From The Front Lines
Follow the Adversary: The Top 3 Red Team Exploitation Paths from 2024
Though 2024 may be behind us, many of the security threats and vulnerabilities that organizations faced last year remain. The CrowdStrike Professional Services Red Team tracks them all in its efforts […]
Redefining Incident Response in the Modern Era
CrowdStrike Incident Response (IR) services sees firsthand why organizations facing today’s evolving threat landscape require advanced capabilities to detect, respond, and remediate cyberattacks in ne[…]
CrowdStrike Named a Leader with “Bold Vision” in 2024 Forrester Wave for Cybersecurity Incident Response Services
CrowdStrike has been named a Leader in The Forrester Wave™: Cybersecurity Incident Response Services, Q2 2024. This recognition demonstrates for us our unwavering commitment to providing the technolog[…]
How to Defend Employees and Data as Social Engineering Evolves
Adversaries have long used social engineering to trick their victims into providing access or information not available to the public. Social engineering continues to prove effective and will likely b[…]
The Anatomy of an ALPHA SPIDER Ransomware Attack
ALPHA SPIDER is the adversary behind the development and operation of the Alphv ransomware as a service (RaaS). Over the last year, ALPHA SPIDER affiliates have been leveraging a variety of novel tech[…]
CrowdStrike Services Offers Incident Response Executive Preparation Checklist
The CrowdStrike Incident Response Executive Preparation Checklist is a template to help organizations consider the roles of their executives before, during and after an incident. CrowdStrike tabletop […]
Business as Usual: Falcon Complete MDR Thwarts Novel VANGUARD PANDA (Volt Typhoon) Tradecraft
VANGUARD PANDA Background On May 24, 2023, industry and government sources detailed China-nexus activity in which the threat actor dubbed Volt Typhoon targeted U.S.-based critical infrastructure entit[…]
Discovering the MOVEit Vulnerability with the CrowdStrike Falcon Platform
On June 15, 2023, Progress Software announced a critical vulnerability in the MOVEit file transfer software (CVE-2023-35708). This was the third vulnerability impacting the file transfer software (May[…]
Adversaries Go Hands-On in Japan: Know the Threat and Know the Solution
Japan, known for its innovation and efficiency, is a globally recognized industry leader. This puts Japan-based organizations at risk of being recognized as potentially valuable targets by both crimin[…]
Movin’ Out: Identifying Data Exfiltration in MOVEit Transfer Investigations
Summary Points Organizations around the globe continue to experience the fallout of the MOVEit Transfer exploit CVE-2023-34362 CrowdStrike incident responders have identified evidence of mass file exf[…]
Behind the Curtain: Falcon OverWatch Hunting Leads Explained
Most hunting enthusiasts agree that the thrill of hunting lies in the chase. Equipped with experience and tools of their trade, hunters skillfully search for signs of prey — a broken twig, a track in […]
How Falcon OverWatch Investigates Malicious Self-Extracting Archives, Decoy Files and Their Hidden Payloads
Self-extracting (SFX) archive files have long served the legitimate purpose of easily sharing compressed files with someone who lacks the software to decompress and view the contents of a regular arch[…]
CrowdStrike Discovers First-Ever Dero Cryptojacking Campaign Targeting Kubernetes
CrowdStrike has discovered the first-ever Dero cryptojacking operation targeting Kubernetes infrastructure. Dero is a cryptocurrency that claims to offer improved privacy, anonymity and higher and fas[…]
CrowdStrike Falcon OverWatch Insights: 8 LOLBins Every Threat Hunter Should Know
After dissecting a full year’s worth of interactive intrusion data, the CrowdStrike® Falcon OverWatch™ Elite team has identified the most commonly abused living-off-the-land binaries — and distilled t[…]
How Adversaries Can Persist with AWS User Federation
CrowdStrike Services identified a novel technique used by threat actors that escapes typical containment practices and permits persistence in victim AWS environments. The technique requires that the a[…]
Walking Through Walls: Four Common Endpoint Tools Used to Facilitate Covert C2
Adversaries continue to find new and innovative ways to penetrate an organization’s defenses. Defenders who focus on plugging these holes can find themselves exhausted and frustrated. Hunting for adve[…]
4 Ways Adversaries Hijack DLLs — and How CrowdStrike Falcon OverWatch Fights Back
Dynamic link library (DLL) hijacking is frequently written about by defenders due to its applications in evading automated detections. This technique is even more frequently used by adversaries in int[…]
Enterprise Remediation with CrowdStrike and MOXFIVE, Part 2: Strategies for Containing and Recovering
In Part 1 of this blog series, we highlighted the benefits of CrowdStrike’s investigative approach and the CrowdStrike Falcon® Real Time Response capabilities for avoiding a significant incident in th[…]
Enterprise Remediation with CrowdStrike and MOXFIVE, Part 1: Five Tips for Preparing and Planning
Timing is everything when it comes to responding and recovering from a widespread, destructive attack. As threat actors operate undetected across a victim network and get deeper into the attack lifecy[…]
OWASSRF: CrowdStrike Identifies New Exploit Method for Exchange Bypassing ProxyNotShell Mitigations
CrowdStrike recently discovered a new exploit method (called OWASSRF) consisting of CVE-2022-41080 and CVE-2022-41082 to achieve remote code execution (RCE) through Outlook Web Access (OWA). The new e[…]
CrowdStrike Services Helps Organizations Prioritize Patching Vulnerabilities with CrowdStrike Falcon Spotlight
When the CrowdStrike Services team conducts a proactive security engagement, such as a Cybersecurity Maturity Assessment or Tabletop Exercise, it often uses CrowdStrike Falcon® Spotlight to identify w[…]
Not a SIMulation: CrowdStrike Investigations Reveal Intrusion Campaign Targeting Telco and BPO Companies
CrowdStrike Services reviews a recent, extremely persistent intrusion campaign targeting telecommunications and business process outsourcing (BPO) companies and outlines how organizations can defend a[…]
How Falcon OverWatch Hunts for Out-of-Band Application Security Testing
CrowdStrike Falcon OverWatch™ threat hunters frequently uncover security testing activity in the course of routine hunting. While much of this activity can be confidently attributed to planned and san[…]
Discovering the Critical OpenSSL Vulnerability with the CrowdStrike Falcon Platform
11/1 UPDATE Additional details and mitigating patches are now available on OpenSSL’s website. Two CVEs have been published: CVE-2022-3602 (buffer overflow with potential for remote code execution) and[…]
Adversaries Have Their Heads in Your Cloud
The rapid proliferation of cloud technology has empowered organizations to meet complex challenges with innovative solutions. This flexibility, however, is the antithesis of security — each new cloud […]
“Gitting” the Malware: How Threat Actors Use GitHub Repositories to Deploy Malware
The CrowdStrike Falcon® Complete™ managed detection and response (MDR) team recently uncovered a creative and opportunistic interpretation of a watering hole attack that leverages GitHub to gain acces[…]
CrowdStrike Falcon® Platform Identifies Supply Chain Attack via a Trojanized Comm100 Chat Installer
The CrowdStrike Falcon® platform, leveraging a combination of advanced machine learning and artificial intelligence, identified a new supply chain attack during the installation of a chat-based custom[…]
2022 Threat Hunting Report: Falcon OverWatch Looks Back to Prepare Defenders for Tomorrow’s Adversaries
Another turbulent year for cybersecurity finds itself right at home alongside global economic headwinds and geopolitical tensions. This year has been defined by rampant affiliate activity, a seemingly[…]
Defense Against the Lateral Arts: Detecting and Preventing Impacket’s Wmiexec
Impacket, an open source collection of Python modules for manipulating network protocols, contains several tools for remote service execution, Windows credential dumping, packet sniffing and Kerberos […]
Falcon OverWatch Elite in Action: Tailored Threat Hunting Services Provide Individualized Care and Support
The threat presented by today’s adversaries is as pervasive as it is dangerous — eCrime and state-nexus actors alike are attempting to infiltrate companies and organizations of all sizes and across al[…]
The Call Is Coming from Inside the House: CrowdStrike Identifies Novel Exploit in VOIP Appliance
CrowdStrike Services recently performed an investigation that identified a compromised Mitel VOIP appliance as the threat actor’s entry point. The threat actor performed a novel remote code execution […]
Seven Key Ingredients of Incident Response to Reduce the Time and Cost of Recovery
When a breach occurs, time is of the essence. The decisions you make about whom to collaborate with and how to respond will determine how much impact the incident is going to have on your business ope[…]
OverWatch Casts a Wide Net for Follina: Hunting Beyond the Proof of Concept
CVE-2022-30190, aka Follina, was published by @nao_sec on Twitter on May 27, 2022 — the start of Memorial Day weekend in the U.S. — highlighting once again the need for round-the-clock cybersecurity c[…]
How Defenders Can Hunt for Malicious JScript Executions: A Perspective from OverWatch Elite
An adversary’s ability to live off the land — relying on the operating system’s built-in tooling and user-installed legitimate software rather than tooling that must be brought in — may allow them to […]
Hunting a Global Telecommunications Threat: DecisiveArchitect and Its Custom Implant JustForFun
The security landscape is constantly developing to provide easier ways to establish endpoint visibility across networks through the use of endpoint detection and response (EDR) utilities. However, cer[…]
Proactive Threat Hunting Bears Fruit: Falcon OverWatch Detects Novel IceApple Post-Exploitation Framework
The CrowdStrike Falcon® OverWatch™ proactive threat hunting team has uncovered a sophisticated .NET-based post-exploitation framework, dubbed IceApple. Since OverWatch’s first detection in late 2021, […]
Compromised Docker Honeypots Used for Pro-Ukrainian DoS Attack
Container and cloud-based resources are being abused to deploy disruptive tools. The use of compromised infrastructure has far-reaching consequences for organizations who may unwittingly be participat[…]
Navigating the Five Stages of Grief During a Breach
Every security professional dreads “The Phone Call.” The one at 2 a.m. where the tired voice of a security analyst on the other end of the line shares information that is soon drowned out by your hear[…]
Cloudy with a Chance of Unclear Mailbox Sync: CrowdStrike Services Identifies Logging Inconsistencies in Microsoft 365
Multiple investigations and testing by the CrowdStrike Services team identified inconsistencies in Azure AD sign-in logs that incorrectly showed successful logins via Internet Mail Access Protocol (IM[…]
Falcon OverWatch Threat Hunting Contributes to Seamless Protection Against Novel BlackCat Attack
In an effort to stay ahead of improvements in automated detections and preventions, adversary groups continually look to new tactics, techniques and procedures (TTPs), and new tooling to progress thei[…]
Falcon OverWatch Threat Hunting Uncovers Ongoing NIGHT SPIDER Zloader Campaign
Over recent months, the CrowdStrike Falcon® OverWatch™ team has tracked an ongoing, widespread intrusion campaign leveraging bundled .msi installers to trick victims into downloading malicious payload[…]
Nowhere to Hide: Detecting a Vishing Intrusion at a Retail Company
The CrowdStrike Falcon OverWatch™ 2021 Threat Hunting Report details the interactive intrusion activity observed by hunters from July 2020 to June 2021. While the report brings to light some of the ne[…]
Hunting pwnkit Local Privilege Escalation in Linux (CVE-2021-4034)
In November 2021, a vulnerability was discovered in a ubiquitous Linux module named Polkit. Developed by Red Hat, Polkit facilitates the communication between privileged and unprivileged processes on […]
Early Bird Catches the Wormhole: Observations from the StellarParticle Campaign
StellarParticle is a campaign tracked by CrowdStrike as related to the SUNSPOT implant from the SolarWinds intrusion in December 2020 and associated with COZY BEAR (aka APT29, "The Dukes"). The Stella[…]
Better Together: The Power of Managed Cybersecurity Services in the Face of Pressing Global Security Challenges
The results from the 2021 Global Security Attitude Survey paint a bleak picture of how organizations globally are feeling about the cybersecurity landscape before them. Organizations are grappling wit[…]
Mind the MPLog: Leveraging Microsoft Protection Logging for Forensic Investigations
In an incident response investigation, CrowdStrike analysts use multiple data points to parse the facts of who, what, when and how. As part of that fact-finding mission, analysts investigating Windows[…]
CrowdStrike Services Offers Incident Response Tracker for the DFIR Community
The CrowdStrike Incident Response Tracker is a convenient spreadsheet that includes sections to document indicators of compromise, affected accounts, compromised systems and a timeline of significant […]
OverWatch Exposes AQUATIC PANDA in Possession of Log4Shell Exploit Tools During Hands-on Intrusion Attempt
Following the Dec. 9, 2021, announcement of the Log4j vulnerability, CVE 2021-44228, CrowdStrike Falcon® OverWatch™ has provided customers with unrivaled protection and 24/7/365 vigilance in the face […]
Baselining and Hunting Log4Shell with the CrowdStrike Falcon® Platform
Note: This post first appeared in r/CrowdStrike. First and foremost: if you’re reading this post, I hope you’re doing well and have been able to achieve some semblance of balance between life and work[…]
CrowdStrike Services Launches Log4j Quick Reference Guide (QRG)
The Log4j vulnerability burst onto the scene just a few weeks ago, but to many defenders it already feels like a lifetime. It has rapidly become one of the top concerns for security teams in 2021, and[…]
CrowdStrike Launches Free Targeted Log4j Search Tool
The recently discovered Log4j vulnerability has serious potential to expose organizations across the globe to a new wave of cybersecurity risks as threat actors look to exploit this latest vulnerabili[…]
Nowhere to Hide: Detecting SILENT CHOLLIMA’s Custom Tooling
CrowdStrike Falcon OverWatch™ recently released its annual threat hunting report, detailing the interactive intrusion activity observed by hunters over the course of the past year. The tactics, techni[…]
Credentials, Authentications and Hygiene: Supercharging Incident Response with Falcon Identity Threat Detection
CrowdStrike Incident Response teams leverage Falcon Identity Threat Detection (ITD) for Microsoft Active Directory (AD) and Azure AD account authentication visibility, credential hygiene and multifact[…]
Falcon OverWatch Granted Patents for Two Innovative Workflow Tools
The breadth and depth of data available to CrowdStrike Falcon OverWatch™ threat hunters has the potential to be a double-edged sword. On one side, the wealth of data gives hunters the comprehensive vi[…]
Tales From the Cryptojacking Front Lines
Throughout 2021, the CrowdStrike Falcon OverWatch™ team has observed the volume of cryptojacking intrusions more than quadruple compared to 2020. ECrime adversaries are using cryptojacking as a means […]
Nowhere to Hide: Protecting a Telecommunications Company from Targeted Attacks
CrowdStrike Falcon OverWatch™ recently released its annual threat hunting report, detailing the interactive intrusion activity observed by hunters over the course of the past year. Intrusions against […]
OverWatch Elite In Action: Prompt Call Escalation Proves Vital to Containing Attack
For a defender, time is critical. As CrowdStrike Falcon® OverWatch™ threat hunters know firsthand, adversaries can move from initial access to lateral movement in just minutes. This blog and the real […]
Stopping GRACEFUL SPIDER: Falcon Complete’s Fast Response to Recent SolarWinds Serv-U Exploit Campaign
This blog describes how the CrowdStrike Falcon® Complete™ team quickly responded to a recent campaign involving the SolarWinds Serv-U product exploitation. SolarWinds issued a public notice of the vul[…]
LightBasin: A Roaming Threat to Telecommunications Companies
LIMINAL PANDA has targeted telecommunications organizations in Africa and South Asia using a range of custom tools — including SIGTRANslator, CordScan and PingPong — while demonstrating in-depth under[…]
Hunting for the Confluence Exploitation: When Falcon OverWatch Becomes the First Line of Defense
Today’s security defenders are faced with a continuously evolving battleground. The number of security vulnerabilities uncovered annually has grown every year for the past four years. Moreover, advers[…]
The Myth of Part-time Threat Hunting, Part 2: Leveraging the Power of Human Ingenuity
The race between hunter and hunted is defined as much by stealth as it is by speed. In Part 2 of this two-part blog series, we dive into why having hunters immersed full time in the threat hunting mis[…]
SuperMem: A Free CrowdStrike Incident Response Tool for Automating Memory Image Processing
Performing memory analysis in incident response investigations can be tedious and challenging because of the lack of commercial options for processing memory samples, no all-in-one open-source tools t[…]
Falcon OverWatch Hunts Down Adversaries Where They Hide
There is an endless struggle between hunters and adversaries. As soon as hunters shine a light on the latest malicious activities, adversaries pivot and find a new way to hide in the shadows. Indeed, […]
Shining a Light on DarkOxide
Since September 2019, Falcon OverWatch™ has been tracking an as yet unattributed actor, conducting targeted operations against organizations within the Asia Pacific (APAC) semiconductor industry. Crow[…]
2021 Threat Hunting Report: OverWatch Once Again Leaves Adversaries with Nowhere to Hide
This time last year, the CrowdStrike Falcon® OverWatch™ reported on mounting cyber threats facing organizations as they raced to adopt work-from-home practices and adapt to constraints imposed by the […]
Malware Analysis in the Modern SOC
The security operations center, or SOC, is the heart and soul of an enterprise that identifies, investigates and remediates security threats. However, modern-day threats continue to evolve, making it […]
Hypervisor Jackpotting, Part 2: eCrime Actors Increase Targeting of ESXi Servers with Ransomware
This is Part 2 of a three-part blog series. Read Part 1 and Part 3. CrowdStrike has observed a significant increase in eCrime actors targeting VMware ESXi hypervisors with ransomware since our Februar[…]
NTLM Keeps Haunting Microsoft
Two severe Windows NT LAN Manager (NTLM) vulnerabilities were recently disclosed: PetitPotam and AD-CS relay (specifically ESC8). These vulnerabilities follow a pattern of NTLM issues in recent years.[…]
Shut the Door: Guarding Against SonicWall GMS Remote Code Execution (CVE-2021-20020)
The Advanced Research Team at CrowdStrike Intelligence discovered two vulnerabilities in SonicWall Global Management System 9.3 (GMS) that, when combined, allow unauthenticated attackers to remotely e[…]
Keep Your Tools Patched: Preventing Remote Code Execution with Falcon Complete
In this blog, we describe a recent incident that highlights the CrowdStrike Falcon® Complete™ managed detection and response team’s ability to act as an extension of our customer’s security team to qu[…]
Squashing SPIDERS: Threat Intelligence, Threat Hunting and Rapid Response Stops SQL Injection Campaign
In this blog, we describe a campaign of recent activity where CrowdStrike observed an actor likely related to CARBON SPIDER performing SQL injections in order to gain code execution as an initial infe[…]
Visibility in Incident Response: Don’t Chase Ghosts in Your IT Estate
To effectively respond to a cybersecurity incident, having complete visibility into all assets (endpoint devices, applications, user accounts) across your IT estate is a critical success factor for re[…]
How to Avoid Being Impacted by a Managed Service Provider (MSP) Breach
Managed service providers (MSPs) provide extremely important and valuable services by assisting organizations with information technology related tasks such as provisioning software or Active Director[…]
New Ransomware Variant Uses Golang Packer
CrowdStrike recently observed a ransomware sample borrowing implementations from previous HelloKitty and FiveHands variants and using a Golang packer compiled with the most recent version of Golang (G[…]
The Myth of Part-time Hunting, Part 1: The Race Against Ever-diminishing Breakout Times
The term “threat hunting” is increasingly thrown around the cybersecurity industry as a catch-all for any proactive or human-lead defensive security measures. This is evidenced by the SANS 2020 Threat[…]
Response When Minutes Matter: Falcon Complete Disrupts WIZARD SPIDER eCrime Operators
In this blog, we describe a string of recent incidents in which the CrowdStrike Falcon® Complete™ team observed a financially motivated eCrime operator (likely WIZARD SPIDER) use compromised external […]
Ransomware Actors Evolved Their Operations in 2020
In 2020, CrowdStrike Services observed the continued evolution and proliferation of eCrime adversaries engaging in big game hunting (BGH) ransomware techniques. This trend is continuing into 2021 — a […]
CrowdStrike Falcon® Protects Customers from Recent COZY BEAR Sophisticated Phishing Campaign
A recent sophisticated phishing campaign that delivers advanced malware is targeting diplomatic and sensitive organizations and think tanks around the world. This activity cluster, tracked by CrowdStr[…]
Another Brick in the Wall: eCrime Groups Leverage SonicWall VPN Vulnerability
BLOG UPDATE AUG. 6, 2021: Following further communication with the SonicWall PSIRT, the vulnerability was identified as CVE-2021-20028, affecting End of Life SonicWall VPN Devices running SMA/SRA vers[…]
Under Attack: Protecting Against Conti, DarkSide, REvil and Other Ransomware
CrowdStrike predicted in 2020 that the ransomware threat would only worsen, and news reports since have borne this out. Stories of ransomware attacks since the start of May 2021 alone include: DarkSid[…]
Falcon Complete Disrupts Malvertising Campaign Targeting AnyDesk
Although malvertising has been around for quite a while, it continues to be an effective way to lure unsuspecting users to install malware. In this blog, we describe a clever malvertising campaign tha[…]
Cyber Insurance Is Not a Substitute for Cybersecurity
Ransomware is becoming increasingly pernicious — recently, the DarkSide attack disrupted a major U.S. fuel pipeline, and soon after another ransomware attack targeted four countries connected with the[…]
Response When Minutes Matter: When Good Tools Are Used for (R)Evil
This Falcon Complete incident response investigation recap was originally published by IT-daily.net on Apr. 13, 2021. It was late on a Saturday afternoon, and the Southern Hemisphere CrowdStrike Falco[…]
Where Is the Cyber Insurance Market Going?
The ongoing ransomware outbreak has led to frequent and significant security incidents at organizations across the globe, such as the recent DarkSide attack that disrupted a major fuel pipeline — one […]
DarkSide Goes Dark: How CrowdStrike Falcon Customers Were Protected
The CrowdStrike Falcon® platform provides CrowdStrike clients with protection from DarkSide ransomware DarkSide is a ransomware as a service (RaaS) associated with an eCrime group tracked by CrowdStri[…]
Response When Minutes Matter: Rising Up Against Ransomware
This blog describes a recent incident that highlights the CrowdStrike Falcon® Complete™ team’s ability to act as an extension of a customer’s security team to quickly detect, triage and contain an act[…]
Ransomware Preparedness: A Call to Action
Hardly a day passes without news of another company, hospital, school district or municipal government temporarily brought to a halt by ransomware. In fact, ransomware attacks have become so commonpla[…]
The Pernicious Effects of Ransomware
Ransomware is hardly new, but several recent high-profile cases underscore that it not only remains a persistent threat, it’s also a growing one. The “great pivot” to remote work in 2020 increased the[…]
Security in Sweatpants: Embracing Remote Workers via Zero Trust
The “Great Pivot” of 2020, when the global pandemic forced many organizations to allow employees work from anywhere, accelerated both the adoption of cloud technology and support for hybrid working en[…]
Falcon Complete Stops Microsoft Exchange Server Zero-Day Exploits
This week, Microsoft reported a rare cybersecurity event: an ongoing mass exploitation of Microsoft Exchange servers by an alleged state-sponsored adversary, driven through a variety of zero-day explo[…]
Mapping It Out: Analyzing the Security of eBPF Maps
Extended Berkeley Packet Filter, or eBPF, is a fascinating part of the Linux kernel that has seen rapid growth and improvement over the last few years. Originally designed for high-speed packet filter[…]
Don’t Get Schooled: Understanding the Threats to the Academic Industry
The academic and education industry is large and complex. It comprises a diverse range of institutions, from elementary schools through to research organizations, and spans both the public and private[…]
Blocking SolarMarker Backdoor
In this blog, we take a look at a recent detection that was blocked by the CrowdStrike Falcon®® platform’s next-generation antivirus (NGAV). SolarMarker* backdoor features a multistage, heavily obfusc[…]
Skeletons in the IT Closet: Seven Common Microsoft Active Directory Misconfigurations that Adversaries Abuse
The modern IT organization has a wide variety of responsibilities and competing priorities. As a result, cybersecurity is often overlooked in favor of projects that have an immediate impact on busines[…]
Holiday Cyber Warnings Will Echo Across 2021
A recent article in Dark Reading, “Nowhere to Hide: Don’t Let Your Guard Down This Holiday Season” by CrowdStrike Product Director Scott Taschler, provides ominous warnings of adversary activity and p[…]
Intelligence-led Rapid Recovery: Getting Back to Business Faster
When a cybersecurity incident occurs, it can be an overwhelming experience resulting in infected endpoints, data theft, user disruption, extortion and even downtime that causes business interruption. […]
2020 Key Findings and Trends From Incident Response and Proactive Services
The annual CrowdStrike Services Cyber Front Lines Report released this month shares statistics, trends and themes gleaned from a year’s worth of data and observations by our world-class incident respo[…]
CrowdStrike Launches Free Tool to Identify and Help Mitigate Risks in Azure Active Directory
Executive Summary CrowdStrike launches CrowdStrike Reporting Tool for Azure (CRT), a free community tool that will help organizations quickly and easily review excessive permissions in their Azure AD […]
Leftover Lunch: Finding, Hunting and Eradicating Spicy Hot Pot, a Persistent Browser Hijacking Rootkit
In this blog, we take a look at a recent incident that involved a persistent browser hijacking rootkit dubbed “Spicy Hot Pot.” The name comes from Huorong (Tinder) Security, which first publicly repor[…]
Hiding in Plain Sight: Remediating “Hidden” Malware with Real Time Response
Malware remediation is not always clear-cut. In this blog post, the CrowdStrike® Falcon Complete™ and Endpoint Recovery Services teams take you behind the scenes to highlight just one of numerous chal[…]
This Year’s CrowdStrike Services Report Offers Observations on 2020 Cyber Threat Trends and Insights for 2021
The CrowdStrike Services team has issued its latest report: “CrowdStrike Services Cyber Front Lines Report: Observations From the Front Lines of Incident Response and Proactive Services in 2020 and In[…]
CrowdStrike Offers Cybersecurity Professional Services in AWS Marketplace
Digital transformation initiatives are accelerating the adoption of cloud technologies across industries as organizations look to evolve their business processes and models. CrowdStrike and AWS are wo[…]
Hacking Farm to Table: Threat Hunters Uncover Rise in Attacks Against Agriculture
Life on the farm isn’t what it used to be. With overall cyberattacks on the rise, even agriculture has found itself in the crosshairs of cyber threat actors. In fact, during the last ten months alone,[…]
The Critical Role of Cybersecurity in M&A: Part 3, Post-Close
In the post-close phase of an M&A transaction, the deal may be done but the job of integration has just begun. From a systems point of view, this means connecting the networks, applications, directori[…]
The Critical Role of Cybersecurity in M&A: Part 2, Pre-Close
This is Part 2 of our three-part blog series on the critical importance of cybersecurity in the M&A process. Part 1 addressed due diligence, and in this blog, we cover the pre-close phase. Part 3 disc[…]
The Critical Role of Cybersecurity in M&A: Part 1, Due Diligence
COVID-19 has disrupted virtually every aspect of business, and the mergers and acquisitions (M&A) pipeline is no exception. However, while overall M&A activity had fallen by more than 55% year over ye[…]
Duck Hunting with Falcon Complete: Remediating a Fowl Banking Trojan, Part 3
This blog is the last in a three-part series presenting the CrowdStrike® Falcon Complete™ team’s analysis of the recent QakBot campaigns observed in the wild and outlining a strategy for the remote id[…]
Successful Threat Hunting Starts with a SEARCH
Threat hunting is the discipline of employing human analysts to actively search for and disrupt distinctly human threats. It leverages smart and creative defenders to identify the stealthy techniques […]
Duck Hunting with Falcon Complete: A Fowl Banking Trojan Evolves, Part 2
This blog is Part 2 of a three-part blog series detailing the reemergence and evolution of QakBot in the spring and summer of 2020. In this installment we cover analysis of the QakBot ZIP-based delive[…]
Duck Hunting with Falcon Complete: Analyzing a Fowl Banking Trojan, Part 1
Adversaries constantly develop new tactics that enhance their capabilities to deploy malware across networked environments and monetize infected systems. This blog is Part 1 of a three-part series det[…]
Getting the Bacon from the Beacon
In recent months, CrowdStrike® Services has observed a continued increase in the use of Cobalt Strike by eCrime and nation-state adversaries to conduct their operations following the initial access to[…]
New Report: Falcon OverWatch Threat Hunting Leaves Adversaries with Nowhere to Hide
CrowdStrike® Falcon OverWatch™ has released its new report, 2020 Threat Hunting Report: Insights from the CrowdStrike Falcon® OverWatch Team. Now in its third year, this report continues to pull back […]
Response When Minutes Matter: A Simple Clue Uncovers a Global Attack Campaign
In this blog, we describe a recent incident that highlights the CrowdStrike® Falcon Complete™ team’s ability to act as an extension of our customer’s security team to quickly detect, triage and contai[…]
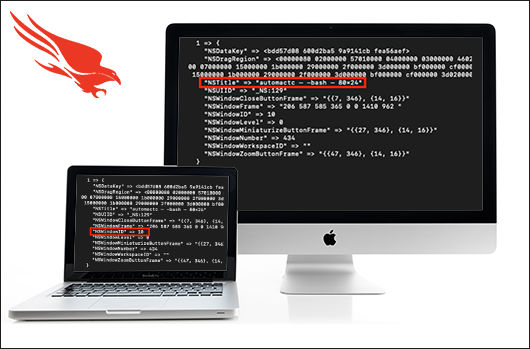
Finding Waldo: Leveraging the Apple Unified Log for Incident Response
As of macOS 10.12 Sierra, incident responders have been able to turn to a new endpoint log source for investigative answers: the Apple Unified Log (AUL). This log format, standardized across the Apple[…]
The Current State of Exploit Development, Part 2
In Part 1 of this two-part blog series, we addressed binary exploitation on Windows systems, including some legacy and contemporary mitigations that exploit writers and adversaries must deal with in t[…]
Response When Minutes Matter: RDP — Remote Desktop Pwnage, Part 2
In Part 1 of this two-part “Tales from the Trenches” blog, we examined a stealthy Remote Desktop Protocol (RDP) intrusion uncovered by CrowdStrike® Falcon CompleteTM experts. In this installment, we’l[…]
Response When Minutes Matter: RDP — Remote Desktop Pwnage, Part 1
Welcome to the CrowdStrike® Falcon CompleteTM team’s first “Tales from the Trenches” blog, where we describe a recent intrusion that shows how the Falcon Complete managed detection and response (MDR) […]
The Current State of Exploit Development, Part 1
Memory corruption exploits have historically been one of the strongest accessories in a good red teamer's toolkit. They present an easy win for offensive security engineers, as well as adversaries, by[…]
Attackers Are Trying to Take a Bite Out of the Apple
Over the past year, CrowdStrike® Services has observed threat actors increasingly targeting macOS environments — and using relatively unsophisticated methods to gain access. Even though workplace macO[…]
Manufacturing Industry in the Adversaries’ Crosshairs
Since January 2020, the CrowdStrike® Falcon OverWatch™ managed threat hunting team has observed an escalation in hands-on-keyboard activity. The COVID-19 pandemic has fundamentally shifted the way bus[…]
Automating Remote Remediation of TrickBot via Falcon’s Real Time Response API: Part 2
This is Part 2 in a two-part blog series covering the CrowdStrike® Falcon Complete™ team’s ability to remotely remediate “TrickBot,” a modular trojan that is particularly devastating when paired with […]
Automating Remote Remediation of TrickBot via Falcon’s Real Time Response API: Part 1
The combination of commodity banking malware and ransomware is nothing new in the threat landscape. Adversaries continue to develop new tactics that enhance their capabilities to quickly spread malwar[…]
Attackers Are Targeting Cloud Service Providers
Companies are increasingly relying on cloud-based infrastructure, especially as more of their employees are working remotely — and may continue to do so. Public, private and hybrid clouds allow access[…]
CrowdStrike’s work with the Democratic National Committee: Setting the record straight
June 5, 2020 UPDATE Blog update following the release of the testimony by Shawn Henry, CSO and President of CrowdStrike Services, before the House Intelligence Committee that was recently declassified[…]
The Wand Is Only as Good as the Magician: Getting the Most From Prevention Tools
As organizations deal with newly remote workers and business uncertainty, prevention is more important than ever. Cyberattackers are looking to capitalize on the current climate and seek vulnerabiliti[…]
Employing FeatureUsage for Windows 10 Taskbar Forensics
During a cybersecurity investigation, digital forensics and incident response (DFIR) professionals need to obtain information from different artifacts to determine exactly what has occurred on a machi[…]
Staying Off the Land: A Threat Actor Methodology
With offense-focused methodologies being created around “living off the land” and “bring your own land,” we would like to cover a somewhat overlooked concept: “staying off the land.” This simple conce[…]
Threat Hunting Uncovers More Intrusions Against Healthcare in Midst of COVID-19 Pandemic
In recent weeks and months, the world has witnessed the global COVID-19 pandemic place unprecedented pressure on the healthcare system. Concurrently, the pandemic has been the catalyst for a paradigm […]
New Emphasis on an Old Problem: Patch Management and Accountability
Vulnerability and patch management is a decades-old cybersecurity problem, and given the current worldwide pandemic and how nation-state and eCrime adversaries are exploiting it — mitigating vulnerabi[…]
How to Sniff Out (and Block) BloodHound Attacks
The growing adversary focus on “big game hunting” (BGH) in ransomware attacks — targeting organizations and data that offer a higher potential payout — has sparked a surge in the use of BloodHound, a […]
Common Attacks and Effective Mitigation: 2020 CrowdStrike Services Report Key Findings (Part 2 of 2)
Your organization is constantly under attack, and every day, adversaries are developing new ways to breach your network. How can you keep them out? You need to know about today’s most common attack te[…]
Know Your Attackers: 2020 CrowdStrike Services Report Key Findings (Part 1 of 2)
The cybersecurity landscape is always evolving, but one thing remains constant: Cyber adversaries continue to be relentless and innovative in their efforts to find gaps in your organization’s security[…]
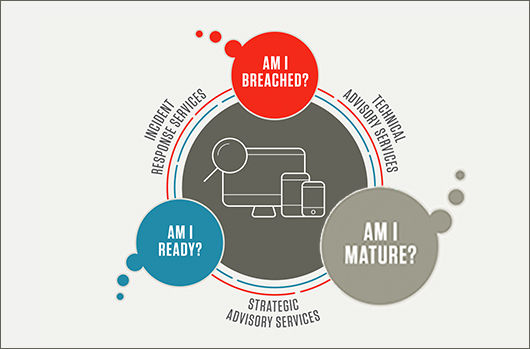
A Roadmap to Cybersecurity Maturity, Part 2: Am I Mature?
A new report from CrowdStrike® Services titled “Achieving Security Maturity: A Roadmap to Building a Robust Cybersecurity Capability” addresses the three questions organizations must answer if they ar[…]
A Roadmap to Cybersecurity Maturity, Part 1: Am I Breached?
A new report from CrowdStrike® Services titled “Achieving Security Maturity: A Roadmap to Building a Robust Cybersecurity Capability,” examines the characteristics of a mature cybersecurity program — […]
A Legal Perspective: Best Practices for Prevention and Immediate Response to a Breach
This blog originally appeared on Nov.20, 2019, as an article in LawyersWeekly.com.au, a site dedicated to independent news, analysis and opinion about the practice of law in Australia. It was written […]
Video Highlights the 4 Key Steps to Successful Incident Response
  Given the current threat landscape, most organizations will likely encounter a cyber incident at some point, which will require them to respond and manage it effectively. The speed, efficie[…]
Weeding out WannaMine v4.0: Analyzing and Remediating This Mineware Nightmare
Although the world of mineware is not new to the security industry, it continues to grow as adversaries develop new capabilities to compromise systems and turn them into bots used for mining cryptocur[…]
Saved by the Shell: Reconstructing Command-Line Activity on MacOS
In Mac OSX Lion (10.7), Apple introduced a feature called “User Interface (UI) Preservation”, intended to save the state of application windows and restore them upon future launches. Like many feature[…]
Falcon OverWatch Threat Hunting Report Finds an Increase in eCrime as Adversaries Mature Their Skills
The CrowdStrike® Falcon OverWatch™ elite threat hunting team has released a new report, The 2019 OverWatch Mid-Year Report: Observations from the Front Lines of Threat Hunting. This is the second year[…]
5 Tips for a Happy Marriage Between IT Cybersecurity and Operational Technology Teams
We sit in a dusty break room, notepads in hand, and nervously watch the corporate IT cybersecurity and industrial operational technology (OT) teams meet one another for the first time. The OT team — c[…]
Unraveling the Spiderweb: Timelining ATT&CK Artifacts Used by GRIM SPIDER
The tactic of singling out large organizations for high ransom payouts has signaled a shift in the eCrime ecosystem, with a focus on targeted, low-volume, high-return criminal activity. It’s a type of[…]
Make Ugly Babies Cute Again: An M&A Crisis Aversion Story
Parents have an inherent predisposition to believe their children are absolutely beautiful. Even when their children aren't much more than tiny blobs that eat, sleep and cry (read: newborns), parents […]
When Tabletop Exercises Become Real-World Events
It happened again a couple months ago; an eerie sense of déjà vu as I read reports about suspected malware-enabled ATM jackpotting in Latin America. I had seen this attack before — not in the headline[…]
Mimikatz in the Wild: Bypassing Signature-Based Detections Using the “AK47 of Cyber”
This blog shares information on some examples of how the CrowdStrike® Falcon® OverWatch™ team has observed the open-source tool known as Mimikatz being used in the wild – including an unusual use of t[…]
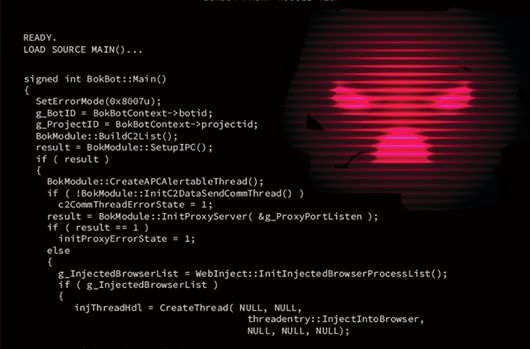
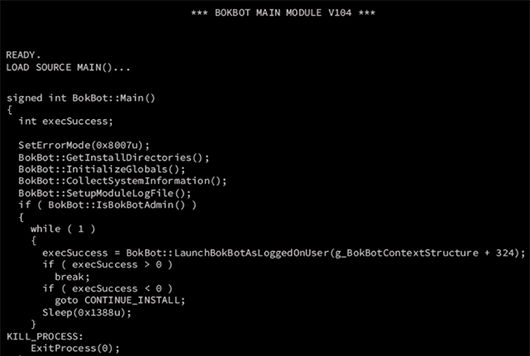
Interception: Dissecting BokBot’s “Man in the Browser”
BokBot: Proxy Module This article is a continuation of CrowdStrike’s recent blog, “Digging Into BokBot’s Core Module,” and provides a detailed analysis of the inner workings of the BokBot proxy module[…]
AutoMacTC: Automating Mac Forensic Triage
Performing macOS incident response (IR) investigations can be challenging, considering the difficulties in quickly capturing, parsing and analyzing forensic data across disparate affected systems. Rec[…]
Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]
\ CrowdStrike® Falcon® detections now align with the MITRE ATT&CK™ framework, a valuable tool that provides consistent, industry-standard terminology for describing and analyzing detections. Sometimes[…]
Threat Actor “Magecart”: Coming to an eCommerce Store Near You
Threat actors that target eCommerce platforms to skim credit card information from online shoppers are commonly referred to under the umbrella threat actor name “Magecart.” This blog analyzes recently[…]
Analyzing Targeted Intrusions Through the ATT&CK Framework Lens [VIDEO]
  The security community is quickly adopting the MITRE ATT&CK framework as a standard way to categorize adversary intrusion behavior. However, one of its potential limitations is a lack of hi[…]
Digging into BokBot’s Core Module
Introduction BokBot, developed and operated by the actor named LUNAR SPIDER, was first observed in 2017 and the CrowdStrike’s Falcon® Overwatch™ and Falcon Intelligence™ teams have analyzed these infe[…]
Adversary Extends Persistence by Modifying System Binaries
At the end of September 2018, the CrowdStrike® Falcon OverWatch™ team identified suspicious interactive activity on a Linux host within a customer’s network infrastructure. An unknown actor accessed a[…]
Confessions of a Responder: The Hardest Part of Incident Response Investigations
It’s not the disk forensics. It’s not the log analysis. It’s not even the lawyers (we love working with law firms!). It’s the lack of an effective technology deployment strategy. CrowdStrike® Services[…]
Managed Threat Hunting Meets the Challenge of the Tenacious Adversary
Dealing with an active, dedicated adversary during an incident is very different than what many consider the more “traditional” incident response process of finding and removing malware. The tradition[…]
Your Jenkins Belongs to Us Now: Abusing Continuous Integration Systems
"Continuous integration (CI) is the process of automating the build and testing of code every time a team member commits a change." — Sam Guckenheimer, Microsoft Azure Introduction Jenkins is the lead[…]
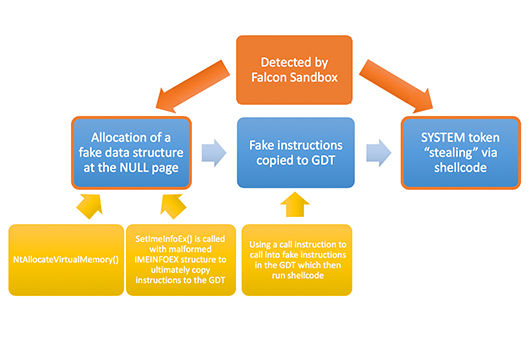
Leveraging Falcon Sandbox to Detect and Analyze Malicious PDFs Containing Zero-Day Exploits
The discovery by security researchers in March 2018 of a PDF sample that contains exploits for two zero-day vulnerabilities has confirmed that exploiting PDF readers is still considered a viable attac[…]
Evaluating Your Organization's Security Approach: Tips For BOD and C-Level Execs
For the last two decades or more, cybersecurity and its failures have directly impacted organizations’ bottom lines.The call for boards of directors and C-level executives to take a more active role i[…]
Kovter Killer: How to Remediate the APT of Clickjacking
Kovter is a well known form of clickjacking malware that has been around for years. While it is mostly nuisance malware, it incorporates neat tricks that are far more advanced than its use case would […]
I Know What You Did Last Month: A New Artifact of Execution on macOS 10.13
Introduction Analysts that perform macOS forensics have had few, if any, artifacts of program execution to rely on during investigations — until now. In macOS 10.13 (High Sierra), Apple introduced Cor[…]
Spark Hot Potato: Passing DataFrames Between Scala Spark and PySpark
Introduction This blog introduces some of the innovative techniques the CrowdStrike Data Science team is using to address the unique challenges inherent in supporting a solution as robust and comprehe[…]
Hiding in Plain Sight: Using the Office 365 Activities API to Investigate Business Email Compromises
Update: While this blog post originally covered the Office 365 Activities API, that functionality has been disabled by Microsoft as of Friday, June 6, 2018. However, there are still data sources avail[…]
An In-Depth Analysis of Samsam Ransomware and BOSS SPIDER
Introduction This analysis provides an in-depth view of the Samsam ransomware, which is developed and operated by the actor tracked by CrowdStrike® Falcon Intelligence™ as BOSS SPIDER. The infection c[…]
Trying to Dance the Samba: An Exercise in Weaponizing Vulnerabilities
Introduction This blog tells the story of a failed Samba exploitation attempt. The goal was to assess what it would take for an adversary to weaponize publicly disclosed vulnerabilities in Samba. The […]
Hidden Administrative Accounts: BloodHound to the Rescue
Defending an organization from today’s sophisticated attacks is no easy task. It often requires security teams to be ready at a moment’s notice to respond to an incident, in addition to managing the d[…]
WannaMine Cryptomining: Harmless Nuisance or Disruptive Threat?
Cryptocurrencies are in high demand. The usage and monetary value of Bitcoin, Litecoin, Ethereum, and many others have skyrocketed worldwide. The increase in purchasing power and liquidity is driving […]
IR Team Investigations Uncover eCrime Use of Nation-State Attack Methods
The much-anticipated CrowdStrike® Cyber Intrusion Services Casebook for 2017 offers detailed accounts of some of the cases the CrowdStrike Services incident response (IR) team has investigated over th[…]
Chip Flaws Spectre and Meltdown are Actually Three Vulnerabilities and Proving Hard to Mitigate
The latest computer flaws to make global headlines are ominously titled “Spectre” and “Meltdown” and they represent a unique breed of trouble, requiring unprecedented industry collaboration and manual[…]
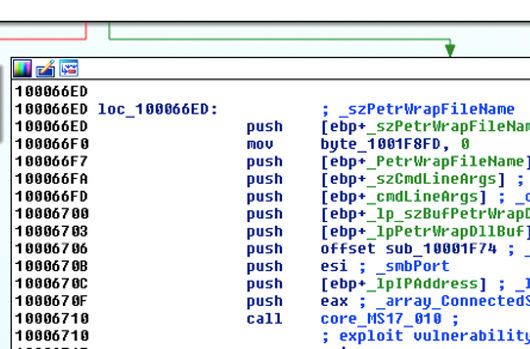
BadRabbit MS17-010 Exploitation Part Two: Elevate Privileges
Overview This post continues the technical analysis of the BadRabbit ransomware attacks discussed in Part One of this two-part series. Part One described how BadRabbit uses MS17-010 to both leak a tra[…]
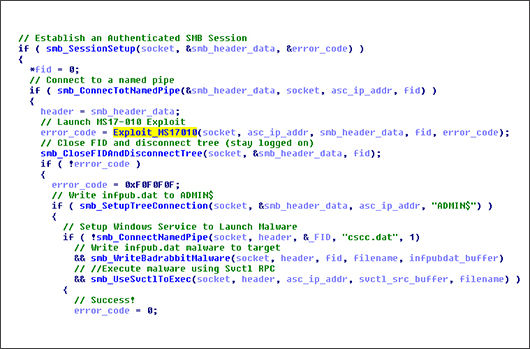
BadRabbit MS17-010 Exploitation Part One: Leak and Control
Overview On October 23, 2017, CrowdStrike® became aware of a new type of ransomware called BadRabbit. The initial infection occurred via a drive-by download masquerading as an Adobe Flash update. Once[…]
CCleaner Stage 2: In-Depth Analysis of the Payload
Overview Recently, CrowdStrike® analyzed the backdoor embedded in the legitimate PC cleaning utility CCleaner version 5.33, as reported in the blog post Protecting the Software Supply Chain: Deep Insi[…]
NotPetya Technical Analysis Part II: Further Findings and Potential for MBR Recovery
Update: Due to naming convention consistency in the industry, CrowdStrike is now calling this variant of Petya - NotPetya. Executive Summary This technical analysis is a continuation of the previous t[…]
NotPetya Technical Analysis - A Triple Threat: File Encryption, MFT Encryption, Credential Theft
Update: Due to naming convention consistency in the industry, CrowdStrike is now calling this variant of Petya - NotPetya. Executive Summary This technical analysis provides an in-depth analysis and r[…]
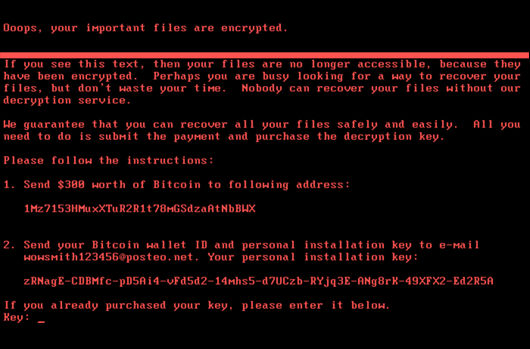
CrowdStrike Protects Against NotPetya Attack
Update: Due to naming convention consistency in the industry, CrowdStrike is now calling this variant of Petya - NotPetya. On June 27 at approximately 10:30 UTC, a new ransomware family began propagat[…]
Stopping Cyber “Shakedowns” — How to Protect Against Extortion-Based eCrime
Internet extortion and “datanapping” have become common occurrences, with increasingly high-profile victims ranging from hospitals to Hollywood studios. A new webcast explores the growth in stealthy e[…]
Seeing the Forest For the Trees: How Proactive Threat Hunting Stops the Mega-Breach
In a recent CrowdCast webinar, CrowdStrike’s Senior Director of Hunting Operations, Kris Merritt, discusses core problems associated with automating cybersecurity detection and how companies seeking t[…]
CrowdResponse Release and new @Tasks modules
With the ongoing need to effectively and quickly detect and respond to attacks, CrowdStrike is excited to release a new version of CrowdResponse. This new update introduces the addition of @Tasks to p[…]
State of the Criminal Address
Over the past few months CrowdStrike has conducted several investigations in the hospitality, food services, and gaming industries, helping organizations investigate and remediate attacks by criminal […]
Solving Intractable Performance Problems Through Vertical Engineering
Owning the Image Object File Format, the Compiler Toolchain, and the Operating System As the Windows kernel continues to pursue in its quest for ever-stronger security features and exploit mitigations[…]
Reconnaissance Detection (Blue Team)
As we move through this Red Team vs. Blue Team series, our intent is to provide insight into both sides of the struggle. That said, detecting reconnaissance activity is something that few blue teams s[…]
Open Source Active Reconnaissance (Red Team)
With the current threat landscape and likelihood of targeted attacks, organizations are dealing with myriad attempts to breach their network on a daily basis. This makes understanding how attackers le[…]
The Security Roadmap – Planning for Job Security
In my previous blog post titled “’You Want Me to Do What?’ A Guide to Interpreting Cybersecurity Recommendations”, we discussed various pitfalls related to interpreting and implementing cybersecurity […]
More Than Just Your eSignature: The Analysis
CrowdStrike recently conducted an investigation for a client operating in the healthcare sector that was subject to an ongoing phishing scam focused on harvesting credentials for cloud email providers[…]
The Importance of Logs
Across all of the nation-state targeted attacks, insider thefts, and criminal enterprises that CrowdStrike has investigated, one thing is clear: logs are extremely important. Event logs from individua[…]
“You Want Me to Do What?” A Guide to Interpreting Cybersecurity Recommendations
Congratulations! You’ve reached the end of yet another proactive engagement with a security services provider. Now that the engagement is over, what does that mean for you and your business? It usuall[…]
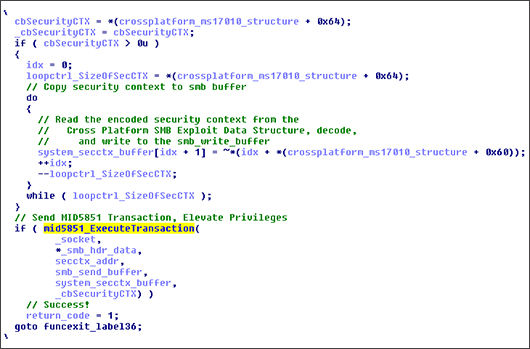
Chopping packets: Decoding China Chopper Web shell traffic over SSL
Introduction The Chopper Web shell is a widely used backdoor by Chinese and other malicious actors to remotely access a compromised Web server. Deployment of the Chopper shell on the server is fairly […]
Surgeon with a Shotgun! - Memory Forensics
With the ever-increasing need for speed and accuracy for digital investigations and incident response, it is imperative that organizations are able to provide answers quickly. These organizations rely[…]
Parsing Sysmon Events for IR Indicators
Intro and Installation A dedicated endpoint monitoring tool is quickly becoming a necessity among organizations to increase visibility, logging, and alerting to combat targeted attacks and commodity m[…]
The Battle for Safe Networks Could End with Open Sharing of Information
In our last post, Shawn Henry, president of CrowdStrike Services and sought-after cybersecurity expert, talked with us about cybersecurity trends in 2014 and 2015. In this installment of that conversa[…]
How cybercrime and cybersecurity affects nations and geopolitics
The Adversary Manifesto recently spoke with Shawn Henry, President of CrowdStrike Services about geopolitics and cybersecurity. Henry is a sought-after expert on cybersecurity who was formerly the exe[…]
The Adversary Manifesto: A Q&A with CrowdStrike’s VP of Threat Intelligence
Adam Meyers runs CrowdStrike's Global Threat Intelligence team and is responsible for creating actionable intelligence that enables customers to understand the who, what, and why of a targeted attack.[…]
Mo' Shells Mo' Problems - Network Detection
Disclaimer: CrowdStrike derived this information from investigations in non-classified environments. Since we value our client's privacy and interests, some data has been redacted or sanitized. In pre[…]
Mo' Shells Mo' Problems - File List Stacking
Disclaimer: CrowdStrike derived this information from investigations in non-classified environments. Since we value our clients’ privacy and interests, some data has been redacted or sanitized. In our[…]
Mo' Shells Mo' Problems - Deep Panda Web Shells
Disclaimer: CrowdStrike derived this information from investigations in non-classified environments. Since we value our client's privacy and interests, some data has been redacted or sanitized. Crowds[…]
- 1
- 2
- 3
- 4
- ...
- 20
- >





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)