This blog was originally published on August 6, 2020.
BloodHound is a public and freely available attack path discovery tool which uses graph theory to map the relationships in an Active Directory (AD) environment. It allows hackers (or pen testers) to know precisely three things: Which computers give admin rights to any user, which users effectively have admin rights to any computer, and effective group membership information (see Figure 1). Because BloodHound can be used maliciously, organizations need to better understand how it is being used, how to protect privileged users, and how to prevent attacks. Security Boulevard recently (August 6, 2020) revived this discussion on a popular AD testing (or attacker) tool, so we’re refreshing your reminder of the CrowdStrike® solution (formerly Preempt Security).
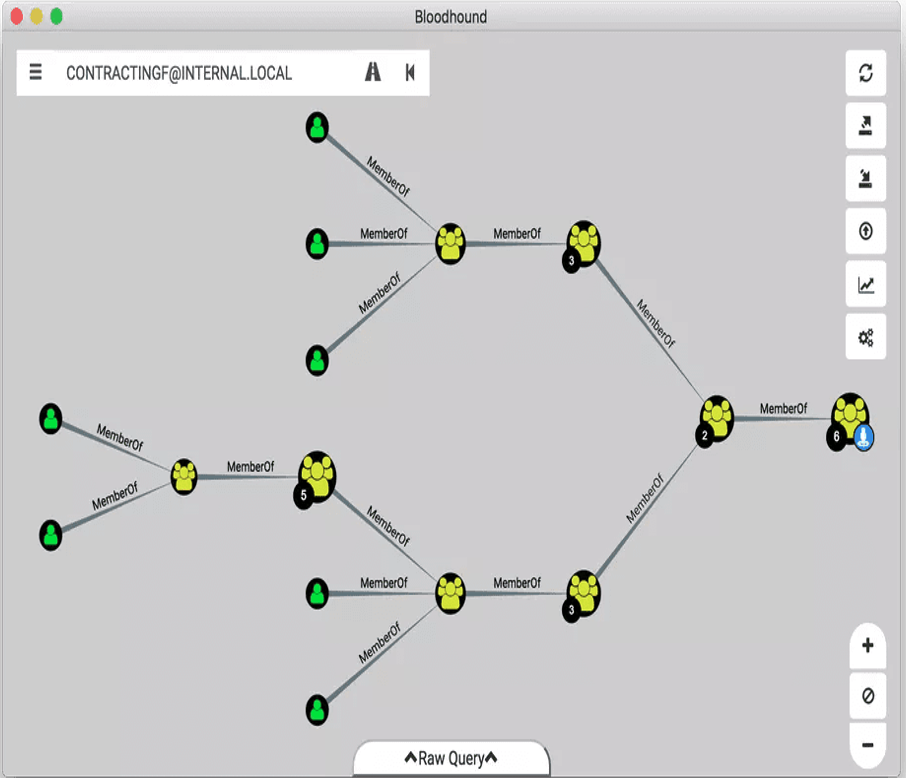 Figure 1. BloodHound Link Analysis
Figure 1. BloodHound Link Analysis
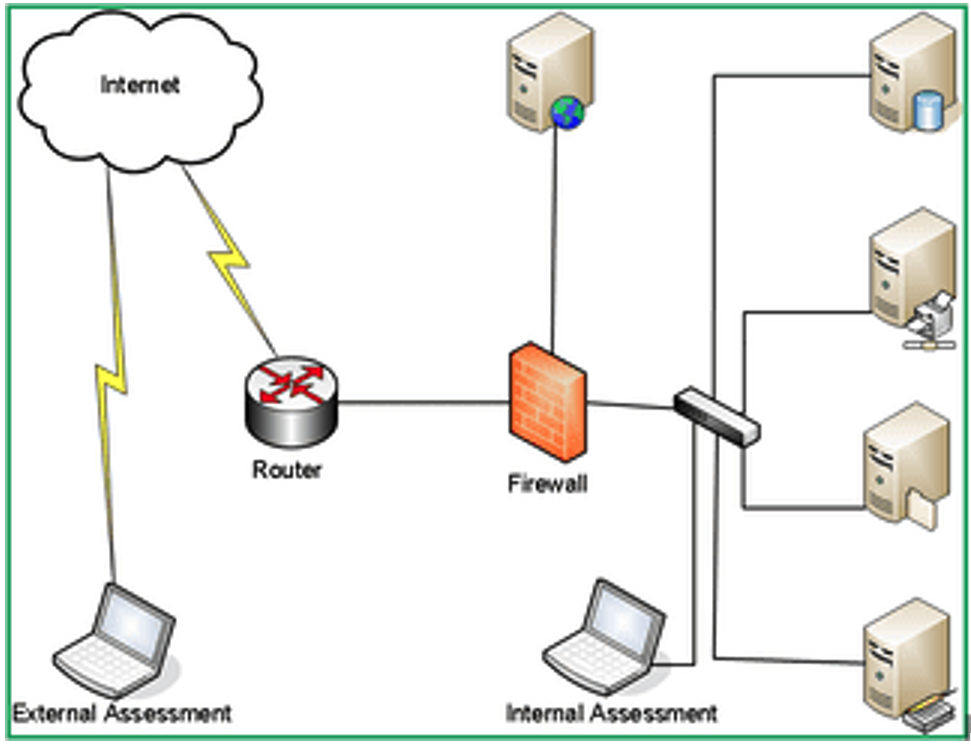 Figure 2. Internal vs. External Assessment
Figure 2. Internal vs. External Assessment
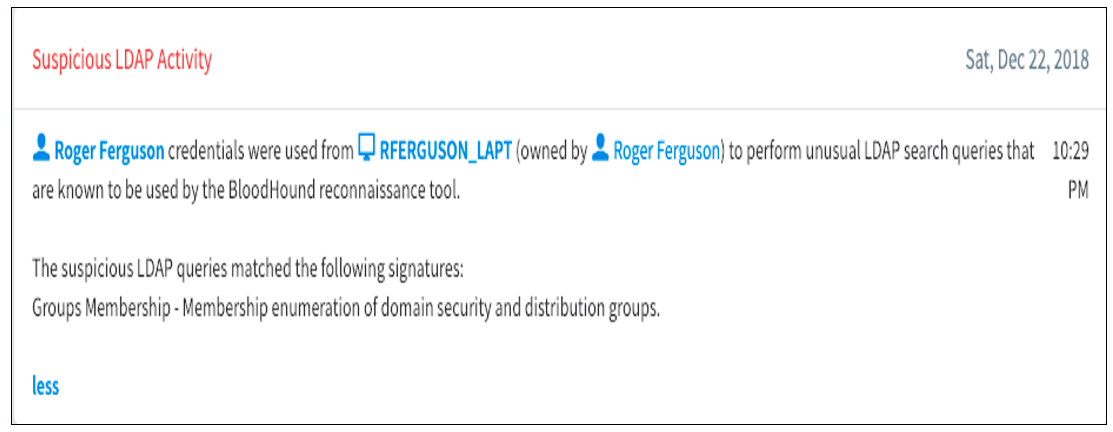 Figure 3. Catching a BloodHound Attack
In addition to catching malicious activity in real time, CrowdStrike can also alert organizations when administrative accounts are being used on too many machines. This is a critical use case because protecting against administrative account misuse is key to helping your AD administrator and security engineers reduce the attack surface.
Figure 3. Catching a BloodHound Attack
In addition to catching malicious activity in real time, CrowdStrike can also alert organizations when administrative accounts are being used on too many machines. This is a critical use case because protecting against administrative account misuse is key to helping your AD administrator and security engineers reduce the attack surface.
 Figure 1. BloodHound Link Analysis
Figure 1. BloodHound Link AnalysisInternal Pen Testing With BloodHound
Organizations leverage BloodHound for internal pen testing because it helps simulates one of two scenarios:- What an external attacker can accomplish after they get past the initial breach
- What a malicious insider can accomplish once inside the network
 Figure 2. Internal vs. External Assessment
Figure 2. Internal vs. External AssessmentProtecting Privileged Users Against BloodHound
BloodHound session enumeration (as also seen in Figure 2) can assist in expanding network access to the attacker by identifying users and groups that can lead the attacker to access local administrator rights. In order to protect against these internal network attacks that aim to take control of enhanced privileges, organizations need to deploy a solution that can continuously monitor and learn user behavior in the network. When risky behavior is spotted (i.e., a user account with administrative privileges accesses a server that it normally doesn’t access and does so from an unknown device). Organizations need to be able to respond to the potential threat in real time. CrowdStrike offers continuous monitoring and machine learning of user behavior in the network to help detect the use of tools such as BloodHound, Mimikatz, PowerView, and others. In addition to CrowdStrike’s own machine learning and analytics, organizations can set policies that are specific to their own corporate policy and critical infrastructure to make sure that their security is unique to their own environment. Policy can be set to protect any asset to ensure that critical data stores and assets remain protected from insider threats.Preempt BloodHound Attacks
The CrowdStrike Falcon®® platform helps customers detect BloodHound usage in their network to both pass rigorous pen testing audits as well as detect real-life attacks. Below is an example (Figure 3) of how a user leveraging BloodHound to gain administrative privileges was caught. Figure 3. Catching a BloodHound Attack
Figure 3. Catching a BloodHound Attack
Adaptive Threat Prevention
The comprehensiveness of the CrowdStrike policy engine helps organizations enable conditional access policies to respond in real time when BloodHound is detected. In addition, a security risk score will be assigned to the accounts involved in running the tools (both on the endpoint and the user’s account) to generate one or more of the following actions:- Multi-factor authentication (MFA): AD enumeration (not commonly used) can be challenged via conditional access for risky users/conditions by prompting them to verify their identity with MFA. This helps with the end user experience as well as increases AD security.
- Block: After suspicious activity is detected trying to access network services, the system can
instantly block or limit the accounts from access. - Reset Password: Since pen testing is highly dependent on stealing passwords, resetting passwords is a good security practice for when any weak password is detected or when suspicious user activity is occurring.
Additional Resources
- Learn more by reading a white paper, “Disrupting the Cyber Kill Chain: How to Contain Use of Tools and Protocols.”
- Visit the CrowdStrike Falcon® Identity Protection solutions webpage.
- Request a demo of CrowdStrike Falcon Zero Trust or Falcon Identity Threat Detection products.
- Read expert insights and analysis on other complex threats — download the CrowdStrike 2020 Global Threat Report.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































