware have been observed to communicate with the C2 servers 91.213.233.219, which is assumed to be located in Kyrgyzstan, and 178.57.218.189, which is located in Russia. Both suggest a nexus to the Russian-speaking area. Interestingly, a few high-profile targets have been identified, including government institutions, financial institutions, and entities in the education sector. Among the diverse set of victims, we spotted the ministry of foreign affairs of a European government, several banks, and the logistics base of the United Nations. Assessing the Actor’s Intent Incidents like this involving RecJS are a clear example that malware analysis alone hardly answers the question of the actor’s intent. Even with contextual information such as the distribution vector and victimology, there is no obvious explanation whether this is a targeted attack. Based on the broad infection strategy of the drive-by scenario and the comparatively small number of victims, the heavy ratio of high-profile to inconsequential victims is unexpected. The actor may have started out using a broad targeting without a specific victimology or monetization in mind: Once launched and depending on the infection success, those victims that appear suitable for a specific monetization technique may be capitalized. Alternatively, IT personnel such as web developers and administrators might have been targeted on purpose as outlined in the example above involving the drive-by infection of a webmaster forum. Infected systems could be leveraged to steal credentials for corporate infrastructures. These credentials may serve as a stepping stone to infiltrate the infrastructure of specific institutions or allow for targeted spear phishing. The challenge of attribution extends far beyond technical analysis, this is where the reverse engineer must see through the eyes of an intelligence analyst, making and testing hypothesis about the intentions of the actor. This is a difficult and often uncomfortable task for those who live in the binary space of code, one that the analysts at CrowdStrike deal with every day. For more information on the RecJS malware, feel free to contact us at intelligence@crowdstrike.com. If you think you are up to the challenge of analyzing the motivations of malicious adversaries, check our job listings to join the mission!






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)




















































