This blog was originally published on June 11, 2019.
Researchers from Preempt (now CrowdStrike), have discovered how to bypass the Enhanced Protection for Authentication (EPA) mechanism to successfully launch NTLM relay attacks on any server that supports WIA (Windows Integrated Authentication) over TLS.
This attack technique could be used by attackers to attack critical servers such as:
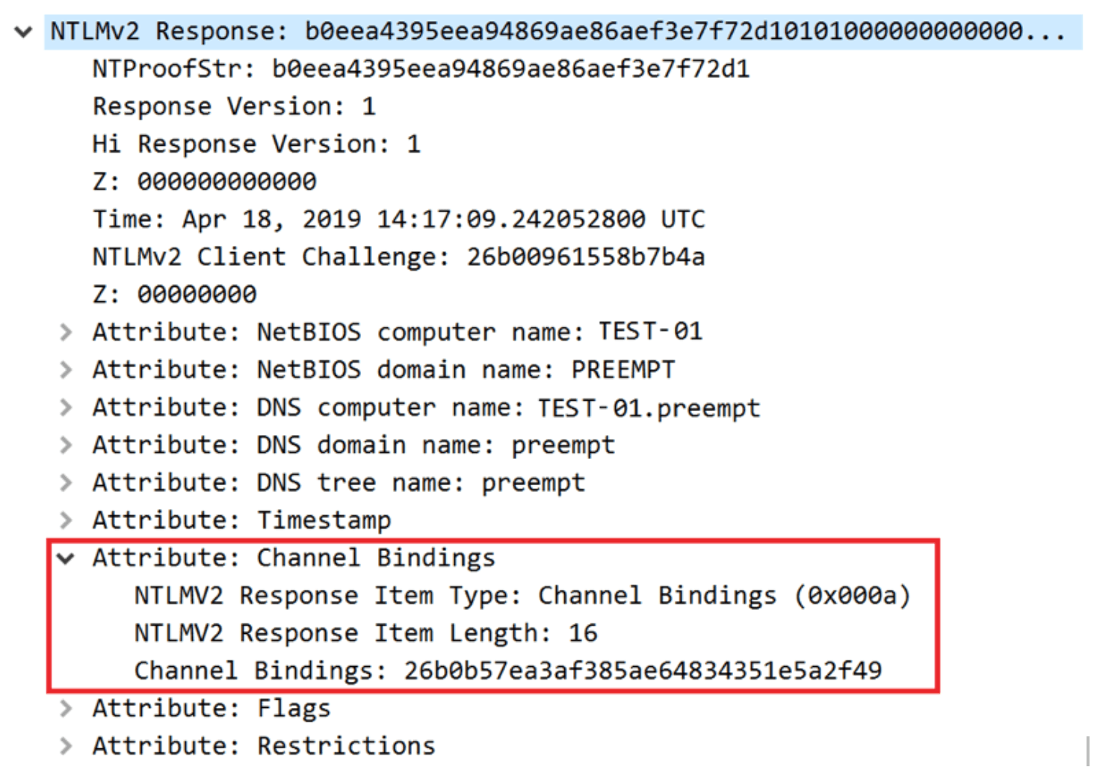 Figure 1. The NTLM_AUTHENTICATE message with channel binding
Figure 1. The NTLM_AUTHENTICATE message with channel binding
 Figure 2. The malicious NTLM_CHALLENGE message with channel binding element
We believe that this is a serious attack vector because EPA is practically the only line of defense guarding critical servers such as AD FS or OWA. In many organizations, it is very likely that an attacker with a small footprint in the network could make users authenticate via NTLM and relay their credentials. In fact, since AD FS and OWA are often open to the internet, in some cases, an attacker could compromise these servers with no infected machines just by sending a malicious email (e.g., the attack depicted here).
Figure 2. The malicious NTLM_CHALLENGE message with channel binding element
We believe that this is a serious attack vector because EPA is practically the only line of defense guarding critical servers such as AD FS or OWA. In many organizations, it is very likely that an attacker with a small footprint in the network could make users authenticate via NTLM and relay their credentials. In fact, since AD FS and OWA are often open to the internet, in some cases, an attacker could compromise these servers with no infected machines just by sending a malicious email (e.g., the attack depicted here).
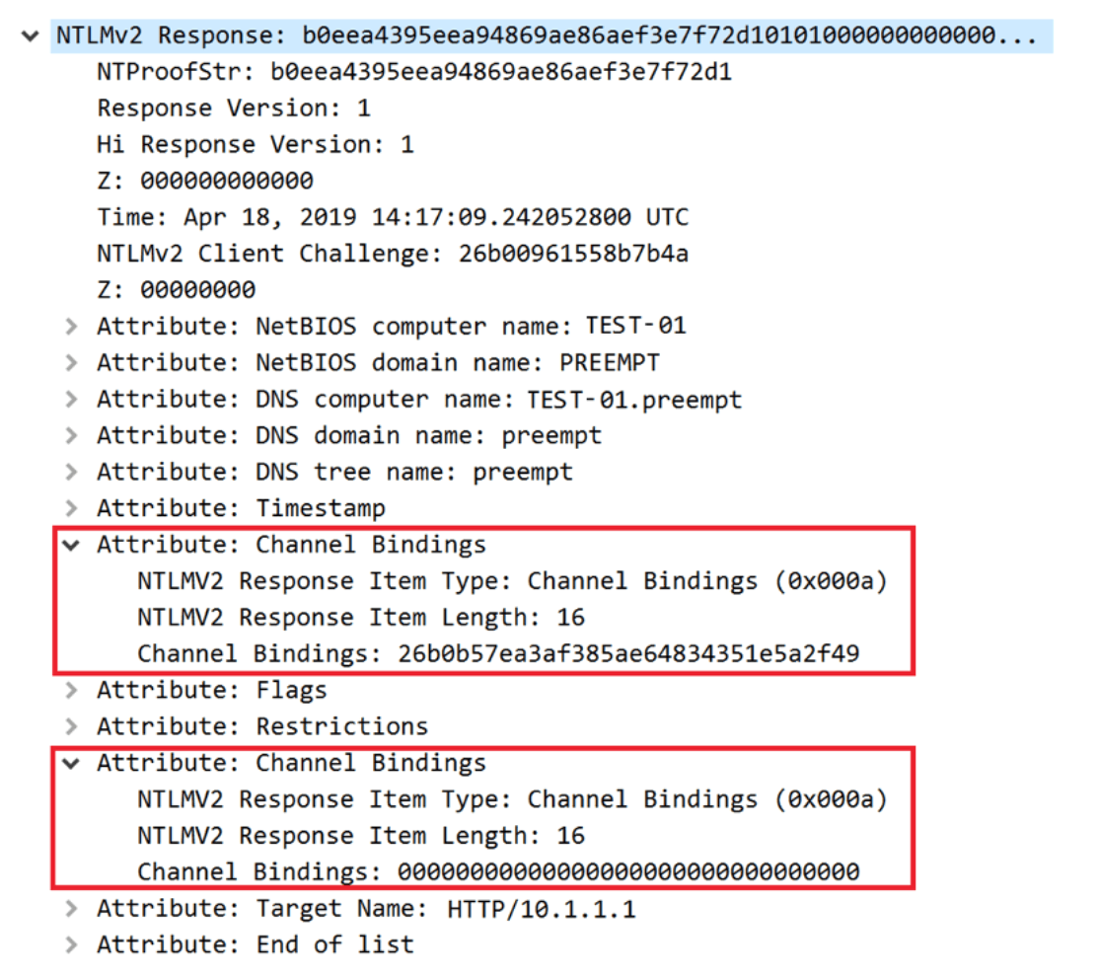 Figure 3 – NTLM_AUTHENTICATE message with our implanted channel binding
Figure 3 – NTLM_AUTHENTICATE message with our implanted channel binding
- Exchange (OWA): Perform NTLM relay to a mail server and steal user emails
- Active Directory Federation Services (AD-FS): Perform NTLM relay to HTTPS sessions and impersonate users on cloud resources.
- Active Directory: Perform NTLM relay to LDAPS and configure directory with malicious settings.
EPA – Background
NTLM relay is one of the most prevalent attacks on Active Directory environments. There are two mitigation techniques offered by Microsoft to thwart NTLM relay attacks: one is server signing, which is used mainly in SMB and DCE/RPC, and the second is channel binding which is also known as EPA. EPA is a mechanism that ensures that all packets sent over a TLS channel are sent by a party that knows the client’s secret (in the NTLM case, the NT hash). This is achieved through binding the Windows authentication process with the TLS session by requiring the client to sign a derivative of the server’s certificate using the GSSAPI security. In NTLM, this is achieved by adding a specific channel binding AV pair in the NTLM_AUTHENTICATE message. Since the entire AV pairs structure is signed in the NTProofStr, an attacker cannot modify it without knowing the user’s NT hash. Figure 1. The NTLM_AUTHENTICATE message with channel binding
Figure 1. The NTLM_AUTHENTICATE message with channel bindingBypass EPA
In a separate discovery, our researchers have found a way to remove the message integrity code (MIC) from the NTLM authentication. With the MIC missing, attackers can tamper with the NTLMSSP_CHALLENGE message. How can this be used to their advantage? The NTLMSSP_CHALLENGE message contains a TargetInfo field and NTLM clients usually echo all AV pairs in the TargetInfo and include these in the AV pairs in the NTLMSSP_AUTHENTICATE message. This means that an attacker that can modify NTLM messages can send a malicious NTLM_CHALLENGE with a channel binding of their choice to attack any server that is protected with EPA. Figure 2. The malicious NTLM_CHALLENGE message with channel binding element
Figure 2. The malicious NTLM_CHALLENGE message with channel binding element Figure 3 – NTLM_AUTHENTICATE message with our implanted channel binding
Figure 3 – NTLM_AUTHENTICATE message with our implanted channel bindingAdditional Resources
- Learn more by reading the white paper, “The Security Risk of NTLM.”
- Visit the CrowdStrike Falcon® Identity Protection solutions webpage.
- Request a demo of CrowdStrike Falcon Zero Trust or Falcon Identity Threat Detection products.
- Read expert insights and analysis on other complex threats — download the CrowdStrike 2020 Global Threat Report.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































